HDLC Support for SCATS Overview
The Sydney Coordinated Adaptive Traffic System (SCATS), is an intelligent transportation system that manages the dynamic (on-line, real-time) timing of signal phases at traffic signals, meaning that it tries to find the best phasing (i.e. cycle times, phase splits and offsets) for a traffic situation (for individual intersections as well as for the whole network). SCATS is based on the automatic plan selection from a library in response to the data derived from loop detectors or other road traffic sensors. SCATS uses sensors at each traffic signal to detect vehicle presence in each lane and pedestrians waiting to cross at the local site. The vehicle sensors are generally inductive loops installed within the road pavement. The pedestrian sensors are usually push buttons. Various other types of sensors can be used for vehicle presence detection, provided that a similar and consistent output is achieved. Information collected from the vehicle sensors allows SCATS to calculate and adapt the timing of traffic signals in the network.
High-Level Data Link Control (HDLC) is a group of data link (Layer 2) protocols used to transmit synchronous data packets between point-to-point nodes. Data is organized into addressable frames. This format has been used for other multipoint-to-multipoint protocols, and inspired the HDLC-like framing protocol described in RFC 1662. HDLC uses a zero-insertion/deletion process (bit stuffing) to ensure that the bit pattern of the delimiter flag does not occur in the fields between flags. The HDLC frame is synchronous and therefore relies on the physical layer (Layer 1) to clock and synchronize frame transmission and reception.
This feature is being developed as an IOx app which integrates with the existing virtualization layers available in IOS XE based IoT routers. The intended application is to have a SCATS controller connected to the router via serial cable. The SCATs protocol the app will follow is documented in specification TSI-SP-068.
The following figure is an example of a typical SCATS traffic control network application:
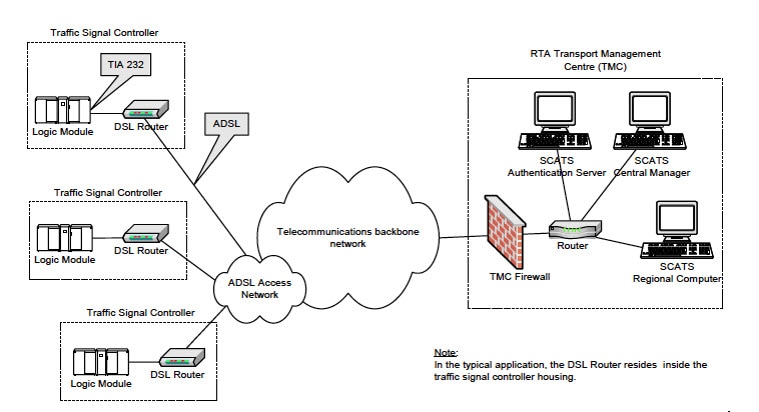
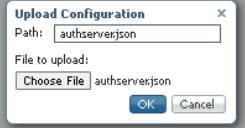
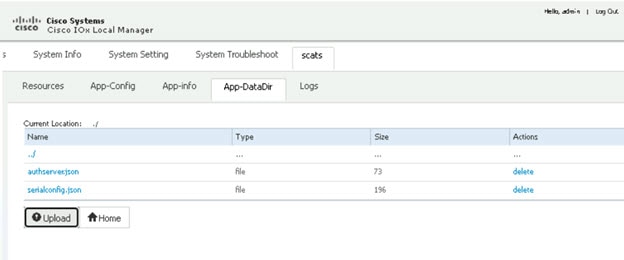
In the above figure, an IR1101 plays the role of the DSL Router to which the Traffic Signal Controller (TSC) is connected via a serial interface. Upon connection to the TSC, the router obtains a Site ID from the controller, which it will then forward to the SCATs Authentication Server. The authentication servers will be provided to the IOx app through a JSON file including IP and port and there can be up to three authentication servers that the IOx app can cycle through.
Once the Authentication Server has received the Site ID, it will reply to the router with the corresponding SCATs regional computer IP and port that matches that Site ID. All further communication is then done transparently from TSC to Regional Computer.
