VPN Console: Hierarchy Tree
Available Languages
Table Of Contents
Specific Edge Device (by Site)
Audit Service Requests—for Specific Customer
Audit Service Requests—for Specific VPN (Customer Tab)
Audit Service Requests—for Specific VPN (VPN Tab)
VPN Console: Hierarchy Tree
In the left pane, the hierarchy pane, of the VPN Console window is a tree of information, known as the hierarchy tree, as shown in Figure 12-1, "Hierarchy Tree in VPN Console."
Figure 12-1 Hierarchy Tree in VPN Console
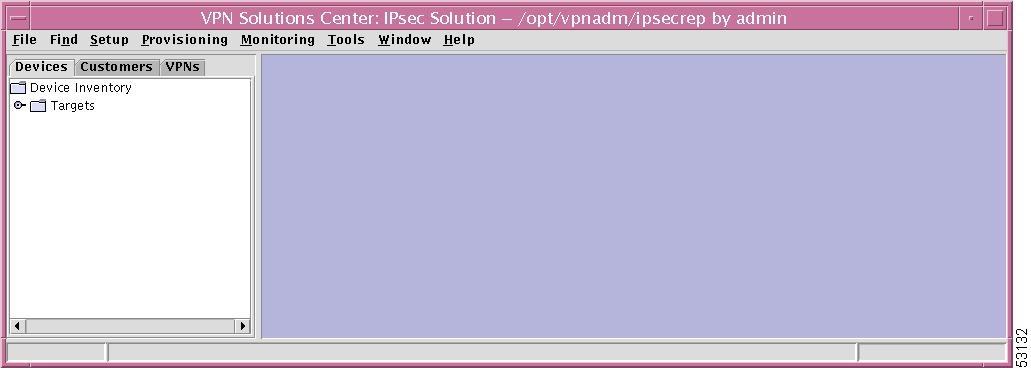
The hierarchy pane in the VPN Console window has three tabs, which allow access to information about the following:
•
VPNs
Within the tree, click on the open-close icon that appears to the left of each node to toggle between the expanded and collapsed view of that node.
Devices
In the hierarchy pane of the VPN Console window, you can click the Devices tab and then completely expand Device Inventory. This shows all created Networks as a subset of Targets, as shown in Figure 12-2, "Device Inventory Expanded."
Figure 12-2 Device Inventory Expanded
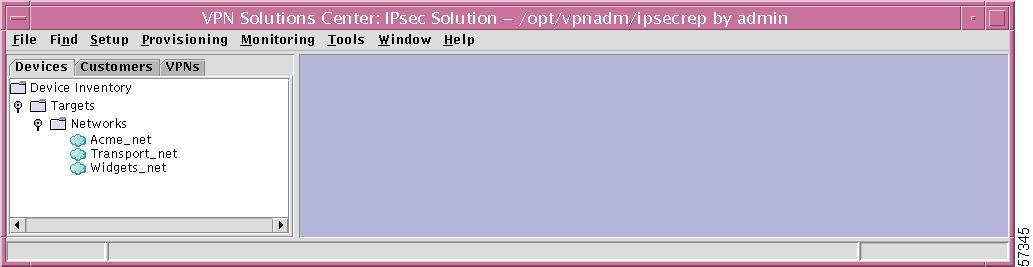
This section is explained in detail in the following subsections:
The explanations are mapped to menu task bar explanations in other chapters. Additionally, the following subsections explain functions that are not available through the menu task bar.
