Overview
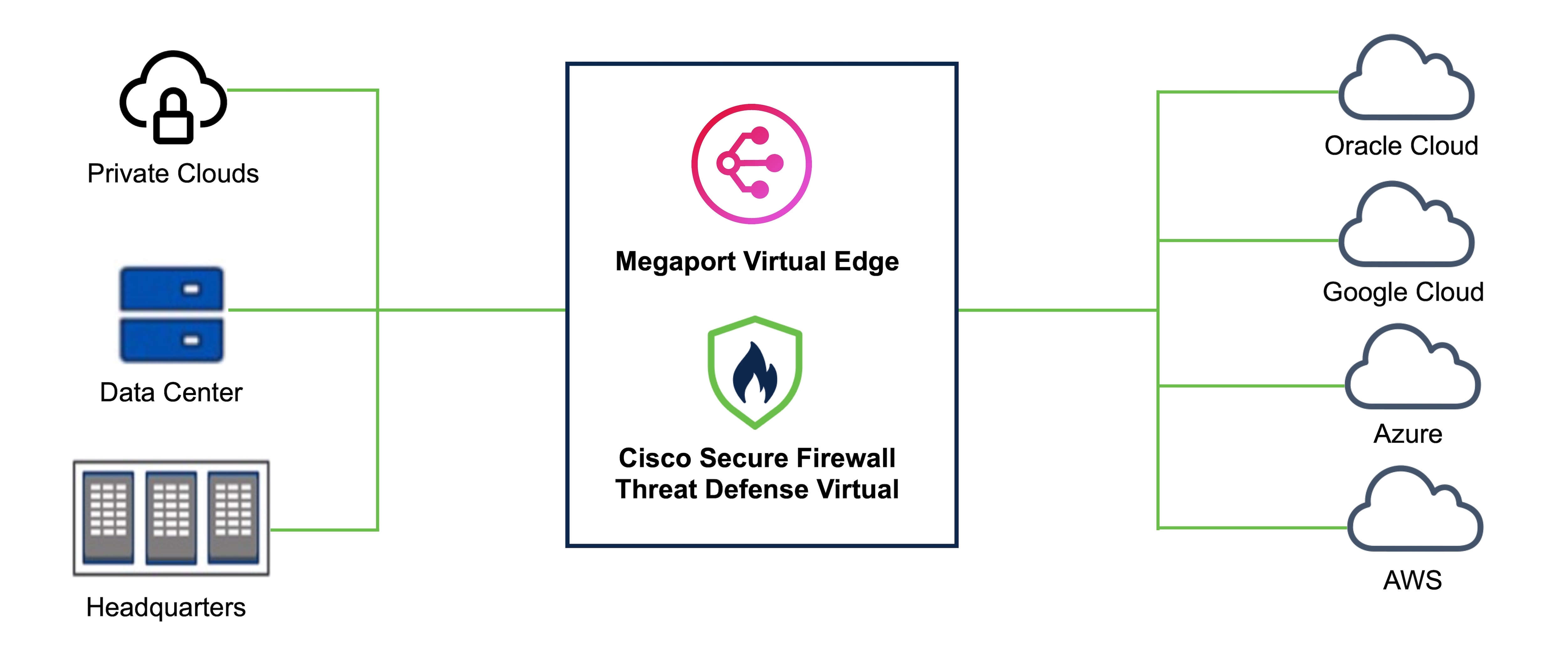
Business critical data can originate from diverse sources ranging from multiple public clouds, private clouds, and internal servers to a remote employee's device. Securing each data entity individually is time consuming and challenging due to lack of compliance between all the data points. With the increase in such use cases, you must be able to deploy the firewall quickly and securely at your network edge in a way that provides scalability and flexibility.
Megaport Virtual Edge (MVE) is an on-demand Network Function Virtualization (NFV) service on Megaport’s Software Defined Network (SDN), with a global reach of more than 280 cloud on-ramps and more than 800 data centers. The MVE enables you to secure branch-to-cloud, cloud-to-cloud, and branch-to-branch connectivity over private networks, Layer-2 networks with dedicated bandwidth, and low latency. From the Megaport portal, you can deploy SD-WAN gateways, virtual routers, transit gateways, and virtual firewalls at the network edge.
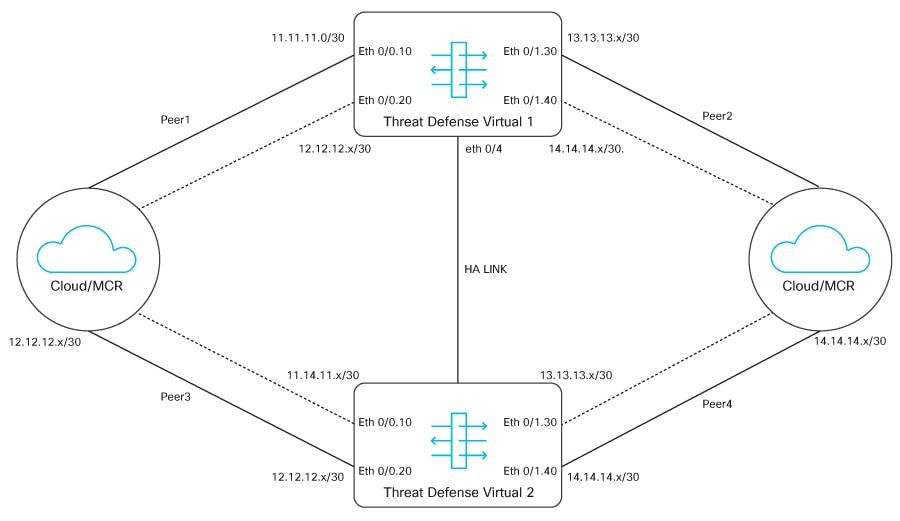
From Secure Firewall version 7.2.8, you can deploy the Threat Defense Virtual as an MVE that enables you to create a security service chain in your hybrid and multi-cloud workflows; and deploy a single point solution for personal devices, data centers, and the closest availability zones of your cloud platforms such as AWS, Azure, and GCP. This integration reduces data transit over potentially unsecure networks and allows you to seamlessly implement your security solution without worrying about problems with robustness and scalability.
Use the Megaport portal to deploy the Threat Defense Virtual and connect all your data centers to multi-cloud applications in a single place. All the data packets are routed using Megaport’s private global network. After deployment, the Threat Defense Virtual can be managed by either the on-box Firewall Device Manager, the Cloud-Delivered Firewall Management Center, or the On-Premises Firewall Management Center.

 Feedback
Feedback