Onboarding Overview
Cloud-Delivered Firewall Management Center is supported on Threat Defense Virtual devices running Secure Firewall versions 7.0.3,7.2.0, and later. To see all supported versions and product compatibility, see Secure Firewall Threat Defense Compatibility Guide for more information.
There are three different types of scenarios in which you onboard a threat defense virtual device to the cloud-delivered Firewall Management Center:
-
Onboard a new threat defense virtual device
-
Onboard a threat defense virtual device that is currently managed by the device manager

Note
If you onboard a device manager-managed device to the Cloud-Delivered Firewall Management Center, you can no longer manage the device with the device manager.
-
Onboard a threat defense virtual device that is currently managed by an on-prem management center. See Migrate Secure Firewall Threat Defense to Cloud for more information.

Note
The following scenarios occur when you either move or migrate a device to the Cloud-Delivered Firewall Management Center:
-
If you delete a device from an on-prem management center or Secure Firewall Threat Defense device manager to onboard to the Cloud-Delivered Firewall Management Center, the change of managers wipes any policies configured through the on-prem management center.
-
If you migrate a device from an on-prem management center to the Cloud-Delivered Firewall Management Center, the device retains the majority of your previously configured policies.
If you do not know if your device is already managed by an alternative manager, use the show managers command on the CLI.
-
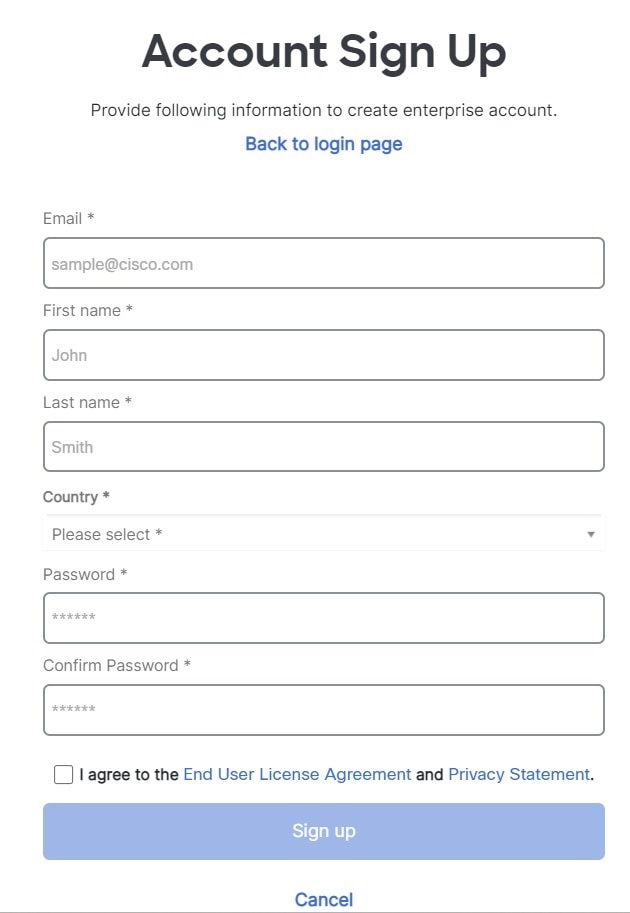
This guide provides information on the basics of managing threat Defense Virtual using Cloud-Delivered Firewall Management Center. For more detailed information on CDO, see Cisco Defense Orchestrator.

 ).
).