Targets
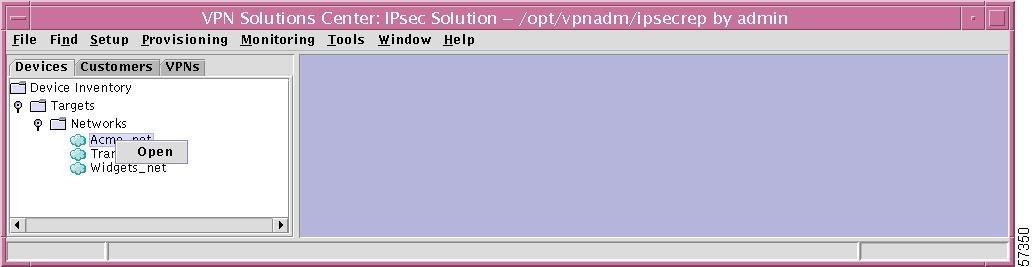
If you right-click on Targets in the hierarchy pane, you get a window as shown in Figure 12-3, "Targets Choice," which gives you the opportunity to create a New Target. This function cannot be implemented through the menu task bar. To do this, refer to the "New Target" section.
Figure 12-3 Targets Choice
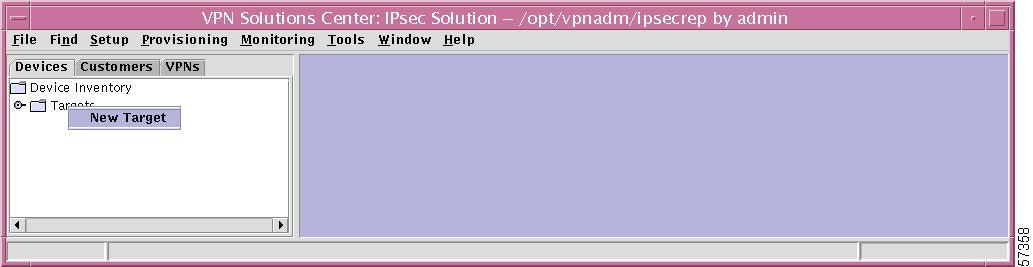
Networks
If you right-click on Networks in the hierarchy pane, you get a window as shown in Figure 12-4, "Networks Choices," which gives you the opportunity to do the following:
•
Find Network Left-click on Find Network. The results are explained in the "Find Network" section.
•
Refresh Left-click on Refresh, which refreshes the hierarchy tree with the most current information.
Figure 12-4 Networks Choices
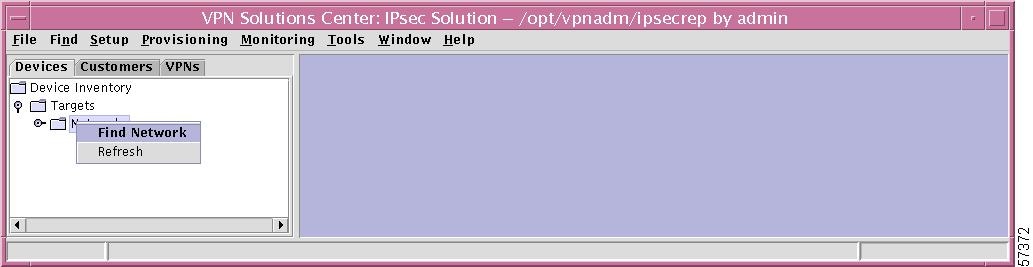
Specific Network
If you right-click on any of the networks listed under Networks in the hierarchy pane, you get a window as shown in Figure 12-5, "Specific Network Choice," which gives you the opportunity to left-click on Open to open that network for viewing or modifying. To do this, refer to the "Open Networks" section.

Note
An alternative to a right-click on any of the networks listed under Networks and then a left-click of Open is to double left-click on any of the networks listed under Networks.
Figure 12-5 Specific Network Choice
New Target
To create a single New Target and identify the network and domain that it will join, from the hierarchy pane, do the following:
Step 1
From the hierarchy tree, expand Device Inventory and right-click on Targets.
Step 2
Left-click on the resulting New Target, as shown in Figure 12-3, "Targets Choice."
