Default configuration
When you boot up the router for the first time, the router looks for a default file name-the PID of the router. For example, C8161-G2 looks for a file named C8161-G2.cfg. The Cisco 8100 Series Secure Routers looks for this file before finding the standard files-router-confg or the ciscortr.cfg.
The C8161-G2 looks for a file named C8161-G2.cfg file in the bootflash. If the file is not found in the bootflash, the router then looks for the standard files-router-confg and ciscortr.cfg. If none of the files are found, the router then checks for any inserted USB that may have stored these files in the same particular order.
 Note |
If there is a configuration file with the PID as its name in an inserted USB, but one of the standard files are in bootflash, the system finds the standard file for use. |
Use the show running-config command to view the initial configuration, as shown in the following example:
Router# show running-config
Building configuration...
Current configuration : 6118 bytes
!
! Last configuration change at 18:09:54 UTC Tue Sep 9 2025
!
version 17.18
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform resource service-plane-heavy
!
hostname Router
!
boot-start-marker
boot-end-marker
!
!
aaa new-model
!
!
!
!
aaa session-id common
!
!
!
!
!
!
!
!
!
!
login on-success log
!
!
!
!
!
!
!
subscriber templating
!
!
!
!
!
!
!
!
!
!
!
!
!
product-analytics
!
!
crypto pki trustpoint TP-self-signed-303776382
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-303776382
revocation-check none
rsakeypair TP-self-signed-303776382
hash sha512
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
hash sha512
!
!
crypto pki certificate chain TP-self-signed-303776382
certificate self-signed 01
3082032E 30820216 A0030201 02020101 300D0609 2A864886 F70D0101 0D050030
30312E30 2C060355 04030C25 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 33303337 37363338 32301E17 0D323530 38323730 36303931
315A170D 33353038 32373036 30393131 5A303031 2E302C06 03550403 0C25494F
532D5365 6C662D53 69676E65 642D4365 72746966 69636174 652D3330 33373736
33383230 82012230 0D06092A 864886F7 0D010101 05000382 010F0030 82010A02
82010100 B2521F68 C09E24B1 89E40B24 853626B1 7F3F531D 6D02C649 66F1BD76
8D5E402E 96D34B24 94E7FFE6 3CDFE83B C5FF2734 BCB5C95B 96A8470F F73A5DD4
7F5CEF51 17BF69F9 61E8921D 4DB29641 DEA5DC94 DEEEF577 F8BC38AF 5EDA4DFD
7BEC6B6F 22B387E9 228C26B8 24E6874F 15E37DDE 2DACAB5B CE9145A7 D927CC5F
E406C5FB E0644A0A 5DD223AA D7BE44A3 9BECB90B 770B033E 31F3D7F3 818BF19A
7249E78C F746D6B0 E2ECD2CC C6338E9D 67292CC0 2B4C0C5E 2FBE57A0 CCBBDF1B
C0732BC7 55D55A5D AC2C8511 F9AEE8DE F36678A2 08B4693D 5325AB35 A67724F8
CCC604BA C0D2BB14 E26CC9C4 50B9818E F311FE57 F397FD1A FCAE2041 A1B2DDEC
79EB45C1 02030100 01A35330 51301D06 03551D0E 04160414 0AB72B54 4F5A1C91
6B4D0922 B5EB5529 24638466 301F0603 551D2304 18301680 140AB72B 544F5A1C
916B4D09 22B5EB55 29246384 66300F06 03551D13 0101FF04 05300301 01FF300D
06092A86 4886F70D 01010D05 00038201 0100A9D5 BAE37659 4226FF9A 59835CAC
9ECC9170 BCCC78AE EE48674A DFCF359C AD363065 61706435 50E96ACB 82B30090
6A417C53 4E7E9000 77AAAC84 887A5006 E1DE278B 0F3B59DF 306A6240 7344AE5B
C8B75372 EDEB27A4 E4497541 D67ECD79 97F5910A 17181502 CE1417BE 867C2151
8CBE3380 8BE23C6A BC633AAB 252491A5 E3B40685 F5AE5AFE 3184884D AD0AEA0F
BA2EC3D7 3C8BF748 84BFF882 99DA3471 11BE6758 29144FC9 18CAE5FB 2399743C
30FC8AFC 84E61852 BAEA0CD7 14B13BC3 67D58D25 5408266B 2A442399 926169A0
4ADBE01B F7F7F790 075B37D7 C2B9EDCF 3427C015 9401B552 3DE68D26 88B24C19
FDF935A7 9CB0CD21 273FBF2C 77BC31CF 080F
quit
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030
82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D
CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520
1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE
4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC
7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188
68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7
C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191
C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44
DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201
06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85
4B3D31E5 1B3E6A17 606AF333 3D3B4C73 E8300D06 092A8648 86F70D01 010B0500
03820101 00507F24 D3932A66 86025D9F E838AE5C 6D4DF6B0 49631C78 240DA905
604EDCDE FF4FED2B 77FC460E CD636FDB DD44681E 3A5673AB 9093D3B1 6C9E3D8B
D98987BF E40CBD9E 1AECA0C2 2189BB5C 8FA85686 CD98B646 5575B146 8DFC66A8
467A3DF4 4D565700 6ADF0F0D CF835015 3C04FF7C 21E878AC 11BA9CD2 55A9232C
7CA7B7E6 C1AF74F6 152E99B7 B1FCF9BB E973DE7F 5BDDEB86 C71E3B49 1765308B
5FB0DA06 B92AFE7F 494E8A9E 07B85737 F3A58BE1 1A48A229 C37C1E69 39F08678
80DDCD16 D6BACECA EEBC7CF9 8428787B 35202CDC 60E4616A B623CDBD 230E3AFB
418616A9 4093E049 4D10AB75 27E86F73 932E35B5 8862FDAE 0275156F 719BB2F0
D697DF7F 28
quit
!
