Overview of Catalyst SD-WAN integration with Security Cloud Control Firewall Management
You can use Cisco SD-WAN solutions, including the Catalyst and Secure Router series, with Cisco security portfolio to control and manage network security features.
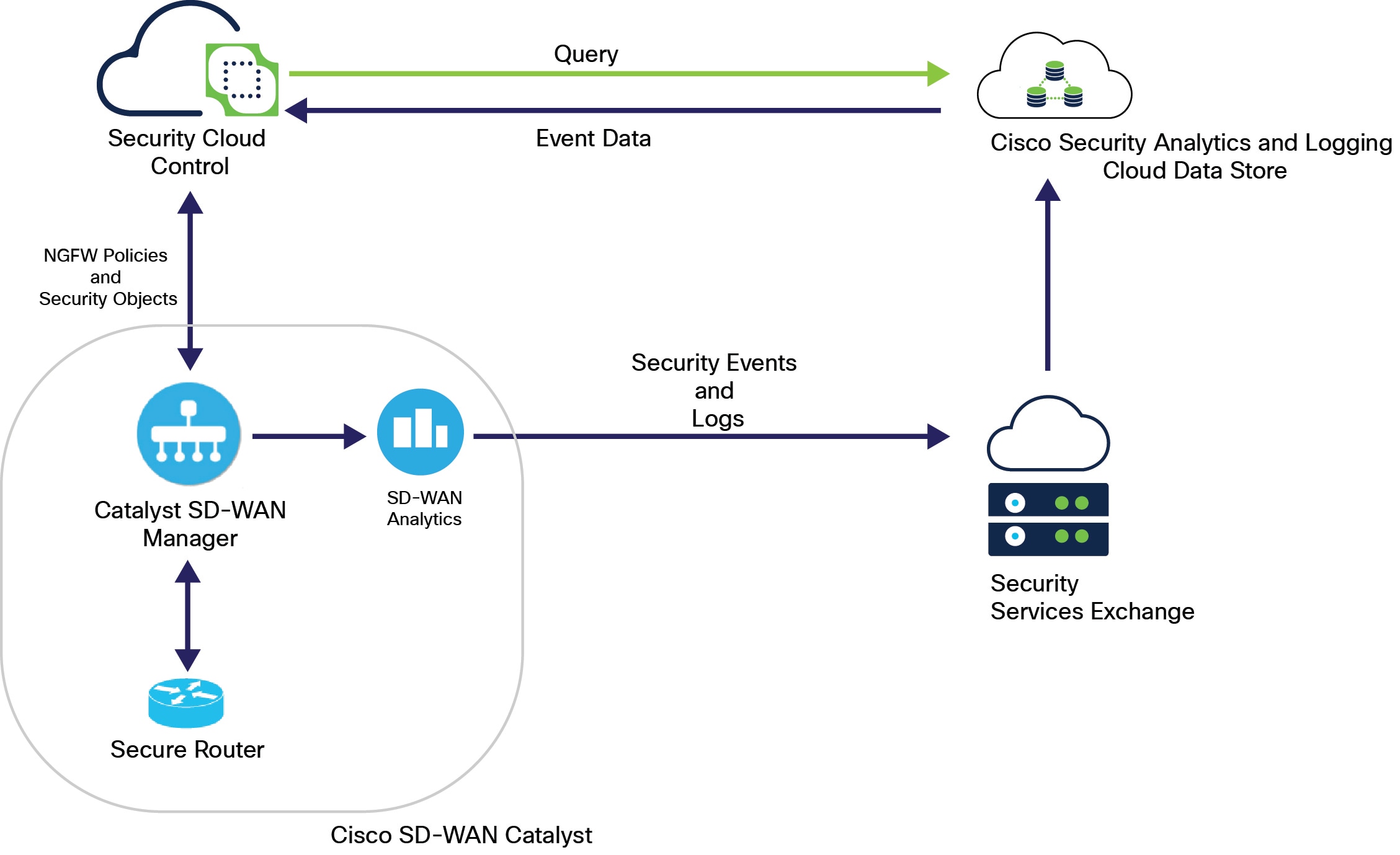
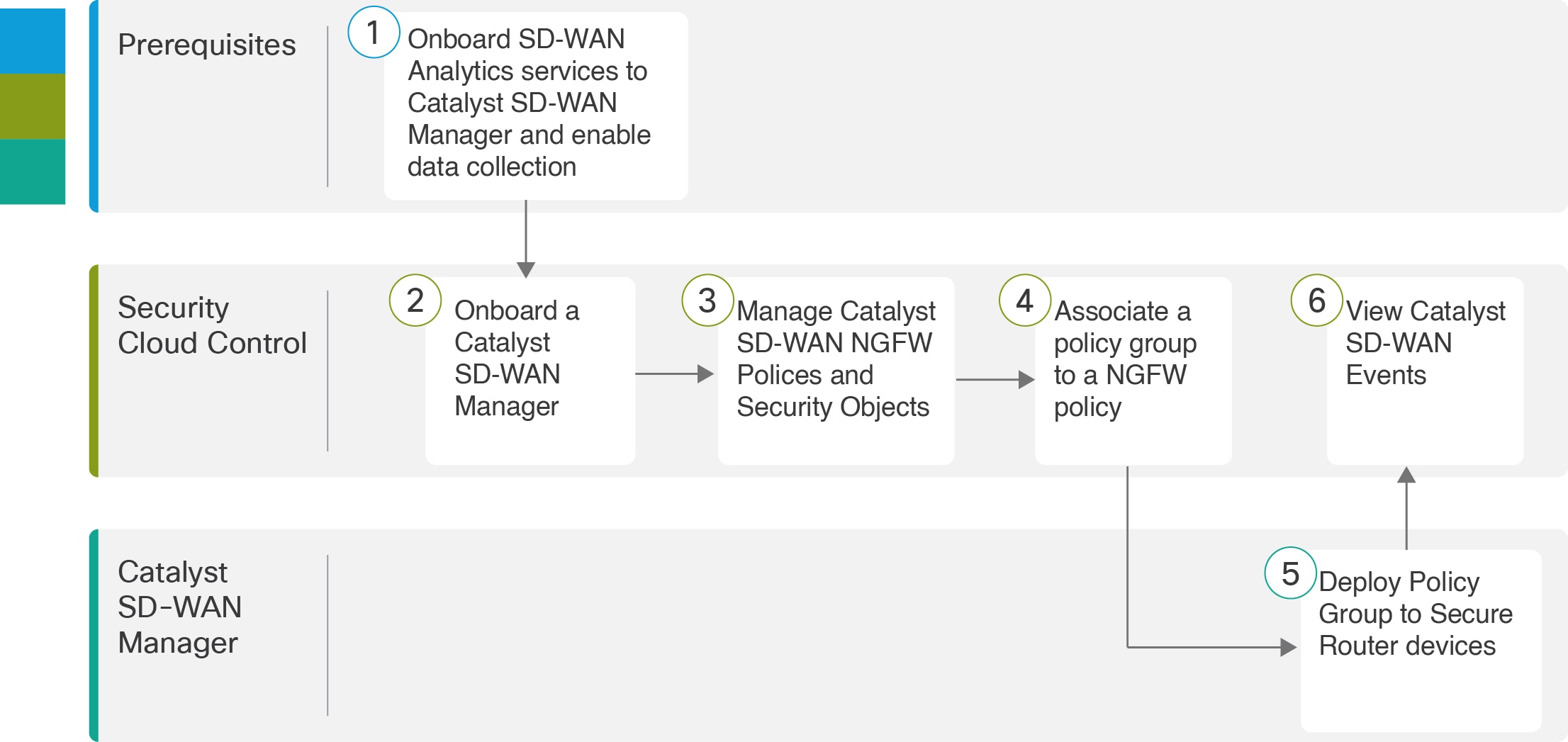
The integration of Security Cloud Control Firewall Management and Catalyst SD-WAN Manager provides centralized management for Cisco Catalyst SD-WAN and Branch WAN environments. This enables organizations to configure, monitor, and enforce security policies across their networks. It also facilitates advanced troubleshooting, rule optimization, and change management on Catalyst SD-WAN Manager.
Benefits
This integration allows you to:
-
Efficiently manage security policies and objects, configure and edit them, and push changes using the Security Cloud Control Firewall Management dashboard.
-
Effective monitoring and detection of security threats from a centralized Security Cloud Control Firewall Management dashboard.