Step 3
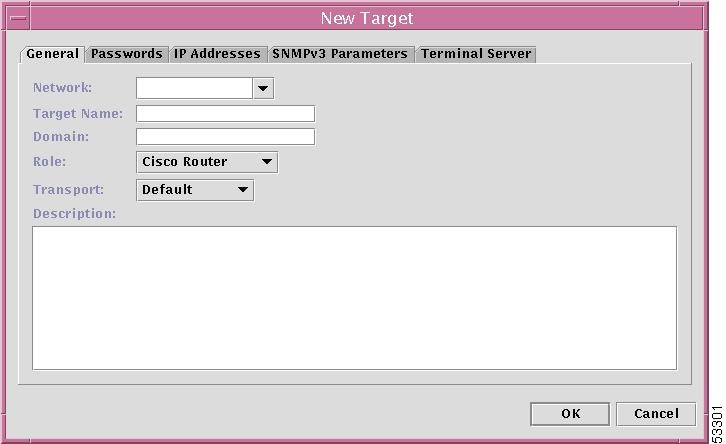
From the resulting New Target window, as shown in Figure 12-6, "New Target Window," enter the following information for the General tab

Note
A target may have been created from configuration files (only possible for Cisco Routers), by navigating from Setup > Create Targets From Router Configurations from the menu task bar, see "VPN Console: Setup Menu." In this case, however, you still need to set the password, as described in Step 5.
•
Network Use the drop-down menu to select the network to which this new target will be added. If you choose Add New Network, NewNetwork1 appears in the field. Highlight that name when it appears in the field and replace it with a new unique valid name.
•
Target Name Enter a unique name for the target in the network chosen in Network.
•
Domain If the network chosen in Network uses a domain, that domain must be entered here. If the network chosen in Network does not use a domain, do not enter information in this field.
•
Role Use the drop-down menu to identify this target as either a Cisco Router or a Terminal Server.

Note
The role chosen can never be changed. To change the role, the target needs to be deleted and re-created.
•
Transport Use the drop-down menu to select a transport mechanism, Default (netsys.gtl.transportMechanism is originally set to TGS_TELNET), TGS_TELNET, TGS_SSH, or TGS_TFTP.

Note
Secure Shell (SSH) is not incorporated into this product. SSH is separately available through CCO. For more information about accessing SSH, refer to the section Installing the Secure Shell (SSH) Module for VPN Solutions Center 2.0 in Chapter 2 of the Cisco VPN Solutions Center Installation Guide.
•
Description In this field, you can enter meaningful information that can be used for clarification and future reference. This field is optional.
Figure 12-6 New Target Window
Step 4
Click OK to exit this GUI window; click Cancel to cancel; or click one of the other tabs. When you click the Passwords tab, you proceed to Step 5. When you click the IP Addresses tab, you proceed to Step 7. When you click the SNMPv3 Parameters tab, you proceed to Step 9. When you click the Terminal Server tab, you proceed to Step 11.
When you click OK, the result is a new Target entry. Password information is required, as explained in the next step.
Step 5
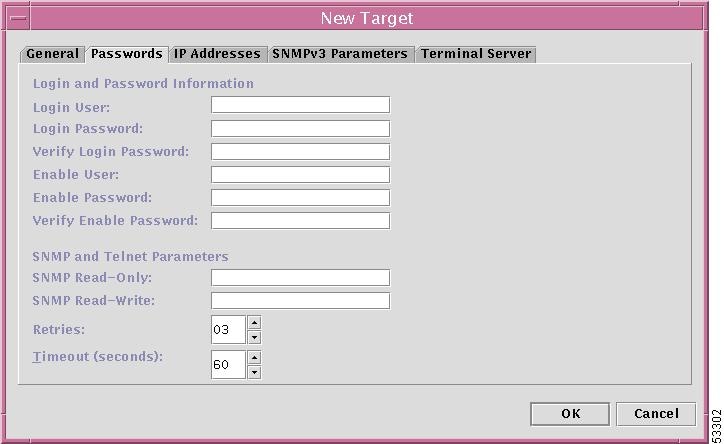
When you choose the Passwords tab in the New Target window shown in Figure 12-6, "New Target Window," the result is a window, as shown in Figure 12-7, "New Target Window—Passwords Tab." Enter the following information:
•
Login User In this field, enter the user identifier for logging in (optional for Cisco Router).
•
Login Password In this field, enter the password to authenticate the user with user-privileges only (required).
