Quality of Service, Bandwidth Management and Security Configuration
Available Languages
Table Of Contents
Quality of Service, Bandwidth Management, and Security Configuration
Quality of Service (QoS) Configuration
Cisco 3745 Router Configuration
Cisco Catalyst 4506 Switch Configuration
Cisco 7206 Router Configuration
Bandwidth Management Using RSVP Agents
RSVP Configuration on Cisco Routers
Cisco Unified CallManager Configuration to Support RSVP
Firewall Security Configuration
Firewall Services Module (FWSM) Configuration
Quality of Service, Bandwidth Management, and Security Configuration
This chapter addresses IP network infrastructure topics, such as Quality of Service (QoS), bandwidth management of VoIP call traffic using Resource Reservation Protocol (RSVP) agent software, and firewalls to restrict access. It describes the deployed test environments used during Cisco Unified Communications Release 5.0(2) testing for IP telephony systems, but does not contain detailed installation and configuration instructions.
This chapter includes the following sections:
•
Quality of Service (QoS) Configuration
•
Bandwidth Management Using RSVP Agents
•
Firewall Security Configuration
Quality of Service (QoS) Configuration
This section provides sample configuration files that show how Quality of Service (QoS) settings were configured on selected switches and WAN routers during Cisco Unified Communications Release 5.0(2) testing for IP telephony. For the testing, QoS was configured on the following Cisco devices that passed VoIP traffic to and from SCCP, analog, and T1-PRI endpoints:
•
Cisco 1760 modular access router
•
Cisco 2651 and Cisco 2691 multiservice routers
•
Cisco 3640 multiservice router
•
Cisco 3725 and Cisco 3745 multiservice access routers
•
Cisco 7206 router
•
Cisco Catalyst 4506 switch
QoS was also configured on the following devices to test VoIP traffic to and from SIP, analog, and T1-PRI endpoints:
•
Cisco 3745 multiservice access router
•
Cisco 3845 router
•
Cisco Catalyst 4506 switch
•
Cisco 7206 router
•
Cisco Catalyst 3550 switch
These devices were configured for QoS based on the recommendations in the Enterprise QoS Solution Reference Network Design Guide http://www.cisco.com/univercd/cc/td/doc/solution/esm/qossrnd.pdf. This document provides design considerations and guidelines for implementing Cisco QoS within an enterprise environment on specific Cisco router and Cisco Catalyst switch types.
Most devices tested during Cisco Unified Communications Release 5.0(2) were configured with Cisco AutoQoS. For additional information about AutoQos, see the "Quality of Service Commands" chapter in the Cisco IOS Quality of Service Solutions Command Reference at http://www.cisco.com/en/US/products/ps6441/products_command_reference_book09186a0080497066.html.
For general information on QoS on Cisco devices, see http://www.cisco.com/en/US/tech/tk543/tk759/tsd_technology_support_protocol_home.html.
This section includes portions of the configuration files for the following devices:
•
Cisco 3745 Router Configuration
•
Cisco Catalyst 4506 Switch Configuration
•
Cisco 7206 Router Configuration
Cisco 3745 Router Configuration
This section shows a portion of the serial interface configuration for the Cisco 3745 router that was used in QoS testing. It demonstrates how to configure auto qos voip trust on the LAN-to-WAN edge using Cisco AutoQoS. For additional installation and configuration information, see the Cisco 3745 Multiservice Access Router documentation available at http://www.cisco.com/en/US/products/hw/routers/ps282/tsd_products_support_series_home.html.
class-map match-any AutoQoS-VoIP-RTP-Trustmatch ip dscp efclass-map match-any AutoQoS-VoIP-Control-Trustmatch ip dscp cs3match ip dscp af31!policy-map AutoQoS-Policy-Trustclass AutoQoS-VoIP-RTP-Trustpriority percent 70class AutoQoS-VoIP-Control-Trustbandwidth percent 5class class-defaultfair-queue!controller T1 0/0framing esflinecode b8zschannel-group 1 timeslots 1-24 speed 64!interface Serial0/0:1description WAN connection to SJC-RFD-WAN-1 port 2/0/4no ip addressencapsulation frame-relayno fair-queueframe-relay traffic-shaping!interface Serial0/0:1.1 point-to-pointip address 10.3.180.13 255.255.255.252frame-relay interface-dlci 104class AutoQoS-FR-Se0/0:1-104auto qos voip trust!map-class frame-relay AutoQoS-FR-Se0/0:1-104frame-relay cir 1536000frame-relay bc 15360frame-relay be 0frame-relay mincir 1536000service-policy output AutoQoS-Policy-Trustlogging trap debugginglogging facility local1logging 10.3.2.129!rmon event 33333 log trap AutoQoS description "AutoQoS SNMP traps for Voice Drops" owner AutoQoSCisco Catalyst 4506 Switch Configuration
This section shows a portion of the configuration file for a Cisco Catalyst 4506 switch that was used in QoS testing. It demonstrates how to configure global QoS and the ports which were linked to Cisco Unified IP Phones. For additional installation and configuration information, see the Cisco Catalyst 4500 series documentation available at http://www.cisco.com/en/US/products/hw/switches/ps4324/tsd_products_support_series_home.html.
qos dblqos map dscp 24 25 26 27 28 29 30 31 to tx-queue 4qos map dscp 32 33 34 35 36 37 38 39 to tx-queue 4qos map cos 3 to dscp 26qos map cos 5 to dscp 46qos!policy-map autoqos-voip-policyclass class-defaultdbl!interface FastEthernet4/25description 7960 to SFO-ORD-103-2621switchport access vlan 903switchport trunk encapsulation dot1qswitchport mode accessswitchport voice vlan 903load-interval 30qos trust device cisco-phonespanning-tree portfast trunkspanning-tree bpduguard enablespanning-tree guard root!interface FastEthernet4/26description description 7960 to SFO-ORD-103-2650switchport access vlan 903switchport mode accessswitchport voice vlan 903load-interval 30qos trust device cisco-phonetx-queue 3priority highshape percent 33spanning-tree portfast trunkspanning-tree bpduguard enablespanning-tree guard root!nterface FastEthernet4/28description 7970 to SFO-ORD-104-3745switchport access vlan 904switchport trunk encapsulation dot1qswitchport mode trunkswitchport voice vlan 904load-interval 30qos trust device cisco-phonespanning-tree portfast trunkspanning-tree bpduguard enablespanning-tree guard root!Cisco 7206 Router Configuration
This section shows a portion of the configuration file for a Cisco 7206 core router that was used in QoS testing. It demonstrates how to configure auto qos voip trust on the WAN-to-LAN edge using Cisco AutoQoS. For additional installation and configuration information, see the Cisco 7200 series router documentation available at http://www.cisco.com/en/US/products/hw/routers/ps341/tsd_products_support_series_home.html.
