|
Object Name
|
The name of the TLS/SSL decryption policy. The name can contain a maximum of 32 characters.
|
|
Server Certificate Checks
|
|
Expired Certificate
|
Defines what the policy should do if the server certificate has expired. Available options include:
-
Drop: Drop traffic
-
Decrypt: Decrypt traffic
|
|
Untrusted Certificate
|
Defines what the policy should do if the server certificate is not trusted. Available options include:
-
Drop: Drop traffic
-
Decrypt: Decrypt traffic
|
|
Certificate Revocation Status
|
Defines whether the Online Certificate Status Protocol (OCSP) should be used to check the revocation status of the server
certificate. Available options include: Enabled or Disabled.
|
|
Unknown Revocation Status
|
Defines the policy action if the OCSP revocation status is unknown.
-
Drop: Drop traffic
-
Decrypt: Decrypt traffic
|
|
Unsupported Mode Checks
|
|
Unsupported Protocol Versions
|
Defines the unsupported protocol versions.
|
|
Unsupported Cipher Suites
|
Defines the unsupported cipher suites.
|
|
Failure Mode
|
Defines the failure mode. The options are Close and Open.
|
|
Certificate Bundle
|
Select the Use Default CA Certificate checkbox to use the default CA.
|
|
Minimal TLS Version
|
Sets the minimum version of TLS that the proxy should support. Available options include: TLS 1.0, TLS 1.1, or TLS 1.2
|
|
Proxy Certificate Attributes
|
|
RSA Keypair Modules
|
