Encrypted Tunnel Deployment Guide
Available Languages
Contents
Introduction
This document introduces the 8.7 Mobility Encrypted Tunnel and provides general guidelines for its deployment. The purpose of this document is to:
Pre-requisite
You must have AireOS 8.0 or higher release on a Wireless LAN Controller in order to upgrade to the 8.5MR1 or 8.7 code.
Note
This feature is functional only in 8.5MR1 and 8.7 and above releases and is supported on 3504, 5520 and 8540 controllers.
Product or Feature Overview
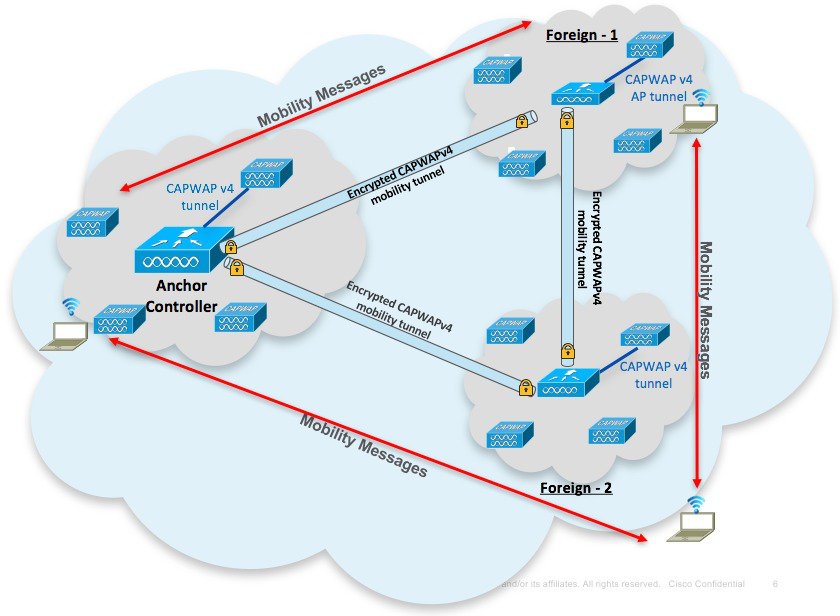
The scope of the document is to provide a high level system description of support for End-to-End encryption of Mobility tunnel between Anchor and Foreign WLC. The document also describes the basic assumptions from the WLC perspective to support End-to-End encryption of Mobility tunnel between Anchor and Foreign WLC.
The architecture for End-to-End encryption of Mobility tunnel between Anchor and Foreign WLC is shown in the diagram below. In this architecture the WLCs are connected