Overview
The Cisco Secure Firewall Threat Defense Virtual runs the same software as physical Cisco Firewall Threat Defense to deliver proven security functionality in a virtual form factor. The Firewall Threat Defense Virtual can be deployed in the public OCI. It can then be configured to protect virtual and physical data center workloads that expand, contract, or shift their location over time.
OCI Compute Shapes
A shape is a template that determines the number of CPUs, amount of memory, and other resources that are allocated to an instance. The Firewall Threat Defense Virtual support the following OCI shape types:
|
OCI Shape |
Supported Threat Defense Virtual version |
Attributes |
Interfaces |
|
|---|---|---|---|---|
|
oCPUs |
RAM (GB) |
|||
|
Intel VM.DenseIO2.8 |
7.3.x and later |
8 |
120 |
Minimum 4, Maximum 8 |
|
Intel VM.StandardB1.4 |
7.3.x and later |
4 |
48 |
Minimum 4, Maximum 4 |
|
Intel VM.StandardB1.8 |
7.3.x and later |
4 |
96 |
Minimum 4, Maximum 8 |
|
Intel VM.Standard1.4 |
7.3.x and later |
4 |
28 |
Minimum 4, Maximum 4 |
|
Intel VM.Standard1.8 |
7.3.x and later |
8 |
56 |
Minimum 4, Maximum 8 |
|
Intel VM.Standard2.4 |
7.1, 7.2.x, and 7.3.x |
4 |
60 |
Minimum 4, Maximum 4 |
|
Intel VM.Standard2.8 |
7.1, 7.2.x, and 7.3.x |
8 |
120 |
Minimum 4, Maximum 8 |
|
Intel VM.Standard3.Flex* |
7.3.x and later |
4 |
16 |
Minimum 4, Maximum 4 |
|
7.3.x and later |
6 |
24 |
Minimum 4, Maximum 6 |
|
|
7.3.x and later |
8 |
32 |
Minimum 4, Maximum 8 |
|
|
Intel VM.Optimized3.Flex* |
7.3.x and later |
4 |
16 |
Minimum 4, Maximum 8 |
|
7.3.x and later |
6 |
24 |
Minimum 4, Maximum 10 |
|
|
7.3.x and later |
8 |
32 |
Minimum 4, Maximum 10 |
|
|
AMD VM.Standard.E4.Flex* |
7.3.x and later |
4 |
16 |
Minimum 4, Maximum 4 |
|
7.3.x and later |
6 |
24 |
Minimum 4, Maximum 6 |
|
|
7.3.x and later |
8 |
32 |
Minimum 4, Maximum 8 |
|
|
AMD VM.Standard.E5.Flex |
7.6.4 and later |
4 |
16 |
Minimum 4, Maximum 4 |
|
7.6.4 and later |
6 |
24 |
Minimum 4, Maximum 6 |
|
|
7.6.4 and later |
8 |
32 |
Minimum 4, Maximum 8 |
|
|
AMD VM.Standard.E6.Flex |
7.6.4 and later |
4 |
16 |
Minimum 4, Maximum 4 |
|
7.6.4 and later |
6 |
24 |
Minimum 4, Maximum 6 |
|
|
7.6.4 and later |
8 |
32 |
Minimum 4, Maximum 8 |
|
 Note |
We recommend using the Flex compute shapes. |
-
*SR-IOV mode is supported with Flex shapes from Version 7.4.x and later.
-
In OCI, 1 oCPU is equal to 2 vCPU.

Note
For the VM.Standard.A1.Flex shape, 1 oCPU is equivalent to 1 vCPU.