class-map match-any AutoQoS-VoIP-RTP-Trustmatch ip dscp efclass-map match-all going-pcmatch access-group 121class-map match-any AutoQoS-VoIP-Control-Trustmatch ip dscp cs3match ip dscp af31class-map match-all blamatch ip rtp 16384 16383!policy-map AutoQoS-Policy-Trustclass AutoQoS-VoIP-RTP-Trustpriority percent 70class AutoQoS-VoIP-Control-Trustbandwidth percent 5class class-defaultfair-queue!interface Serial5/4:1no ip addressencapsulation frame-relayno fair-queueno arp frame-relayframe-relay traffic-shapingframe-relay lmi-type ansiframe-relay intf-type dce!interface Serial5/4:1.1 point-to-pointip address 10.3.180.14 255.255.255.252no arp frame-relayframe-relay interface-dlci 104class AutoQoS-FR-Se5/4:1-104auto qos voip trust!interface Serial6/2:1no ip addressencapsulation frame-relayno fair-queueno arp frame-relayframe-relay traffic-shapingframe-relay lmi-type ansiframe-relay intf-type dce!interface Serial6/2:1.1 point-to-pointip address 10.3.180.10 255.255.255.252no arp frame-relayframe-relay interface-dlci 103class AutoQoS-FR-Se6/2:1-103auto qos voip trust!map-class frame-relay AutoQoS-FR-Se5/4:1-104frame-relay cir 1536000frame-relay bc 15360frame-relay be 0frame-relay mincir 1536000service-policy output AutoQoS-Policy-Trust!map-class frame-relay AutoQoS-FR-Se6/2:1-103frame-relay cir 1536000frame-relay bc 15360frame-relay be 0frame-relay mincir 1536000service-policy output AutoQoS-Policy-Trust!rmon event 33333 log trap AutoQoS description "AutoQoS SNMP traps for Voice Drops" owner AutoQoSBandwidth Management Using RSVP Agents
http://www.cisco.com/en/US/products/ps6441/products_feature_guide09186a0080615754.html#wp1008975
RSVP Configuration on Cisco Routers
Cisco Unified CallManager Configuration to Support RSVP
Firewall Security Configuration
-- Firewalls have been deployed in the SJC and DFW sites to protect network access to the datacenter devices. Object-groups and access-lists have been created and implemented based on the devices/IP's documented on the Columbus 1.0 Webpage, feedback from the team, and observations from the testing being performed on Thursday.
-- Object-groups are very key in simplifying changes to the firewalls as subnets and devices are added to the network. The majority of changes to the network that involve the currently defined types of devices can be changed as needed with only a modification to the object-group.
-- The full configurations are attached. The descriptive object-group names and the remarks within the ACLs should make it relatively easy to understand the intentions of most configuration items.
-- Commands to allow all traffic to/from a particular device:
object-group network BLINDLY-TRUSTED
network-object host <IP address>
-- Commands to allow all traffic through the FWSM or PIX
access-group ALLOW-ALL in interface inside
access-group ALLOW-ALL in interface outside
-- Commands to re-enable filtering traffic through the FWSM or PIX
access-group INSIDE-IN in interface inside
access-group OUTSIDE-IN in interface outside
-- SIP ports 5060-5062 for both udp and tcp are being allowed. If more SIP ports are added the 2 SIP-PORTS object groups will need to be updated.
-- We used the default policy maps. A fine tuning of the policy map may be necessary/useful.
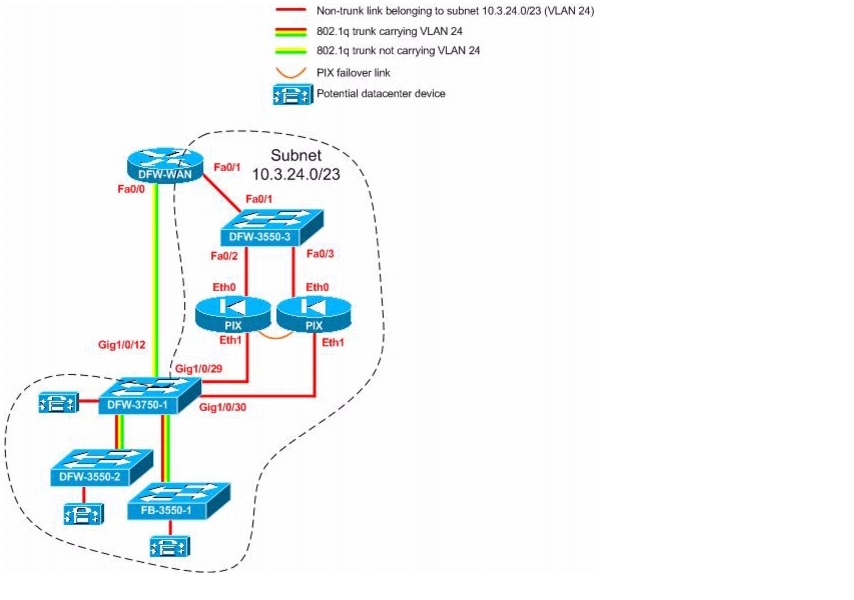
Secure PIX Firewall Setup
-- Two PIX 535's added in transparent mode with Active / Standby failover.
