Changing a Device's IP Address in Security Cloud Control
When you onboard an device to Security Cloud Control using an IP address, Security Cloud Control stores that IP address in its database and communicates with the device using that IP address. If the IP address of the device changes, you can update the IP address stored in Security Cloud Control to match the new address. Changing the device's IP address on Security Cloud Control does not change device's configuration.
To change the IP address, Security Cloud Control uses to communicate with a device, follow this procedure:
Procedure
|
Step 1 |
In the left pane, click |
|
Step 2 |
Click the Devices tab to locate the device. |
|
Step 3 |
Click the appropriate device type tab. You can use the filter and search functionalities to find the required device. |
|
Step 4 |
Select the device whose IP address it is you want to change. |
|
Step 5 |
Above the Device Details pane, click the edit button next to the device's IP address. 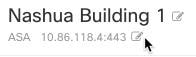
|
|
Step 6 |
Enter the new IP address in the field and click the blue check button. No change is made to the device itself, so the device's Configuration Status will continue to show that it is Synced. |


 . Notice that
. Notice that  .
.
 at the top-left corner.
at the top-left corner.
 icon.
icon.
 Feedback
Feedback