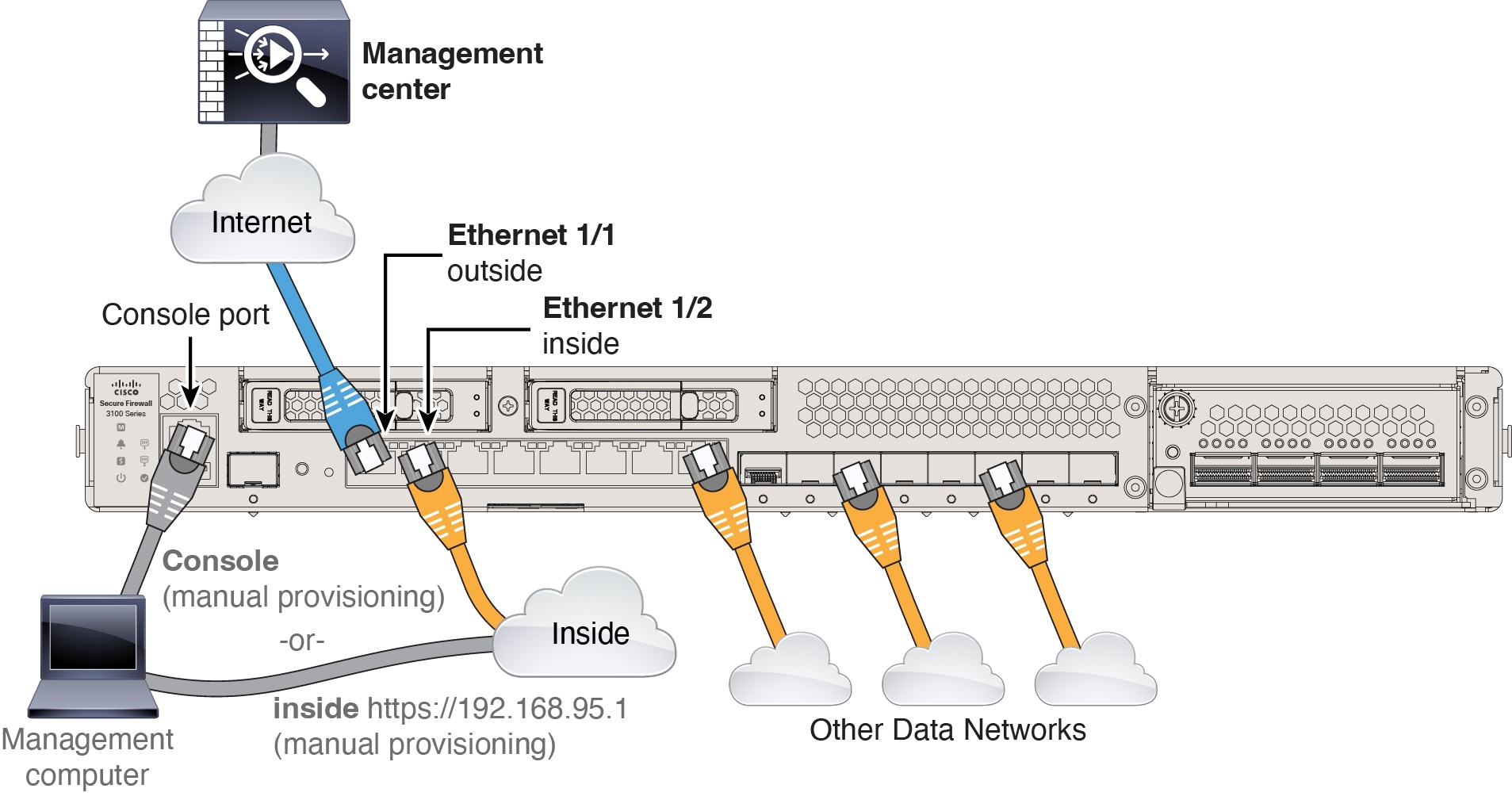
Cable the Firewall
-
(Optional) Obtain a console adapter—The firewall ships with a DB-9 to RJ-45 serial cable, so you may need to buy a third party DB-9-to-USB serial cable to make the connection.
