- Cisco Jabber Overview
- Configuration and Installation Workflows
- Configure Directory Integration
- Set Up Certificate Validation
- Configure Service Discovery
- Configure a Service Profile
- Configure IM and Presence Service
- Configure Voice and Video Communication
- Configure Voicemail
- Configure Conferencing
- Configure the Clients
- Integrate with Directory Sources
- Install the Clients
- Remote Access
- Cisco Jabber Features and Options
- Cisco Jabber Reference Information
- Integrate with Directory Sources for an On-Premises Deployment
- Configure Contact Sources
- Cisco Unified Communications Manager User Data Service
- When to Configure Directory Integration
- Configure Directory Integration in a Service Profile
- Advanced Directory Integration in the Configuration File
- UDS Parameters
- Directory Server Configuration Examples
- Domain Controller Connection
- Manual Server Connections for Cisco Jabber for Windows
- UDS Integration
- LDAP Integration with Expressway for Mobile and Remote Access
- Simple Authentication for Cisco Jabber for Windows
- Simple Authentication for Mobile Clients and Cisco Jabber for Mac
- Simple Authentication with SSL for Cisco Jabber for Windows
- Simple Authentication with SSL for Mobile Clients
- OpenLDAP Integration
- AD LDS Integration
Integrate with Directory Sources
Integrate with Directory Sources for an On-Premises Deployment
Configure Directory Integration for an On-Premises Deployment.
| Command or Action | Purpose |
|---|
Configure Contact Sources
The client requires a contact source to search for users and to support contact resolution.
You can configure Enhanced Directory Integration (EDI), Basic Directory Integration (BDI), and Cisco Unified Communications Manager User Data Service (UDS) as contact sources.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | To configure EDI as a contact source, see Domain Name Retrieval and Directory Server Discovery. |
EDI is an LDAP-based contact source and is the default contact source used by Cisco Jabber for Windows. |
| Step 2 | To configure BDI as a contact source, see Authentication with Contact Sources. |
BDI is an LDAP-based contact source and is the default contact source used by Cisco Jabber for Mac, iOS, and Android clients. |
| Step 3 | To configure UDS as a contact source, see Enable Integration with UDS and Set UDS Service Parameters |
Cisco Unified Communications Manager UDS is a Cisco Unified Communications Manager contact source and is available as a contact source for all Cisco Jabber clients. UDS is the contact source used for Expressway Mobile and Remote Access. |
Enhanced Directory Integration
EDI uses native Microsoft Windows APIs to retrieve contact data from the directory service.
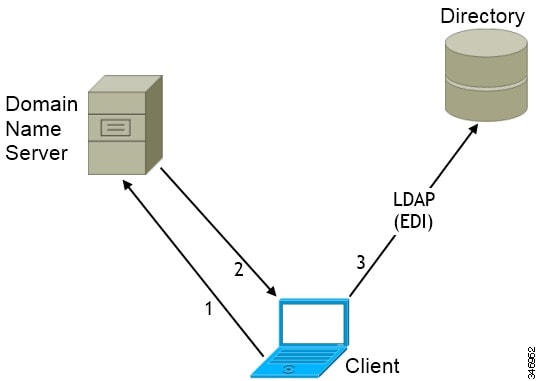
Domain Name Retrieval
Cisco Jabber for Windows retrieves the fully qualified DNS domain from the USERDNSDOMAIN environment variable on the client workstation.
After the client gets the DNS domain, it can locate the Domain Name Server and retrieve SRV records.
In some instances, the value of the USERDNSDOMAIN environment variable does not resolve to the DNS domain that corresponds to the domain of the entire forest. For example, when an organization uses a sub-domain or resource domain. In this case, the USERDNSDOMAIN environment variable resolves to a child domain, not the parent domain. As a result, the client cannot access information for all users in the organization.
If the USERDNSDOMAIN environment variable resolves to a child domain, you can use one of the following options to enable Cisco Jabber for Windows to connect to a service in the parent domain:
-
Ensure that the Global Catalog or LDAP directory server can access all users in the organization.
-
Configure your DNS server to direct the client to a server that can access all users in the organization when Cisco Jabber for Windows requests a Global Catalog or LDAP directory server.
-
Configure Cisco Jabber for Windows to use the FQDN of the parent domain.
Specify the FQDN of the parent domain as the value of the PrimaryServerName parameter in your client configuration as follows: <PrimaryServerName>parent-domain-fqdn</PrimaryServerName>
Directory Server Discovery
Directory Server |
SRV Record |
|---|---|
Global Catalog |
_gc._msdcs._tcp.domain.com |
Domain Controller LDAP-based directory servers |
_ldap._msdcs._tcp.domain.com |
Basic Directory Integration
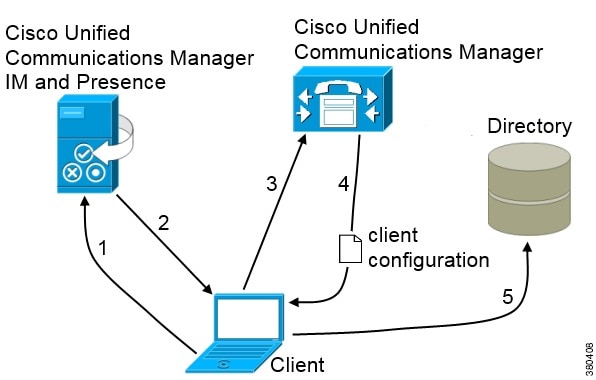
When using Basic Directory Integration ( BDI), the client retrieves contact data from the directory service as follows.
-
The client connects to the Cisco Unified Presence or Cisco Unified Communication Manager IM and Presence Service node.
-
The client gets the LDAP profile configuration section in the service profile from the Cisco Unified Presence or Cisco Unified Communication Manager IM and Presence Service node.
The service profile contains the location of Cisco Unified Communication Manager (TFTP) node. Depending on your configuration, the service profile can also contain the credentials to authenticate with the directory.
-
The client connects to the Cisco Unified Communication Manager node.
-
The client downloads the client configuration file from the Cisco Unified Communication Manager node.
The client configuration file contains the location of the directory. Depending on your configuration, the client configuration file can also contain the credentials to authenticate with the directory.
-
The client uses the directory location and the authentication credentials to connect to the directory.
