Cisco Secure Firewall Management Center
(formerly Firepower Management Center) Data Sheet
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
The Cisco Secure Firewall Management Center (FMC) is your administrative nerve center for managing critical Cisco network security solutions. It provides complete and unified management over firewalls, application control, intrusion prevention, URL filtering, and advanced malware protection. Quickly and easily go from managing a firewall to controlling applications to investigating threats and remediating malware outbreaks. It is a key part of the broad and integrated Cisco Secure portfolio, delivering in-depth analysis, streamlined security management across the network and cloud, and accelerated incident investigation and response, working across your Cisco and third-party technologies.
Comprehensive visibility and policy control
● Provides exceptional visibility into what is running in your network and cloud so you can see what needs to be protected.
● Rapidly detects suspicious/malicious traffic and quickly creates custom rules to prevent the attack from advancing.
● Built in forensics give a detailed analysis of malware to safely remediate with a graphical representation of all the devices the attack has infected.
● Creates firewall rules and controls thousands of commercial and custom applications used in your environment.
● Shares context with Cisco Secure Workload, allowing firewalls in the network to be “workload aware” for better protection of dynamic applications everywhere in your environment.
● Defines the intrusion prevention levels, URL reputation rules, and malware threat defense policies. It solves problems such as: “When network traffic is coming from a specific country using this particular application with a file attached, I can apply this level of intrusion inspection, analyze the file for malware, and send it to the integrated sandbox, if necessary.”
Automated security for dynamic defense
The Firewall Management Center continually monitors how your network is changing. It streamlines operations and improves your security by:
● Automatically correlating and prioritizing new attack events with your network’s vulnerabilities to alert you to attacks that may have been successful. Your security team can focus on those events that matter the most.
● Analyzing your network’s vulnerabilities and automatically recommending the appropriate security policies to put in place. You can adapt your defenses to changing conditions and implement security measures tailored specifically to your network.
● Correlating specific events from network, endpoint, intrusion, and security intelligence sources. You are alerted if individual hosts show signs of compromise from unknown attacks.
● Applying file policy criteria. If those are met, it automatically analyzes the file to identify known malware and/or sends the file to an integrated sandbox to identify unknown malware.
Centralized Event and Policy Manager
The Firewall Management Center is the centralized event and policy manager for:
● Cisco Secure Firewall Threat Defense (FTD), both on-premises and virtual
● Cisco Secure IPS (formerly Firepower NGIPS)
● Cisco Firepower Threat Defense for ISR
● Cisco Malware Defense (formerly Advanced Malware Protection, or AMP)
The Firewall Management Center (FMC) discovers real-time information about changing network resources and operations. You get a full contextual basis for making informed decisions (Figure 1). In addition to providing a wide breadth of intelligence, FMC delivers a fine level of detail, including:
● Trends and high-level statistics. This information helps you understand your security posture at a given moment in time as well as how it’s changing, for better or worse.
● Event detail, compliance, and forensics. These provide an understanding of what happened during a security event. They help improve defenses, support breach containment efforts, and aid in legal enforcement actions.
● Workflow data. You can easily export this data to other solutions to improve incident response management.
● Real-time device health monitoring. Quickly see the status of your devices either from a consolidated, high-level view or via detailed, customizable status pages (Figure 2).