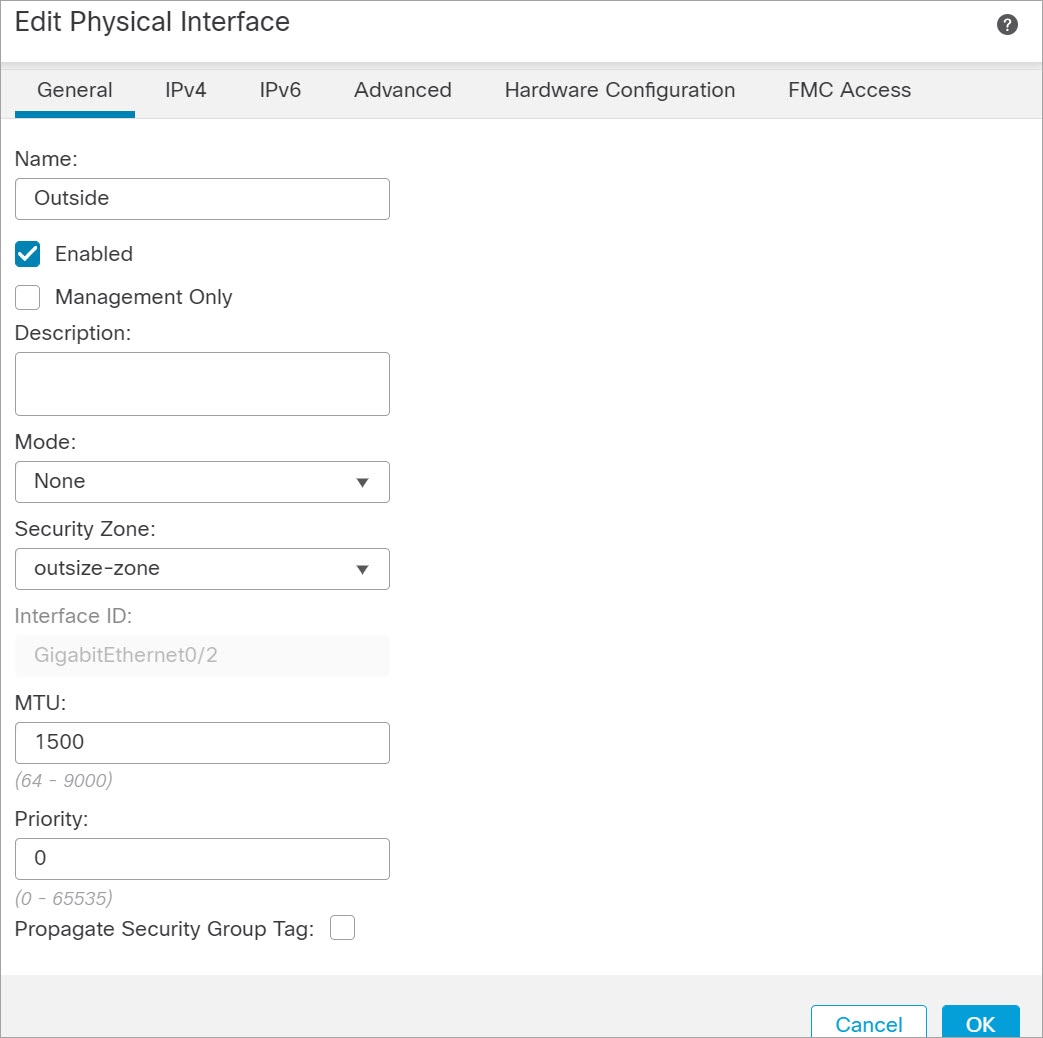
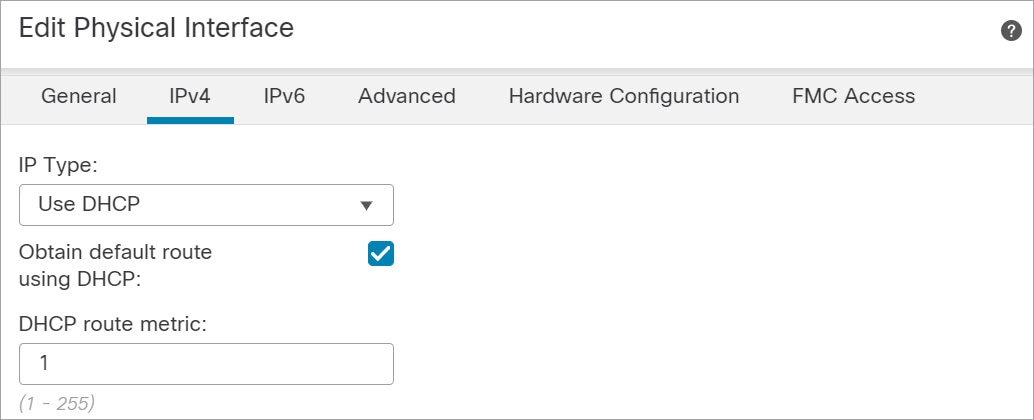
