Overview
You can deploy the Threat Defense Virtual using Microsoft Hyper-V, from Release 10.0.0.
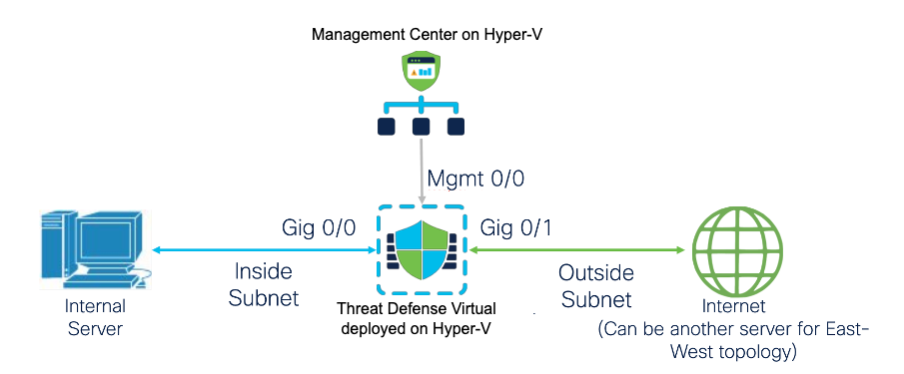
The following subnets are set up in Hyper-V for the Threat Defense Virtual:
Management Subnet → For Management Center (Mgmt 0/0).
Inside Subnet → Internal network (Gig 0/0).
Outside Subnet → External or Internet-facing network (Gig 0/1).
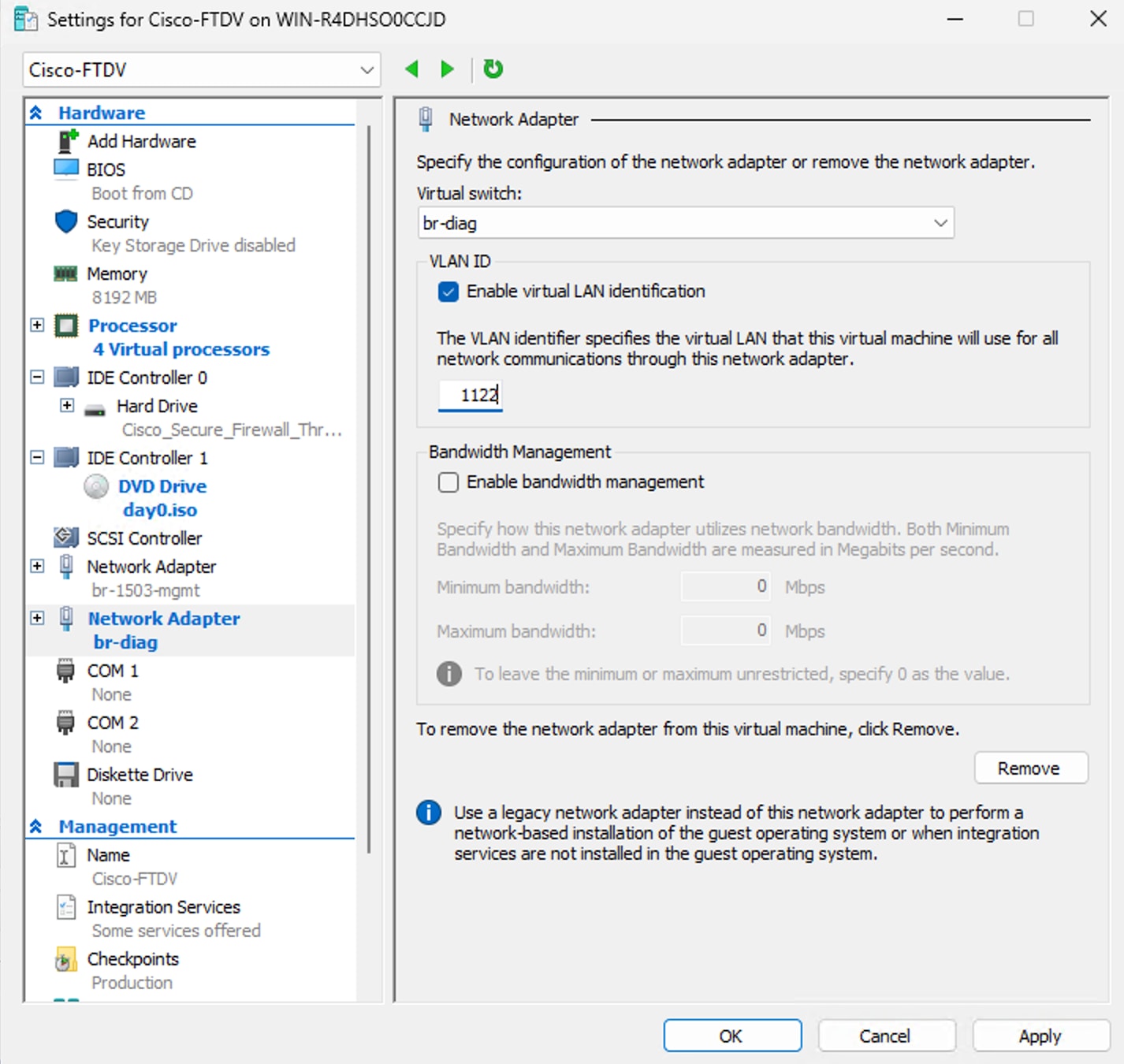
Diagnostic Subnet -> For diagnostics and reporting, cannot be used for traffic.