Authentication with Contact Sources
Specify credentials in Cisco Unified Presence or Cisco Unified Communications Manager — Specify credentials in a profile on the server. The client can then retrieve the credentials from the server to authenticate with the directory. This method is the most secure option for storing and transmitting credentials.
Set common credentials in the client configuration file — Specify a shared username and password in the client configuration file. The client can then authenticate with the directory server. Important: The client transmits and stores these credentials as plain text.
Use a well-known or public set of credentials for an account that has read-only permissions.
Use anonymous binds — Configure the client to connect to the directory source with anonymous binds.
- Specify LDAP Directory Configuration on Cisco Unified Presence
- Specify LDAP Directory Configuration on Cisco Unified Communications Manager
- Set Credentials in the Client Configuration
- Use Anonymous Binds
Specify LDAP Directory Configuration on Cisco Unified Presence
If your environment includes Cisco Unified Presence release 8.x, you can specify directory configuration in the LDAP profile. The client can then get the directory configuration from the server to authenticate with the directory source.
Complete the steps to create an LDAP profile that contains authentication credentials, and then assign that profile to users.
What to Do Next
Specify any additional BDI information in the client configuration file.
Specify LDAP Directory Configuration on Cisco Unified Communications Manager
If your environment includes Cisco Unified Communications Manager release 9.x and later, you can specify credentials when you add a directory service. The client can then get the configuration from the server to authenticate with the directory source.
Complete the steps to add a directory service, apply the directory service to the service profile, and specify the LDAP authentication configuration for the directory service.
Set Credentials in the Client Configuration
The client transmits and stores these credentials as plain text.
Use a well-known or public set of credentials for an account that has read-only permissions.
The following is an example configuration:
<Directory> <BDIConnectionUsername>admin@example.com</BDIConnectionUsername> <BDIConnectionPassword>password</BDIConnectionPassword> </Directory>
Use Anonymous Binds
To use anonymous binds, you set the following parameters in the client configuration file:
Parameter |
Value |
|---|---|
DirectoryServerType |
BDI |
| BDIPrimaryServerName |
IP address FQDN |
BDIEnableTLS |
True |
| BDISearchBase1 |
Searchable organizational unit (OU) in the directory tree |
| BDIBaseFilter | Object class that your directory service uses; for example, inetOrgPerson |
| BDIPredictiveSearchFilter | UID or other search filter A search filter is optional. |
The following is an example configuration:
<Directory> <DirectoryServerType>BDI</DirectoryServerType> <BDIPrimaryServerName>11.22.33.456</BDIPrimaryServerName> <BDIEnableTLS>True</BDIEnableTLS> <BDISearchBase1>ou=people,dc=cisco,dc=com</BDISearchBase1> <BDIBaseFilter>(&(objectClass=inetOrgPerson)</BDIBaseFilter> <BDIPredictiveSearchFilter>uid</BDIPredictiveSearchFilter> </Directory>
Cisco Unified Communications Manager User Data Service
User Data Service (UDS) is a REST interface on Cisco Unified Communications Manager that provides contact resolution.
-
If you set the DirectoryServerType parameter to use a value of UDS in the client configuration file.
With this configuration, the client uses UDS for contact resolution when it is inside or outside of the corporate firewall.
-
If you deploy Expressway for Remote and Mobile Access.
With this configuration, the client automatically uses UDS for contact resolution when it is outside of the corporate firewall.
You synchronize contact data into Cisco Unified Communications Manager from a directory server. Cisco Jabber then automatically retrieves that contact data from UDS.
Enable Integration with UDS
To enable integration with UDS, perform the following steps:
Set UDS Service Parameters
You can set service parameters for UDS on Cisco Unified Communications Manager.
UDS Service Parameters
Parameter |
Description |
||
|---|---|---|---|
Enable All User Search |
Allows searches for all users in the directory (search with no last name, first name, or directory number specified). The default value is true. |
||
User Search Limit |
Limits the number of users returned in a query. The default value is 64. |
||
Number of Digits to Match |
Specifies the number of digits to match when users search for phone numbers.
|
Contact Resolution with Multiple Clusters
For contact resolution with multiple Cisco Unified Communications Manager clusters, synchronize all users on the corporate directory to each cluster. Provision a subset of those users on the appropriate cluster.
When users in Europe call users in North America, Cisco Jabber retrieves the contact details for the user in Europe from cucm-cluster-na.
When users in North America call users in Europe, Cisco Jabber retrieves the contact details for the user in North America from cucm-cluster-eu.
Federation
Federation lets Cisco Jabber users communicate with users who are provisioned on different systems and who are using client applications other than Cisco Jabber.
Interdomain Federation
Interdomain federation enables Cisco Jabber users in an enterprise domain to share availability and send instant messages with users in another domain.
You configure interdomain federation for Cisco Jabber on Cisco Unified Presence or Cisco Unified Communications Manager IM and Presence Service. See the appropriate server documentation for more information.
Intradomain Federation
Intradomain federation enables users within the same domain to share availability and send instant messages between Cisco Unified Presence and Microsoft Office Communications Server, Microsoft Live Communications Server, or another presence server.
Cisco Unified Presence: Integration Guide for Configuring Partitioned Intradomain Federation for Cisco Unified Presence Release 8.6 and Microsoft LCS/OCS
Cisco Unified Communications Manager IM and Presence Service: Partitioned Intradomain Federation for IM and Presence Service on Cisco Unified Communications Manager
Configure Intradomain Federation for BDI or EDI
In addition to configuring intradomain federation on the presence server, you might need to specify some configuration settings in the Cisco Jabber configuration files.
To resolve contacts during contact search or retrieve contact information from your directory, Cisco Jabber requires the contact ID for each user. Cisco Unified Presence uses a specific format for resolving contact information that does not always match the format on other presence servers such as Microsoft Office Communications Server or Microsoft Live Communications Server.
The parameters that you use to configure intradomain federation depend on whether you use Enhanced Directory Integration (EDI) or Basic Directory Integration (BDI). EDI uses native Microsoft Windows APIs to retrieve contact data from the directory service and is only used by Cisco Jabber for Windows. For BDI, the client retrieves contact data from the directory service and is used by Cisco Jabber for Mac, Cisco Jabber for Android, and Cisco Jabber for iPhone and iPad.