-
Analyze security threats from logs and events in the Security Cloud Control Firewall Management dashboard with data sent from Security Analytics and Logging.
Security Cloud Control Firewall Management provides these capabilities:
-
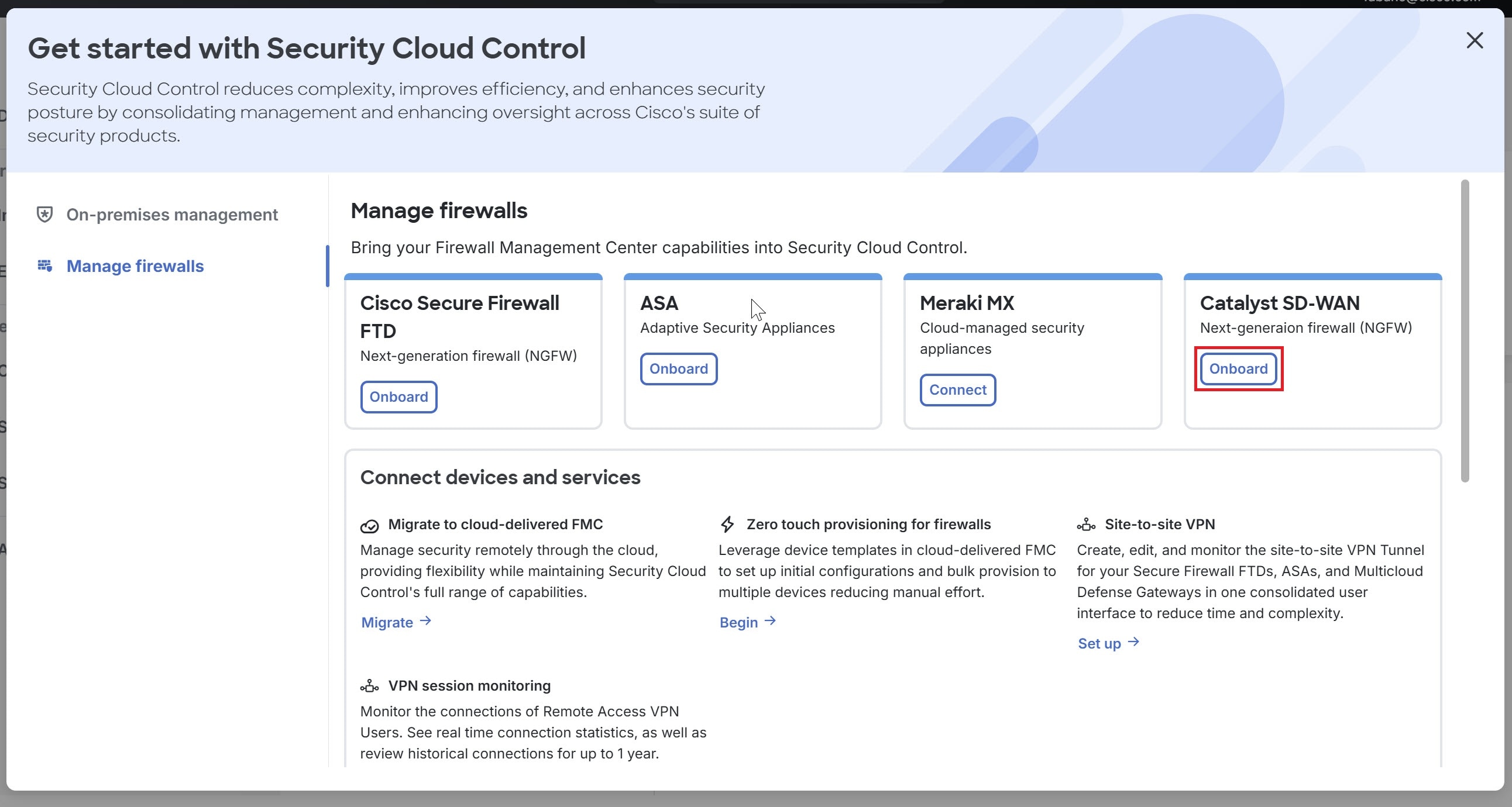
Security Discovery: Identifies existing security configurations and policies through the onboarded Catalyst SD-WAN Manager.
-
Policy Creation: Enables the creation of new security objects and policies using its platform.