•
Verify Login Password In this field, enter the exact same password that you entered in Login Password (required).
•
Enable User In this field, enter the user identifier of the user with privileged mode, the user who can make configuration changes (optional).
•
Enable Password In this field, enter the privileged mode password for the router making configuration changes (required).
•
Verify Enable Password In this field, enter the exact same password that you entered in Enable Password (required).
•
SNMP Read-Only In this field, enter either public or private (Many tasks use SNMP to access the routers. For these tasks, this field is required.)
•
SNMP Read-Write In this field, enter either public or private (Many tasks use SNMP to access the routers. For these tasks, this field is required.)
•
SNMP and Telnet parameters Retries In this field, enter the number of times a connection will be attempted before a permanent failure occurs (defaults to: 03).

Note
Be sure to set this value appropriate to your network.
•
SNMP and Telnet parameters Timeout (seconds) In this field, enter the number of seconds to wait for a connection before retrying or a failure is registered (defaults to: 60).

Note
Be sure to set this value appropriate to your network.
Figure 12-7 New Target Window—Passwords Tab
Step 6
Click OK to exit this GUI window; click Cancel to cancel; or click one of the other tabs. When you click the IP Addresses tab, you proceed to Step 7. When you click the SNMPv3 Parameters tab, you proceed to Step 9. When you click the Terminal Server tab, you proceed to Step 11. When you click the General tab, you proceed to Step 3.
When you click OK, the result is that the passwords are set for the target created in New Target.
Step 7
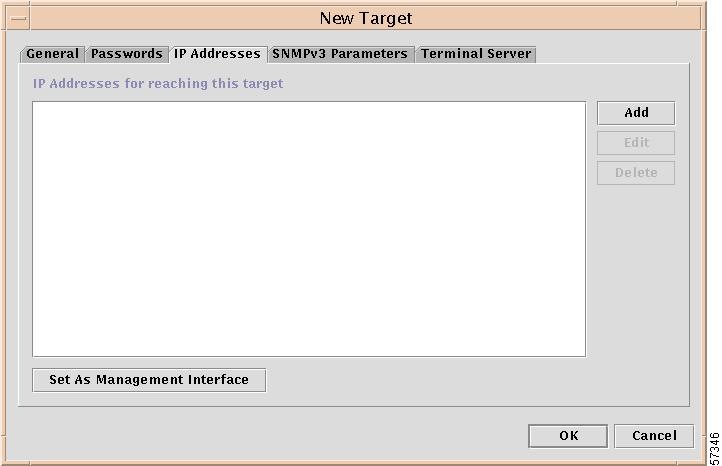
When you choose the IP Addresses tab in the New Target window shown in Figure 12-6, "New Target Window." The result is a window, as shown in Figure 12-8, "IP Addresses Window."

Note
If you are using name resolution, such as Domain Naming System (DNS) or Network Information Service (NIS), the Target Name specified in Step 3 is sufficient. If you are not using DNS, you must specify an IP address in the New Target window. The first IP address specified in the window is the one used. If DNS fails, the system uses the first available IP address.

Note
For each target that has the Role identified as Terminal Server in the General tab (see Step 3), we recommend to Add the IP Address for this target, unless the terminal server has the IOS configurations to expand its own host name to IP address.
Figure 12-8 IP Addresses Window
Step 8
Click one of the following buttons:
•
Add
To add an IP address, click the Add button and you will receive a window as shown in Figure 12-9, "Add IP Address Window."
Figure 12-9 Add IP Address Window
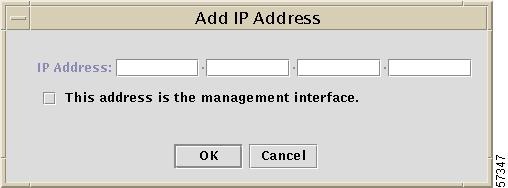
a.
Enter a valid IP address.
b.
If you choose to use this IP address for communication with this target, click the button This address is the management interface.

Note
If you add multiple IP addresses and select This address is the management interface multiple times, only the last selection will be treated as the management interface.
c.