<Directory> <BDIUseSIPURIToResolveContacts>true</BDIUseSIPURIToResolveContacts> <BDISipUri>non-default-attribute</BDISipUri> <BDIUriPrefix>sip:</BDIUriPrefix> </Directory>
<Directory> <UseSIPURIToResolveContacts>true</UseSIPURIToResolveContacts> <SipUri>non-default-attribute</SipUri> <UriPrefix>sip:</UriPrefix> </Directory>
Client Configuration for Directory Integration
You can configure directory integration through service profiles using Cisco Unified Communications Manager release 9 or later or with the configuration file. Use this section to learn how to configure the client for directory integration.
When both a service profile and a configuration file are present, the following table describes which parameter value takes precedence.
Service Profile |
Configuration File |
Which Parameter Value Takes Precedence? |
|---|---|---|
Parameter value is set |
Parameter value is set |
Service profile |
Parameter value is set |
Parameter value is blank |
Service profile |
Parameter value is blank |
Parameter value is set |
Configuration file |
Parameter value is blank |
Parameter value is blank |
Service profile blank (default) value |
 Note | Cisco Unified Presence, Release 8.x profiles cannot be used for directory integration. |
- When to Configure Directory Integration
- Configure Directory Integration in a Service Profile
- Advanced Directory Integration in the Configuration File
When to Configure Directory Integration
 Note | Install Cisco Jabber for Windows on a workstation that is registered to an Active Directory domain. In this environment, you do not need to configure Cisco Jabber for Windows to connect to the directory. The client automatically discovers the directory and connects to a Global Catalog server in that domain. |
Configure Directory Integration in a Service Profile
With Cisco Unified Communications Manager release 9 and later, you can provision users with service profiles and deploy the _cisco-uds SRV record on your internal domain server.
The client can then automatically discover Cisco Unified Communications Manager and retrieve the service profile to get directory integration configuration. For information about service discovery, see Configure Service Discovery.
| Command or Action | Purpose |
|---|
Add a Directory Service
| Step 1 | Open the Cisco Unified CM Administration interface. |
| Step 2 | Select . The Find and List UC Services window opens. |
| Step 3 | Select Add New. The UC Service Configuration window opens. |
| Step 4 | Select Directory from the UC Service Type menu and then select Next. |
| Step 5 | Set all appropriate values for the directory service and then select Save. |
What to Do Next
Apply Directory Service.
Directory Profile Parameters
|
Directory Service Configuration |
Description |
||
|---|---|---|---|
|
Primary server |
Specifies the address of the primary directory server. This parameter is required for manual connections where the client cannot automatically discover the directory server. |
||
|
Secondary server |
|||
|
Tertiary Server |
Specifies the address of the tertiary directory server. |
||
|
Use UDS for Contact Resolution |
Specifies if the client uses UDS as a contact source.
|
||
|
Use Logged On User Credential |
|
||
|
Username |
Lets you manually specify a shared username that the client can use to authenticate with the directory server. By default, the client uses Integrated Windows Authentication when connecting to the directory server. This parameter lets you manually specify a username in scenarios where it is not possible to authenticate with the directory server with the user's Microsoft Windows credentials. Use only a well-known or public set of credentials for an account that has read-only permissions. |
||
|
Password |
Lets you manually specify a shared password that the client can use to authenticate with the directory server. By default, the client uses Integrated Windows Authentication when connecting to the directory server. This parameter lets you manually specify a password in scenarios where it is not possible to authenticate with the directory server with the user's Microsoft Windows credentials. Use only a well-known or public set of credentials for an account that has read-only permissions. |
||
|
Search Base 1 Search Base 2 Search Base 3 |
Specifies a location in the directory server from which searches begin. In other words, a search base is the root from which the client executes a search. By default, the client searches from the root of the directory tree. You can specify the value of up to three search bases in your OU to override the default behavior. Active Directory does not typically require a search base. Specify search bases for Active Directory only for specific performance requirements. Specify a search base for directory servers other than Active Directory to create bindings to specific locations in the directory.
|
||
|
Recursive Search on All Search Bases |
Select this option to perform a recursive search of the directory starting at the search base. Use recursive searches to allow the Cisco Jabber client contact search queries to search all of the LDAP directory tree from a given search context (search base). This is a common option when searching LDAP. This is a required field. The default value is True. |
||
|
Base Filter |
Specifies a base filter for Active Directory queries. Specify a directory subkey name only to retrieve objects other than user objects when you query the directory. The default value is (&(objectCategory=person)( objectClass=user). |
||
|
Predictive Search Filter |
Defines filters to apply to predictive search queries. You can define multiple, comma-separated values to filter search queries. The default value is Ambiguous Name Resolution (ANR). You must configure your directory server to set attributes for ANR if you want the client to search for those attributes. |
Service Discovery will use UDS search when the Use UDS for Contact Resolution option is selected, otherwise it uses BDI or EDI search. During service discovery the Username, Password, SearchBase1, PrimaryServerName, ServerPort1, UriPrefix, UseJabberCredentials, BaseFilter, PredictiveSearchFilter, and DirectoryServerType in the directory profile will be used to connect to LDAP server for contact search.
Manual sign on uses the Username and Password from the directory profile to connect to the LDAP server for contact search.
Attribute Mappings
It is not possible to change the default attribute mappings in a service profile. If you plan to change any default attribute mappings, you must define the required mappings in a client configuration file.
Apply Directory Service to a Service Profile
| Step 1 | Select . The Find and List Service Profiles window opens. |
| Step 2 | Select Add New. The Service Profile Configuration window opens. |
| Step 3 | Add the directory services to the directory profile. See the Directory Profile Parameters topic for information about the specific settings that are needed for the directory profile. |
| Step 4 | Select Save. |
Advanced Directory Integration in the Configuration File
You can configure directory integration in the Cisco Jabber configuration file. The following sections show the parameters that can be configured and also includes a section covering examples of the configuration..
Summary of Directory Integration Configuration Parameters
The following tables are a summary of all directory integration parameters.
Attribute Mapping
These parameters are used for attribute mapping with LDAP directory servers.
|
BDI Parameters |
EDI Parameters |
|---|---|
|
Directory Server Connection
These parameters are used for connecting to LDAP directory servers.
|
BDI Parameters |
EDI Parameters |
|---|---|
Contact Resolution and Directory Query
These parameters are used for contact resolution and directory queries with LDAP directory servers.
|
BDI Parameters |
EDI Parameters |
|---|---|
|
UDS
These parameters are used for interacting with UDS as a contact source.