-- PIX is only protecting VLAN 24 (10.3.24.0/23) in the "Datacenter"
Figure 18-1 Secure PIX Firewall Tested Topology
PIX Version 7.0(101)150!firewall transparenthostname DFW-PIX-1enable password ****************** encryptednames!interface Ethernet0speed 100duplex fullnameif outsidesecurity-level 0!interface Ethernet1speed 100duplex fullnameif insidesecurity-level 100!passwd 2KFQnbNIdI.2KYOU encryptedboot system flash:/cdisk7.0.101.150ftp mode passiveobject-group service SIP-PORTS-TCP tcpport-object range sip 5062object-group service PHONE-VOICE-TCP tcpdescription *** TCP protocols used by phonesport-object eq 2000port-object eq 2443port-object eq ctiqbeport-object eq 8080group-object SIP-PORTS-TCPobject-group service SIP-PORTS-UDP udpport-object range sip 5062object-group service PHONE-VOICE-UDP udpdescription *** UDP protocols used by phonesport-object eq tftpport-object eq domaingroup-object SIP-PORTS-UDPobject-group service GW-VOICE-TCP tcpdescription *** TCP protocols used by voice gatewaysport-object eq 2428port-object eq h323object-group service GW-VOICE-UDP udpdescription *** UDP protocols used by voice gatewaysport-object eq 1719port-object eq 2427object-group service ALL-VOICE-TCP tcpgroup-object GW-VOICE-TCPgroup-object PHONE-VOICE-TCPobject-group service ALL-VOICE-UDP udpgroup-object GW-VOICE-UDPgroup-object PHONE-VOICE-UDPobject-group network MPnetwork-object host 10.3.24.16network-object host 10.3.24.17object-group network UNITYCnetwork-object host 10.3.24.8object-group network UNITYnetwork-object host 10.3.24.13network-object host 10.3.24.15object-group network EXCHGnetwork-object host 10.3.24.12network-object host 10.3.24.14object-group network IPNetfusionnetwork-object host 10.3.26.13network-object host 10.3.26.14object-group network KICKSTARTnetwork-object host 10.3.2.20object-group network BLINDLY-TRUSTEDgroup-object MPgroup-object UNITYCgroup-object UNITYgroup-object EXCHGgroup-object IPNetfusiongroup-object KICKSTARTobject-group network EVERYONEnetwork-object 10.0.0.0 255.0.0.0object-group network IP-PHONESnetwork-object 10.3.26.0 255.255.254.0network-object 10.3.181.0 255.255.255.0network-object 10.3.2.0 255.255.254.0network-object 10.9.207.128 255.255.255.192network-object 10.3.28.0 255.255.254.0network-object 10.3.30.0 255.255.254.0network-object 10.3.53.0 255.255.255.0network-object host 10.3.90.7object-group network DFW-CCMnetwork-object host 10.3.24.2network-object host 10.3.24.3network-object host 10.3.24.4network-object host 10.3.24.5network-object host 10.3.24.6network-object host 10.3.24.7object-group network MOH-SRVRnetwork-object host 10.3.24.7object-group network SJC-CCMnetwork-object host 10.9.10.4network-object host 10.9.14.4network-object host 10.9.10.5network-object host 10.9.14.5network-object host 10.9.10.6network-object host 10.9.14.6network-object host 10.9.10.7object-group network RFD-CCMnetwork-object host 10.9.20.2network-object host 10.9.20.3network-object host 10.9.20.4network-object host 10.9.20.5network-object host 10.9.20.6network-object host 10.9.20.7object-group network SFO-CCMnetwork-object host 10.9.30.3network-object host 10.9.30.4network-object host 10.9.30.5network-object host 10.9.30.6network-object host 10.9.30.7network-object host 10.9.30.8network-object host 10.9.30.9object-group network ORD-CCMnetwork-object host 10.9.40.3network-object host 10.9.40.4network-object host 10.9.40.5network-object host 10.9.40.6network-object host 10.9.40.7network-object host 10.9.40.8network-object host 10.9.40.9object-group network NYC-CCMnetwork-object host 10.3.60.2network-object host 10.3.60.3object-group network RDU-CCMnetwork-object host 10.3.90.5network-object host 10.3.90.6object-group network ATL-CMEnetwork-object host 10.3.80.2network-object host 10.3.81.2network-object host 10.3.181.190network-object host 10.3.83.2network-object host 10.3.84.2network-object host 10.3.82.2object-group network YYZ-CMEnetwork-object host 10.3.181.194network-object host 10.3.71.2network-object host 10.3.74.2network-object host 10.3.75.2object-group service RTP udpport-object range 16384 32768object-group network H323-GWSnetwork-object host 10.3.24.9network-object host 10.9.12.12network-object host 10.9.22.20network-object 10.3.2.0 255.255.254.0object-group network MGCP-GWSnetwork-object host 10.3.26.100network-object host 10.3.26.102network-object 10.3.2.0 255.255.254.0object-group network VOICE-GWSgroup-object H323-GWSgroup-object MGCP-GWSobject-group network DNS-SRVRnetwork-object host 10.3.26.2network-object host 10.3.2.121object-group network DHCP-SRVRnetwork-object host 10.3.26.2object-group network NETMGMT-SRVRnetwork-object host 10.9.12.21network-object host 10.9.22.34object-group network NTP-SRVRnetwork-object host 10.3.24.1network-object host 10.3.2.100object-group service ICC-TCP tcpdescription *** Inter-cluster communicationport-object eq h323group-object SIP-PORTS-TCPobject-group network ADMIN-ACCESSnetwork-object 10.3.2.0 255.255.254.0network-object 10.21.0.0 255.255.0.0network-object 10.25.0.0 255.255.0.0network-object 10.32.0.0 255.255.0.0network-object 10.77.0.0 255.255.0.0network-object 10.82.0.0 255.255.0.0network-object 10.89.0.0 255.255.0.0network-object 10.94.0.0 255.255.0.0network-object 64.0.0.0 255.0.0.0network-object 128.107.0.0 255.255.0.0network-object 171.0.0.0 255.0.0.0network-object 172.0.0.0 255.0.0.0network-object 192.0.0.0 255.0.0.0network-object 198.0.0.0 255.0.0.0object-group service ADMIN-PORTS-TCP tcpport-object eq wwwport-object eq httpsport-object eq 8080port-object eq 8443port-object eq telnetport-object eq sshport-object eq ftpport-object eq 445port-object eq 3389port-object eq 5900port-object eq ftp-dataobject-group service ADMIN-PORTS-UDP udpport-object eq tftpport-object eq 20object-group service ICC-UDP udpdescription *** Inter-cluster communicationgroup-object SIP-PORTS-UDPobject-group network GKS-OUTnetwork-object host 10.9.12.99network-object host 10.3.62.99network-object host 10.9.22.99network-object host 10.3.70.99object-group service GK-TCP-UDP tcp-udpdescription *** Communications to GKport-object eq 1718port-object eq 1719port-object eq 1720object-group service SRST-UDP udpport-object eq sipobject-group service SRST-TCP tcpport-object eq sipobject-group network SRSTnetwork-object host 10.3.181.201network-object host 10.3.181.205object-group network SIP-PROXYnetwork-object host 10.3.51.2access-list ALLOW-ALL extended permit ip any anyaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** OSPFaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit ospf any anyaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** All ICMP trafficaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit icmp any anyaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** NTP -- Not sure if both ports are 'ntp'access-list INSIDE-IN remark *** Also we may not need one direction if there is a fixup.access-list INSIDE-IN remark ***access-list INSIDE-IN extended permit udp object-group NTP-SRVR eq ntp any eq ntpaccess-list INSIDE-IN