-
Install SFP/SFP+ modules into ports Ethernet 1/9 and higher.
-
See the hardware installation guide for more information.
-
If you use zero-touch provisioning, do not cable both the outside and the Management interface. This guide covers management on the outside interface, but you may want to use zero-touch provisioning on Management with high availability. If you use zero-touch provisioning on outside and want to use high availability, you will have to change the outside IP address to a static address after registration.







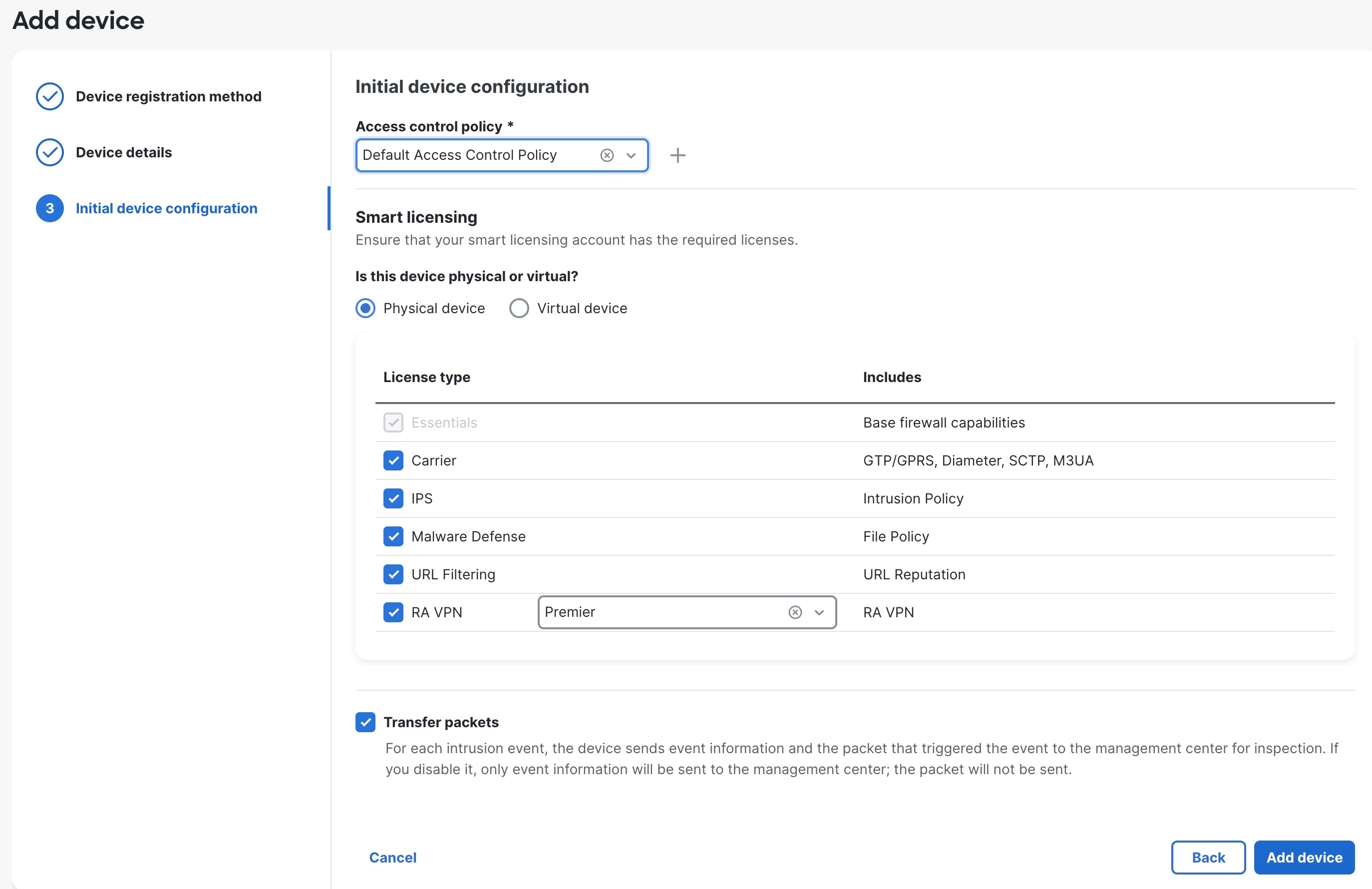

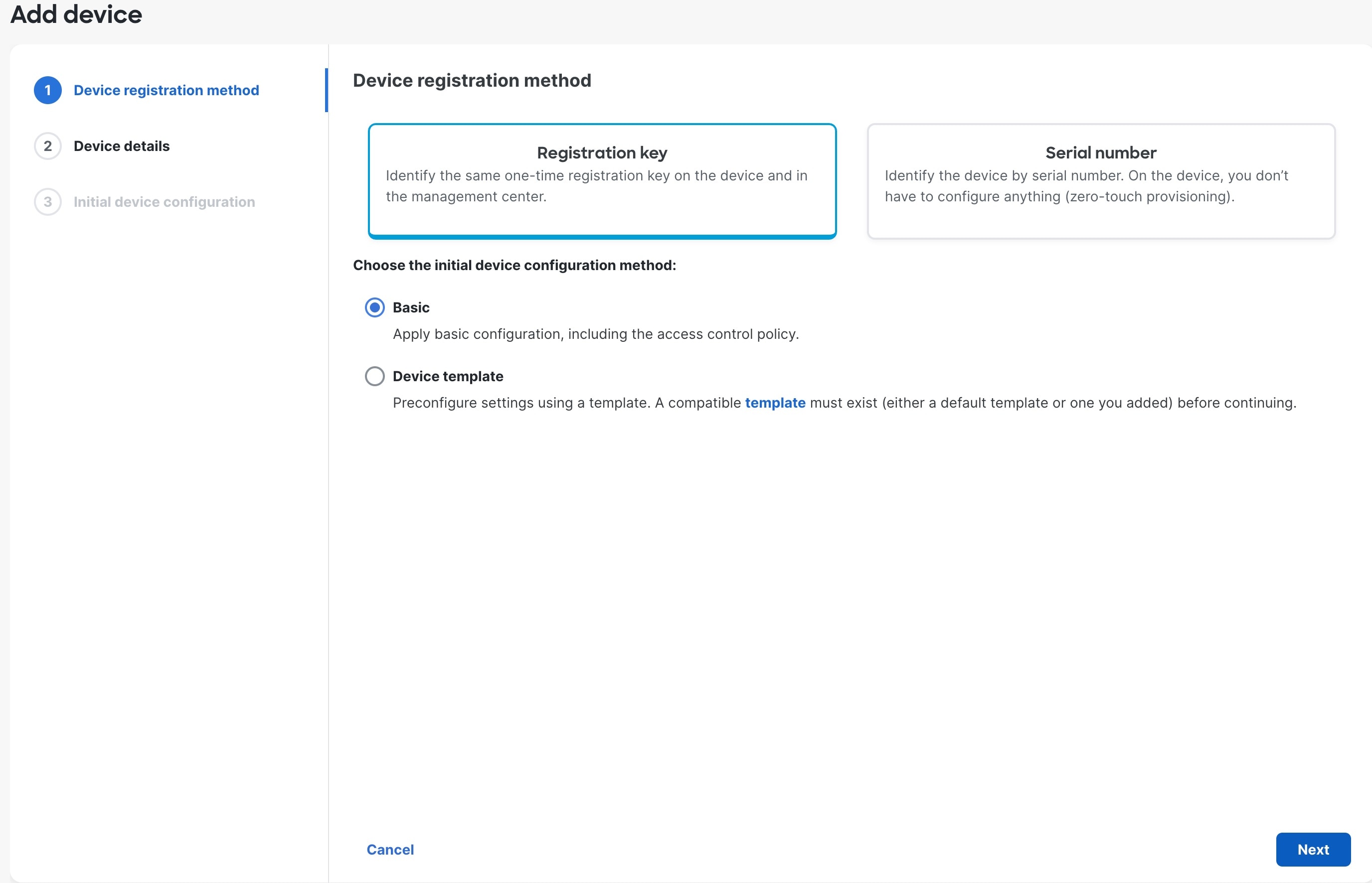
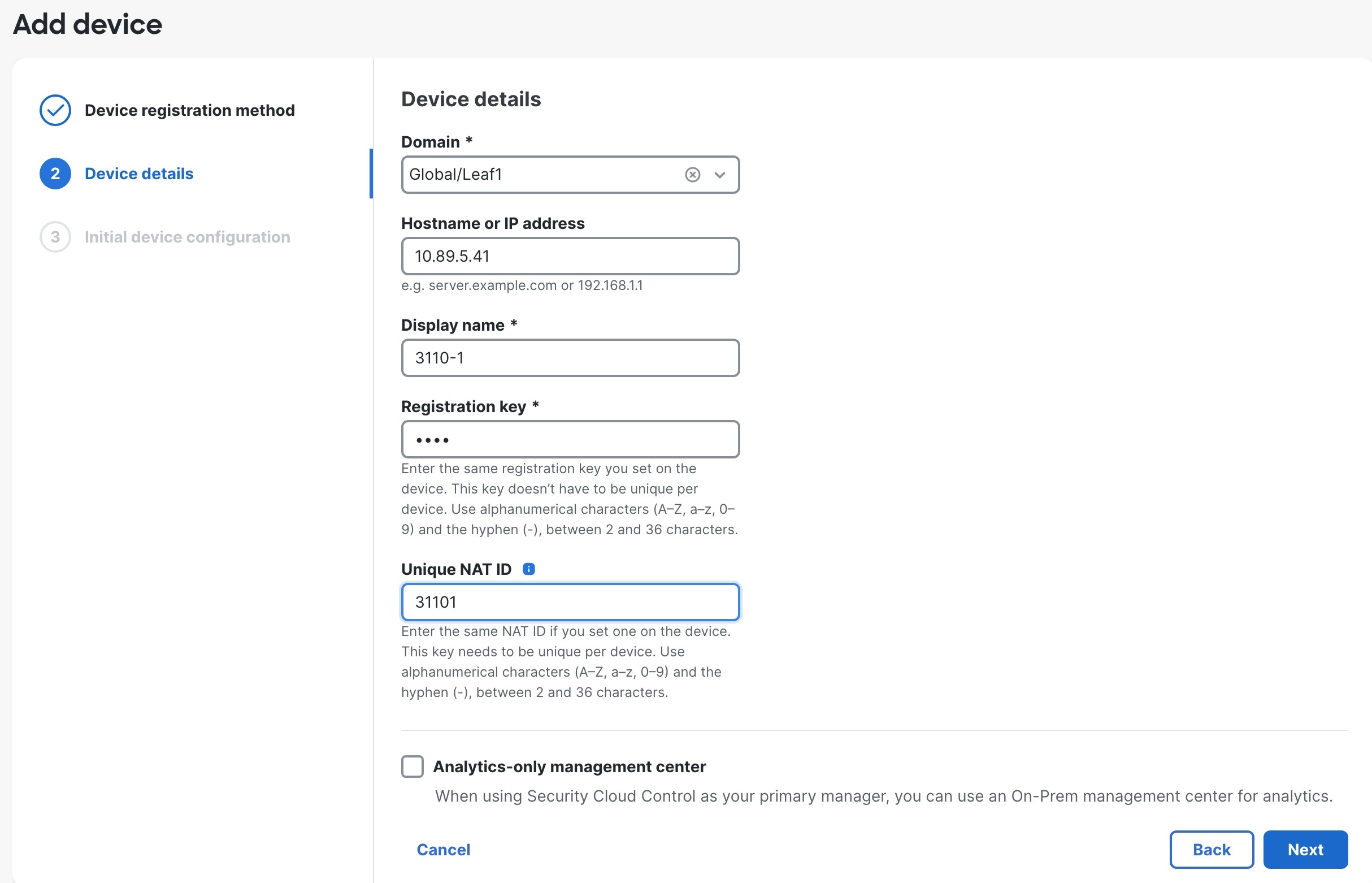
 Feedback
Feedback