Security Cloud Control Integration
A Security Cloud Control is a unified security management platform that
-
integrates with Cisco SD-WAN Manager to enable centralized security policy management and configuration,
-
allows configuration of objects and policies in the Cisco SD-WAN Manager from SCC’s Micro frontend (MFE) user interface,
-
provides a unified interface for configuration and monitoring of security policy,
-
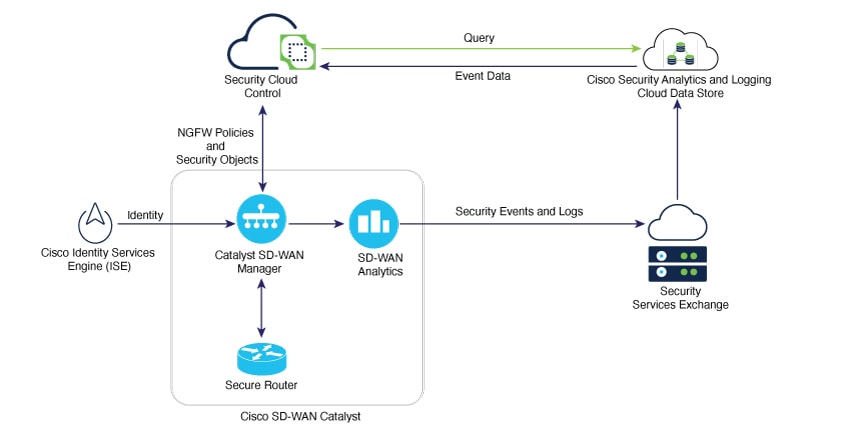
configures, monitors, and troubleshoots security policies for the Secure Router or Catalyst Next-Generation Firewall (NGFW), and
-
provides centralized orchestration, security discovery, policy creation, log and analytics viewing, and security policy implementation across multiple Cisco solutions.
Integration of Security Cloud Control with Cisco SD-WAN Manager helps Network Operations (NetOps) and Security Operations (SecOps) team optimize their day-to-day operations. NetOps teams can use Cisco SD-WAN Manager to handle networking events, configurations, and workflows, while Security Cloud Control serves as a dedicated tool for configuring and managing security functions.
For more information about Security Cloud Control, see Overview of Security Cloud Control
Key aspects of Security Cloud Control integration
Security Cloud Control integration includes:
-
Configuring security objects and policies from Security Cloud Control and pushing them to Secure Router devices through Cisco SD-WAN Manager,
-
Automatically synchronizing Next-Generation Firewall (NGFW) policies with Security Cloud Control to Cisco SD-WAN Manager,

Note
The security policies in NGFW are managed by the Cisco SD-WAN Manager, providing advanced security features like intrusion prevention, malware protection, and URL filtering. You can create the following objects and policies in Security Cloud Control after a successful integration.
-
Objects: Application List, Data Prefix, FQDN, Geolocation, Identity, Port, Protocol, Security Group Tag, Signature, URL Allow, URL Block, and Zone.
-
Policies: Advanced Inspection Profile, Advanced Malware Protection, Intrusion Prevention, TLS/SSL Decryption, TLS/SSL Profile, and URL Filtering.
-
-
Synchronizing existing Cisco Catalyst objects and profiles in Cisco SD-WAN Manager with Security Cloud Control,
-
Synchronizing device inventory in Cisco SD-WAN Manager with the SCC Tenant periodically,
-
Creating and editing new Next-generation firewall (NGFW) policies within Security Cloud Control, and
-
Visualizing logs and events through Security Cloud Control. It requires the following:
-
Security Analytics and Logging license.
-
Analytics is enabled under cloud services admin settings.
Cisco SD-WAN Analytics provides analytics data to Security Services Exchange (SSX). SSX normalizes logs and events after receiving them from Cisco SD-WAN Manager and stores it in Cisco Security Analytics and Logging for visualization through Security Cloud Control.
-
-
Automatic role assignment for Security Cloud Control users in Cisco SD-WAN Manager. For more information, see User roles in Security Cloud Control and Cisco Catalyst SD-WAN Manager
Integration Scenarios
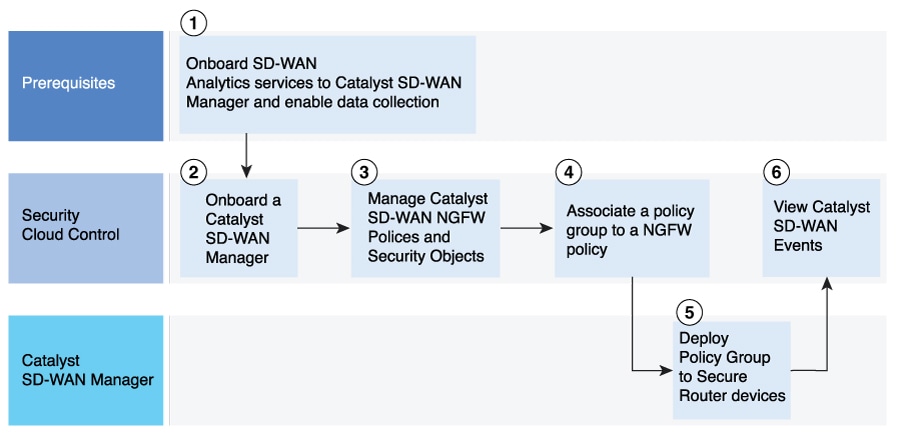
The integration of Cisco SD-WAN Manager with Security Cloud Control enables seamless policy management for both new and existing SecOps users. This integration supports two types of deployment scenarios:
-
New Users: Cisco SD-WAN Manager has no pre-existing policy objects, policies, or security configurations.
-
Existing Users: Cisco SD-WAN Manager has pre-existing policy objects, policies, and security configurations.
The integration process involves syncing and reconciling policies between Cisco SD-WAN Manager and Security Cloud Control that may already be deployed in the devices.
 Feedback
Feedback