extended permit udp any eq ntp object-group NTP-SRVR eq ntpaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** DHCP and DNSaccess-list INSIDE-IN remark *** DHCP setting assumes no hosts directly connected to FWaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit udp object-group EVERYONE eq bootpc object-group DHCP-SRVR eq bootpsaccess-list INSIDE-IN extended permit udp object-group EVERYONE object-group DNS-SRVR eq domainaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** Network Mgmtaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit udp object-group NETMGMT-SRVR eq snmp object-group EVERYONE eq snmpaccess-list INSIDE-IN extended permit udp object-group EVERYONE eq snmptrap object-group NETMGMT-SRVR eq snmptrapaccess-list INSIDE-IN extended permit tcp object-group NETMGMT-SRVR object-group EVERYONE eq sshaccess-list INSIDE-IN extended permit udp object-group EVERYONE object-group NETMGMT-SRVR eq tftpaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** Traffic between CCM clustersaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group SJC-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group RFD-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group SFO-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group ORD-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group NYC-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group RDU-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group ATL-CME object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group YYZ-CME object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group SIP-PROXY object-group ICC-TCPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group SJC-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group RFD-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group SFO-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group ORD-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group NYC-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group RDU-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group ATL-CME object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group YYZ-CME object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group SIP-PROXY object-group ICC-UDPaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** ... between CCMs and GKsaccess-list INSIDE-IN remark *** (We could make the ports more granular.)access-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group GKS-OUT object-group GK-TCP-UDPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group GKS-OUT object-group GK-TCP-UDPaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** CCMs to SIP Proxied phonesaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group IP-PHONES object-group SIP-PORTS-TCPaccess-list INSIDE-IN extended permit udp object-group DFW-CCM object-group IP-PHONES object-group SIP-PORTS-UDPaccess-list INSIDE-IN remark ***********************************************access-list INSIDE-IN remark *** Workarounds; outside of Security Policy ***access-list INSIDE-IN remark ***********************************************access-list INSIDE-IN remark ***access-list INSIDE-IN remark *** CSCsc11305 ICT & GKaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group SJC-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group RFD-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group SFO-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group ORD-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group NYC-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group RDU-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group ATL-CME range 32768 65535access-list INSIDE-IN extended permit tcp object-group DFW-CCM object-group YYZ-CME range 32768 65535access-list INSIDE-IN remark ***access-list INSIDE-IN remark *** CSCsc55543 MOH & SIPaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit udp object-group MOH-SRVR object-group RTP object-group EVERYONE object-group RTPaccess-list INSIDE-IN remark ***************************************************access-list INSIDE-IN remark *** For convenience; outside of Security Policy ***access-list INSIDE-IN remark ***************************************************access-list INSIDE-IN remark *** Allow everything from blindly trusted sources until port use is determinedaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit ip object-group BLINDLY-TRUSTED anyaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** Allow Telnet Everywhereaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp any any eq telnetaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** Allow Admin accessaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp any object-group ADMIN-ACCESS object-group ADMIN-PORTS-TCPaccess-list INSIDE-IN extended permit udp any object-group ADMIN-ACCESS object-group ADMIN-PORTS-UDPaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** Nothing else shall pass hereaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended deny ip any anyaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** OSPFaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit ospf any anyaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** All ICMP trafficaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit icmp any anyaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** NTP -- Not sure if both ports are 'ntp'access-list OUTSIDE-IN remark *** Also we may not need one direction if there is a fixup.access-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit udp object-group NTP-SRVR eq ntp any eq ntpaccess-list OUTSIDE-IN extended permit udp any eq ntp object-group NTP-SRVR eq ntpaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** Network mgmtaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit udp object-group NETMGMT-SRVR eq snmp object-group EVERYONE eq snmpaccess-list OUTSIDE-IN extended permit udp object-group EVERYONE eq snmptrap object-group NETMGMT-SRVR eq snmptrapaccess-list OUTSIDE-IN extended permit tcp object-group NETMGMT-SRVR object-group EVERYONE eq sshaccess-list OUTSIDE-IN extended permit udp object-group EVERYONE object-group NETMGMT-SRVR eq tftpaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** Voice protocols from phones to CCMaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group IP-PHONES object-group DFW-CCM object-group PHONE-VOICE-TCPaccess-list OUTSIDE-IN extended permit udp object-group IP-PHONES object-group DFW-CCM object-group PHONE-VOICE-UDPaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** Voice protocols from gateways to other gateways and CCMaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group VOICE-GWS object-group DFW-CCM object-group GW-VOICE-TCPaccess-list OUTSIDE-IN extended permit udp object-group VOICE-GWS object-group DFW-CCM object-group GW-VOICE-UDPaccess-list OUTSIDE-IN extended permit tcp object-group VOICE-GWS object-group VOICE-GWS object-group GW-VOICE-TCPaccess-list OUTSIDE-IN extended permit udp object-group VOICE-GWS object-group VOICE-GWS