-
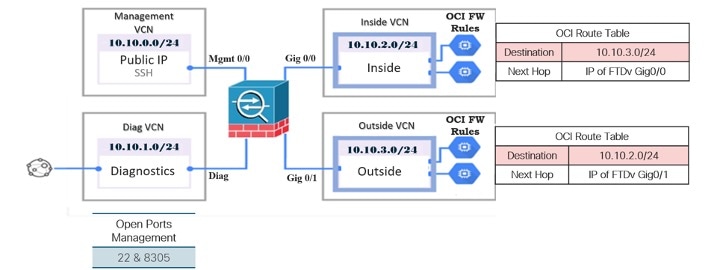
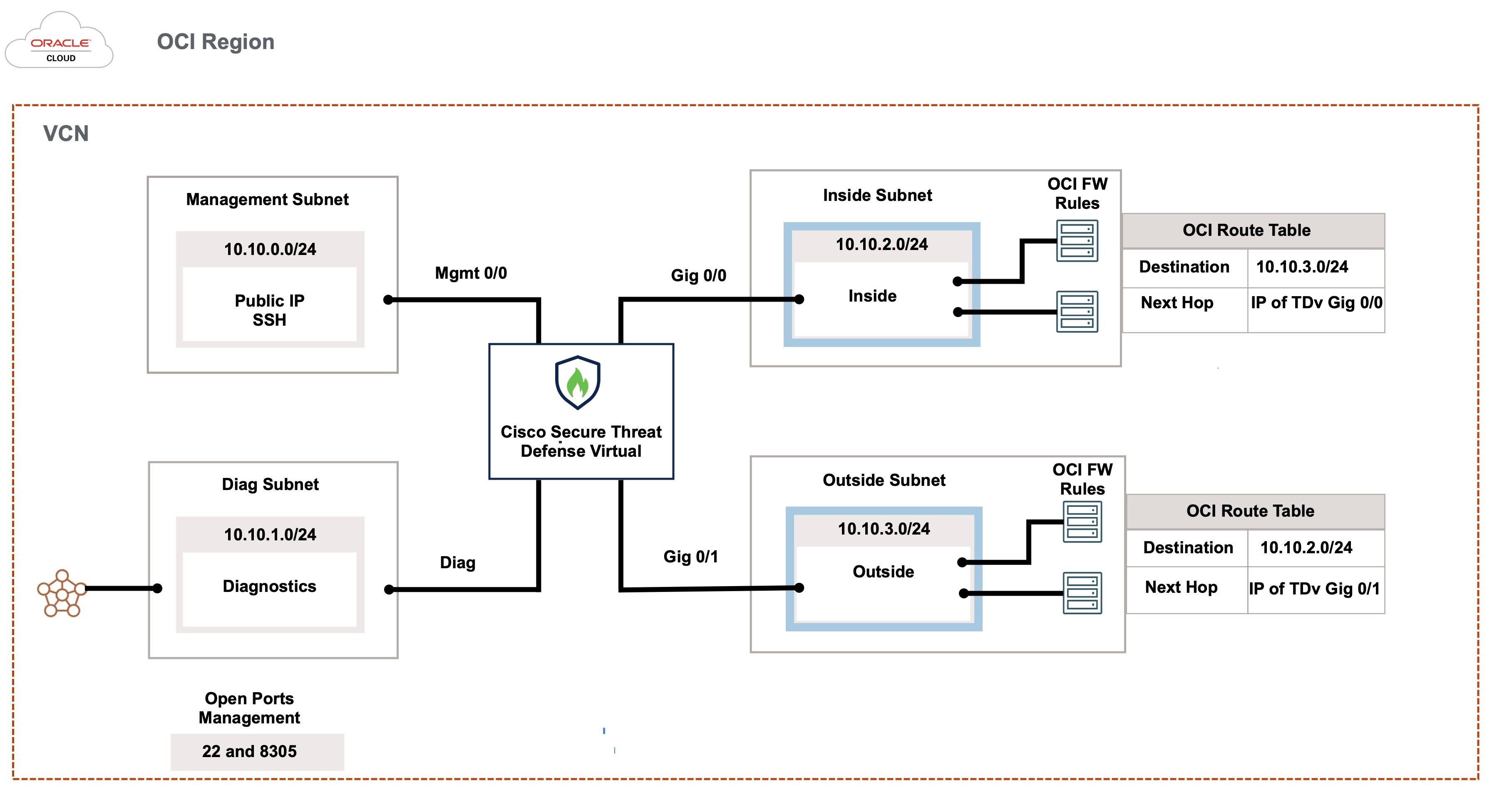
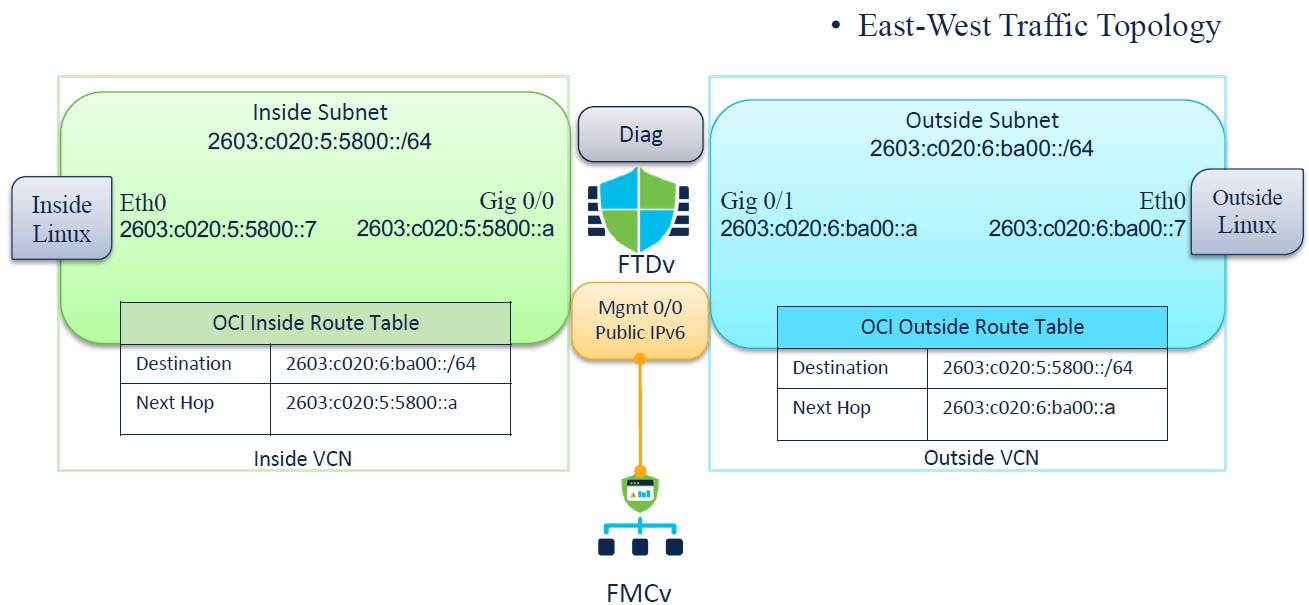
The Firewall Threat Defense Virtual requires a minimum of 4 interfaces.
Recommendations for using the OCI Compute shapes supported by version Firewall Threat Defense Virtual 7.3 and later.
-
OCI marketplace image version 7.3.0-69-v3 and later are compatible only with the OCI compute shapes of Firewall Threat Defense Virtual 7.3 and later.
-
You can use the OCI compute shapes supported by Firewall Threat Defense Virtual 7.3 and later only for new deployments.
-
OCI compute shapes version 7.3.0-69-v3 and later are not compatible with upgrading VMs that are deployed with Firewall Threat Defense Virtual using the OCI compute shape versions earlier to Firewall Threat Defense Virtual 7.3.
-
The billing will continue for the VM.DenseIO2.8 compute shape subscription, even after you shut down the instance. For more information, see OCI Documentation.