through CAPWAP based mobility tunnels which use DTLS encryption between the WLCs. The client data passes through secure DTLS encrypted CAPWAP tunnel between AP to WLC and between the Foreign and Anchor WLCs it passes through the CAPWAP based mobility tunnels which use DTLS encryption. Thus, through the entire data path from the client network to the Anchor WLC the client data is passing through encrypted tunnel with no scope for Man in the Middle snooping.
Configuring Encrypted Mobility Tunnel
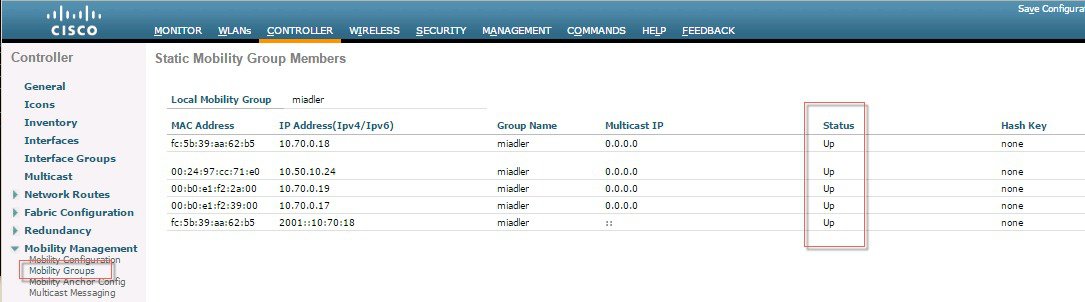
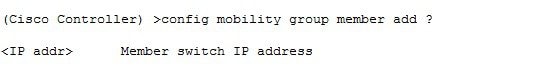
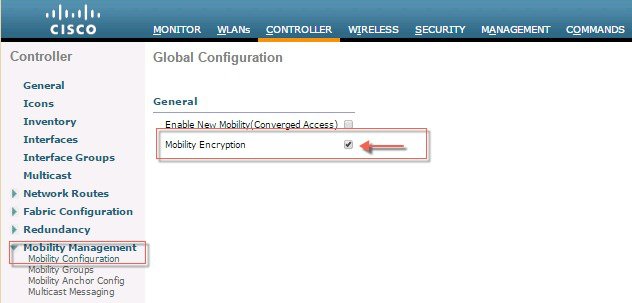
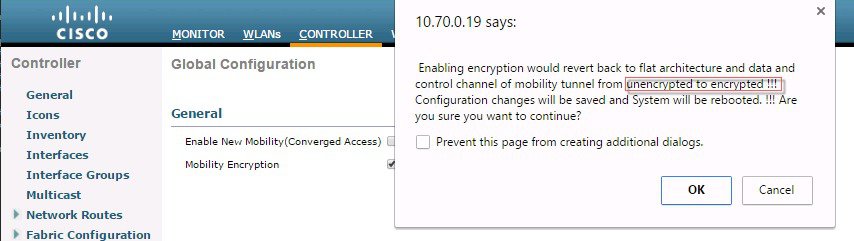
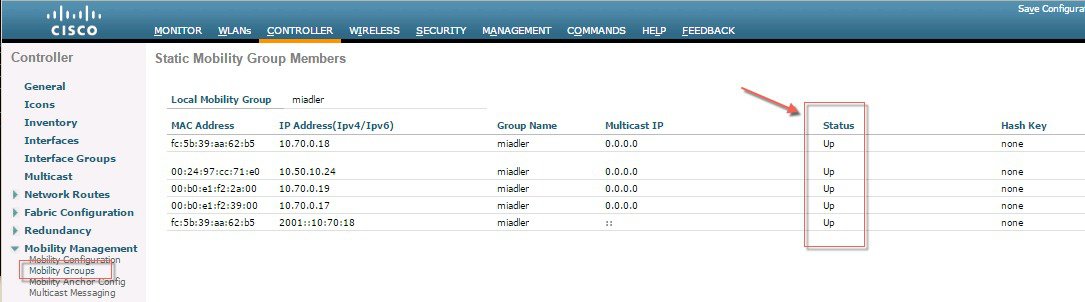
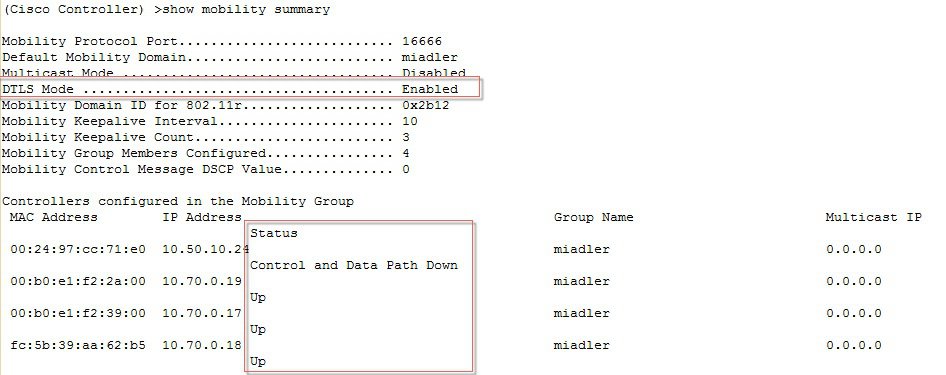
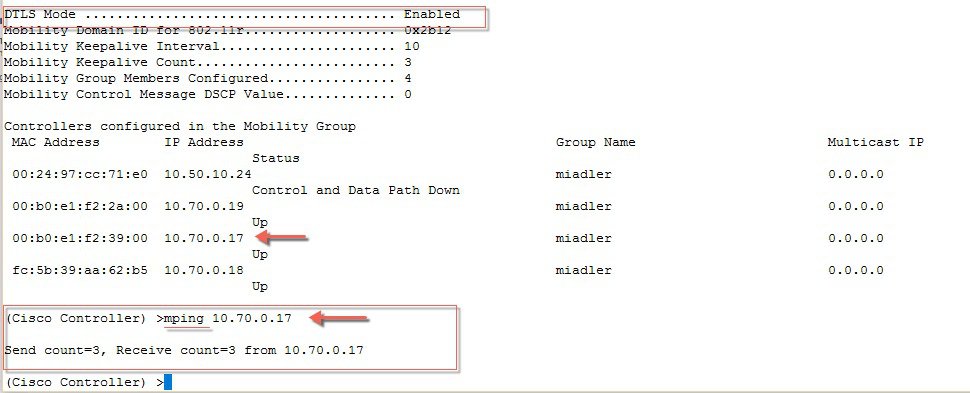
ProcedureTo configure End to End Encrypted Mobility Tunnel in the release 8.7 follow the steps as indicated below.
Copyright © 2018, Cisco Systems, Inc. All rights reserved.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)


 Feedback
Feedback