Directory Server Type Parameter
Parameter |
Value |
Description |
|---|---|---|
DirectoryServerType |
BDI EDI UDS |
|
EDI and BDI Directory Integration Parameters
The following sections lists details about the EDI and BDI parameters you can configure for LDAP-based directory integration.
- Attribute Mapping Parameters
- Directory Connection Parameters
- IM Address Scheme Parameters
- Directory Query Parameters
- Phone Number Masks Parameter
- Contact Photo Parameters
Attribute Mapping Parameters
BDI Parameter |
EDI Parameter |
Directory Attribute |
Exists in Global Catalog by Default |
Is Indexed by Default |
Set for Ambiguous Name Resolution (ANR) by Default |
||||
|---|---|---|---|---|---|---|---|---|---|
BDICommonName |
CommonName |
cn |
Yes |
Yes |
No |
||||
BDIDisplayName |
DisplayName |
displayName |
Yes |
Yes |
Yes |
||||
BDIFirstname |
Firstname |
givenName |
Yes |
Yes |
Yes |
||||
BDILastname |
Lastname |
sn |
Yes |
Yes |
Yes |
||||
BDIEmailAddress |
EmailAddress |
Yes |
Yes |
Yes |
|||||
|
|
msRTCSIP-PrimaryUserAddress |
Yes |
Yes |
Yes |
||||
BDIPhotoSource |
PhotoSource |
thumbnailPhoto |
No |
No |
No |
||||
BDIBusinessPhone |
BusinessPhone |
telephoneNumber |
Yes |
No |
No |
||||
BDIMobilePhone |
MobilePhone |
mobile |
Yes |
No |
No |
||||
BDIHomePhone |
HomePhone |
homePhone |
Yes |
No |
No |
||||
BDIOtherPhone |
OtherPhone |
otherTelephone |
Yes |
No |
No |
||||
|
|
Yes |
No |
No |
|||||
BDITitle |
Title |
title |
Yes |
No |
No |
||||
BDICompanyName |
CompanyName |
company |
Yes |
Yes |
No |
||||
BDIUserAccountName |
UserAccountName |
sAMAccountName |
Yes |
Yes |
Yes |
||||
BDIDomainName |
DomainName |
EDI - userPrincipalName BDI - dn |
Yes |
Yes |
No |
||||
BDICountry |
co |
Yes |
No |
No |
|||||
BDILocation |
Location |
EDI - co BDI - location |
Yes |
No |
No |
||||
BDINickname |
Nickname |
displayName |
Yes |
Yes |
Yes |
||||
BDIPostalCode |
PostalCode |
postalCode |
Yes |
No |
No |
||||
BDICity |
City |
l |
Yes |
Yes |
No |
||||
BDIState |
State |
st |
Yes |
Yes |
No |
||||
BDIStreetAddress |
StreetAddress |
streetAddress |
Yes |
No |
No |
Attributes on the Directory Server
You must index attributes on your LDAP directory server so that the client can resolve contacts.
-
sAMAccountName
-
displayName
-
sn
-
name
-
proxyAddresses
-
mail
-
department
-
givenName
-
telephoneNumber
Additionally, ensure you index the following attributes for secondary number queries: 
Note
By default secondary number queries are enabled in Cisco Jabber for Windows. You can disable secondary number queries with the DisableSecondaryNumberLookups parameter.
-
msRTCSIP-PrimaryUserAddress
-
Replicating attributes to your Global Catalog server generates traffic between Active Directory servers in the domain. For this reason, replicate attributes to your Global Catalog server at a time when network traffic can handle extra load.
-
If you do not want to replicate attributes to a Global Catalog server, configure Cisco Jabber to connect to a Domain Controller. However, the client queries single domains only when it connects to a Domain Controller.
Directory Connection Parameters
|
BDI Parameter |
EDI Parameter |
Value |
Description |
||
|---|---|---|---|---|---|
ConnectionType |
|
||||
BDILDAPServerType |
AD OpenLDAP |
|
|||
BDIPresenceDomain |
Domain of the presence node. |
Required parameter. Specifies the domain of the presence node. The client appends this domain to the user ID to create an IM address. For example, a user named Adam McKenzie has the user ID amckenzie. You specify example.com as the presence node domain. When the user logs in, the client constructs the IM address amckenzie@example.com for Adam McKenzie. |
|||
BDIPrimaryServerName |
PrimaryServerName |
Required parameter. Specifies the address of the primary directory server. This parameter is required for manual connections where the client cannot automatically discover the directory server.
|
|||
SecondaryServerName |
IP address FQDN |
Specifies the address of the backup directory server. This parameter is required for manual connections where the client cannot automatically discover the directory server. |
|||
BDIServerPort1 |
ServerPort1 |
||||
ServerPort2 |
ServerPort2 |
Port number |
|||
UseWindowsCredentials |
0 1 |
|
|||
BDIUseJabberCredentials |
true false |
|
|||
BDIConnectionUsername |
ConnectionUsername |
Lets you manually specify a shared username that the client can use to authenticate with the directory server. The client transmits and stores this username as plain text. By default, Cisco Jabber for Windows uses Integrated Windows Authentication when connecting to the directory server. This parameter lets you manually specify a username in scenarios where it is not possible to authenticate with the directory server with the user's Microsoft Windows credentials. Use only a well-known or public set of credentials for an account with read-only permissions to the directory. |
|||
BDIConnectionPassword |
ConnectionPassword |
Lets you manually specify a shared password that the client can use to authenticate with the directory server. The client transmits and stores this password as plain text. By default, Cisco Jabber for Windows uses Integrated Windows Authentication when connecting to the directory server. This parameter lets you manually specify a password in scenarios where it is not possible to authenticate with the directory server with the user's Microsoft Windows credentials. Use a well-known or public set of credentials for an account with read-only permissions to the directory. |
|||
BDIEnableTLS |
true false |
|
|||
UseSSL |
0 1 |
|
|||
UseSecureConnection |
0 1 |
|
IM Address Scheme Parameters
|
BDI Parameter |
EDI Parameter |
Value |
Description |
|---|---|---|---|
|
BDIUseSipUriTo ResolveContacts |
UseSipUriTo ResolveContacts |
false |
|
|
BDIUriPrefix |
UriPrefix |
prefix string |
Specifies a prefix to remove from the SipUri or BDISipUri parameter. For example, sip: may prefix the msRTCSIP-PrimaryUserAddress directory attribute. |
|
BDISipUri |
SipUri |
msRTCSIP PrimaryUser Address |
Specifies the directory attribute field that the IM Address scheme field is mapped to. |
<Directory> <BDIUseSIPURIToResolveContacts>true</BDIUseSIPURIToResolveContacts> <BDISipUri>non-default-attribute</BDISipUri> <BDIUriPrefix>sip:</BDIUriPrefix> </Directory>
<Directory> <UseSIPURIToResolveContacts>true</UseSIPURIToResolveContacts> <SipUri>non-default-attribute</SipUri> <UriPrefix>sip:</UriPrefix> </Directory>
Directory Query Parameters
|
BDI Parameter |
EDI Parameter |
Value |
Description |
||
|---|---|---|---|---|---|
|
BDIBaseFilter |
BaseFilter |
Specifies a base filter for Active Directory queries. Specify a directory subkey name only to retrieve objects other than user objects when you query the directory. The default value for all clients is (&(objectCategory=person)( objectClass=user). Configuration files can contain only valid XML character entity references. Use & instead of & if you specify a custom base filter. |
|||
|
BDIUseANR |
true false |
Configure your directory server to set attributes for ANR if you want the client to search for those attributes. |
|||
|
BDIPredictiveSearchFilter |
PredictiveSearchFilter |
Defines filters to apply to predictive search queries. You can define multiple, comma-separated values to filter search queries.