-
Cohesive Strategy: Supports a cohesive strategy for implementing security objects, policies, and profiles across multiple Cisco solutions.
-
Log and Analytics Viewing: Offers capabilities for viewing logs and analytics data.
-
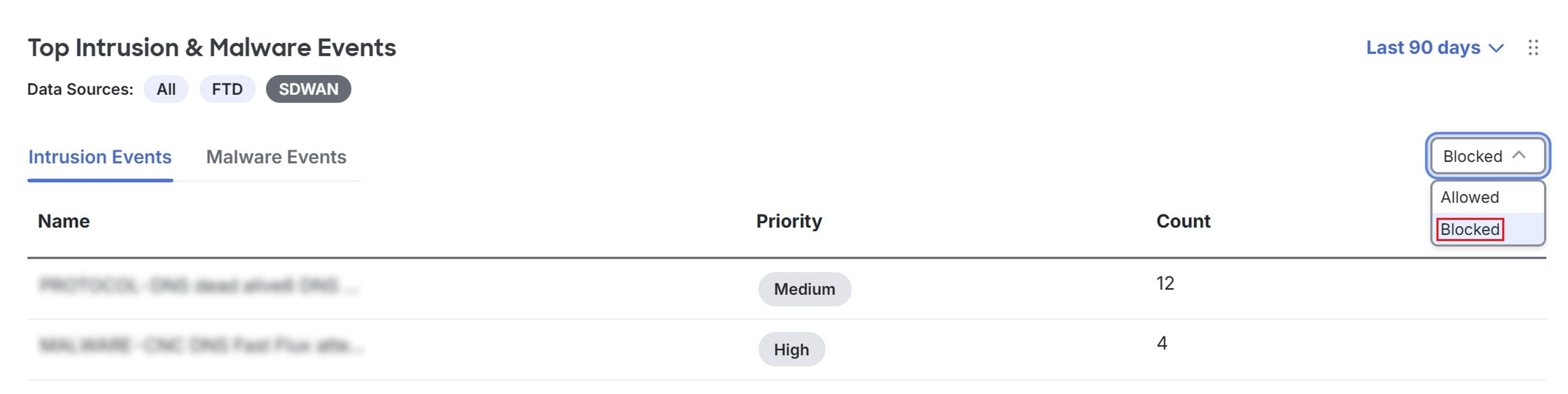
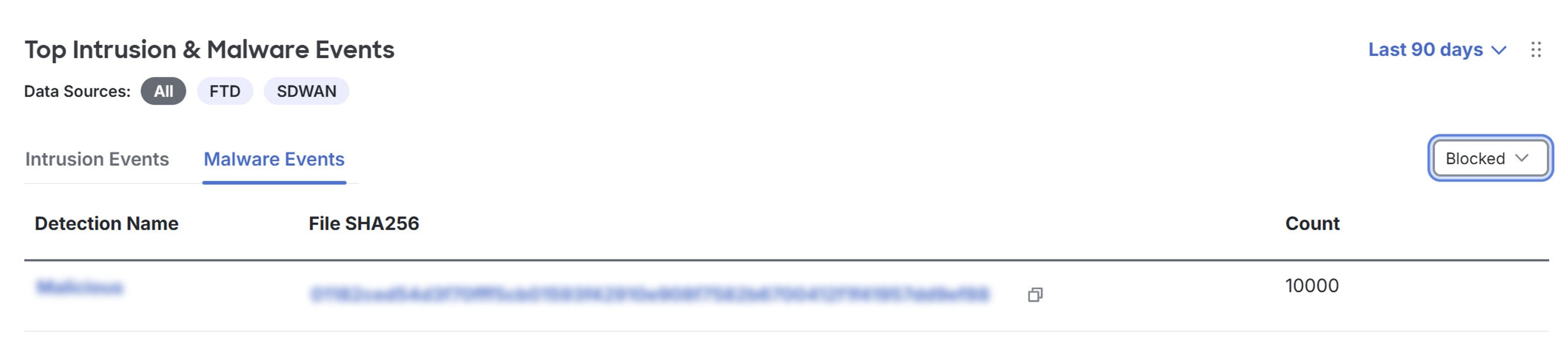
View intrusion and malware events: Displays intrusion and malware events detected within the network from Secure Router.

 .
.
 Feedback
Feedback