Configuring Dynamic ARP Inspection
Available Languages
Contents
- Configuring Dynamic ARP Inspection
- Information About DAI
- Understanding ARP
- Understanding ARP Spoofing Attacks
- Understanding DAI and ARP Spoofing Attacks
- Interface Trust States and Network Security
- Logging DAI Packets
- Licensing Requirements for DAI
- Prerequisites for DAI
- Guidelines and Limitations for DAI
- Default Settings for DAI
- Configuring DAI
- Enabling or Disabling DAI on VLANs
- Configuring the DAI Trust State of a Layer 2 Interface
- Enabling or Disabling Additional Validation
- Configuring the DAI Logging Buffer Size
- Configuring DAI Log Filtering
- Verifying the DAI Configuration
- Monitoring and Clearing DAI Statistics
- Configuration Examples for DAI
- Example 1 Two Devices Support DAI
- Configuring Device A
- Configuring Device B
Configuring Dynamic ARP Inspection
This chapter describes how to configure dynamic Address Resolution Protocol (ARP) inspection (DAI) on a Cisco Nexus 3000 Series switch.
This chapter includes the following sections:
- Information About DAI
- Licensing Requirements for DAI
- Prerequisites for DAI
- Guidelines and Limitations for DAI
- Default Settings for DAI
- Configuring DAI
- Verifying the DAI Configuration
- Monitoring and Clearing DAI Statistics
- Configuration Examples for DAI
Information About DAI
- Understanding ARP
- Understanding ARP Spoofing Attacks
- Understanding DAI and ARP Spoofing Attacks
- Interface Trust States and Network Security
- Logging DAI Packets
Understanding ARP
ARP provides IP communication within a Layer 2 broadcast domain by mapping an IP address to a MAC address. For example, host B wants to send information to host A but does not have the MAC address of host A in its ARP cache. In ARP terms, host B is the sender and host A is the target.
To get the MAC address of host A, host B generates a broadcast message for all hosts within the broadcast domain to obtain the MAC address associated with the IP address of host A. All hosts within the broadcast domain receive the ARP request, and host A responds with its MAC address.
Understanding ARP Spoofing Attacks
ARP spoofing attacks and ARP cache poisoning can occur because ARP allows a reply from a host even if an ARP request was not received. After the attack, all traffic from the device under attack flows through the attacker’s computer and then to the router, switch, or host.
An ARP spoofing attack can affect hosts, switches, and routers connected to your Layer 2 network by sending false information to the ARP caches of the devices connected to the subnet. Sending false information to an ARP cache is known as ARP cache poisoning. Spoof attacks can also intercept traffic intended for other hosts on the subnet.
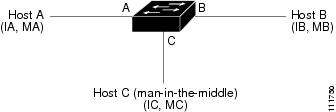
Hosts A, B, and C are connected to the device on interfaces A, B, and C, all of which are on the same subnet. Their IP and MAC addresses are shown in parentheses; for example, host A uses IP address IA and MAC address MA. When host A needs to send IP data to host B, it broadcasts an ARP request for the MAC address associated with IP address IB. When the device and host B receive the ARP request, they populate their ARP caches with an ARP binding for a host with the IP address IA and a MAC address MA; for example, IP address IA is bound to MAC address MA. When host B responds, the device and host A populate their ARP caches with a binding for a host with the IP address IB and the MAC address MB.
Host C can poison the ARP caches of the device, host A, and host B by broadcasting two forged ARP responses with bindings: one for a host with an IP address of IA and a MAC address of MC and another for a host with the IP address of IB and a MAC address of MC. Host B and the device then use the MAC address MC as the destination MAC address for traffic intended for IA, which means that host C intercepts that traffic. Likewise, host A and the device use the MAC address MC as the destination MAC address for traffic intended for IB.
Because host C knows the true MAC addresses associated with IA and IB, it can forward the intercepted traffic to those hosts by using the correct MAC address as the destination. This topology, in which host C has inserted itself into the traffic stream from host A to host B, is an example of a man-in-the middle attack.