Configure your directory server to set attributes for ANR if you want the client to search for those attributes. |
|||
|
DisableSecondaryNumberLookups |
0 1 |
|
|||
|
SearchTimeout |
|||||
|
UseWildcards |
0 1 |
|
|||
|
MinimumCharacterQuery |
Sets the minimum number of characters in a contact name to query the directory. For example, if you set 2 as the value of this parameter, the client searches the directory when users enter at least two characters in the search field. |
||||
|
BDISearchBase1 |
SearchBase1 SearchBase2 SearchBase3 SearchBase4 SearchBase5 |
Specifies a location in the directory server from which searches begin. In other words, a search base is the root from which the client executes a search. By default, the client searches from the root of the directory tree. You can specify the value of up to five search bases in your OU to override the default behavior. Active Directory does not typically require a search base. Specify search bases for Active Directory only for specific performance requirements. Specify a search base for directory servers other than Active Directory to create bindings to specific locations in the directory.
|
Base Filter Examples
The following are example base filters you can use to look up specific locations or objects.
Find only specific groups:
(&(objectClass=user)(memberOf=cn=group-name,ou=Groups,dc=example,dc=com))
Find a nested group within a group:
(&(objectClass=user)(memberOf:search-oid:=cn=group-name,ou=Groups,dc=example,dc=com))
Find only enabled accounts and non-administrator accounts:
(&(objectCategory=person)(objectClass=user)(!(userAccountControl:search-oid:=2)) (!(sAMAccountName=*_dbo))(!(sAMAccountName=*-admin)))
Phone Number Masks Parameter
|
Parameter |
Value |
Description |
|---|---|---|
|
PhoneNumberMasks |
Specifies masks to use when users search for phone numbers. For example, a user receives a call from +14085550100. In the directory, this number is +(1) 408 555 0100. The following mask resolves the number: +1408|+(#) ### ### #### The length of mask strings cannot exceed the size restriction for registry subkey names. |
Phone masks apply to phone numbers before the client searches your directory. If you configure phone masks correctly, directory searches succeed as exact query matches and prevent any impact to performance of your directory server.
|
Element |
Description |
|---|---|
|
Phone number pattern |
Provides a number pattern to retrieve phone numbers from your directory. To add a phone mask, you specify a number pattern that applies to the mask. For example, to specify a mask for searches that begin with +1408, you can use the following mask: +1408|+(#) ### ### #### To enable a mask to process phone numbers that have the same number of digits, but different patterns, use multiple masks with the same number of digits.
|
|
Pipe symbol (|) |
Separates number patterns and masks. For example, +1408|+(#) ### ### ####|+34|+(##) ### ####. |
|
Wildcard character |
Substitutes one or more characters for a subset of possible matching characters. Any wildcard character can exist in a phone mask.
|
|
Reverse mask |
Applies a number pattern from right to left. For example, a mask of +3498|R+34 (98) 559 #### applied to +34985590199 results in +34 (98) 559 0199. You can use both forward and reverse masks. |
Contact Photo Parameters
BDI Parameter |
EDI Parameter |
Value |
Description |
|---|---|---|---|
BDIPhotoUriSubstitutionEnabled |
PhotoUriSubstitutionEnabled |
|
|
BDIPhotoUriSubstitutionToken |
PhotoUriSubstitutionToken |
Specifies a directory attribute to insert in the photo URI; for example, sAMAccountName. |
|
BDIPhotoUriWithToken |
PhotoUriWithToken |
Specifies a photo URI with a directory attribute as a variable value. For example: http://staffphoto.example.com/sAMAccountName.jpg The parameter applies to LDAP directory integrations. To configure photo URI substitution, you set the directory attribute as the value of BDIPhotoUriSubstitutionToken. The client must be able to retrieve the photos from the web server without credentials. |
|
BDIPhotoSource |
PhotoSource |
Directory attribute |
The name of a directory attribute that stores a contact photo as a binary object or a URI to a contact photo. |
Contact Photo Retrieval
Cisco Jabber retrieves and displays contact photos with the following methods.
 Note | When you change a photo in the Active Directory, the photo can take up to 24 hours to refresh in Cisco Jabber. |
URI substitution
Cisco Jabber dynamically builds a URL to contact photos with a directory attribute and a URL template.
- Specify true as the value of the BDIPhotoUriSubstitutionEnabled or PhotoUriSubstitutionEnabled parameter.