Click OK to continue.
The IP address is added to the field, as shown in Figure 12-10, "Result of Adding an IP Address."
Figure 12-10 Result of Adding an IP Address
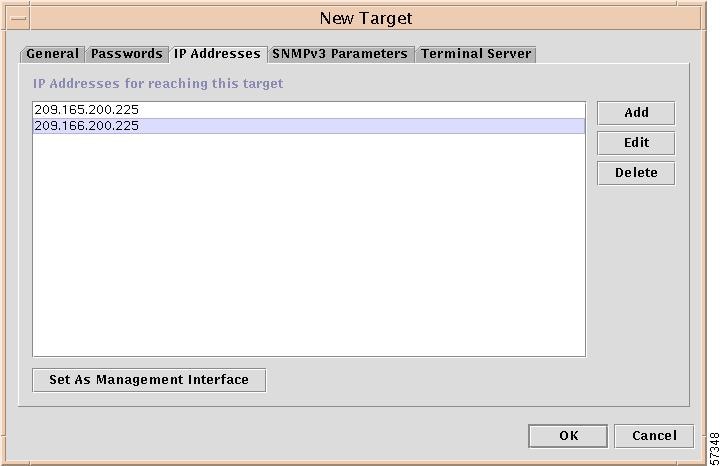
From Figure 12-10, you can select an address and click the Set As Management Interface button. This overrides any previous management interface selection.
•
Edit
To edit an IP address, highlight an existing IP address in a field, like the field in Figure 12-10, "Result of Adding an IP Address,"and click Edit. You will receive a window as shown in Figure 12-11, "Edit IP Address Window.
Figure 12-11 Edit IP Address Window
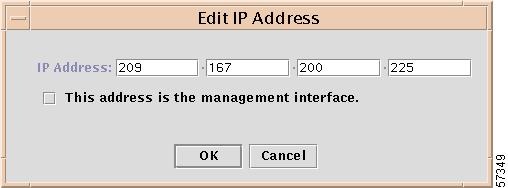
a.
Edit any and all of the address blocks.
b.
If you choose to use this IP address for communication with this target, click the button This address is the management interface.

Note
This selection overrides any previous management interface selection.
c.
Click OK to continue.
In the field in Figure 12-10, the highlighted IP address will be changed to reflect the edits.
•
Delete
Highlight an existing IP address in the field, like the field in Figure 12-10, "Result of Adding an IP Address,"and click Delete. You will receive a window as shown in Figure 12-12, "Delete Confirmation."
Figure 12-12 Delete Confirmation
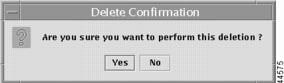
Click Yes to delete the IP address and No not to delete the IP Address.
When you click the SNMPv3 Parameters tab, you proceed to Step 9. When you click the Terminal Server tab, you proceed to Step 11. When you click the General tab, you proceed to Step 3. When you click the Passwords tab, you proceed to Step 5.
Step 9
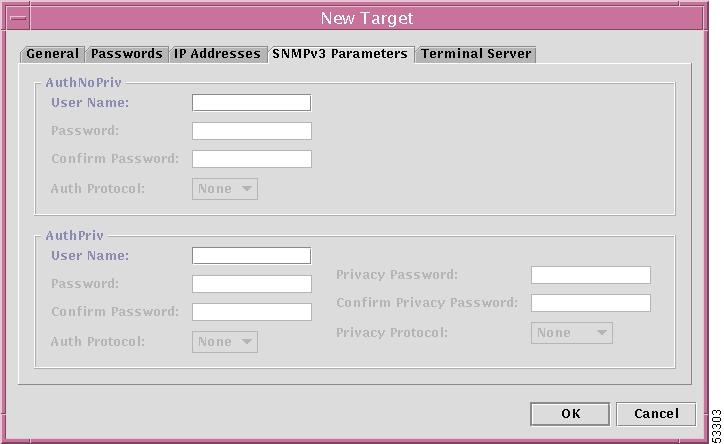
When you choose the SNMPv3 Parameters tab in the New Target window shown in Figure 12-6, "New Target Window," the result is a window, as shown in Figure 12-13, "New Target Window—SNMPv3 Parameters Tab."