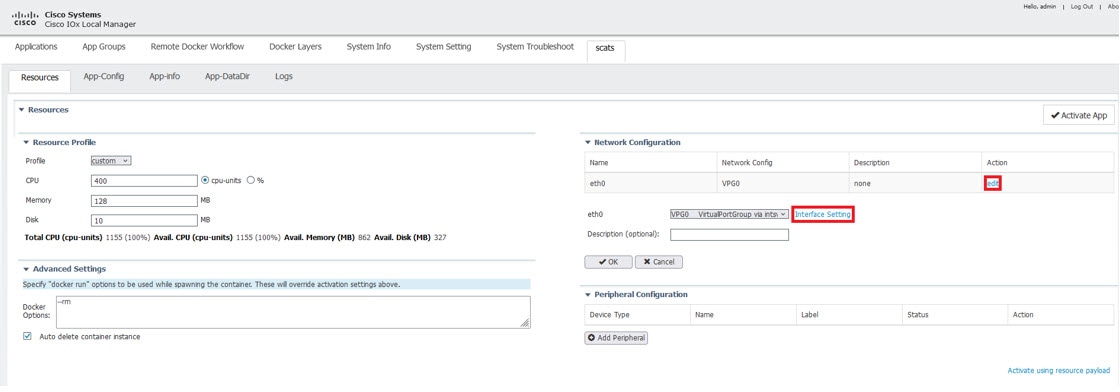
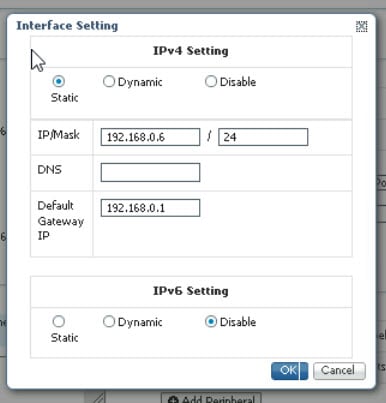
The router will use two modes to communicate with the TSC (HDLC and non-HDLC). There are four available serial configurations, and the user can select which configurations will be used by enabling or disabling them through a second JSON file provided to the app.
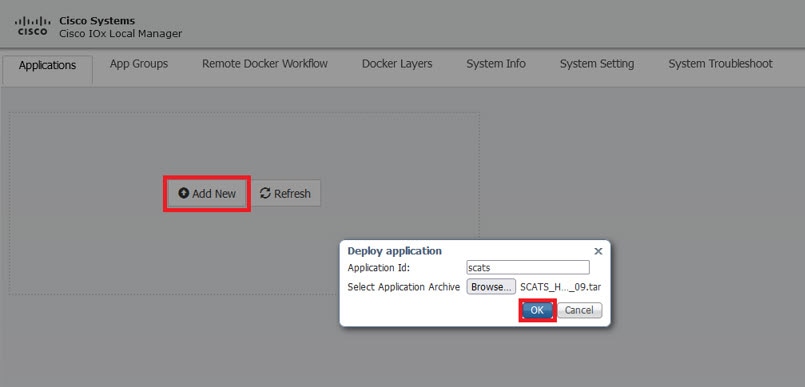
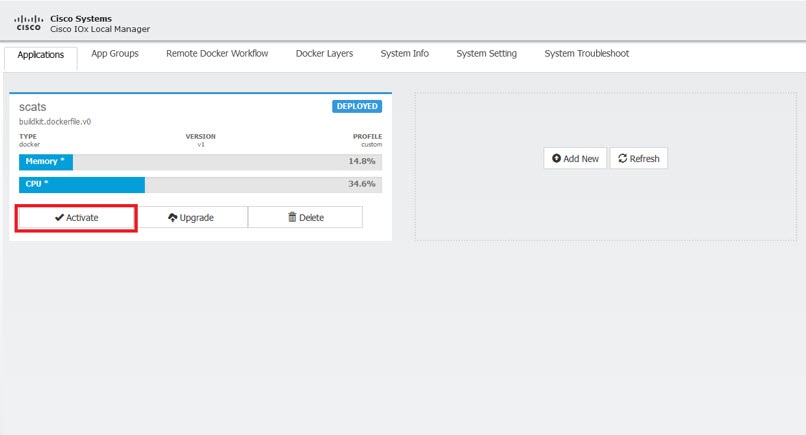
