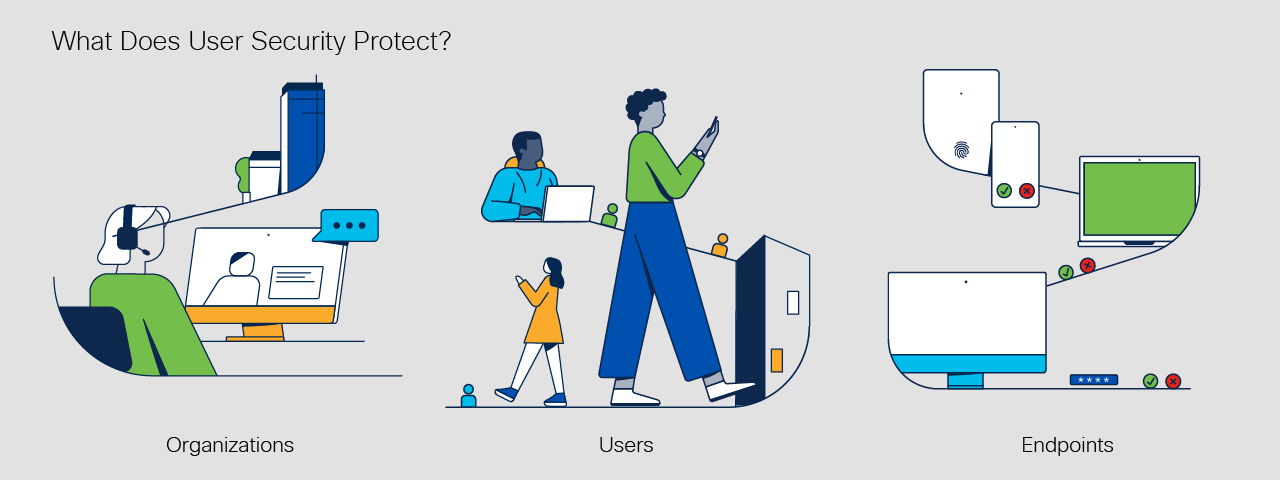
What is the importance of user security?
User security is important because it helps organizations, and their users, protect employee, customer, and corporate data from threats, financial loss, and identity theft. Strong end-user security hygiene can also support regulation compliance, prevent reputational damage, and preserve customer trust.