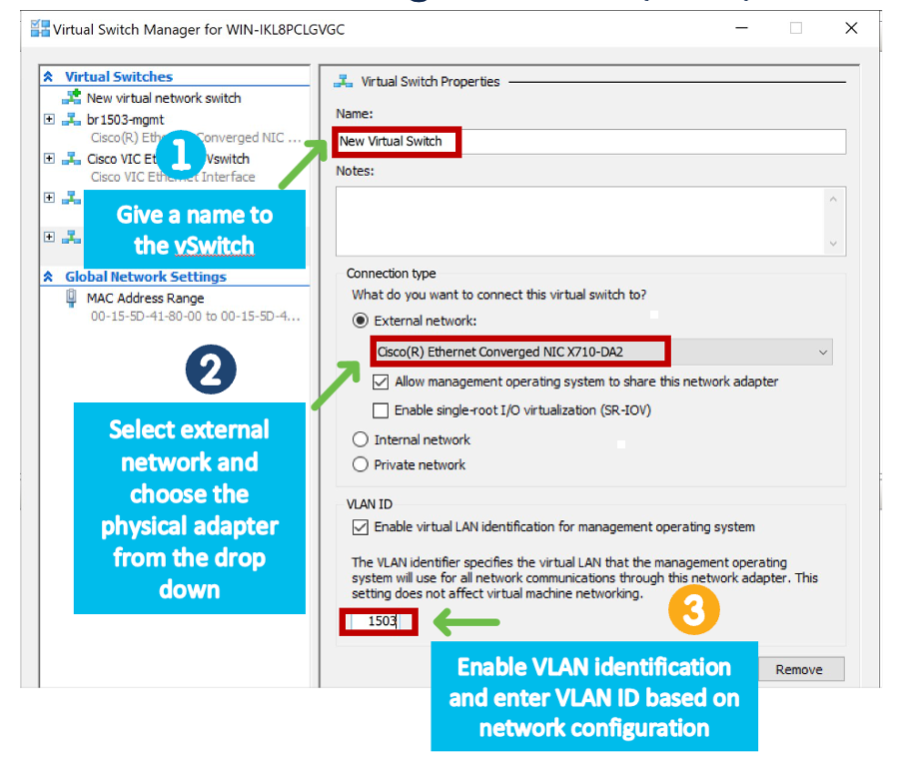
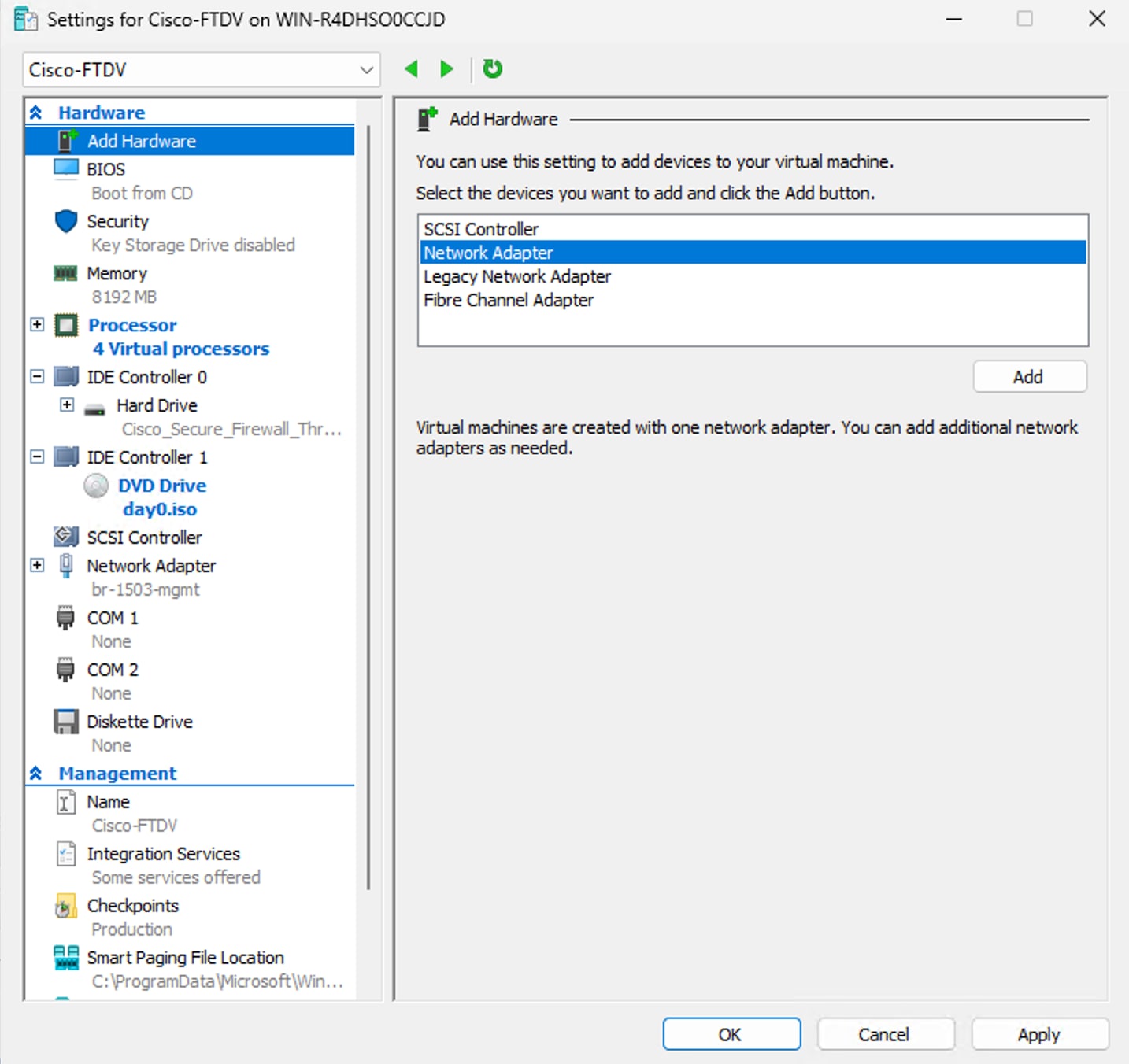
These are created using Hyper-V