Understanding DAI and ARP Spoofing Attacks
DAI ensures that only valid ARP requests and responses are relayed. When DAI is enabled and properly configured, a Cisco NX-OS device performs these activities:
- Intercepts all ARP requests and responses on untrusted ports
- Verifies that each of these intercepted packets has a valid IP-to-MAC address binding before updating the local ARP cache or before forwarding the packet to the appropriate destination
- Drops invalid ARP packets
DAI can determine the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a Dynamic Host Configuration Protocol (DHCP) snooping binding database. This database is built by DHCP snooping if DHCP snooping is enabled on the VLANs and on the device. It can also contain static entries that you create. If the ARP packet is received on a trusted interface, the device forwards the packet without any checks. On untrusted interfaces, the device forwards the packet only if it is valid.
You can configure DAI to drop ARP packets when the IP addresses in the packets are invalid or when the MAC addresses in the body of the ARP packets do not match the addresses specified in the Ethernet header.
Interface Trust States and Network Security
DAI associates a trust state with each interface on the device. Packets that arrive on trusted interfaces bypass all DAI validation checks, and packets that arrive on untrusted interfaces go through the DAI validation process.
In a typical network configuration, the guidelines for configuring the trust state of interfaces are as follows:
- Untrusted
Interfaces that are connected to hosts
- Trusted
Interfaces that are connected to devices
With this configuration, all ARP packets that enter the network from a device bypass the security check. No other validation is needed at any other place in the VLAN or in the network.
Caution
Use the trust state configuration carefully. Configuring interfaces as untrusted when they should be trusted can result in a loss of connectivity.
Figure 2. ARP Packet Validation on a VLAN Enabled for DAI.In this figure, assume that both device A and device B are running DAI on the VLAN that includes host 1 and host 2. If host 1 and host 2 acquire their IP addresses from the DHCP server connected to device A, only device A binds the IP-to-MAC address of host 1. If the interface between device A and device B is untrusted, the ARP packets from host 1 are dropped by device B and connectivity between host 1 and host 2 is lost.
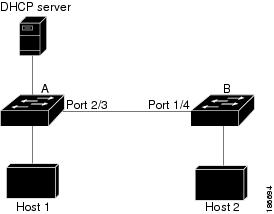
If you configure interfaces as trusted when they should be untrusted, you may open a security hole in a network. If device A is not running DAI, host 1 can easily poison the ARP cache of device B (and host 2, if you configured the link between the devices as trusted). This condition can occur even though device B is running DAI.
DAI ensures that hosts (on untrusted interfaces) connected to a device that runs DAI do not poison the ARP caches of other hosts in the network; however, DAI does not prevent hosts in other portions of the network from poisoning the caches of the hosts that are connected to a device that runs DAI.
If some devices in a VLAN run DAI and other devices do not, then the guidelines for configuring the trust state of interfaces on a device running DAI becomes the following:
- Untrusted
Interfaces that are connected to hosts or to devices that are not running DAI
- Trusted
Interfaces that are connected to devices that are running DAI
To validate the bindings of packets from devices that are not running DAI, configure ARP ACLs on the device running DAI. When you cannot determine the bindings, isolate at Layer 3 the devices that run DAI from devices that do not run DAI.
Note
Depending on your network setup, you may not be able to validate a given ARP packet on all devices in the VLAN.
Logging DAI Packets
Cisco NX-OS maintains a buffer of log entries about DAI packets processed. Each log entry contains flow information, such as the receiving VLAN, the port number, the source and destination IP addresses, and the source and destination MAC addresses.
You can also specify the type of packets that are logged. By default, a Cisco NX-OS device logs only packets that DAI drops.
If the log buffer overflows, the device overwrites the oldest DAI log entries with newer entries. You can configure the maximum number of entries in the buffer.
Note
Cisco NX-OS does not generate system messages about DAI packets that are logged.
Licensing Requirements for DAI
This table shows the licensing requirements for DAI.