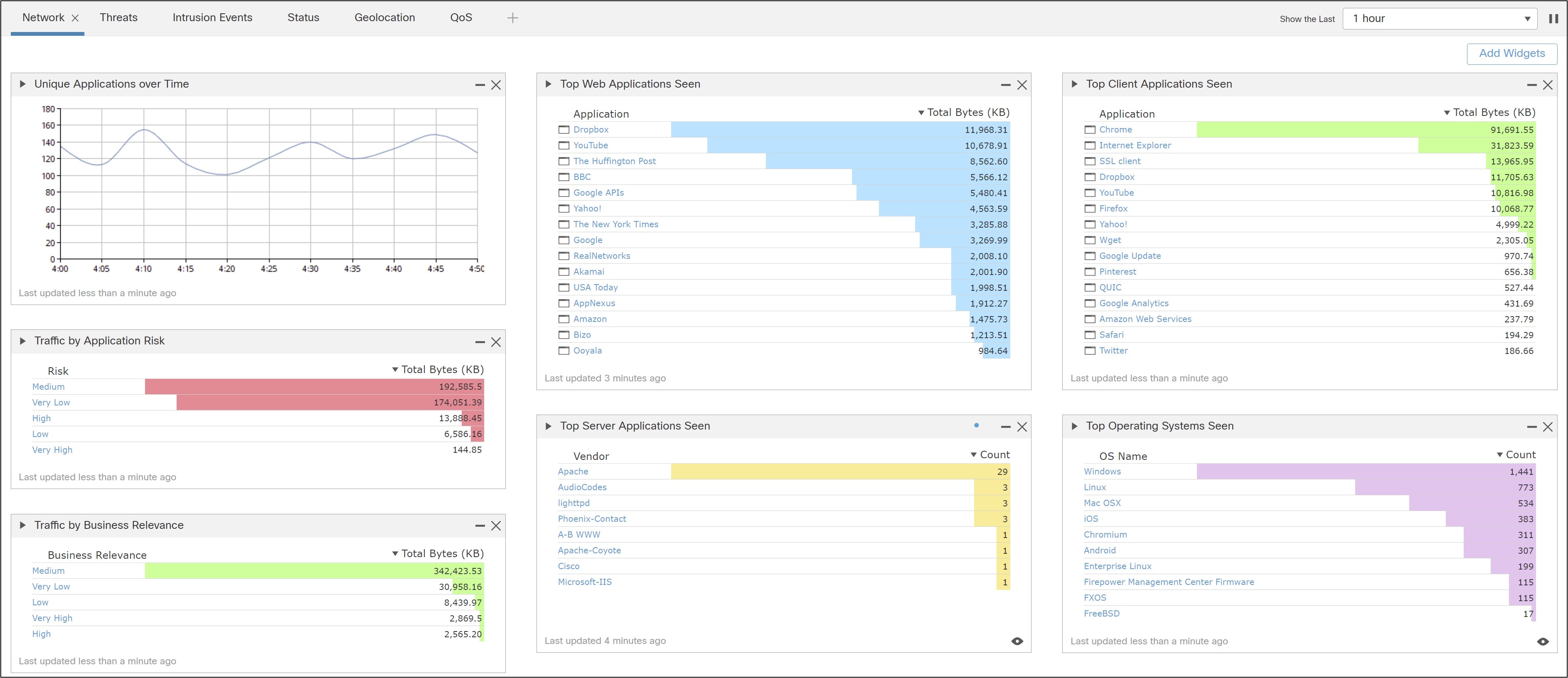
Contextual network and security information
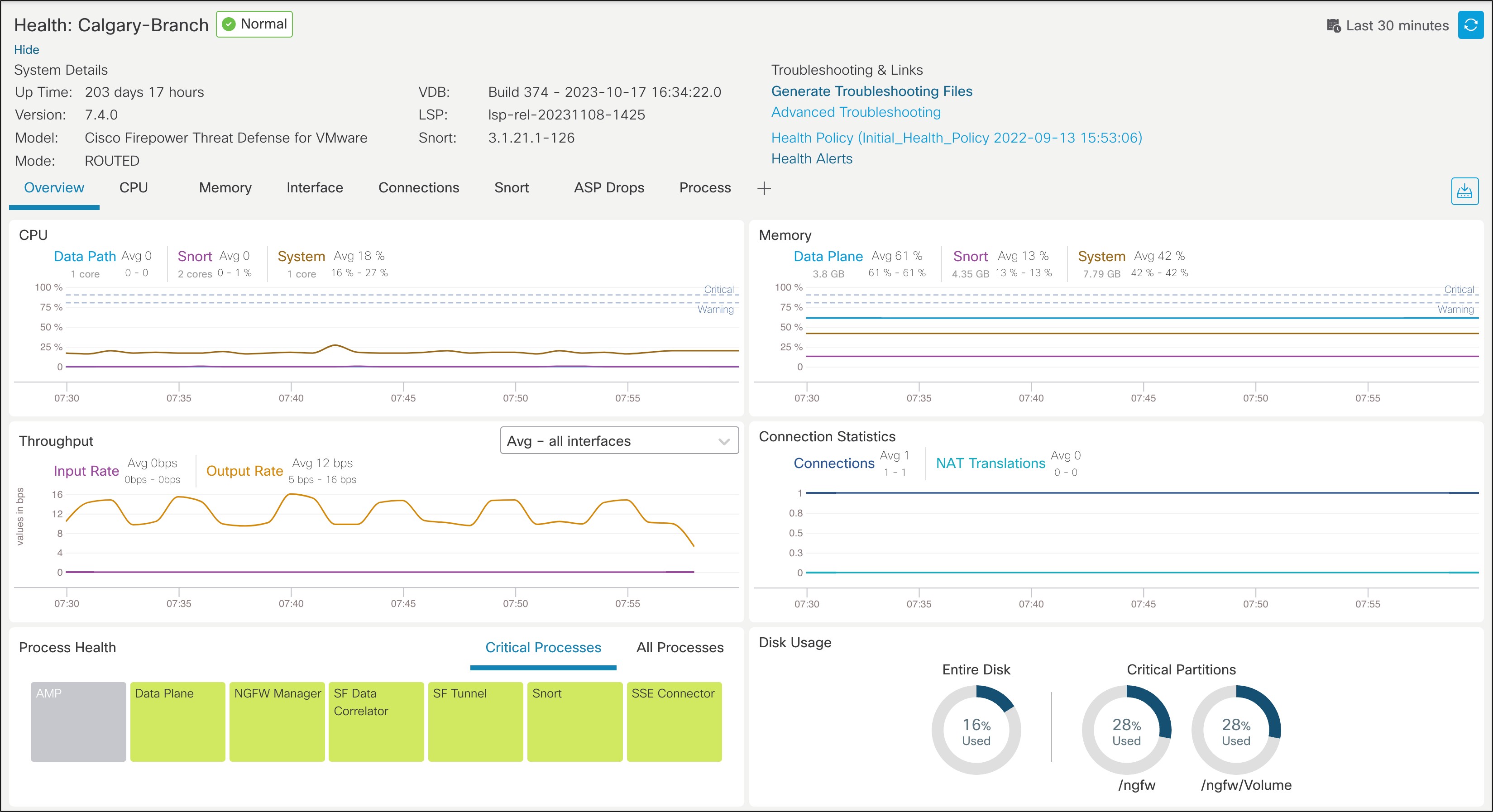
Real-time Device Health Monitor
Centralized Policy and Operations
● Maintain consistent policies: Write a policy once and scale enforcement consistently across multiple security controls throughout your network.
● Reduce complexity: Get unified management and automated threat correlation across tightly integrated security functions, including application firewalling, next-generation Intrusion Prevention, and file and malware protection.
● Accelerate key security operations functions: Increase efficiency by removing manual processes. Access security patches and new features faster by completing software upgrades in just a few clicks.
| Feature |
Benefit |
| Unified management of multiple security functions across multiple solutions |
Facilitates the centralized management of the Cisco security environment, including:
● Cisco Secure Firewall Threat Defense
● Cisco Secure IPS
● Cisco Firepower Threat Defense for ISR
● Cisco Malware Defense
|
| Integrated policy management over multiple security functions |
● Configures firewall access, application control, threat prevention, URL filtering, and advanced malware protection settings in a single policy
● Eases policy administration, reduces errors, and promotes consistency
● Enables a single policy to be deployed to multiple security solutions
|
| Network Discovery |
● Discovers users, applications, and a multitude of devices through passive analysis of network traffic
● Provides context and helps to determine the impact of attacks against your specific environment
● Allows you to tune Intrusion Prevention signature sets to the systems discovered on your network
● Supports third-party vulnerability management integration
|
| Separation of duties and role-based access control |
● Create administrative user personas such as NetOps or SecOps to clearly define responsibilities
● Granular role-based access control allows users to be given specific access rights to perform only the actions they are responsible for
|
| Integrated Azure AD Identity based access policy control with Cisco Identify Services Engine (ISE) |
● Newly supported Azure AD based User/Group based access control.
● Integrates with ISE for Azure AD based User Identity integration.
