Auto Scale Solution
The following sections describe how the components of the Auto Scale solution work for the Firewall Threat Defense Virtual on GCP.
Overview
Firewall Threat Defense Virtual Auto Scale for GCP is a complete serverless implementation that makes use of serverless infrastructure provided by GCP (Cloud Functions, Load Balancers, Pub/Sub, Instance Groups, etc.).
Some of the key features of the Firewall Threat Defense Virtual Auto Scale for GCP implementation include:
-
GCP Deployment Manager template-based deployment.
-
Support for scaling metrics based on CPU utilization..
-
Support for Firewall Threat Defense Virtual deployment and multi-availability zones.
-
Support for automatic registration and de-registration of Firewall Threat Defense Virtual.
-
Completely automated configuration automatically applied to scaled-out Firewall Threat Defense Virtual instances.
-
Support for automatic application of NAT policy, access policy, and routes, to Firewall Threat Defense Virtual.
-
Support for Load Balancers and multi-availability zones.
-
Support for Firewall Management Center Virtual on other platforms.
-
Cisco provides an Auto Scale for GCP deployment package to facilitate the deployment.
-
Threat Defense Virtual instances responds to health probes with loopback interface.
Guidelines and Limitations
-
Only IPv4 is supported.
-
Licensing - Only BYOL is supported. PAYG licensing is not supported.
-
Device functionality errors are not displayed in the logs.
-
The maximum number of devices supported is 25. This is the maximum limit in a Firewall Management Center Virtual instance.
-
On all Secure Firewall versions, you can use the provided templates to deploy the Threat Defense Virtual auto scale solution. The Threat Defense Virtual instances are deployed with a minimum of 4 interfaces - 1 management, 1 diagnostic, and 2 data interfaces.
From Secure Firewall version 7.4.1, you can also deploy the Threat Defense Virtual without the diagnostic interface. In this scenario also, the deployment is done with a minimum of 4 interfaces - 1 management, and 3 data interfaces. To do this, modify the template parameters - diagFirewallRule, diagSubnetworkName, diagVpcName, and withDiagnostic, as per the description given in Input Parameters.
-
Cold standby or Snapshot methods to reduce scale-out time are not supported.
-
Schedule based scaling is not supported.
-
Auto Scaling based on Average Memory Utilization is not supported.
-
Scale-In/Scale-Out may decrease/increase the number of instances by more than 1. However, the Firewall Threat Defense Virtual instances will only deregister/register on the Firewall Management Center Virtual sequentially, that is, one by one.
-
During scale-in, there is a connection draining time of 300s. You can also manually configure the draining time to a required period.
-
The external Load Balancer is created by the template that is provided. Customizing DNS requirements of the Load Balancer’s public IP is not supported.
-
Users have to fit their existing infrastructure into the sandwich model of implementation.
-
For details on errors faced during the scale-out and scale-in process, analyze the logs of the Cloud Functions.
-
NAT, security policies attached to device group, and static routes, are applied to the newly created Firewall Threat Defense.
-
If you are deploying the solution for more than 1 Firewall Threat Defense Virtual, then the deployment time will increase as the Firewall Management Center Virtual can handle only one registration request at a time. Deployment time also increases when scaling out adds more than one Firewall Threat Defense Virtual instance. Currently, all registrations and de-registrations are sequential.
-
Device Group, NAT rules, and network objects, have to be created in Firewall Management Center Virtual before Auto Scaling is initiated. Note that the ILB and ELB IPs are only available after deploying the solution. So, you can create dummy objects and update the objects after the actual IPs are obtained.
Auto Scale Use Case
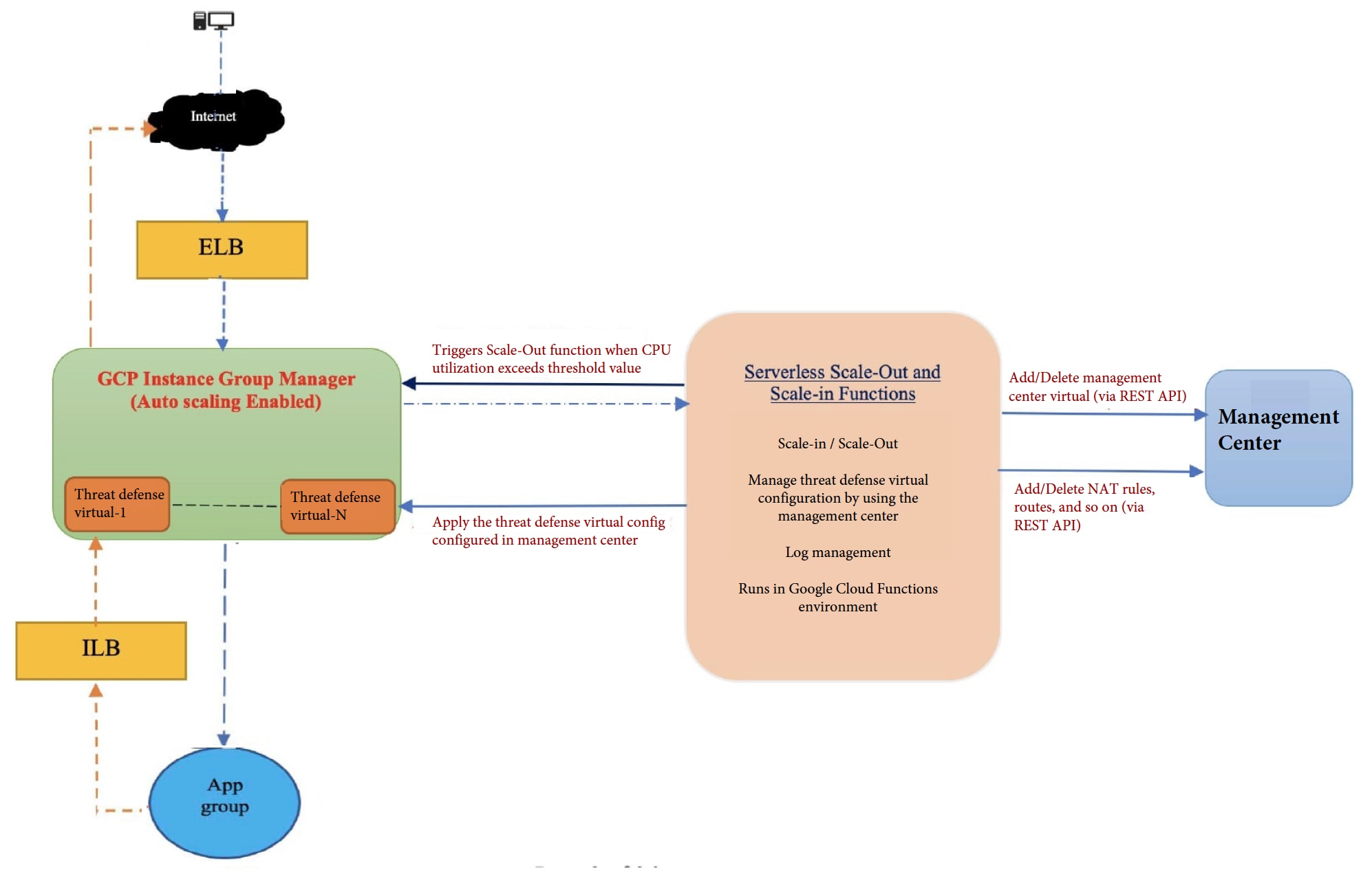
The Firewall Threat Defense Virtual Auto Scale for GCP is an automated horizontal scaling solution that positions a Firewall Threat Defense Virtual instance group sandwiched between a GCP Internal load balancer (ILB) and a GCP External load balancer (ELB).
-
The ELB distributes traffic from the Internet to Firewall Threat Defense Virtual instances in the instance group; the Firewall Threat Defense Virtual then forwards traffic to the application.
-
The ILB distributes outbound Internet traffic from an application to Firewall Threat Defense Virtual instances in the instance group; the Firewall Threat Defense Virtual then forwards traffic to the Internet.
-
A network packet will never pass through both (internal & external) load balancers in a single connection.
-
The number of Firewall Threat Defense Virtual instances in the scale set will be scaled and configured automatically based on load conditions.

On all Secure Firewall versions, you can use the provided templates to deploy the Threat Defense Virtual auto scale solution. The Threat Defense Virtual instances are deployed with a minimum of 4 interfaces - 1 management, 1 diagnostic, and 2 data interfaces.
From Secure Firewall version 7.4.1, you can also deploy the Threat Defense Virtual without the diagnostic interface. In this scenario also, the deployment is done with a minimum of 4 interfaces - 1 management, and 3 data interfaces. To do this, modify the template parameters - diagFirewallRule, diagSubnetworkName, diagVpcName, and withDiagnostic, as per the description given in Input Parameters.
Scope
This document covers the detailed procedures to deploy the serverless components for the Firewall Threat Defense Virtual Auto Scale for GCP solution.
 Important |
|




 Feedback
Feedback