- Specify a directory
attribute to use as a dynamic token as the value of the
BDIPhotoUriSubstitutionToken or PhotoUriSubstitutionToken parameter. For
example,
<BDIPhotoUriSubstitutionToken>sAMAccountName</BDIPhotoUriSubstitutionToken>
<PhotoUriSubstitutionToken>sAMAccountName</PhotoUriSubstitutionToken>
- Specify the URL and the
dynamic token as the value of the BDIPhotoUriWithToken or PhotoUriWithToken
parameter. Use a direct URL for photo retrieval. Do not use redirected URLs. For example,
<BDIPhotoUriWithToken>http://staffphoto.example.com/sAMAccountName.jpg</BDIPhotoUriWithToken>
<PhotoUriWithToken>http://staffphoto.example.com/sAMAccountName.jpg</PhotoUriWithToken>
With the example values in the preceding steps, the sAMAccountName attribute might resolve to msmith in your directory. Cisco Jabber then takes this value and replaces the token to build the following URL: http://staffphoto.example.com/msmith.jpg.
Binary objects
Cisco Jabber retrieves the binary data for the photo from your database.
If you are using binary objects from Active Directory do not set BDIPhotoUriWithToken or PhotoUriWithToken.
<BDIPhotoSource>jpegPhoto</BDIPhotoSource>
<PhotoSource>thumbnailPhoto</PhotoSource>
PhotoURL attribute
Cisco Jabber retrieves a URL from a directory attribute.
<BDIPhotoSource>photoUri</BDIPhotoSource>
<PhotoSource>photoUri</PhotoSource>
UDS Parameters
| Parameter | Value | Description |
|---|---|---|
|
PresenceDomain |
Domain of the presence node. |
Required parameter. Specifies the domain of the presence server. The client appends this domain to the user ID to create an IM address. For example, a user named Adam McKenzie has the following user ID: amckenzie. You specify example.com as the presence server domain. When the user logs in, the client constructs the following IM address for Adam McKenzie: amckenzie@example.com. |
|
UdsServer |
IP address FQDN |
Specifies the address of the Cisco Unified Communications Manager User Data Service (UDS) server. This parameter is required for manual connections where the client cannot automatically discover the UDS server. |
|
UdsPhotoUriWithToken |
URI |
Specifies a photo URI with a directory attribute as a variable value; for example, http://www.photo/url/path/%%uid%%.jpg.
The client must be able to retrieve the photos from the web server without credentials. |
|
UseSIPURIToResolveContacts |
true false |
|
|
UriPrefix |
prefix string |
Specifies a prefix to remove from the SipUri or BDISipUri parameter. For example, sip: may prefix the msRTCSIP-PrimaryUserAddress directory attribute. |
|
SipUri |
msRTCSIP-PrimaryUser ddress |
Specifies the directory attribute field that the IM Address scheme field is mapped to. |
IM Address Scheme with UDS
<Directory> <DirectoryServerType>UDS</DirectoryServerType> <UseSIPURIToResolveContacts>true</UseSIPURIToResolveContacts> <SipUri>non-default-attribute</SipUri> <UriPrefix>sip:</UriPrefix> </Directory>
Contact Photo Retrieval with UDS
Cisco Unified Communications Manager User Data Service (UDS) dynamically builds a URL for contact photos with a directory attribute and a URL template.
<UdsPhotoUriWithToken>http://server_name/%%uid%%.jpg</UdsPhotoUriWithToken>
UDS substitutes the %%uid%% token with the value of the userName attribute in UDS. For example, a user named Mary Smith exists in your directory. The value of the userName attribute for Mary Smith is msmith. To resolve the contact photo for Mary Smith, Cisco Jabber takes the value of the userName attribute and replaces the %%uid%% token to build the following URL: http://staffphoto.example.com/msmith.jpg
 Note | When you change a photo in the Active Directory, the photo can take up to 24 hours to refresh in Cisco Jabber. |
-
If you deploy Expressway for Mobile and Remote Access, the client automatically uses UDS for contact resolution when users connect to services from outside the corporate network. When you set up UDS contact resolution for Expressway for Mobile and Remote Access, you must add the web server on which you host the contact photos to the HTTP server allow list in your Cisco Expressway-C server configuration. The HTTP server allow list enables the client to access web services inside the corporate network.
-
All contact photos must follow the format of the URL you specify as the value of UdsPhotoUriWithToken.
Directory Server Configuration Examples
This section describes supported integration scenarios and provides example configurations.
- Domain Controller Connection
- Manual Server Connections for Cisco Jabber for Windows
- UDS Integration
- LDAP Integration with Expressway for Mobile and Remote Access
- Simple Authentication for Cisco Jabber for Windows
- Simple Authentication for Mobile Clients and Cisco Jabber for Mac
- Simple Authentication with SSL for Cisco Jabber for Windows
- Simple Authentication with SSL for Mobile Clients
- OpenLDAP Integration
- AD LDS Integration
Domain Controller Connection
Parameter |
Value |
|---|---|
DirectoryServerType |
EDI |
ConnectionType |
1 |
<Directory><DirectoryServerType>EDI</DirectoryServerType> <ConnectionType>1</ConnectionType></Directory>
Manual Server Connections for Cisco Jabber for Windows
Parameter |
Value |
|---|---|
DirectoryServerType |
EDI |
|
PrimaryServerName |
FQDN IP address |
|
ServerPort1 |
Port number |
SecondaryServerName |
FQDN IP address |
ServerPort2 |
Port number |
<Directory>
<DirectoryServerType>EDI</DirectoryServerType>
<PrimaryServerName>primary-server-name.domain.com</PrimaryServerName> <ServerPort1>1234</ServerPort1> <SecondaryServerName>secondary-server-name.domain.com</SecondaryServerName> <ServerPort2>5678</ServerPort2> </Directory>
UDS Integration
Parameter |
Value |
||
|---|---|---|---|
DirectoryServerType |
UDS |
||
UdsServer |
IP address of the UDS server |
||
UdsPhotoUriWithToken |
Contact photo URL |
||
|
PresenceDomain
|
Server address of your presence domain |
 Note | Configure the DirectoryServerType parameter to UDS only if you want to use UDS for all contact resolution (that is, from inside and outside the corporate firewall). |
<Directory> <DirectoryServerType>UDS</DirectoryServerType> <UdsServer>11.22.33.444</UdsServer> <UdsPhotoUriWithToken>http://server-name/%%uid%%.jpg</UdsPhotoUriWithToken> </Directory>
LDAP Integration with Expressway for Mobile and Remote Access
 Note | LDAP is the default configuration, so it is not necessary to include the DirectoryServerType parameter in your client configuration file. |