● Controls access based on Cisco ISE security group tag, device type and location IP, and rapid threat containment
● Helps enforce compliance, enhance infrastructure security, and streamline service operation
|
| Automatic Security Response |
● Correlate security events to identify stealthy attacks
● Trigger automated responses via:
◦ Syslog ◦ SNMP ◦ Remediation modules |
| Cisco Secure Dynamic Attribute Connector |
● CSDAC Natively running inside from FMC 7.4 onwards
● Provides an automated and programmatic way to manage policies when IP addresses and workloads are constantly changing without having to redeploy changes
● Dramatically reduces the admin overhead required to keep security policies up to date
● Integrates with AWS, Azure, GCP, VMware to source workload tags and to create Dynamic Objects for Policy
● Integrated with SaaS services like Office365, GitHub, Azure Service Tags, Zoom, WebEx for Dynamic Objects based Access enforcement
● Supports Generic text file driven IP Prefixes for open integration. They can contain for example "known IP List”, or "Vulnerable IP list” etc
|
| Threat intelligence |
● Integrates with Cisco Talos® Group’s security, threat, and vulnerability intelligence for up-to-minute threat protection
● Addresses new attack methods with both IP-based and URL-based security intelligence
● Enables ingestion and correlation of threat intelligence from third-party threat feeds and threat intelligence platforms in STIX/TAXII or flat file formats
|
| Application visibility and control |
● Further reduces threats to your network with precise control of thousands of commercial applications
● Uses the open-source standard Open App ID for detailed identification and control over custom applications
|
| Multitenancy management and policy inheritance |
● Creates up to 100 management domains with separate event data, reporting, and network mapping, enforced through role-based access control
● Implements consistent and efficient management through its policy hierarchy structure, with each level inheriting policies above it
|
| Cisco Security Analytics and Logging (SAL) integration |
● Highly scalable, intuitive single view of firewall log management
● Behavioral analysis provides real-time threat detection and faster response times
● Continuous analysis further refines your security posture to better defend against future attempts
|
| SecureX integration |
● Leverage the SecureX™ platform to accelerate threat detection, orchestration, and remediation
● Every Secure Firewall includes entitlement for Cisco SecureX
● The new SecureX ribbon in Firewall Management Center enables SecOps to instantly pivot to SecureX’s open platform, speeding incident response
|
| Cisco Secure Workload integration |
● Integration with Cisco Secure Workload (formerly Tetration) enables comprehensive visibility and policy enforcement for modern distributed and dynamic applications across the network and workload for consistent enforcement in a scalable manner
|
| Reporting and dashboards |
● Provides the visibility you need through customizable dashboards with custom and template-based reports
● Delivers comprehensive alerts and reports for both general and focused information
● Displays event and contextual information in hyperlinked tables, graphs, and charts for easy-to-use analysis
● Monitors network behavior and performance to identify anomalies and maintain system health
|
| Secure boot |
● Secure boot is a mechanism to validate the integrity of Cisco software running on the FMC hardware as your system boots
● If a signature is missing or software is invalid, it will not load and boot will fail
(Hardware FMC appliances only) |
Open APIs for easy integration
FMC makes integration with third-party technologies possible through powerful, feature-rich application programming interfaces. The APIs provide connection points for:
● Moving event data from FMC to another platform, such as a Security Information and Event Management (SIEM) solution.
● Enhancing the information contained in the Cisco IPS database with third-party data. Such data might include vulnerability management.
● Kicking off workflows and remediation steps that are activated by user-defined correlation rules. You could, for example, integrate your workflow with a Network Access Control (NAC) solution to quarantine an infected endpoint or initiate a digital forensic process.
● Supporting third-party reporting and analytics by enabling those solutions to query the FMC database.
These APIs are also used to integrate with several Cisco security products and workflows. These include Cisco Secure Malware Analytics (formerly Cisco AMP Threat Grid) for sandboxing; the Cisco Identity Services Engine (ISE) for identity data and network segmentation; and Cisco Umbrella® for internet-wide domain visibility.
The Cisco Secure Technology Alliance is a security ecosystem that facilitates open, multivendor product integrations to improve security effectiveness through automation and operational simplicity. Cisco is actively partnering with 100s of key security vendors and integration with over ten Cisco security products. To see the latest list, visit Cisco Secure Technical Alliance Partners.
Cisco SecureX connects the breadth of Cisco’s integrated security portfolio and your entire security infrastructure for a consistent experience that unifies visibility, enables automation, and strengthens your security across the network, endpoint, cloud, and applications. The result is simplified security, built into the solutions that you already have.
SecureX’s threat response feature (formerly CTR) integrates threat intelligence from Cisco Talos and third-party sources to automatically research Indicators of Compromise (IOCs), also known as observables, and confirm threats quickly.