object-group GW-VOICE-UDPaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** ICT communicationaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group SJC-CCM object-group DFW-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group RFD-CCM object-group DFW-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group SFO-CCM object-group DFW-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group ORD-CCM object-group DFW-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group NYC-CCM object-group DFW-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group RDU-CCM object-group DFW-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group ATL-CME object-group DFW-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group YYZ-CME object-group DFW-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group SIP-PROXY object-group DFW-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit udp object-group SJC-CCM object-group DFW-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group RFD-CCM object-group DFW-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group SFO-CCM object-group DFW-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group ORD-CCM object-group DFW-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group NYC-CCM object-group DFW-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group RDU-CCM object-group DFW-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group ATL-CME object-group DFW-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group YYZ-CME object-group DFW-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group SIP-PROXY object-group DFW-CCM object-group ICC-UDPaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** SRST servers to CCMaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group SRST object-group DFW-CCM object-group SRST-TCPaccess-list OUTSIDE-IN extended permit udp object-group SRST object-group DFW-CCM object-group SRST-UDPaccess-list OUTSIDE-IN remark ***********************************************access-list OUTSIDE-IN remark *** Workarounds; outside of Security Policy ***access-list OUTSIDE-IN remark ***********************************************access-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** CSCsc11305 ICT & GKaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group SJC-CCM object-group DFW-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group RFD-CCM object-group DFW-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group SFO-CCM object-group DFW-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group ORD-CCM object-group DFW-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group NYC-CCM object-group DFW-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group RDU-CCM object-group DFW-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group ATL-CME object-group DFW-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group YYZ-CME object-group DFW-CCM range 32768 65535access-list OUTSIDE-IN remark ***************************************************access-list OUTSIDE-IN remark *** For convenience; outside of Security Policy ***access-list OUTSIDE-IN remark ***************************************************access-list OUTSIDE-IN remark *** Allow everything from blindly trusted sources until port use is determinedaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit ip any object-group BLINDLY-TRUSTEDaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** Allow Telnet Everywhereaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp any any eq telnetaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** Allow Admin accessaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group ADMIN-ACCESS any object-group ADMIN-PORTS-TCPaccess-list OUTSIDE-IN extended permit udp object-group ADMIN-ACCESS any object-group ADMIN-PORTS-UDPaccess-list OUTSIDE-IN remark *** Nothing else shall pass hereaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended deny ip any anypager lines 24logging enablelogging timestamplogging buffer-size 40000logging buffered debugginglogging trap debugginglogging host outside 10.3.2.129mtu outside 1500mtu inside 1500ip address 10.3.24.18 255.255.254.0 standby 10.3.24.19failoverfailover polltime unit 1 holdtime 3no asdm history enablearp timeout 14400access-group OUTSIDE-IN in interface outsideaccess-group INSIDE-IN in interface insideroute outside 0.0.0.0 0.0.0.0 10.3.24.1 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00timeout mgcp-pat 0:05:00 sip 0:30:00 sip_media 0:02:00timeout uauth 0:05:00 absoluteno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstarttelnet timeout 5ssh timeout 5console timeout 0!class-map inspection_defaultmatch default-inspection-traffic!policy-map asa_global_fw_policyclass inspection_defaultinspect dns maximum-length 512inspect ftpinspect h323 h225inspect h323 rasinspect rshinspect rtspinspect esmtpinspect sqlnetinspect skinnyinspect sunrpcinspect xdmcpinspect sipinspect netbiosinspect tftp!service-policy asa_global_fw_policy globalntp server 10.3.26.1: endFirewall Services Module (FWSM) Configuration
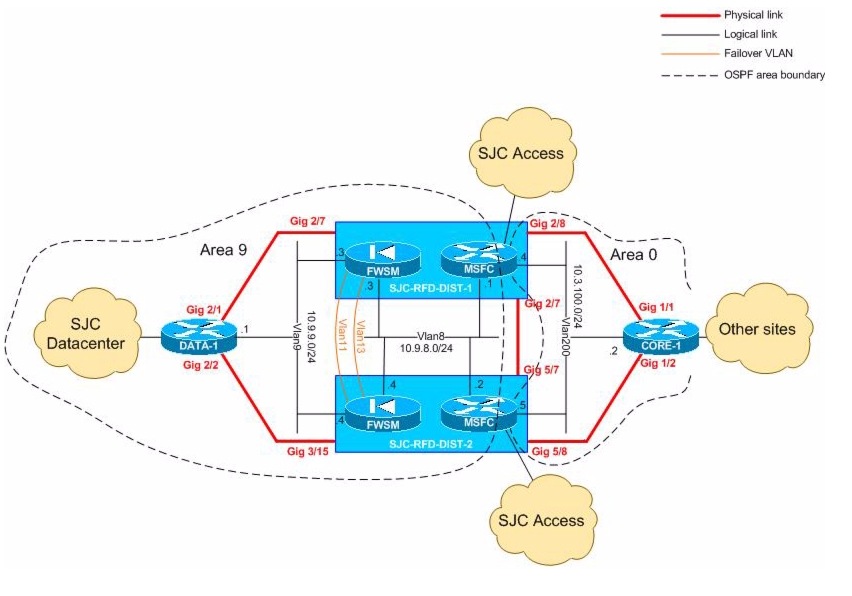
-- Two FWSM's added in routed mode with Active/Standby failover
-- FWSM is protecting VLANs 10, 12, 14, 16 in the "Datacenter"
Figure 18-2 Firewall Service Module (FWSM) Tested Topology
SJC-RFD-FWSM-1(config)# sh run: Saved:FWSM Version 3.1(0)118!hostname SJC-RFD-FWSM-1enable password ******************* encryptednames!interface Vlan8nameif outsidesecurity-level 0ip address 10.9.8.3 255.255.255.0 standby 10.9.8.4!interface Vlan9nameif insidesecurity-level 100ip address 10.9.9.3 255.255.255.0 standby 10.9.9.4!interface Vlan11description LAN Failover Interface!interface Vlan13description STATE Failover Interface!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passiveobject-group service SIP-PORTS-TCP tcpport-object range sip 5062object-group service ICC-TCP tcpdescription *** Inter-cluster communicationport-object eq h323group-object SIP-PORTS-TCPobject-group service SIP-PORTS-UDP udpport-object range sip 5062object-group service ICC-UDP udpdescription *** Inter-cluster communicationgroup-object SIP-PORTS-UDPobject-group service GK-TCP-UDP tcp-udpdescription *** Communications to GKport-object eq 1718port-object eq 1719port-object eq 1720object-group service PHONE-VOICE-TCP tcpdescription *** TCP protocols used by phonesport-object eq 2000port-object eq 2443port-object eq ctiqbeport-object eq 8080group-object SIP-PORTS-TCPobject-group service PHONE-VOICE-UDP udpdescription *** UDP protocols used by phonesport-object eq tftpport-object eq domaingroup-object SIP-PORTS-UDPobject-group service H323-GW-TCP tcpport-object eq h323port-object eq 2000object-group service MGCP-GW-TCP tcpport-object eq 2428port-object eq 2000object-group service SRST-TCP tcpgroup-object H323-GW-TCPgroup-object MGCP-GW-TCPport-object eq sipobject-group service H323-GW-UDP udpport-object eq 1719object-group service MGCP-GW-UDP udpport-object eq 2427port-object eq tftpobject-group service SRST-UDP