!
!
!
!
!
!
!
!
diagnostic bootup level minimal
!
license udi pid C8161-G2 sn FCW2832Y4YB
memory free low-watermark processor 63127
!
spanning-tree extend system-id
!
!
!
!
redundancy
mode none
!
!
!
!
!
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/0/1
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/1/0
!
interface GigabitEthernet0/1/1
!
interface GigabitEthernet0/1/2
!
interface GigabitEthernet0/1/3
!
interface GigabitEthernet0/1/4
!
interface GigabitEthernet0/1/5
!
interface GigabitEthernet0/1/6
switchport
!
interface GigabitEthernet0/1/7
switchport
!
interface Vlan1
no ip address
!
router rip
version 2
network 10.0.0.0
network 192.168.1.0
no auto-summary
!
ip forward-protocol nd
ip forward-protocol udp
ip http server
ip http authentication local
ip http secure-server
!
ip ssh bulk-mode 131072
!
!
!
!
!
!
control-plane
!
!
mgcp behavior rsip-range tgcp-only
mgcp behavior comedia-role none
mgcp behavior comedia-check-media-src disable
mgcp behavior comedia-sdp-force disable
!
mgcp profile default
!
!
!
!
!
!
line con 0
activation-character 13
stopbits 1
line vty 0 4
activation-character 13
transport input ssh
line vty 5 14
activation-character 13
transport input ssh
!
!
!
!
!
!
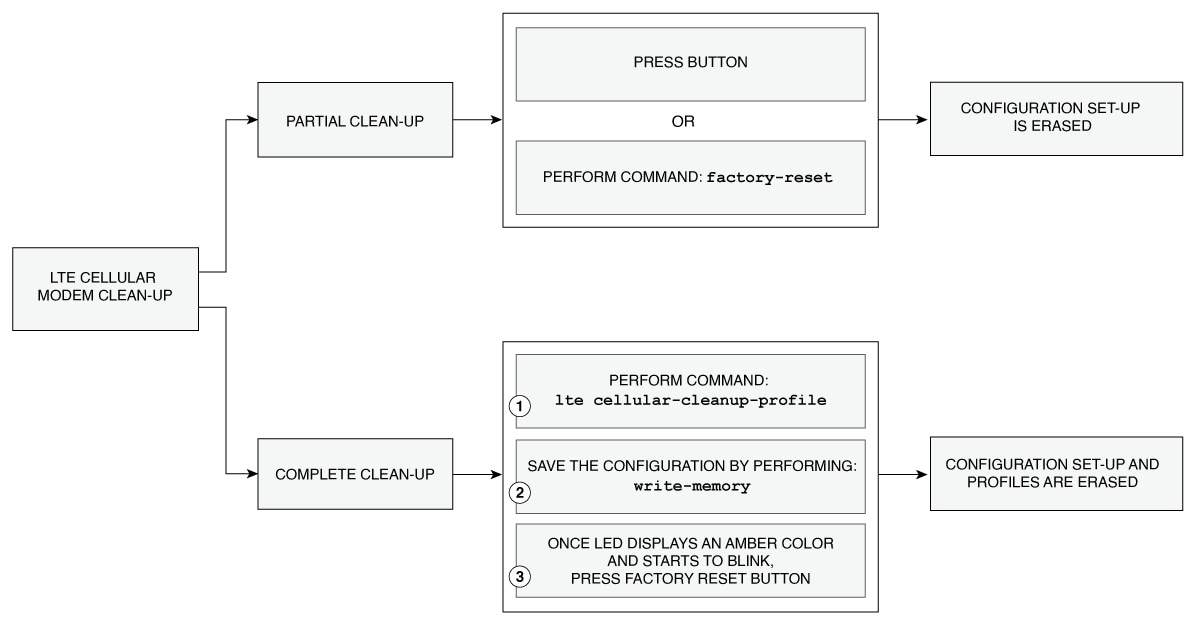
! 
 Feedback
Feedback