For Secure Firewall customers, the SecureX ribbon in the Firewall Management Center (FMC) allows an administrator to instantly pivot back and forth for deeper threat investigation, sharing and maintaining context around incidents.

SecureX in the FMC
Find here the prebuilt workflow playbooks that address common use cases for observable actions, remediations, and incident endpoint enrichment.
Cisco firewalls send data to SecureX with a secure intermediary cloud service. SecureX threat response queries for sightings related to the IP address being investigated and provides an analyst with the additional context. Intrusion events are promoted to investigation-worthy incidents in the Incident Manager, based on Cisco Talos reputation or user-defined filters. This allows your team to quickly investigate and triage to see analytics on intrusion events.
SecureX Orchestrator can invoke FMC API calls, which allows administrators to automate routine FMC tasks, improving efficiency. SecureX is available as a standard for customers with Cisco Secure Firewall and/or any Cisco Secure product.
FMC can be deployed as a physical or virtual appliance, or from the cloud. It can also be consumed as a service. The cloud-delivered FMC, through CDO, has all the benefits of FMC without the need to manage FMC software update itself. You can choose which option works best for your environment. Please visit the current Release Notes for more detailed information.
Hypervisor compatibility and cloud support
Firewall Management Center Virtual supports the following hypervisor types shown below. All models of the FMC Virtual platform will operate with the same RAM requirements: 32 GB recommended**; 28 GB** required. For current versions supported and compatibility with FMC versions, visit current Release Notes.
Table 1. Virtual appliance hypervisor and cloud support
| Hypervisor |
Version and details |
| VMware vSphere |
● ESXi Server 5.1, 5.5, 6.0, 6.5, 6.7, 7.0
● vCenter Server (optional)
● vSphere Web Client, vSphere Client, or OVF Tool for Windows or LinuxC
|
| KVM |
● Ubuntu 18.04 LTS
● Red Hat Enterprise Linux (RHEL) Version 7.1
|
| Amazon Web Services |
● c3.4xlarge: 16 vCPUs, 30 GB
● c4.4xlarge: 16 vCPUs, 30 GB
● c5.4xlarge: 16 vCPUs, 32 GB
|
| Microsoft Azure |
Standard_D4_v2: 8 vCPUs, 28 GB |
| GCP |
c2-standard-8: 8 vCPUs, 32 GB c2-standard-16: 16 vCPU, 64 GB |
| OCI |
VM.Standard 2.4, 60 GB |
| Nutanix |
Nutanix AHV (20201105.12 and later) |
| Hyperflex |
Release 4.5(1a) 4-8 vCPUs, 28-32 GB for FMCv-2,10,25 32 vCPU, 64 GB for FMCv-300 |
Note: Refer to the Cisco Secure Firewall Management Center Virtual Getting Started Guide for more information.
There are several Firewall Management Center models. Choose based on the number of sensor appliances to be monitored (both physical and virtual), the number of hosts in your environment, and the anticipated security events rate (see Table 3). All models provide the same management capabilities.
Table 2 compares the capacities of available Cisco Firewall Management Center physical appliances.