Defines the Proxy Certificate RSA Key modules. Available options include: 1024-bit RSA, 2048-bit RSA, or 4096-bit RSA
|
|
EC Key Type
|
Defines the key type. Available options include: P256, P384, or P521
|
|
Certificate Lifetime (in Days)
|
Sets the lifetime of the proxy certificate (in days).
|
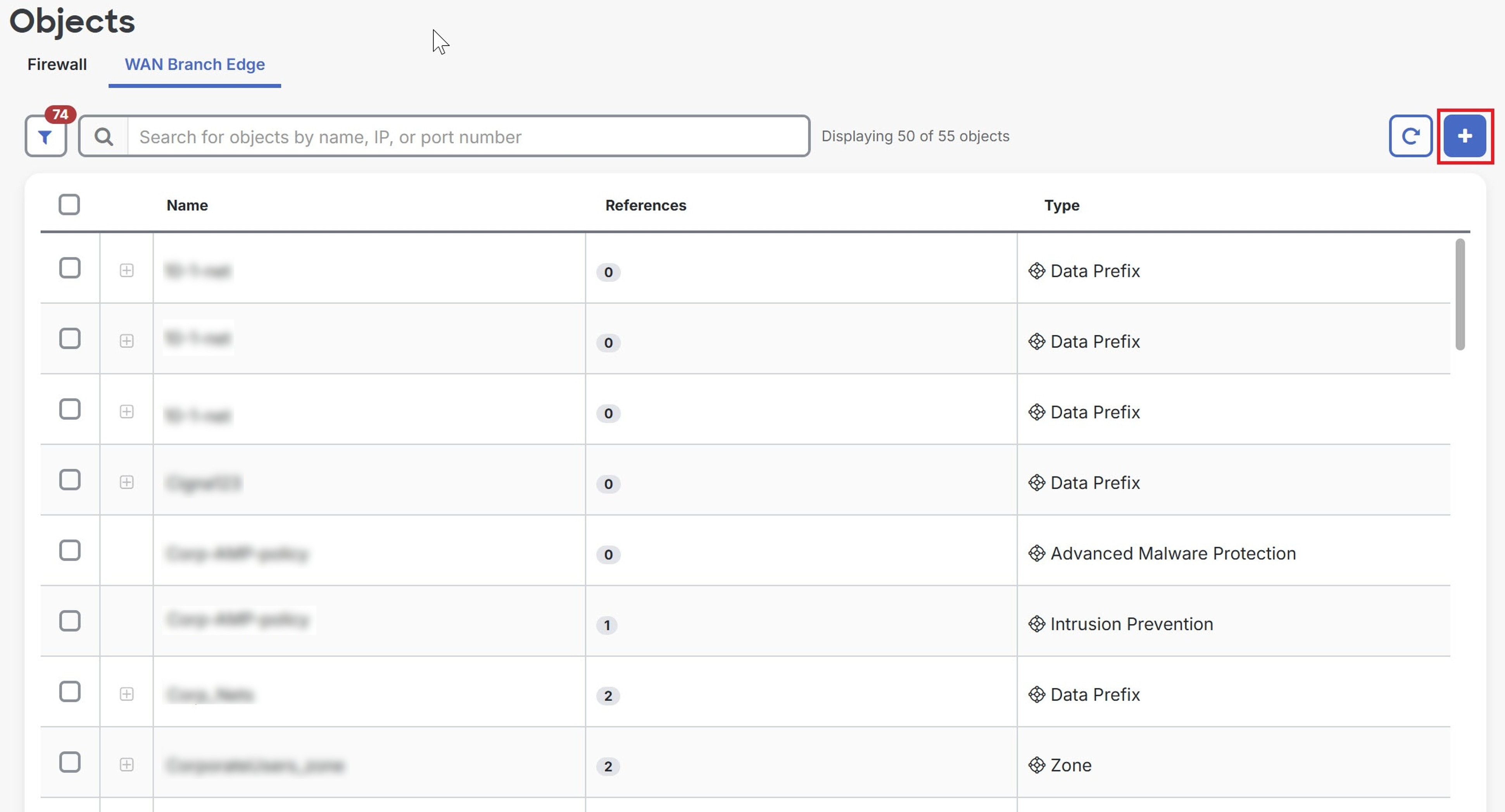

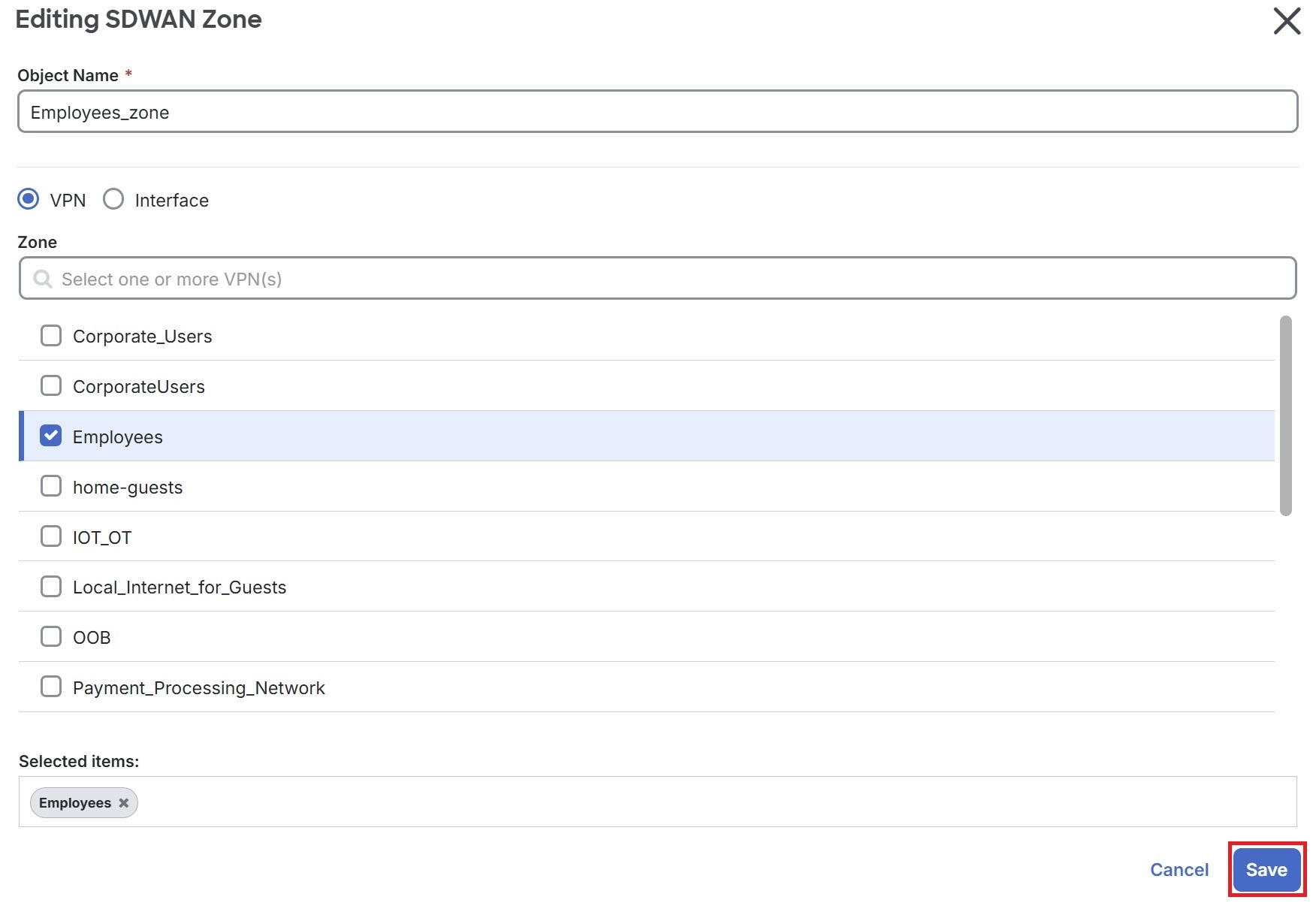
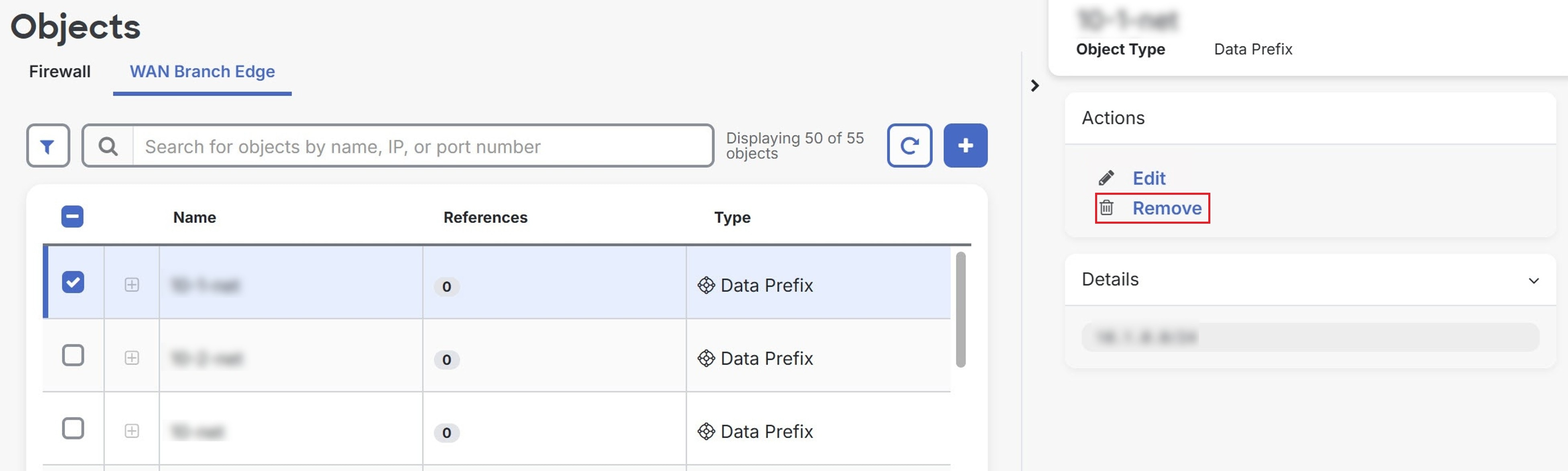
 ) and select objects by
) and select objects by 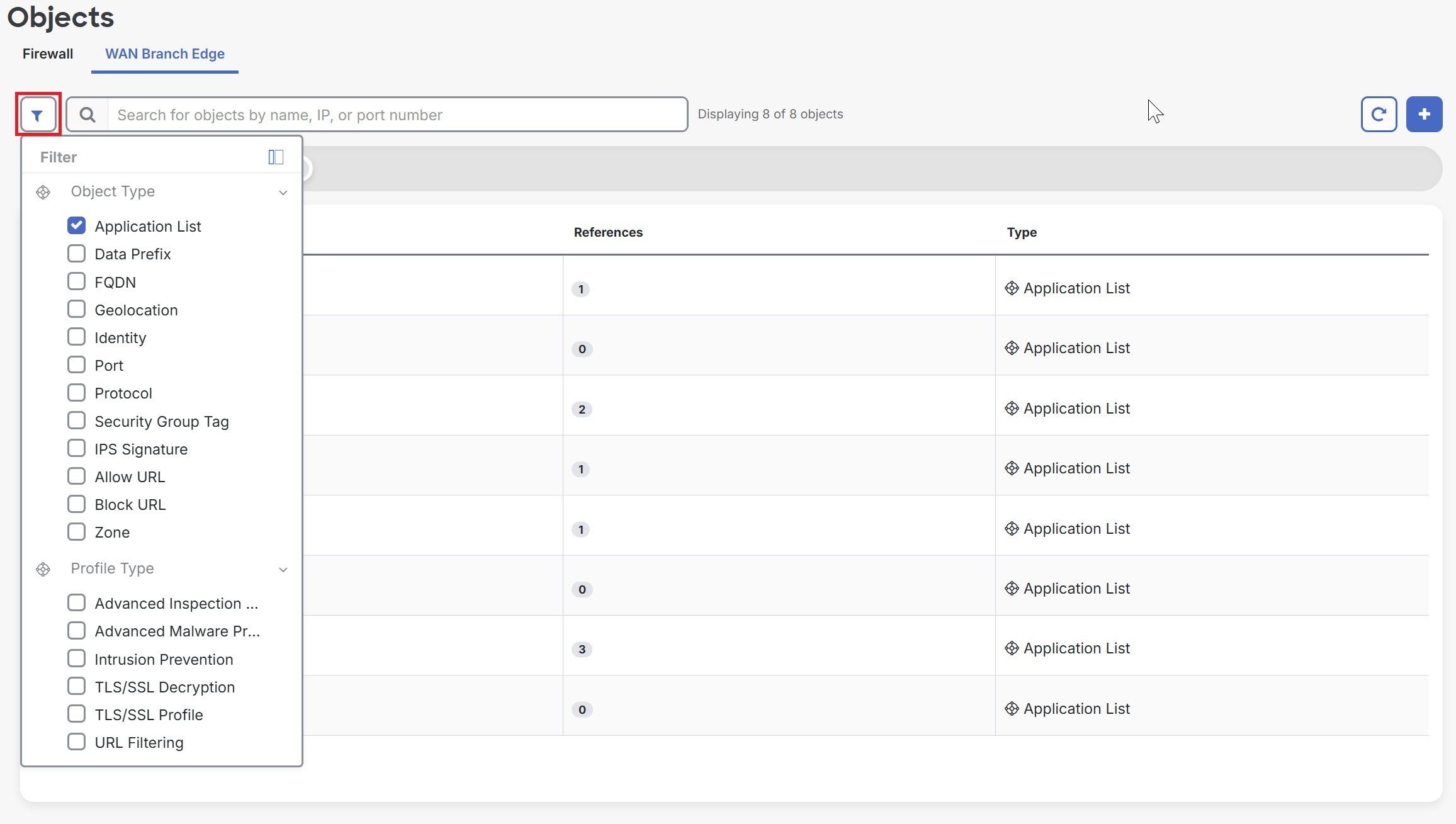
 Feedback
Feedback