virtual switches.
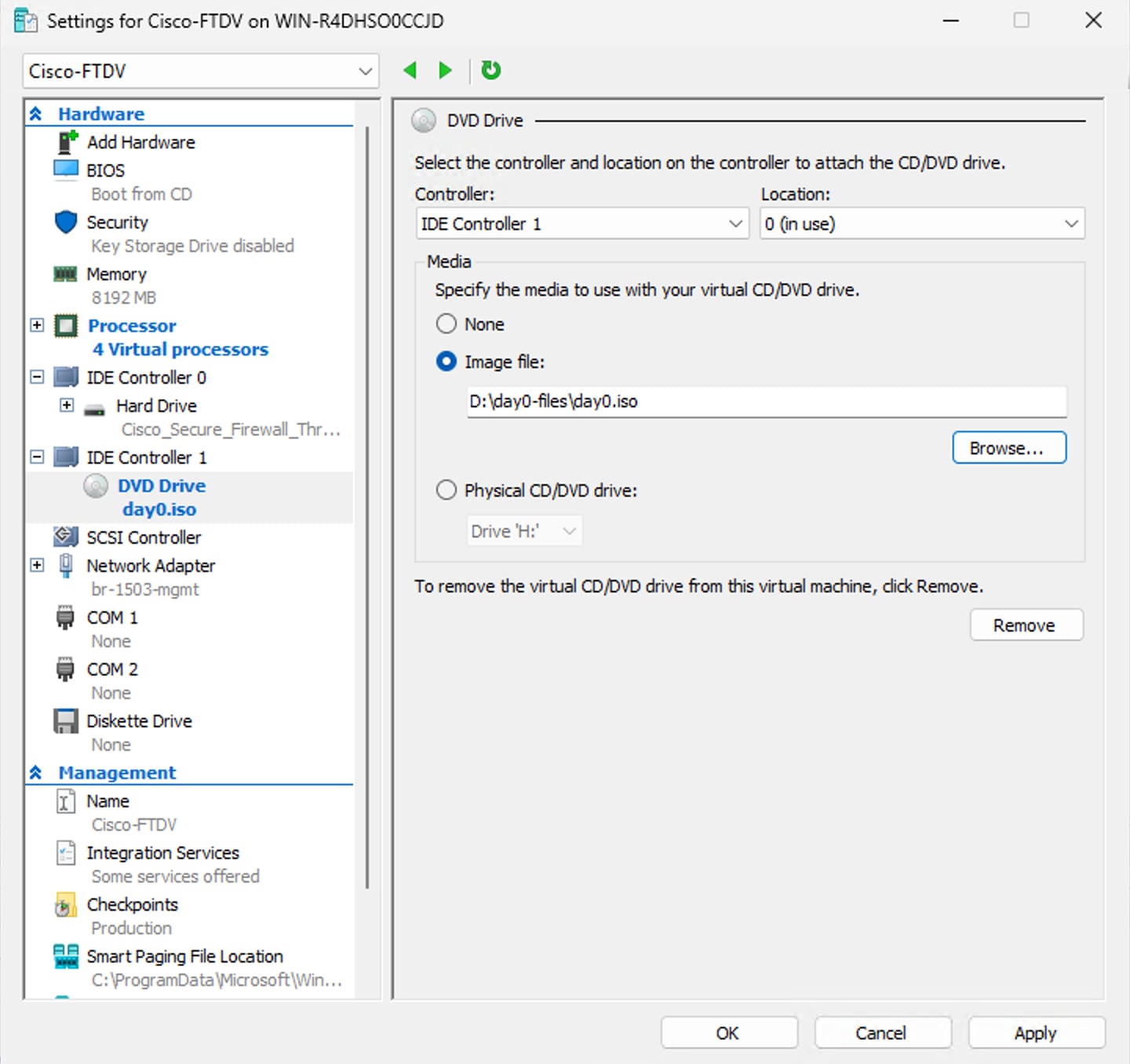
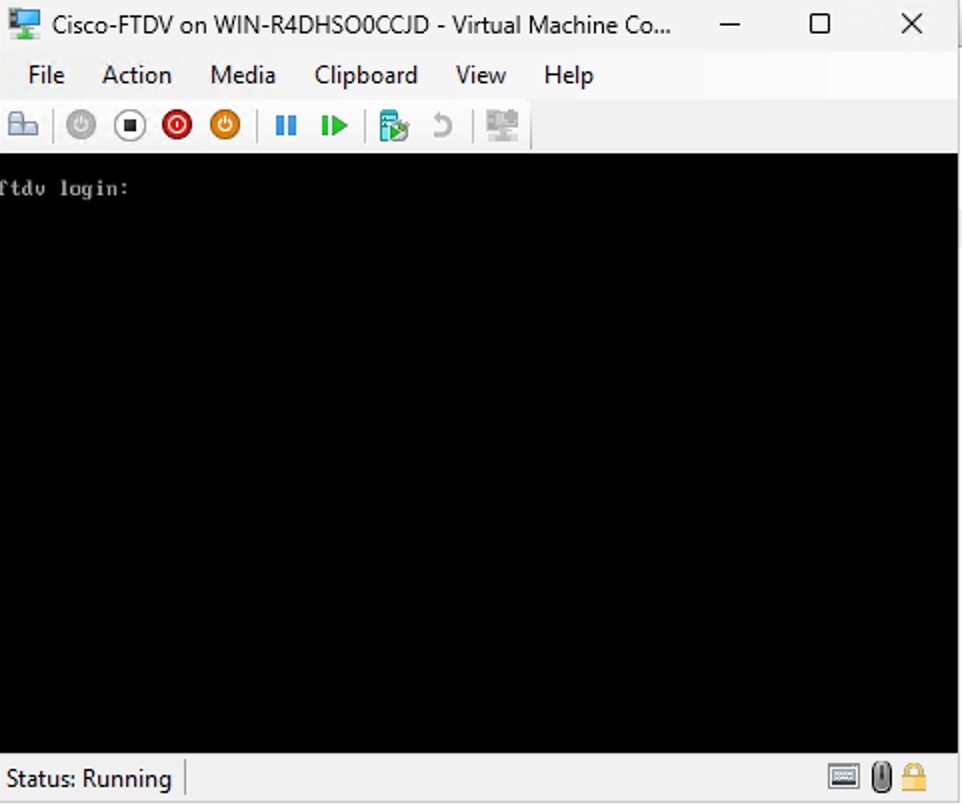
The following figure shows the Threat Defense Virtual deployed on Hyper-V, managed by Management Center.


 Feedback
Feedback