About Secure Firewall Threat Defense Virtual with the Secure Firewall Device Manager
The Secure Firewall Threat Defense Virtual is the virtualized component of the Cisco NGFW solution. The Firewall Threat Defense Virtual provides next-generation firewall services, including stateful firewalling, routing, VPN, Next-Generation Intrusion Prevention System (NGIPS), Application Visibility and Control (AVC), URL filtering, and malware defense.
You can manage the Firewall Threat Defense Virtual using the Secure Firewall Device Manager, a web-based device setup wizard included on some of the Firewall Threat Defense models. The Firewall Device Manager lets you configure the basic features of the software that are most commonly used for small networks. It is especially designed for networks that include a single device or just a few, where you do not want to use a high-powered multiple-device manager to control a large network containing many of the Firewall Threat Defense devices.
If you are managing large numbers of devices, or if you want to use the more complex features and configurations that the Firewall Threat Defense allows, use the Firewall Management Center to configure your devices instead of the integrated Firewall Device Manager. See Managing the Secure Firewall Threat Defense Virtual with the Secure Firewall Management Center for more information.
For troubleshooting purposes, you can access the Firewall Threat Defense CLI using SSH on the Management interface, or you can connect to the Firewall Threat Defense from the Firewall Device Manager CLI.
Default Configuration
The Firewall Threat Defense Virtual default configuration puts the management interface and inside interface on the same subnet. You must have Internet connectivity on the management interface in order to use Smart Licensing and to obtain updates to system databases.
Thus, the default configuration is designed so that you can connect both the Management0-0 and GigabitEthernet0-1 (inside) to the same network on the virtual switch. The default management address uses the inside IP address as the gateway. Thus, the management interface routes through the inside interface, then through the outside interface, to get to the Internet.
You also have the option of attaching Management0-0 to a different subnet than the one used for the inside interface, as long as you use a network that has access to the Internet. Ensure that you configure the management interface IP address and gateway appropriately for the network.
The Firewall Threat Defense Virtual must be powered up on firstboot with at least four interfaces:
-
The first interface on the virtual machine is the management interface (Management0-0).
-
The second interface on the virtual machine is the diagnostic interface (Diagnostic0-0).
-
The third interface on the virtual machine (GigabitEthernet0-0) is the outside interface.
-
The fourth interface on the virtual machine (GigabitEthernet0-1) is the inside interface.
You can add up to six more interfaces for data traffic, for a total of eight data interfaces. For additional data interfaces, make sure that the Source Networks map to the correct Destination Networks, and that each data interface maps to a unique subnet or VLAN. See Configuring VMware Interfaces.
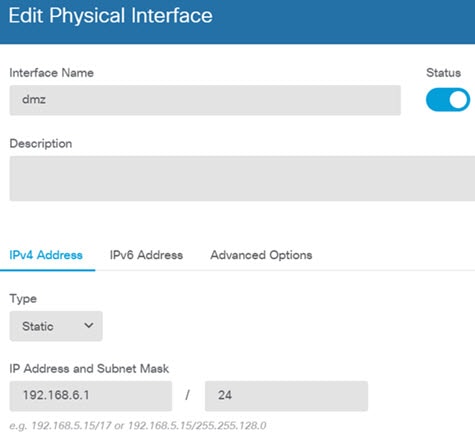
 ) for each interface to define the IP address and other settings.
) for each interface to define the IP address and other settings.
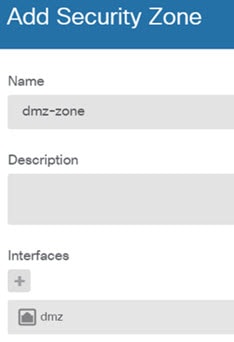
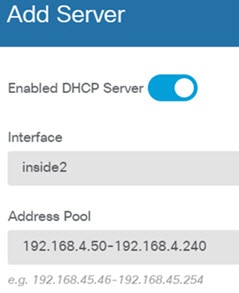
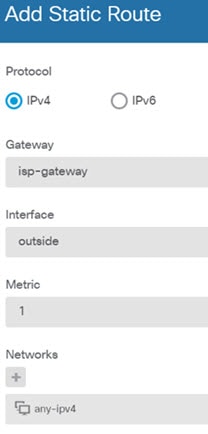
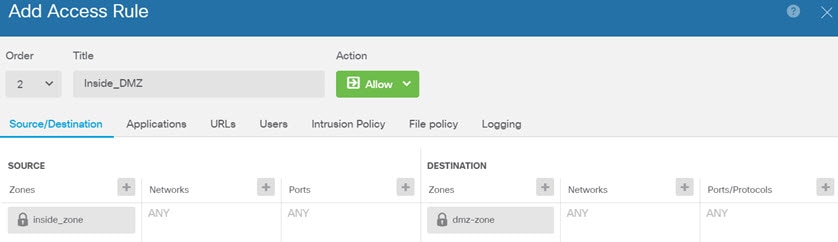
 ), to deploy your changes to the device.
), to deploy your changes to the device.
 Feedback
Feedback