About Security Analytics and Logging (SaaS) in Security Cloud Control
Terminology Note: In this documentation, when Cisco Security Analytics and Logging (a software as a service product) is used with Security Cloud Control for security event monitoring and analysis, you will see this integration referred to as Cisco Security Analytics and Logging (SaaS) or SAL (SaaS).
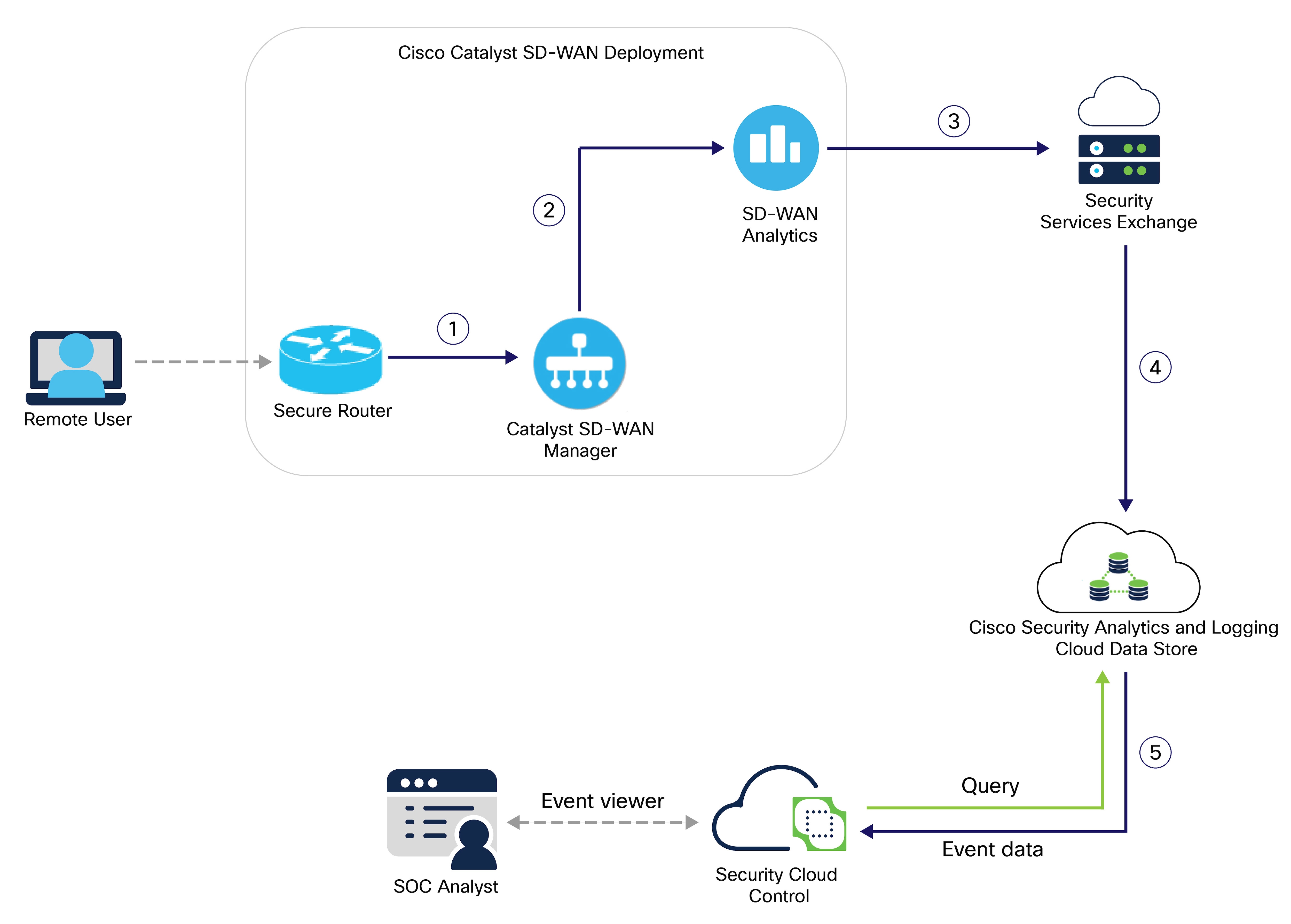
Cisco Security Analytics and Logging (SAL) allows you to capture supported types of security events from all of your firewall devices and view them in one place in Security Cloud Control. The events are stored in the Security Analytics and Logging cloud and viewable from the Event Logging page. The Event Logging page allows you to search, filter and analyze the security event data to understand which security rules are being triggered in your network.

 Feedback
Feedback