If you want this new target to be identified with the security level Auth No Priv, enter the following information:
•
User Name Enter the name of the user that belongs to the group that requires only authentication of the SNMP packet.
•
Password Enter the authentication password of the user specified in User Name.
•
Confirm Password Enter the exact same password as entered in Password.
•
Auth Protocol Use the drop-down menu and choose from md5—the HMAC-MD5-96 authentication level or sha—the HMAC-SHA-96 authentication level.
If you want this new target to be identified with the security level Auth Priv, enter the following information:
•
User Name Enter the name of the user that belongs to a group that requires both authentication and encryption of the SNMP packet.
•
Password Enter the authentication password of the user specified in User Name.
•
Confirm Password Enter the exact same password as entered in Password.
•
Auth Protocol Use the drop-down menu and choose from md5—the HMAC-MD5-96 authentication level or sha—the HMAC-SHA-96 authentication level.
•
Privacy Password Enter the password that enables the encryption of the SNMP packet.
•
Confirm Privacy Password Enter the exact same password as entered in Privacy Password.
•
Privacy Protocol Use the drop-down menu and choose des56—the CBC-DES encryption algorithm.
Figure 12-13 New Target Window—SNMPv3 Parameters Tab
Step 10
Click OK to exit this GUI window; click Cancel to cancel; or click one of the other tabs. When you click the Terminal Server tab, you proceed to Step 11. When you click the General tab, you proceed to Step 3. When you click the Passwords tab, you proceed to Step 5. When you click the IP Addresses tab, you proceed to Step 7.
Step 11
When you choose the Terminal Server tab in the New Target window shown in Figure 12-6, "New Target Window," the result is a window, as shown in Figure 12-14, "New Target Window—Terminal Server Tab."
Figure 12-14 New Target Window—Terminal Server Tab
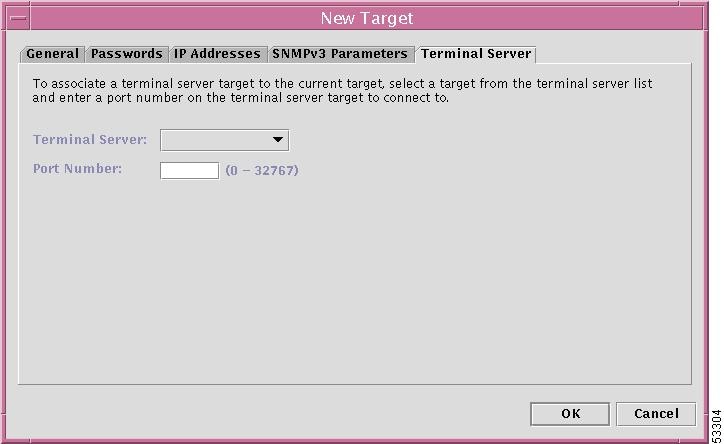
The objective of this path is to associate a terminal server target to the current task.
Enter the following information:
•
Terminal Server Use the drop-down menu and choose from the list of Terminal Servers that have been created.
•
Port Number Enter the port number on which the Telnet Server is connected to the router. The valid range is 0 to 32767.
Step 12
Click OK to exit this GUI window; click Cancel to cancel; or click one of the other tabs. When you click the General tab, you proceed to Step 3. When you click the Passwords tab, you proceed to Step 5. When you click the IP Addresses tab, you proceed to Step 7. When you click the SNMPv3 Parameters tab, you proceed to Step 9.
Open Networks
To open a specific network and perform actions on a minimum of one Cisco Router or Terminal Server, do the following:
Step 1
In the hierarchy tree, double-click on a specific network listed under Networks or right-click on a specific network listed under Networks and then left-click on the resulting Open marker, as shown in Figure 12-15, "Choosing a Specific Network."