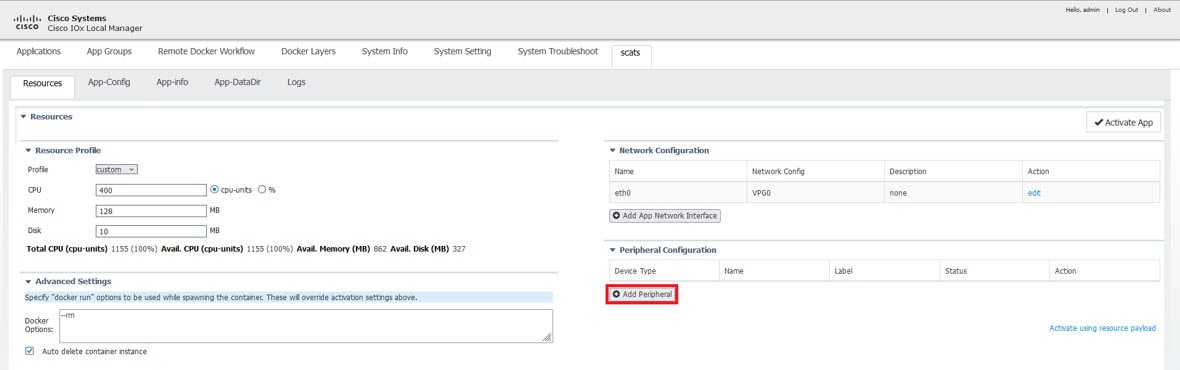
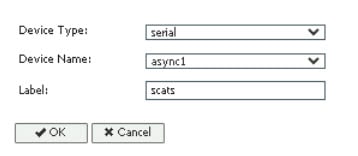
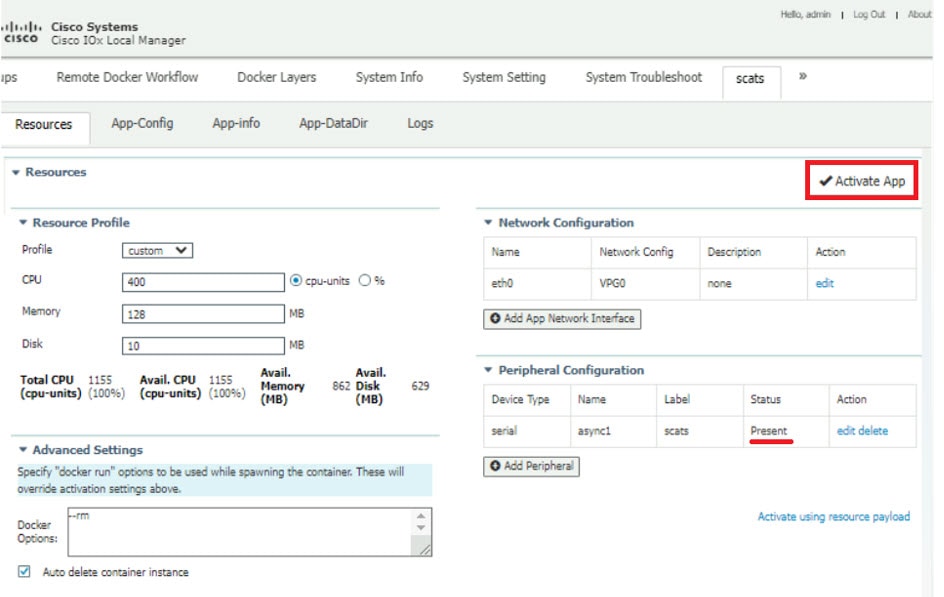
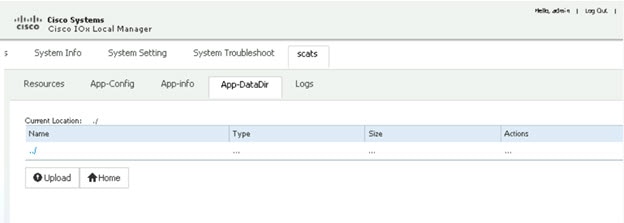
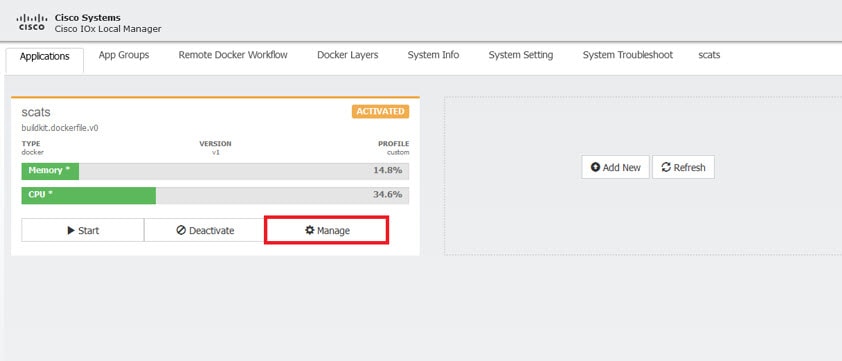
Since this is an IOx app, the feature can be disabled by stopping, deactivating, or uninstalling the app. The application will mainly be deployed using Local Manager. App size is about 50 MB, CPU is 400 units and memory is 128 MB.


 Feedback
Feedback