Introduction
The Cisco Catalyst IR1101 Rugged Series Router is a next generation modular industrial router which has a Base module with additional Pluggable Modules that can be added. The Pluggable Module provides the flexibility of adding different interfaces to the IR1101 platform.
 Note |
The documentation set for this product strives to use bias-free language. For purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. |
The IR1101 also has two Expansion Modules that add key capabilities such as dual LTE Pluggables, mSATA SSD FRU, SFP, additional ethernet and async ports,and Digital GPIO connections.
The IR1101 is the first IoT platform to run the Cisco IOS-XE operating system. IOS-XE is a Linux based OS that comes with many enhancements and more features compared to the classic IOS version.
This secion of the guide also includes:
IR1101 Base Router
The following figure shows the front panel of the IR1101 and highlights some of its capabilities:

|
Item |
Description |
|---|---|
|
1 |
SFP GigE WAN Port (Combo port of #3 below) |
|
2 |
Type A USB 2.0 Host Port |
|
3 |
RJ45 GigE WAN Port (Combo port of #1 above) |
|
4 |
Asynchronous Serial Port (DTE only) |
|
5 |
RJ45 Fast Ethernet LAN Ports |
|
6 |
Grounding Point (On side of device) |
|
7 |
DC Power and Alarm Input |
|
8 |
Type B Mini-USB Console Port |
|
9 |
Reset Button |
|
10 |
Pluggable Module Slot (ex. 4G/LTE module) |
IRM-1100 Expansion Modules
The Expansion Module comes in two types:
-
IRM-1100-SPMI
-
IRM-1100-SP
The following figure shows the front panel of the IRM-1100-SPMI and highlights some of its capabilities:

|
Item |
Description |
||
|---|---|---|---|
|
1 |
4 GPIO + 1 Return (Digital I/O)
|
||
|
2 |
SFP Connector |
||
|
3 |
Pluggable Module |
||
|
4 |
mSATA SSD Slot |
||
|
5 |
Digital I/O LEDs |
The IR-1100-SP Expansion Module is the same as the IR-1100-SPMI module, without the Digital I/O and mSATA components.
More information can be found in IRM-1101 Expansion Module.
Complete details on the IR1101 can be found in the product data sheet.
IRM-1100-4A2T Expansion Module
The IRM-1100-4A2T is an expansion module that can be attached to the IR1101. It offers an additional four asynchronous serial ports and two Ethernet interfaces to the IR1101. The following graphic shows the IRM-1100-4A2T.
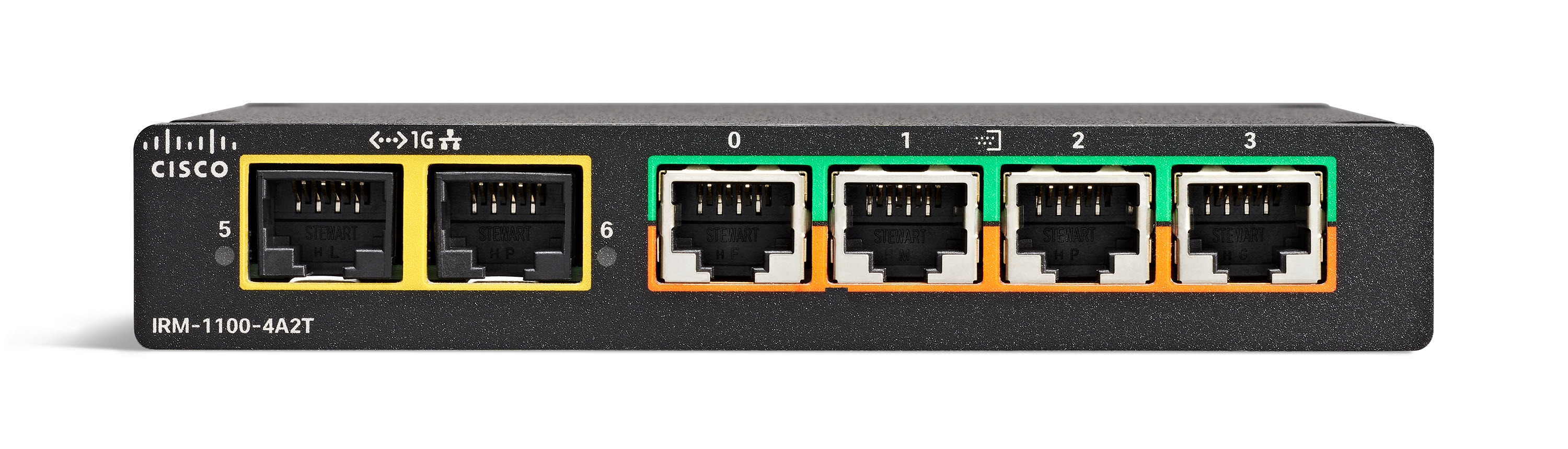
The IRM-1100-4A2T Ethernet interfaces are Layer 2 RJ45 10/100/1000 Mbps ports.
The IRM-1100-4A2T serial ports are RJ45 combo ports (RS232/RS485/RS422).
The IR1101 has two sides that expansion modules mount to. The top is called the Expansion side, and the bottom is called the Compute side. If the additional module is connected to the top, then it is referenced as the Expansion Module (EM) side. If the additional module is connected on the bottom, then it is referenced as the Compute Module (CM) side. Functionality differs depending on which side the expansion module is attached to, and how many and type of expansion modules are in use.
The IRM-1100-4A2T can be managed from the following tools:
-
Cisco DNA Center
-
WebUI
More information can be found in IRM-1100-4A2T Expansion Module.
 Feedback
Feedback