Parameter |
Value |
|---|---|
| BDIPhotoUriWithToken | Contact photo URL when inside the corporate firewall |
| UdsPhotoUriWithToken | Contact photo URL when outside the corporate firewall |
<Directory> <BDIPhotoUriWithToken>http://photo.example.com/sAMAccountName.jpg</BDIPhotoUriWithToken> <UdsPhotoUriWithToken>http://server-name/%%uid%%.jpg</UdsPhotoUriWithToken> </Directory>
Simple Authentication for Cisco Jabber for Windows
<UseWindowsCredentials>0</UseWindowsCredentials> <UseSSL>0</UseSSL> <UseSecureConnection>0</UseSecureConnection> <ConnectionUsername>username</ConnectionUsername> <ConnectionPassword>password</ConnectionPassword>
Simple Authentication for Mobile Clients and Cisco Jabber for Mac
Simple authentication lets you connect to a directory server using simple binds, as in the following example configuration:
<BDIEnableTLS>False</BDIEnableTLS> <BDIConnectionUsername>username</BDIConnectionUsername> <BDIConnectionPassword>password</BDIConnectionPassword> <BDIServerPort1>389/3268</BDIServerPort1>
Simple Authentication with SSL for Cisco Jabber for Windows
<UseWindowsCredentials>0</UseWindowsCredentials> <UseSSL>1</UseSSL> <UseSecureConnection>0</UseSecureConnection> <ConnectionUsername>username</ConnectionUsername> <ConnectionPassword>password</ConnectionPassword>
Simple Authentication with SSL for Mobile Clients
<BDIEnableTLS>True</BDIEnableTLS> <BDIConnectionUsername>username</BDIConnectionUsername> <BDIConnectionPassword>password</BDIConnectionPassword> <BDIServerPort1>636/3269</BDIServerPort1>
OpenLDAP Integration
You can integrate with OpenLDAP using anonymous binds or authenticated binds.
- Anonymous Binds for Cisco Jabber for Windows
- Anonymous Binds for Mobile Clients and Cisco Jabber for Mac
- Authenticated Binds for Cisco Jabber for Windows
- Authenticated Binds for Mobile Clients and Cisco Jabber for Mac
Anonymous Binds for Cisco Jabber for Windows
|
Parameter |
Value |
|---|---|
|
DirectoryServerType |
EDI |
|
ConnectionType |
1 |
| PrimaryServerName |
IP address Hostname |
| UseWindowsCredentials |
0 |
| UseSecureConnection |
1 |
|
SearchBase1 |
Root of the directory service or the organizational unit (OU) |
|
UserAccountName |
Unique identifier such as UID or CN |
|
BaseFilter |
Object class that your directory service uses; for example, inetOrgPerson. |
|
PredictiveSearchFilter |
UID or other search filter |
<Directory> <DirectoryServerType>EDI</DirectoryServerType> <ConnectionType>1</ConnectionType> <PrimaryServerName>11.22.33.456</PrimaryServerName> <UseWindowsCredentials>0</UseWindowsCredentials> <UseSecureConnection>1</UseSecureConnection> <SearchBase1>ou=people,dc=cisco,dc=com</SearchBase1> <UserAccountName>uid</UserAccountName> <BaseFilter>(&(objectClass=inetOrgPerson)</BaseFilter> <PredictiveSearchFilter>uid</PredictiveSearchFilter> </Directory>
Anonymous Binds for Mobile Clients and Cisco Jabber for Mac
|
Parameter |
Value |
|---|---|
|
DirectoryServerType |
BDI |
|
BDILDAPServerType |
OpenLDAP |
| BDIPrimaryServerName |
IP address Hostname |
|
BDIEnableTLS |
True |
| BDISearchBase1 |
Root of the directory service or the organizational unit (OU) |
| BDIServerPort1 |
The port for the primary directory server |
| BDIUserAccountName |
Unique identifier such as uid or cn |
| BDIBaseFilter |
Object class that your directory service uses; for example, inetOrgPerson. |
| (Optional) BDIPredictiveSearchFilter |
uid or other search filter |
<Directory> <DirectoryServerType>BDI</DirectoryServerType> <BDILDAPServerType>OpenLDAP</BDILDAPServerType> <BDIPrimaryServerName>11.22.33.456</BDIPrimaryServerName> <BDIEnableTLS>True</BDIEnableTLS> <BDISearchBase1>ou=people,dc=cisco,dc=com</BDISearchBase1> <BDIServerPort1>636/3269</BDIServerPort1> <BDIUserAccountName>uid</BDIUserAccountName> <BDIBaseFilter>(&(objectClass=inetOrgPerson)</BDIBaseFilter> <BDIPredictiveSearchFilter>uid</BDIPredictiveSearchFilter> </Directory>
Authenticated Binds for Cisco Jabber for Windows
|
Parameter |
Value |
|---|---|
|
DirectoryServerType |
EDI |
|
ConnectionType |
1 |
|
PrimaryServerName |
IP address Hostname |
|
UserWindowsCredentials |
0 |
|
UseSecureConnection |
0 |
|
SearchBase1 |
Root of the directory service or the organizational unit (OU) |
|
UserAccountName |
Unique identifier such as UID or CN |
|
BaseFilter |
Object class that your directory service uses; for example, inetOrgPerson. |
|
PredictiveSearchFilter |
UID or other search filter |
|
ConnectionUsername |
Username |
|
ConnectionPassword |
Password |
<Directory> <DirectoryServerType>EDI</DirectoryServerType> <ConnectionType>1</ConnectionType> <PrimaryServerName>11.22.33.456</PrimaryServerName> <UserWindowsCredentials>0</UserWindowsCredentials> <UseSecureConnection>0</UseSecureConnection> <SearchBase1>ou=people,dc=cisco,dc=com</SearchBase1> <UserAccountName>uid</UserAccountName> <BaseFilter>(&(objectClass=inetOrgPerson)</BaseFilter> <PredictiveSearchFilter>uid</PredictiveSearchFilter> <ConnectionUsername>cn=lds-read-only-user,dc=cisco,dc=com</ConnectionUsername> <ConnectionPassword>password</ConnectionPassword> </Directory>
Authenticated Binds for Mobile Clients and Cisco Jabber for Mac
|
Parameter |
Value |
|---|---|
| DirectoryServerType |
BDI |
| BDILDAPServerType |
OpenLDAP |
| BDIPrimaryServerName |
IP address Hostname |
| BDIEnableTLS |
False |
| BDISearchBase1 |
Root of the directory service or the organizational unit (OU) |
| BDIServerPort1 |
The port for the primary directory server |
| BDIUserAccountName |
Unique identifier such as UID or CN |
| BDIBaseFilter |
Object class that your directory service uses; for example, inetOrgPerson. |
| BDIPredictiveSearchFilter |
(Optional) UID or other search filter |
| BDIConnectionUsername |
Username |
| BDIConnectionPassword |
Password |
<Directory> <DirectoryServerType>BDI</DirectoryServerType> <BDILDAPServerType>OpenLDAP</BDILDAPServerType> <BDIPrimaryServerName>11.22.33.456</BDIPrimaryServerName> <BDIEnableTLS>False</BDIEnableTLS> <BDISearchBase1>ou=people,dc=cisco,dc=com</BDISearchBase1> <BDIServerPort1>389/3268</BDIServerPort1> <BDIUserAccountName>uid</BDIUserAccountName> <BDIBaseFilter>(&(objectClass=inetOrgPerson)</BDIBaseFilter> <BDIPredictiveSearchFilter>uid</BDIPredictiveSearchFilter> <BDIConnectionUsername>cn=administrator,dc=cisco,dc=com</BDIConnectionUsername> <BDIConnectionPassword>password</BDIConnectionPassword> </Directory>
AD LDS Integration
You can integrate with AD LDS or ADAM using specific configurations.
- Anonymous Binds for Cisco Jabber for Windows
- Anonymous Binds for Mobile Clients and Cisco Jabber for Mac
- Windows Principal User Authentication
- AD LDS Principal User Authentication for Cisco Jabber for Windows
- AD LDS Principal User Authentication for Mobile Clients and Cisco Jabber for Mac
Anonymous Binds for Cisco Jabber for Windows
Parameter |
Value |
|---|---|
DirectoryServerType |
EDI |
|
PrimaryServerName |
IP address Hostname |
|
ServerPort1 |
Port number |
UseWindowsCredentials |
0 |
UseSecureConnection |
1 |
|
SearchBase1 |
Root of the directory service or the organizational unit (OU) |
<Directory>
<DirectoryServerType>EDI</DirectoryServerType>
<PrimaryServerName>11.22.33.456</PrimaryServerName> <ServerPort1>50000</ServerPort1>
<UseWindowsCredentials>0</UseWindowsCredentials> <UseSecureConnection>1</UseSecureConnection>
<SearchBase1>dc=adam,dc=test</SearchBase1> </Directory>
Anonymous Binds for Mobile Clients and Cisco Jabber for Mac
Parameter |
Value |
|---|---|
|
BDIPrimaryServerName |
IP address Hostname |
|
BDIServerPort1 |
Port number |
|
BDISearchBase1 |
Root of the directory service or the organizational unit (OU) |
<Directory> <BDIPrimaryServerName>11.22.33.456</BDIPrimaryServerName> <BDIServerPort1>50000</BDIServerPort1> <BDISearchBase1>dc=adam,dc=test</BDISearchBase1> </Directory>
Windows Principal User Authentication
Parameter |
Value |
|---|---|
DirectoryServerType |
EDI |
PrimaryServerName |
IP address Hostname |
ServerPort1 |
Port number |
UseWindowsCredentials |
0 |
UseSecureConnection |
1 |
ConnectionUsername |
Username |
ConnectionPassword |
Password |
UserAccountName |
Unique identifier such as UID or CN |
SearchBase1 |
Root of the directory service or the organizational unit (OU) |
<Directory> <DirectoryServerType>EDI</DirectoryServerType> <PrimaryServerName>11.22.33.456</PrimaryServerName> <ServerPort1>50000</ServerPort1> <UseWindowsCredentials>0</UseWindowsCredentials> <UseSecureConnection>1</UseSecureConnection> <ConnectionUsername>cn=administrator,dc=cisco,dc=com</ConnectionUsername> <ConnectionPassword>password</ConnectionPassword> <UserAccountName>cn</UserAccountName> <SearchBase1>ou=people,dc=cisco,dc=com</SearchBase1> </Directory>
AD LDS Principal User Authentication for Cisco Jabber for Windows
Parameter |
Value |
|---|---|
DirectoryServerType |
EDI |
|
PrimaryServer |
IP address Hostname |
|
ServerPort1 |
Port number |
UseWindowsCredentials |
0 |
UseSecureConnection |
0 |
|
ConnectionUsername |
Username |
|
ConnectionPassword |
Password |
|
UserAccountName |
Unique identifier such as UID or CN |
|
SearchBase1 |
Root of the directory service or the organizational unit (OU) |
<Directory>
<DirectoryServerType>EDI</DirectoryServerType>
<PrimaryServerName>11.22.33.456</PrimaryServerName> <ServerPort1>50000</ServerPort1> <UseWindowsCredentials>0</UseWindowsCredentials> <UseSecureConnection>0</UseSecureConnection> <ConnectionUsername>cn=administrator,dc=cisco,dc=com</ConnectionUsername> <ConnectionPassword>password</ConnectionPassword> <UserAccountName>cn</UserAccountName> <SearchBase1>ou=people,dc=cisco,dc=com</SearchBase1> </Directory>
AD LDS Principal User Authentication for Mobile Clients and Cisco Jabber for Mac
Parameter |
Value |
|---|---|
|
BDIPrimaryServerName |
IP address Hostname |
|
BDIServerPort1 |
Port number |
|
BDIConnectionUsername |
Username |
|
BDIConnectionPassword |
Password |
|
BDIUserAccountName |
Unique identifier such as uid or cn |
|
BDISearchBase1 |
Root of the directory service or the organizational unit (OU) |
<Directory>> <BDIPrimaryServerName>11.22.33.456</BDIPrimaryServerName> <BDIServerPort1>50000</BDIServerPort1> <BDIConnectionUsername>cn=administrator,dc=cisco,dc=com</BDIConnectionUsername> <BDIConnectionPassword>password</BDIConnectionPassword> <BDIUserAccountName>cn</BDIUserAccountName> <BDISearchBase1>ou=people,dc=cisco,dc=com</BDISearchBase1> </Directory>
 Feedback
Feedback