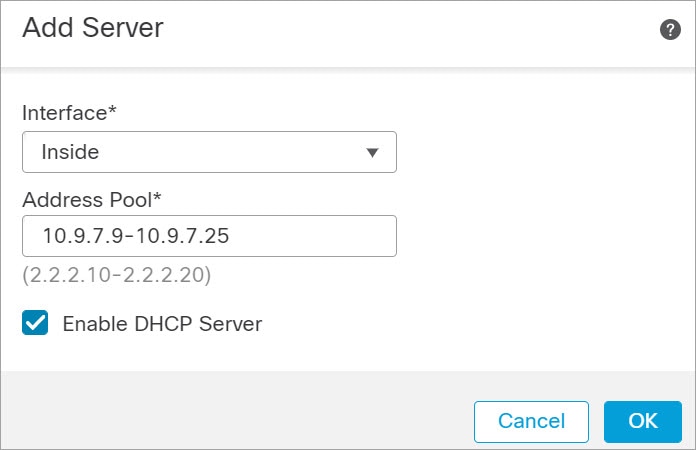
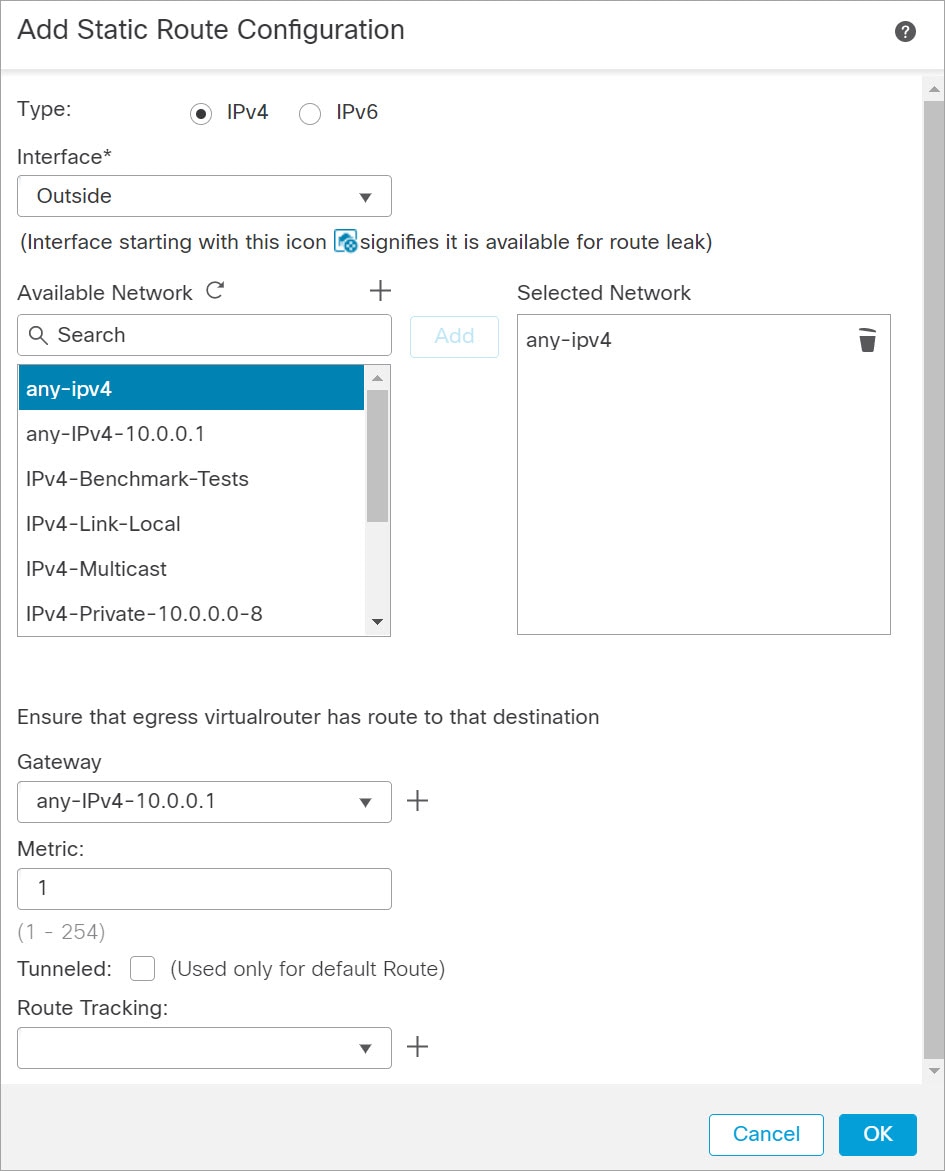
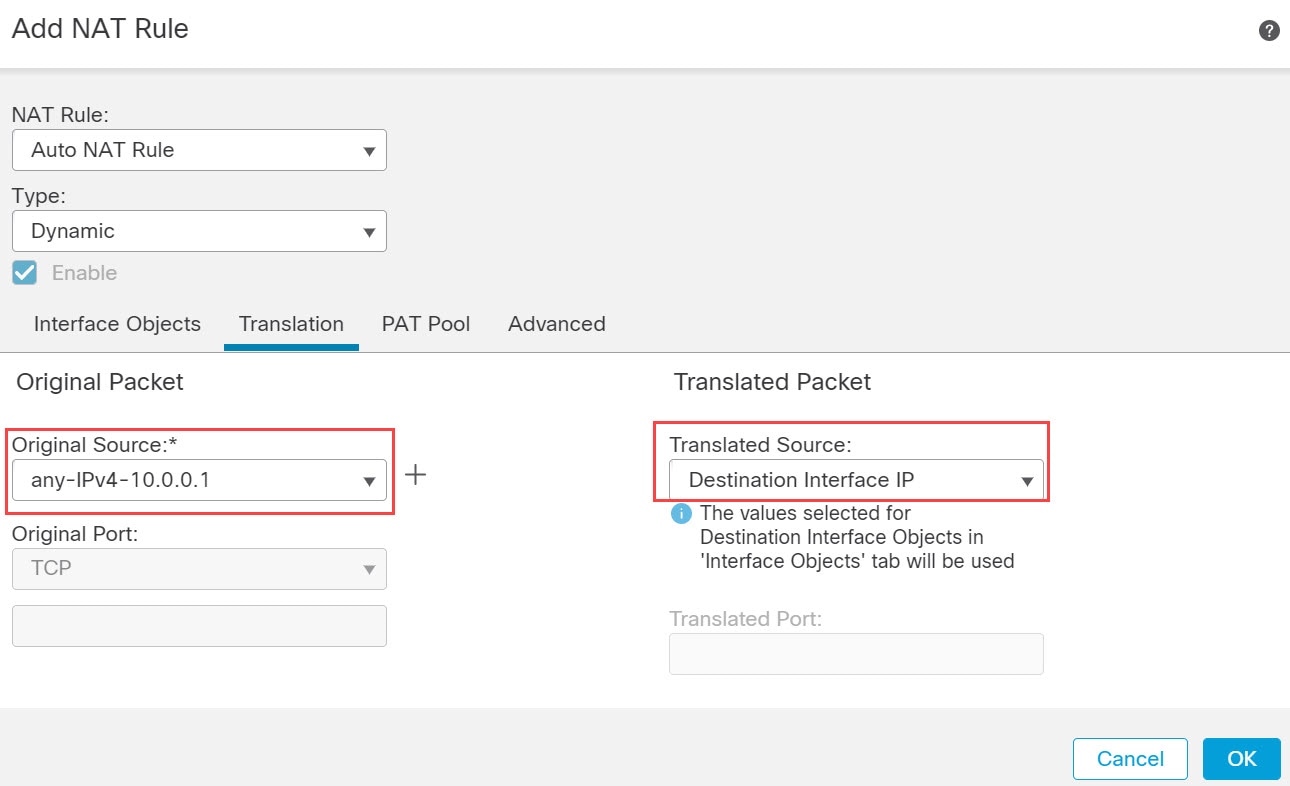
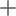 )
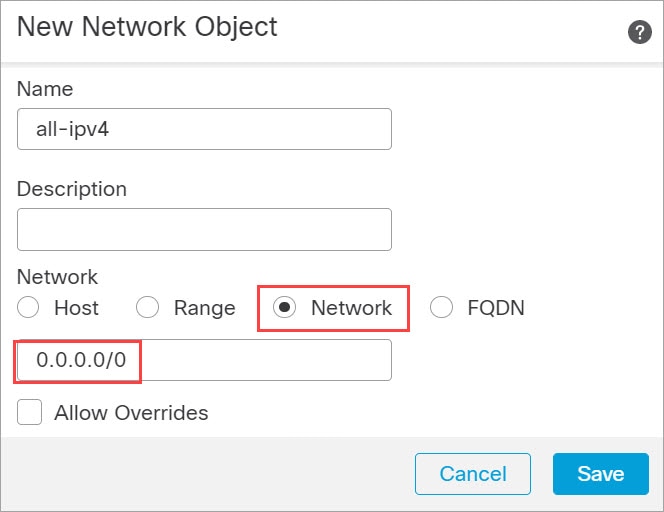
)
 Feedback
Feedback