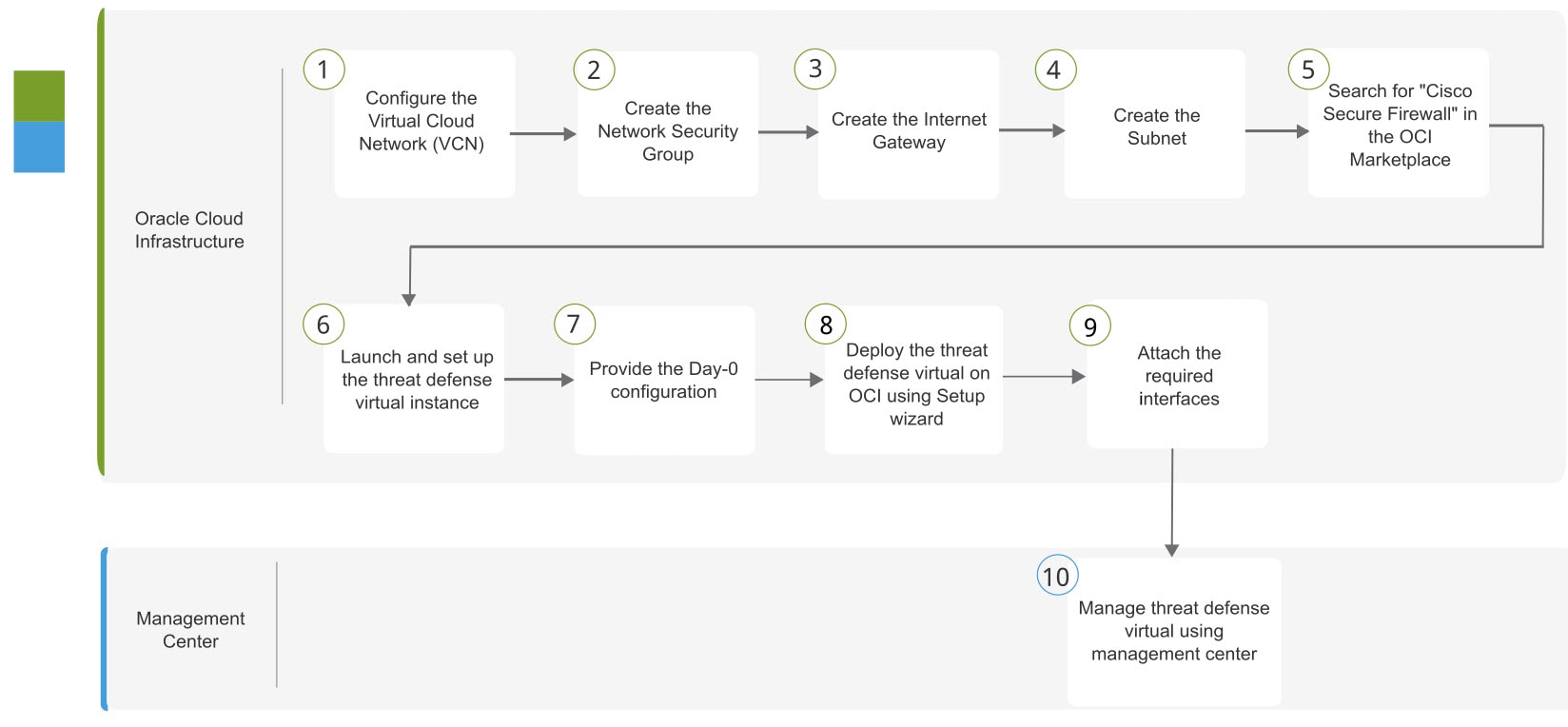
You create an account on OCI, launch a compute instance using the Cisco Firepower NGFW virtual firewall (NGFWv) offering on the Oracle Cloud Marketplace, and choose an OCI shape.

 Feedback
Feedback