udpgroup-object H323-GW-UDPgroup-object MGCP-GW-UDPport-object eq sipobject-group service RTP udpport-object range 16384 32768object-group network MPnetwork-object host 10.9.16.11network-object host 10.9.16.7network-object host 10.9.16.8network-object host 10.9.16.9network-object host 10.9.16.10network-object host 10.9.12.12object-group network CERnetwork-object host 10.9.14.12object-group network UNITYnetwork-object host 10.9.10.12network-object host 10.9.10.13network-object host 10.9.14.13object-group network EXCHGnetwork-object host 10.9.10.8network-object host 10.9.10.9network-object host 10.9.10.10network-object host 10.9.10.11network-object host 10.9.14.8network-object host 10.9.14.9network-object host 10.9.14.10network-object host 10.9.14.11object-group network FAXnetwork-object host 10.9.14.7network-object host 10.9.14.16object-group network PRESnetwork-object host 10.9.12.7object-group network DCSnetwork-object host 10.9.12.5network-object host 10.9.12.6object-group network BLINDLY-TRUSTEDgroup-object MPgroup-object CERgroup-object UNITYgroup-object EXCHGgroup-object FAXgroup-object PRESgroup-object DCSobject-group network EVERYONEnetwork-object 10.0.0.0 255.0.0.0object-group network MOH-SRVRnetwork-object host 10.9.10.7object-group network NTP-SRVRnetwork-object 10.9.8.0 255.255.255.0object-group network NETMGMT-SRVRnetwork-object host 10.9.12.21network-object host 10.9.22.34network-object host 172.18.143.115object-group network DNS-SRVR-OUTnetwork-object host 10.9.20.11object-group network DNS-SRVR-INnetwork-object host 10.9.12.4network-object host 10.9.12.5network-object host 10.9.12.6object-group network DHCP-SRVR-INnetwork-object host 10.9.12.4object-group network GKS-OUTnetwork-object host 10.9.22.99network-object host 10.3.62.99network-object host 10.3.70.99object-group network GKS-INnetwork-object host 10.9.12.99object-group network MGCP-GWS-OUTnetwork-object 10.9.128.32 255.255.255.240network-object 10.9.128.48 255.255.255.240network-object 10.9.128.64 255.255.255.224network-object 10.9.128.96 255.255.255.224network-object 10.9.128.128 255.255.255.240network-object 10.9.129.0 255.255.255.240network-object 10.9.129.16 255.255.255.240network-object 10.9.129.32 255.255.255.240network-object 10.9.129.48 255.255.255.240network-object 10.9.129.64 255.255.255.224network-object 10.9.129.96 255.255.255.224network-object 10.9.130.0 255.255.255.240network-object 10.9.130.16 255.255.255.240network-object 10.9.130.32 255.255.255.240network-object 10.9.130.64 255.255.255.240network-object 10.9.130.96 255.255.255.224network-object 10.9.207.0 255.255.255.240network-object 10.9.207.16 255.255.255.240network-object 10.9.207.32 255.255.255.240network-object 10.9.207.48 255.255.255.240network-object 10.9.207.96 255.255.255.224network-object 10.9.208.0 255.255.255.240network-object 10.9.208.16 255.255.255.240network-object 10.9.208.32 255.255.255.240network-object 10.9.208.48 255.255.255.240network-object 10.9.208.96 255.255.255.224network-object 10.9.209.0 255.255.255.240network-object 10.9.208.64 255.255.255.240network-object 10.9.209.16 255.255.255.240network-object 10.9.209.32 255.255.255.240network-object 10.9.209.48 255.255.255.240network-object 10.9.209.64 255.255.255.240network-object 10.9.130.48 255.255.255.240network-object host 10.9.22.2network-object host 10.9.227.250network-object host 10.9.241.248object-group network H323-GWS-OUTnetwork-object host 10.3.28.2network-object host 10.9.128.139network-object host 10.9.128.140network-object host 10.9.207.20network-object host 10.9.207.98network-object host 10.9.208.98network-object host 10.9.22.26network-object host 10.9.40.11network-object 10.9.128.128 255.255.255.240object-group network H323-GWS-INnetwork-object host 10.9.14.14object-group network DFW-CCMnetwork-object host 10.3.24.2network-object host 10.3.24.3network-object host 10.3.24.4network-object host 10.3.24.5network-object host 10.3.24.6network-object host 10.3.24.7object-group network SJC-CCMnetwork-object host 10.9.10.4network-object host 10.9.14.4network-object host 10.9.10.5network-object host 10.9.14.5network-object host 10.9.10.6network-object host 10.9.14.6network-object host 10.9.10.7object-group network RFD-CCMnetwork-object host 10.9.20.2network-object host 10.9.20.3network-object host 10.9.20.4network-object host 10.9.20.5network-object host 10.9.20.6network-object host 10.9.20.7object-group network SFO-CCMnetwork-object host 10.9.30.3network-object host 10.9.30.4network-object host 10.9.30.5network-object host 10.9.30.6network-object host 10.9.30.7network-object host 10.9.30.8network-object host 10.9.30.9object-group network ORD-CCMnetwork-object host 10.9.40.3network-object host 10.9.40.4network-object host 10.9.40.5network-object host 10.9.40.6network-object host 10.9.40.7network-object host 10.9.40.8network-object host 10.9.40.9object-group network NYC-CCMnetwork-object host 10.3.60.2network-object host 10.3.60.3object-group network RDU-CCMnetwork-object host 10.3.90.5network-object host 10.3.90.6object-group network ATL-CMEnetwork-object host 10.3.80.2network-object host 10.3.81.2network-object host 10.3.181.190network-object host 10.3.83.2network-object host 10.3.84.2network-object host 10.3.82.2object-group network YYZ-CMEnetwork-object host 10.3.181.194network-object host 10.3.71.2network-object host 10.3.74.2network-object host 10.3.75.2object-group network SRSTnetwork-object host 10.9.28.2network-object host 10.9.38.1object-group network IP-PHONESnetwork-object 10.9.82.0 255.255.254.0network-object 10.9.84.0 255.255.254.0network-object 10.9.86.0 255.255.254.0network-object 10.9.88.0 255.255.254.0network-object 10.9.90.0 255.255.254.0network-object 10.9.92.0 255.255.254.0network-object 10.9.94.0 255.255.254.0network-object 10.9.98.0 255.255.254.0network-object 10.9.100.0 255.255.254.0network-object 10.9.102.0 255.255.254.0network-object 10.9.104.0 255.255.254.0network-object 10.9.106.0 255.255.254.0network-object 10.9.108.0 255.255.254.0network-object 10.9.112.0 255.255.254.0network-object 10.9.114.0 255.255.254.0network-object 10.9.116.0 255.255.254.0network-object 10.9.118.0 255.255.254.0network-object 10.9.120.0 255.255.254.0network-object 10.9.122.0 255.255.254.0network-object 10.9.124.0 255.255.254.0network-object 10.9.210.0 255.255.254.0network-object 10.9.212.0 255.255.254.0network-object 10.9.214.0 255.255.254.0network-object 10.9.216.0 255.255.254.0network-object 10.9.218.0 255.255.254.0network-object 10.9.220.0 255.255.254.0network-object 10.9.222.0 255.255.254.0network-object 10.9.226.0 255.255.254.0network-object 10.9.228.0 255.255.254.0network-object 10.9.230.0 255.255.254.0network-object 10.9.232.0 255.255.254.0network-object 10.9.234.0 255.255.254.0network-object 10.9.236.0 255.255.254.0network-object 10.9.240.0 255.255.254.0network-object 10.9.242.0 255.255.254.0network-object 10.9.244.0 255.255.254.0network-object 10.9.246.0 255.255.254.0network-object 10.9.248.0 255.255.254.0network-object 10.9.250.0 255.255.254.0network-object 10.9.252.0 