Product
License Requirement
Cisco NX-OS
DAI requires no license. Any feature not included in a license package is bundled with the Cisco NX-OS system images and is provided at no extra charge to you. For an explanation of the Cisco NX-OS licensing scheme, see the Cisco NX-OS Licensing Guide.
Guidelines and Limitations for DAI
DAI has the following configuration guidelines and limitations:
- DAI is an ingress security feature; it does not perform any egress checking.
- DAI is not effective for hosts connected to devices that do not support DAI or that do not have this feature enabled. Because man-in-the-middle attacks are limited to a single Layer 2 broadcast domain, you should separate the domain with DAI from domains without DAI. This separation secures the ARP caches of hosts in the domain with DAI.
- DAI depends on the entries in the DHCP snooping binding database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. If you want DAI to use static IP-MAC address bindings to determine if ARP packets are valid, DHCP snooping needs only to be enabled. If you want DAI to use dynamic IP-MAC address bindings to determine if ARP packets are valid, DHCP snooping must configured on the same VLANs on which you configure DAI.
- When you use the feature dhcp command to enable the DHCP feature, there is a delay of approximately 30 seconds before the I/O modules receive the DHCP or DAI configuration. This delay occurs regardless of the method that you use to change from a configuration with the DHCP feature disabled to a configuration with the DHCP feature enabled. For example, if you use the Rollback feature to revert to a configuration that enables the DHCP feature, the I/O modules receive the DHCP and DAI configuration approximately 30 seconds after you complete the rollback.
- DAI is supported on access ports, trunk ports, port-channel ports, and private VLAN ports.
- The DAI trust configuration of a port channel determines the trust state of all physical ports that you assign to the port channel. For example, if you have configured a physical port as a trusted interface and then you add that physical port to a port channel that is an untrusted interface, the physical port becomes untrusted.
- When you remove a physical port from a port channel, the physical port does not retain the DAI trust state configuration of the port channel.
- When you change the trust state on the port channel, the device configures a new trust state on all the physical ports that comprise the channel.
- If you want DAI to use static IP-MAC address bindings to determine if ARP packets are valid, ensure that DHCP snooping is enabled and that you have configured the static IP-MAC address bindings.
- If you want DAI to use dynamic IP-MAC address bindings to determine if ARP packets are valid, ensure that DHCP snooping is enabled.
Default Settings for DAI
This table lists the default settings for DAI parameters.
Table 1 Default DAI ParametersParameters
Default
DAI
Disabled on all VLANs.
Interface trust state
All interfaces are untrusted.
Validation checks
No checks are performed.
Log buffer
When DAI is enabled, all denied or dropped ARP packets are logged.
The number of entries in the log is 32.
The number of system messages is limited to 5 per second.
The logging-rate interval is 1 second.
Per-VLAN logging
All denied or dropped ARP packets are logged.
Configuring DAI
- Enabling or Disabling DAI on VLANs
- Configuring the DAI Trust State of a Layer 2 Interface
- Enabling or Disabling Additional Validation
- Configuring the DAI Logging Buffer Size
- Configuring DAI Log Filtering
Enabling or Disabling DAI on VLANs
SUMMARY STEPS
1. configure terminal
2. [no] ip arp inspection vlan list
3. (Optional) show ip arp inspection vlan list
4. (Optional) copy running-config startup-config
DETAILED STEPS
Configuring the DAI Trust State of a Layer 2 Interface
SUMMARY STEPSYou can configure the DAI interface trust state of a Layer 2 interface. By default, all interfaces are untrusted.
A device forwards ARP packets that it receives on a trusted Layer 2 interface but does not check them.
On untrusted interfaces, the device intercepts all ARP requests and responses, verifies that the intercepted packets have valid IP-MAC address bindings before updating the local cache and forwarding the packet to the appropriate destination. If the device determines that packets have invalid bindings, it drops the packets and logs them according to the logging configuration.
1. configure terminal
2. interface type slot / number
3. [no] ip arp inspection trust
4. (Optional) show ip arp inspection interface type slot / number
5. (Optional) copy running-config startup-config
DETAILED STEPS
Enabling or Disabling Additional Validation
SUMMARY STEPSYou can enable or disable additional validation of ARP packets. By default, no additional validation of ARP packets is enabled. When no additional validation is configured, the source MAC address, source IP address check against the IP-to-MAC binding entry for ARP packets is done using the Ethernet source MAC address (not the ARP sender MAC address) and the ARP sender IP address.
DAI intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. You can enable additional validation on the destination MAC address, the sender and target IP addresses, and the source MAC address.
You can use the following keywords with the ip arp inspection validate command to implement additional validations:
- dst-mac
Checks the destination MAC address in the Ethernet header against the target MAC address in the ARP body for ARP responses. When enabled, packets with different MAC addresses are classified as invalid and are dropped.
- ip
Checks the ARP body for invalid and unexpected IP addresses. Addresses include 0.0.0.0, 255.255.255.255, and all IP multicast addresses. Sender IP addresses are checked in all ARP requests and responses, and target IP addresses are checked only in ARP responses.
- src-mac
Checks the source MAC address in the Ethernet header against the sender MAC address in the ARP body for ARP requests and responses. When enabled, packets with different MAC addresses are classified as invalid and are dropped.
When enabling additional validation, follow these guidelines:
- You must specify at least one of the keywords. You can specify one, two, or all three keywords.
- Each ip arp inspection validate command that you enter replaces the configuration from any previous commands. If you enter an ip arp inspection validate command to enable src-mac and dst-mac validations, and a second ip arp inspection validate command to enable ip validation, the src-mac and dst-mac validations are disabled when you enter the second command.
1. configure terminal
2. [no] ip arp inspection validate {[src-mac] [dst-mac] [ip]}
3. (Optional) show running-config dhcp
4. (Optional) copy running-config startup-config
DETAILED STEPS
Configuring the DAI Logging Buffer Size
SUMMARY STEPS
1. configure terminal
2. [no] ip arp inspection log-buffer entries number
3. (Optional) show running-config dhcp
4. (Optional) copy running-config startup-config
DETAILED STEPS
Configuring DAI Log Filtering
SUMMARY STEPSYou can configure how the device determines whether to log a DAI packet. By default, the device logs DAI packets that are dropped.
1. configure terminal
2. Enter one of the following commands:
3. (Optional) show running-config dhcp
4. (Optional) copy running-config startup-config
DETAILED STEPS
Verifying the DAI Configuration
To display the DAI configuration information, perform one of the following tasks.
Command
Purpose
show running-config arp
Displays DAI configuration.
show ip arp inspection
Displays the status of DAI.
show ip arp inspection interface ethernet
Displays the trust state and ARP packet rate for a specific interface.
show ip arp inspection vlan
Displays the DAI configuration for a specific VLAN.
show arp access-lists
Displays ARP ACLs.
show ip arp inspection log
Displays the DAI log configuration.
Monitoring and Clearing DAI Statistics
To monitor and clear DAI statistics, use the commands in this table. For more information about these commands, see the Cisco Nexus 7000 Series NX-OS Security Command Reference.
Command
Purpose
show ip arp inspection statistics
Displays DAI statistics.
show ip arp ethernet
Displays interface-specific DAI statistics.
clear ip arp inspection statistics
Clears DAI statistics.
Configuration Examples for DAI
Example 1 Two Devices Support DAI
These procedures show how to configure DAI when two devices support DAI.
Figure 3. Two Devices Supporting DAI.This figure shows the network configuration for this example. Host 1 is connected to device A, and Host 2 is connected to device B. Both devices are running DAI on VLAN 1 where the hosts are located. A DHCP server is connected to device A. Both hosts acquire their IP addresses from the same DHCP server. Device A has the bindings for Host 1 and Host 2, and device B has the binding for Host 2. Device A Ethernet interface 2/3 is connected to the device B Ethernet interface 1/4.

DAI depends on the entries in the DHCP snooping binding database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically-assigned IP addresses.
Configuring Device A
Configuring Device B
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)


 Feedback
Feedback