Table 2. Cisco Secure Firewall Management Center hardware models
| Performance and functionality |
FMC 1700 |
FMC 2700 |
FMC 4700 |
| Maximum number of sensors managed |
50 |
300 |
1,000 |
| Maximum IPS events |
30 million |
60 million |
400 million |
| Two built-in 10GbE RJ45 OCP3.0 NIC; support for 100 Mbps, 1 Gbps, and 10 Gbps; the primary management port is eth0. You can use eth1, eth2, and eth3 as secondary management or event ports. |
|||
| USB ports |
Two USB 3.0 Type A |
||
| VGA ports |
One 3-row 15-pin DB-15 connector; enabled by default |
||
| SFP ports |
Two fixed SFP+ ports |
||
| Supported SFP+ |
SFP-10G-SR (10 GB) SFP-10G-LR (10 GB) |
SFP-10G-SR (10 GB) SFP-10G-LR (10 GB) |
SFP-10G-SR (10 GB) SFP-10G-LR (10 GB) SFP-25G-SR-S (25 GB) SFP-10/25G-LR-S (25GB) SFP-10/25G-CSR-S (25 GB) |
| Memory |
32 GB |
64 GB |
128 GB |
| RDIMMs (internal component only; not field replaceable) |
Two 16-GB DDR4-3200-MHz DIMMs |
Four16-GB DDR4-3200-MHz DIMMs |
Eight 16-GB DDR4-3200-MHz DIMMs |
| CPU |
AMD 1P Rome 7232P |
AMD 1P Rome 7282 |
AMD 1P Rome 7352 |
| Event storage space |
900 GB |
1.8 TB |
3.2 TB |
| Maximum network map size (hosts/users) |
50,000/ |
150,000/ |
600,000/ |
| Maximum event rate (events per second) |
5000 eps |
12,000 eps |
30,000 eps |
| Network interfaces |
2 x 1 Gbps RJ45 onboard 2 x 10 Gbps SFP+ (order SFPs via Cisco Commerce Workplace) |
2 x 1 Gbps RJ45 onboard 2 x 10 Gbps SFP+ (order SFPs via Cisco Commerce Workplace) |
2 x 1 Gbps RJ45 onboard 2 x 10/25 Gbps SFP+ (order SFPs via Cisco Commerce Workplace) |
| Secure boot |
Yes |
Yes |
Yes |
| Redundancy features |
|||
| Supports high availability |
Yes |
Yes |
Yes |
| System power |
Two 1050-W AC power supplies; hot swappable and redundant as 1+1 |
||
| Power consumption |
2626 BTU/hr |
||
| Storage |
Two 1.2-TB RAID-1, hot swappable |
Four 600-GB RAID 5, hot-swappable |
Ten 1.2-TB RAID-6, hot swappable |
| RAID controller |
One - the chassis has a dedicated internal riser for a PCIe-style Cisco modular RAID controller card. Internal component only; not field replaceable. |
||
| Physical and environmental |
|||
| Form factor |
1RU |
1RU |
1RU |
| Dimensions |
30 x 16.9 x 1.7 in (76.2 x 42.9 x 4.3 cm) |
||
| Shipping weight |
32.2 lb. (16.6 kg) |
34.1 lb. (16.8 kg) |
36 lb. (17.0 kg) |
| Watts (max) |
1,050W |
1,050W |
1,050W |
| Power supply |
100-240 VAC (nominal) 90-264 VAC (min/max 9.2-amp max at 100 VAC 5.2-amp max at 230 VAC |
100-240 VAC (nominal) 90-264 VAC (min/max 9.2-amp max at 100 VAC 5.2-amp max at 230 VAC |
100-240 VAC (nominal) 90-264 VAC (min/max 9.2-amp max at 100 VAC 5.2-amp max at 230 VAC |
| Airflow |
Front to back |
Front to back |
Front to back |
| Operating temperature |
50°F to 95°F (10°C to 35°C) |
||
Table 3 compares the capacities of available Cisco Secure Firewall Management Center virtual appliances.
Table 3. Cisco Firewall Management Center Virtual (FMCv) models
| Performance and functionality |
FMCv(2/10/25) |
FMCv300 |
| Maximum number of sensors managed |
2 10 25 |
300 |
| Maximum IPS events |
10 million |
60 million |
| Memory |
32 GB |
64 GB |
| CPU |
8/4 vCPUs |
32 vCPUs |
| Event storage space |
250 GB |
2.2 TB |
| Maximum network map size (hosts/users) |
50,000/50,000 |
150,000/150,000 |
| Maximum event rate (events per second) |
Varies |
12,000 eps |
| Hypervisor and cloud support |
VMware, KVM, AWS, Azure, GCP, OCI, Nutanix, Hyperflex, OpenStack |
VMware, AWS, OCI |
| Supports high availability |
VMware, AWS, OCI (Not supported on FMCv2) |
VMware, AWS, OCI |
Cloud-delivered FMC can be scaled for your needs. Please refer to our Release Notes for more detailed information on compatibility, supported versions, deployments, and browser requirements.
For ordering and licensing information on virtual and physical appliances as well as cloud-delivered service, please consult the Cisco Network Security Ordering Guide. To place an order, visit the Cisco Ordering Home Page, contact your Cisco sales representative, or call us at 1 800 553 6387.
Find warranty information at the Cisco.com Product Warranties page.
● Cisco Security Management Portfolio
● Cisco Secure Firewall Management Center Release Notes
● Cisco Security Analytics and Logging
● Network Security and Trust for Service Providers
● Cisco Firepower Management Center (Previous Models) Data Sheet