255.255.254.0network-object 10.9.28.0 255.255.255.0network-object 10.9.38.0 255.255.255.0network-object 10.9.142.0 255.255.255.0network-object 10.9.96.0 255.255.254.0object-group network SIP-PROXYnetwork-object host 10.3.51.2access-list mode auto-commitaccess-list ALLOW-ALL extended permit ip any anyaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** All ICMP trafficaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit icmp object-group EVERYONE object-group EVERYONEaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** NTP -- Not sure if both ports are 'ntp'access-list INSIDE-IN remark ***access-list INSIDE-IN extended permit udp object-group EVERYONE eq ntp object-group NTP-SRVR eq ntpaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** DHCP and DNSaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit udp object-group EVERYONE object-group DNS-SRVR-OUT eq domainaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** Network Mgmtaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit udp object-group NETMGMT-SRVR eq snmp object-group EVERYONE eq snmpaccess-list INSIDE-IN extended permit udp object-group EVERYONE eq snmptrap object-group NETMGMT-SRVR eq snmptrapaccess-list INSIDE-IN extended permit tcp object-group NETMGMT-SRVR object-group EVERYONE eq sshaccess-list INSIDE-IN extended permit udp object-group EVERYONE object-group NETMGMT-SRVR eq tftpaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** Traffic between CCM clustersaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group DFW-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group SFO-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group ORD-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group NYC-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group RDU-CCM object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group ATL-CME object-group ICC-TCPaccess-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group YYZ-CME object-group ICC-TCPaccess-list INSIDE-IN extended permit udp object-group SJC-CCM object-group DFW-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group SJC-CCM object-group SFO-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group SJC-CCM object-group ORD-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group SJC-CCM object-group NYC-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group SJC-CCM object-group RDU-CCM object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group SJC-CCM object-group ATL-CME object-group ICC-UDPaccess-list INSIDE-IN extended permit udp object-group SJC-CCM object-group YYZ-CME object-group ICC-UDPaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** COW trafficaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group RFD-CCMaccess-list INSIDE-IN extended permit udp object-group SJC-CCM object-group RFD-CCMaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** H323...access-list INSIDE-IN remark ***access-list INSIDE-IN remark *** ... CCM to GWaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group H323-GWS-OUT eq h323access-list INSIDE-IN remark ***access-list INSIDE-IN remark *** ... inside GW to remote CCMaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group H323-GWS-IN object-group RFD-CCM object-group H323-GW-TCPaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** ... between CCMs and GKsaccess-list INSIDE-IN remark *** (We could make the ports more granular.)access-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group GKS-IN object-group GKS-OUT object-group GK-TCP-UDPaccess-list INSIDE-IN extended permit udp object-group GKS-IN object-group GKS-OUT object-group GK-TCP-UDPaccess-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group GKS-OUT object-group GK-TCP-UDPaccess-list INSIDE-IN extended permit udp object-group SJC-CCM object-group GKS-OUT object-group GK-TCP-UDPaccess-list INSIDE-IN remark ***********************************************access-list INSIDE-IN remark *** Workarounds; outside of Security Policy ***access-list INSIDE-IN remark ***********************************************access-list INSIDE-IN remark ***access-list INSIDE-IN remark *** CSCsc11305 ICT & GKaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group DFW-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group RFD-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group SFO-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group ORD-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group NYC-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group RDU-CCM range 32768 65535access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group ATL-CME range 32768 65535access-list INSIDE-IN extended permit tcp object-group SJC-CCM object-group YYZ-CME range 32768 65535access-list INSIDE-IN remark ***access-list INSIDE-IN remark *** CSCsc55543 MOH & SIPaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit udp object-group MOH-SRVR object-group RTP object-group EVERYONE object-group RTPaccess-list INSIDE-IN remark ***************************************************access-list INSIDE-IN remark *** For convenience; outside of Security Policy ***access-list INSIDE-IN remark ***************************************************access-list INSIDE-IN remark *** Allow everything from blindly trusted sources until port use is determinedaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit ip object-group BLINDLY-TRUSTED anyaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** Allow telnet everywhereaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended permit tcp any any eq telnetaccess-list INSIDE-IN remark ***access-list INSIDE-IN remark *** Nothing else shall pass hereaccess-list INSIDE-IN remark ***access-list INSIDE-IN extended deny ip any anyaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** All ICMP trafficaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit icmp object-group EVERYONE object-group EVERYONEaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** Network mgmtaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit udp object-group NETMGMT-SRVR eq snmp object-group EVERYONE eq snmpaccess-list OUTSIDE-IN extended permit udp object-group NETMGMT-SRVR eq 1438 object-group EVERYONE eq snmpaccess-list OUTSIDE-IN extended permit udp object-group EVERYONE eq snmptrap object-group NETMGMT-SRVR eq snmptrapaccess-list OUTSIDE-IN extended permit tcp object-group NETMGMT-SRVR object-group EVERYONE eq sshaccess-list OUTSIDE-IN extended permit udp object-group EVERYONE object-group NETMGMT-SRVR eq tftpaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** DHCP and DNSaccess-list OUTSIDE-IN remark *** DHCP setting assumes no hosts directly connected to FWaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit udp object-group EVERYONE eq bootps object-group DHCP-SRVR-IN eq bootpsaccess-list OUTSIDE-IN extended permit udp object-group EVERYONE object-group DNS-SRVR-IN eq domainaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** Voice protocols from phones to CCMaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group IP-PHONES object-group SJC-CCM object-group PHONE-VOICE-TCPaccess-list OUTSIDE-IN extended permit udp object-group IP-PHONES object-group SJC-CCM object-group PHONE-VOICE-UDPaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** ICT communicationaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group DFW-CCM object-group SJC-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group SFO-CCM object-group SJC-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group ORD-CCM object-group SJC-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group NYC-CCM object-group SJC-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group RDU-CCM object-group SJC-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group ATL-CME object-group SJC-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit tcp object-group YYZ-CME object-group SJC-CCM object-group ICC-TCPaccess-list OUTSIDE-IN extended permit udp object-group DFW-CCM object-group SJC-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group SFO-CCM object-group SJC-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group ORD-CCM object-group SJC-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group NYC-CCM object-group SJC-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group RDU-CCM object-group SJC-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group ATL-CME object-group SJC-CCM object-group ICC-UDPaccess-list OUTSIDE-IN extended permit udp object-group YYZ-CME object-group SJC-CCM object-group ICC-UDPaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** COW trafficaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group RFD-CCM object-group SJC-CCMaccess-list OUTSIDE-IN extended permit udp object-group RFD-CCM object-group SJC-CCMaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** SRST servers to CCMaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group SRST object-group SJC-CCM object-group SRST-TCPaccess-list OUTSIDE-IN extended permit udp object-group SRST object-group SJC-CCM object-group SRST-UDPaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** MGCP gateways to CCMaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group MGCP-GWS-OUT object-group SJC-CCM object-group MGCP-GW-TCPaccess-list OUTSIDE-IN extended permit udp object-group MGCP-GWS-OUT object-group SJC-CCM object-group MGCP-GW-UDPaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** H323...access-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** ... GW to CCMaccess-list OUTSIDE-IN remark *** (We could make the source address more granular.)access-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group H323-GWS-OUT object-group SJC-CCM object-group H323-GW-TCPaccess-list OUTSIDE-IN extended permit udp object-group H323-GWS-OUT object-group SJC-CCM object-group H323-GW-UDPaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** ... between CCMs and GKsaccess-list OUTSIDE-IN remark *** (We could make the ports more granular.)access-list OUTSIDE-IN remark *** (We could make the source address more granular.)access-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group EVERYONE object-group GKS-IN object-group GK-TCP-UDPaccess-list OUTSIDE-IN extended permit udp object-group EVERYONE object-group GKS-IN object-group GK-TCP-UDPaccess-list OUTSIDE-IN remark ***********************************************access-list OUTSIDE-IN remark *** Workarounds; outside of Security Policy ***access-list OUTSIDE-IN remark ***********************************************access-list OUTSIDE-IN remark ***access-list OUTSIDE-IN remark *** CSCsc11305 ICT & GKaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit tcp object-group DFW-CCM object-group SJC-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group RFD-CCM object-group SJC-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group SFO-CCM object-group SJC-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group ORD-CCM object-group SJC-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group NYC-CCM object-group SJC-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group RDU-CCM object-group SJC-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group ATL-CME object-group SJC-CCM range 32768 65535access-list OUTSIDE-IN extended permit tcp object-group YYZ-CME object-group SJC-CCM range 32768 65535access-list OUTSIDE-IN remark ***************************************************access-list OUTSIDE-IN remark *** For convenience; outside of Security Policy ***access-list OUTSIDE-IN remark ***************************************************access-list OUTSIDE-IN remark *** Allow everything from blindly trusted sources until port use is determinedaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended permit ip any object-group BLINDLY-TRUSTEDaccess-list OUTSIDE-IN remark *** Nothing else shall pass hereaccess-list OUTSIDE-IN remark ***access-list OUTSIDE-IN extended deny ip any anyaccess-list tmp extended permit udp host 1.1.1.1 eq bootps host 1.1.1.1 eq bootpsno pagerlogging enablelogging standbylogging buffered debugginglogging trap debugginglogging host outside 10.3.2.129logging debug-tracemtu outside 1500mtu inside 1500failoverfailover lan unit primaryfailover lan interface flan Vlan11failover polltime unit 1 holdtime 5failover link flin Vlan13failover interface ip flan 1.1.1.1 255.255.255.252 standby 1.1.1.2failover interface ip flin 1.1.1.5 255.255.255.252 standby 1.1.1.6icmp permit any outsideicmp permit any insideno asdm history enablearp timeout 14400access-group OUTSIDE-IN in interface outsideaccess-group INSIDE-IN in interface insideroute outside 172.18.143.115 255.255.255.255 10.9.8.1 1route outside 10.3.2.204 255.255.255.255 10.9.8.1 1route outside 10.3.2.129 255.255.255.255 10.9.8.1 1!router ospf 1network 10.0.0.0 255.0.0.0 area 9area 9 stub no-summarylog-adj-changes!timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00timeout mgcp-pat 0:05:00 sip 0:30:00 sip_media 0:02:00 non_TCP_UDP 0:02:00timeout uauth 0:05:00 absoluteusername cisco password *************** encryptedaaa authentication telnet console LOCALaaa authentication ssh console LOCALsnmp-server host inside 10.9.12.21 community public version 2csnmp-server host outside 10.9.22.34 community public version 2csnmp-server host outside 172.18.143.115 community public version 2cno snmp-server locationno snmp-server contactsnmp-server community publicsnmp-server enable traps snmp authentication linkup linkdown coldstartno sysopt connection permit-ipsectelnet timeout 5ssh 10.3.2.0 255.255.255.0 outsidessh timeout 30console timeout 0!class-map inspection_defaultmatch default-inspection-trafficclass-map default!!policy-map global_policyclass inspection_defaultinspect dns maximum-length 512inspect ftpinspect h323 h225inspect h323 rasinspect netbiosinspect rshinspect skinnyinspect smtpinspect sqlnetinspect sunrpcinspect tftpinspect sipinspect xdmcp!service-policy global_policy globalprompt hostname context: end
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback