Introduction to Threat Defense Virtual in Azure Virtual WAN
Microsoft Azure Virtual WAN employs a 'hub-and-spoke' architecture to manage traffic across various virtual networks and branch locations. Within the Azure Virtual WAN, integrating Threat Defense Virtual with the Azure Virtual hub facilitates the efficient management and inspection of traffic originating from your organization's on-premises (spoke) networks (like headquarters, branches, and remote users) as it passes through the hub to access Vnets on your Azure network. This integration facilitates the management, inspection, filtering, and routing of network traffic through dedicated connectivity channels using Threat Defense Virtual functioning as firewall.
 Note |
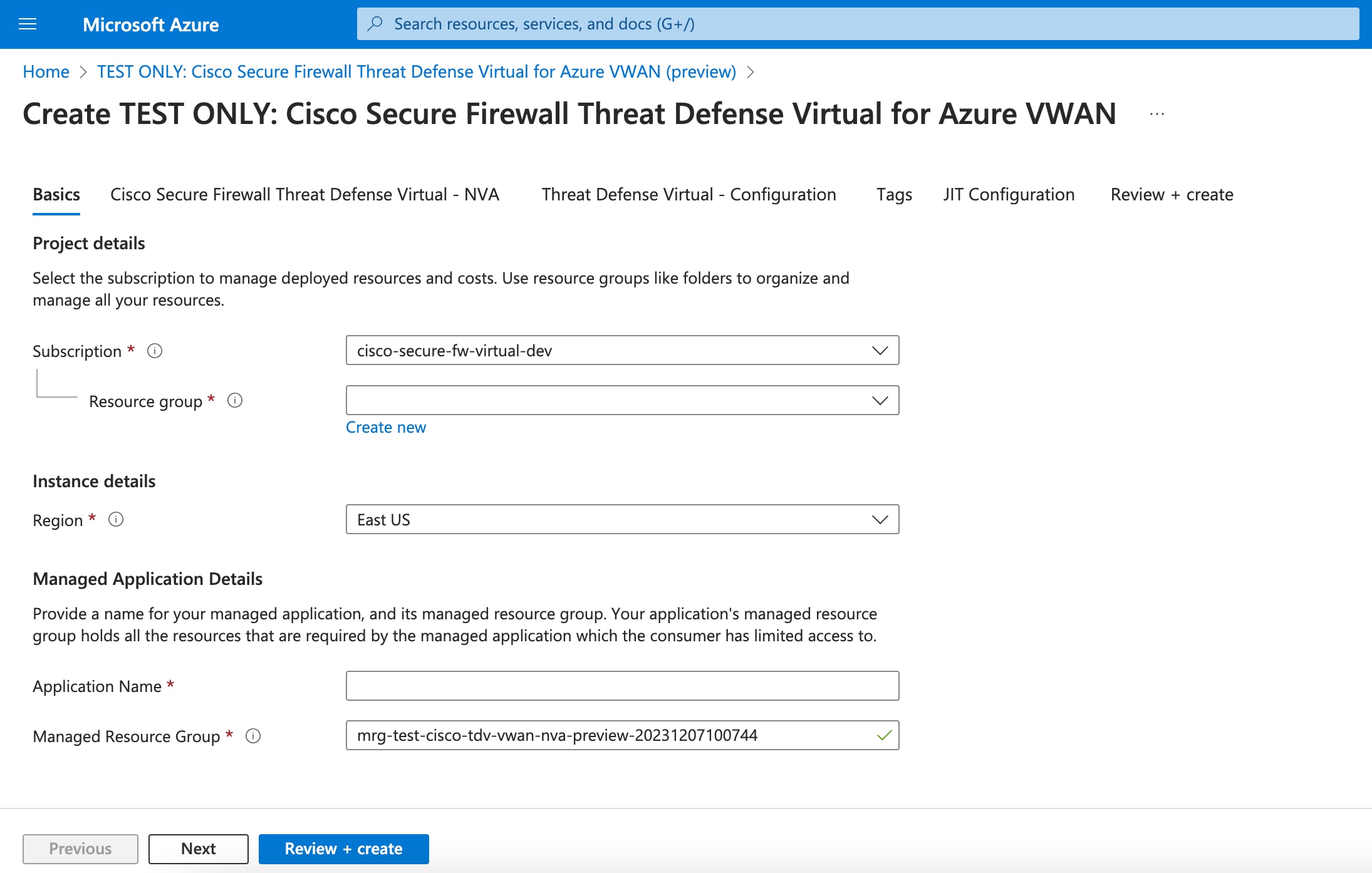
Threat Defense Virtual deployment model with only three interfaces is supported by Azure Virtual WAN. |
Deploying Threat Defense Virtual on the Azure Virtual WAN hub offers several advantages, including:
-
Eliminating the need to implement a firewall solution in each spoke connected to the hub.
-
Leveraging Azure’s inbuilt capabilities of Internal Load Balancer (ILB).
-
Scaling of instances with predefined configuration during deployment.
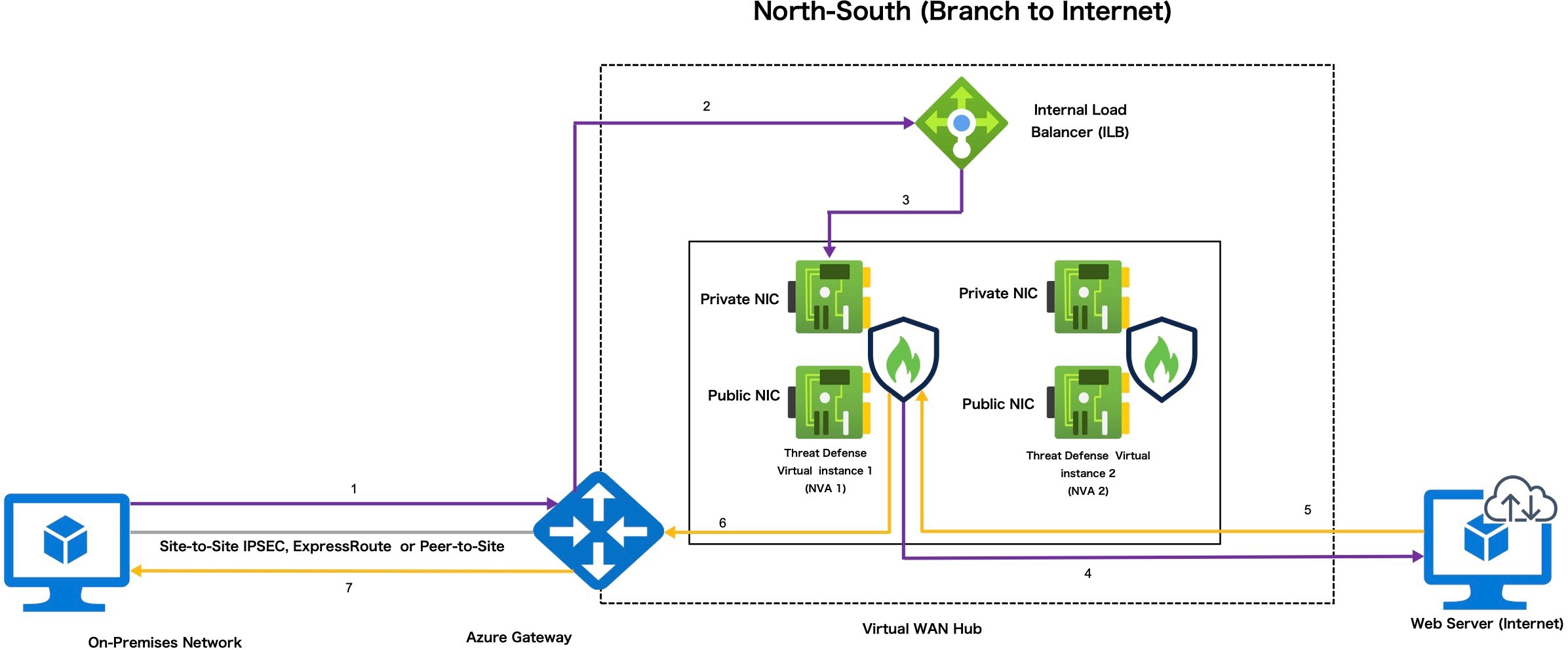
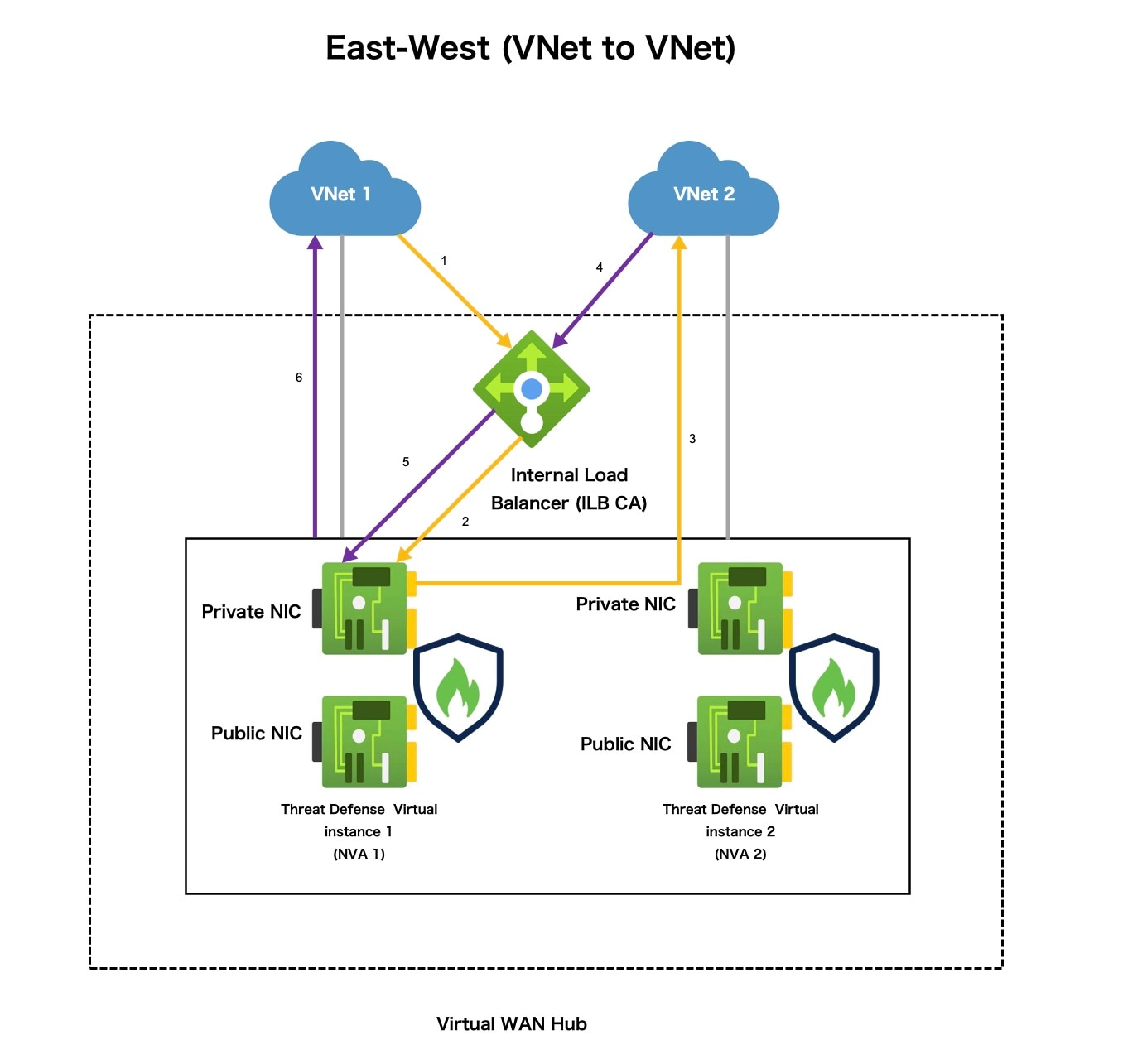
Traffic Routing Through Threat Defense Virtual on Azure Virtual WAN
Routing Traffic Methods in Azure Virtual WAN
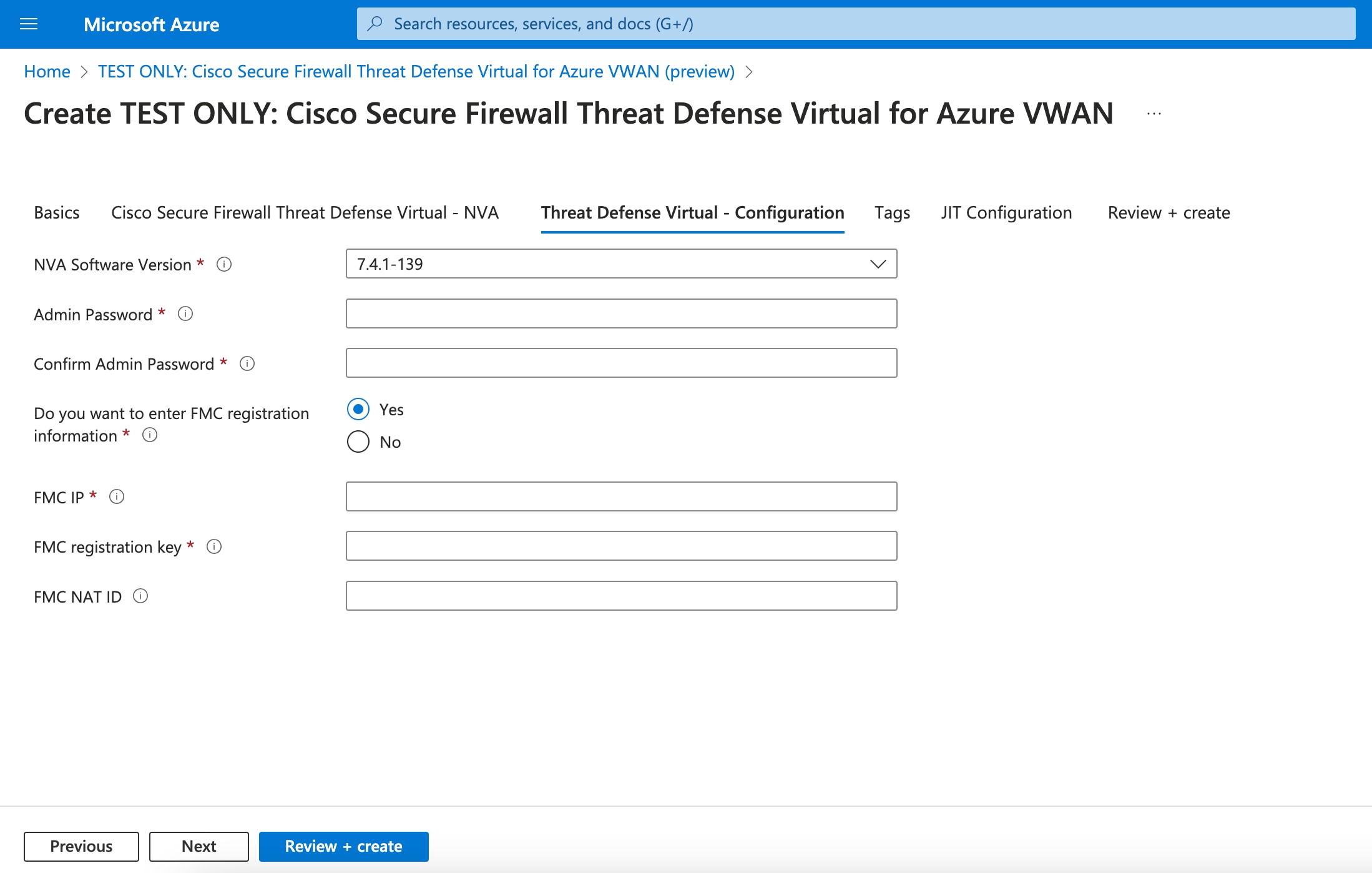
Azure Virtual WAN offers Border Gateway Protocol (BGP), a dynamic routing protocol that helps determine the best route to send traffic between different Azure networks while constantly updating and sharing the routing table. The virtual WAN hub provides a set of BGP endpoints (for High Availability) and Autonomous System Number (ASN), which you must configure as BGP neighbors for Threat Defense Virtual in the management center.
You can also use the static routing method to manually configure routes in the Threat Defense Virtual.
For more information on routing in Azure, see About BGP and VPN Gateway in the Azure documentation.
Routing Intent
Routing Intent is a routing ability in the Azure Virtual WAN hub that simplifies the process of forwarding Internet-bound and Private traffic to the Threat Defense Virtual firewall deployed in the hub for inspection.
For more information, see Routing Intent in the Azure documentation.
 Feedback
Feedback