Figure 12-15 Choosing a Specific Network

Step 2
The result is a window in the data pane with the name of the selected network as the title, as shown in Figure 12-16, "Network—Actions and View."
Figure 12-16 Network—Actions and View
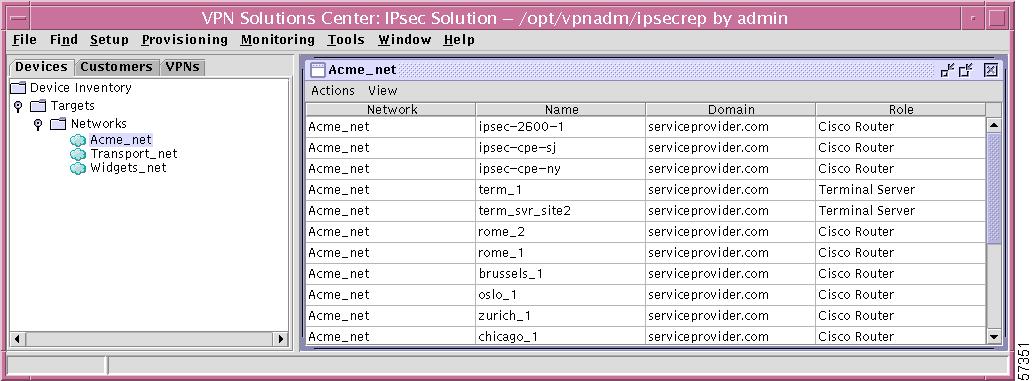
From this window, you can choose one of the following:
Network Window—Actions
Step 1
In the network window created in the "Open Networks" section, in Figure 12-16, "Network—Actions and View," you can highlight one or more rows (target names) to act on. To highlight multiple rows (target names) in a series, click on the first row (target name) of the series then press Shift and click on the final row (target name) to act on. To highlight multiple rows (target names) not in a series, click on the first row (target name), then press Ctrl and click on each of the other rows (target names) you want to act on.

Note
If you choose a single target on which to act, Edit Multiple will not be available (grayed). If you choose multiple targets on which to act, Edit Target and Edit Latest Configuration File will not be available (grayed).
Step 2
Click Actions in the highlighted window and a window as shown in Figure 12-17, "Network—Actions," appears.
Figure 12-17 Network—Actions
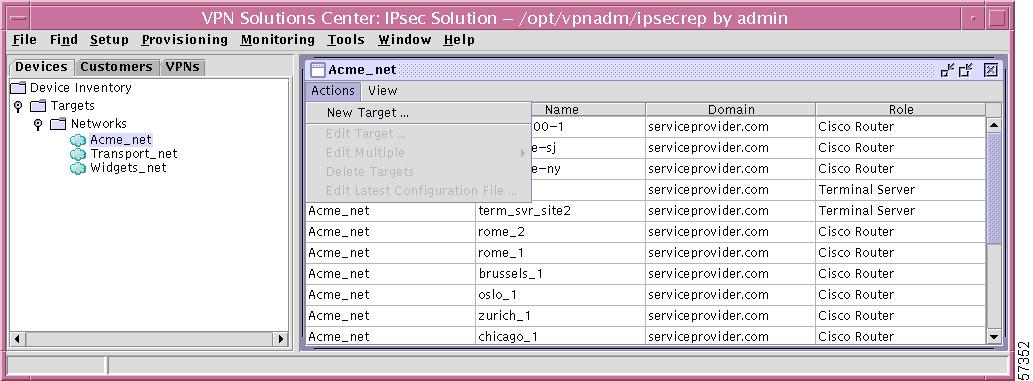
Step 3
Select one of the following:
•
New Target Follow the instructions in the "New Target" section, Step 3. The Network will already be identified as the network chosen in the "Open Networks" section.
•
Edit Target Follow the instructions in the "New Target" section, Step 3. The Network will already be identified as the network chosen in the "Open Networks" section and the Target Name will already be identified as the Name in the highlighted row.
•
Edit Multiple Choose from one of the choices, as shown in Figure 12-18, "Actions—Edit Multiple."
Figure 12-18 Actions—Edit Multiple
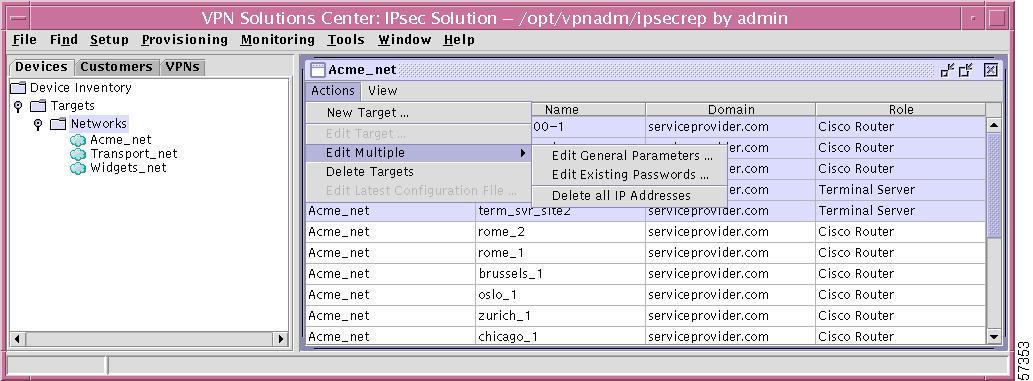
The choices are as follows:
–
Edit General Parameters
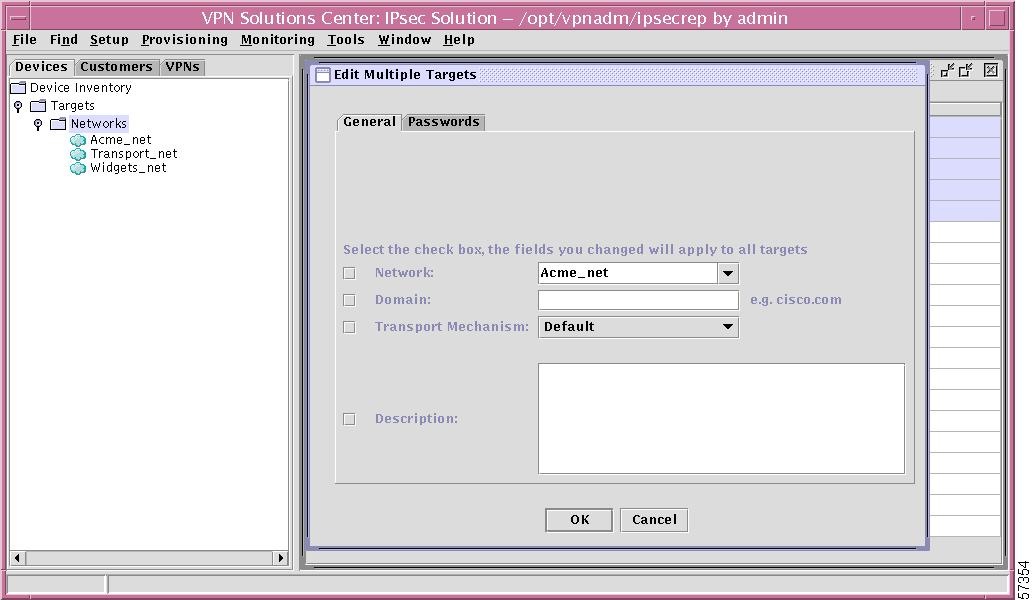
When you make this selection, a window as shown in Figure 12-19, "Edit Multiple Targets—General Tab," appears. Click on one or more of the check boxes and change that setting. Then click OK. These changes will be made for all the targets highlighted in Step 1.

Note
If the Network you choose has an associated Domain, be sure to specify it. Otherwise, do not specify a Domain. The information to be provided is explained in detail in the "New Target" section, Step 3.
You can also choose the Passwords tab, which is explained in the "Edit Existing Passwords" section.
Figure 12-19 Edit Multiple Targets—General Tab
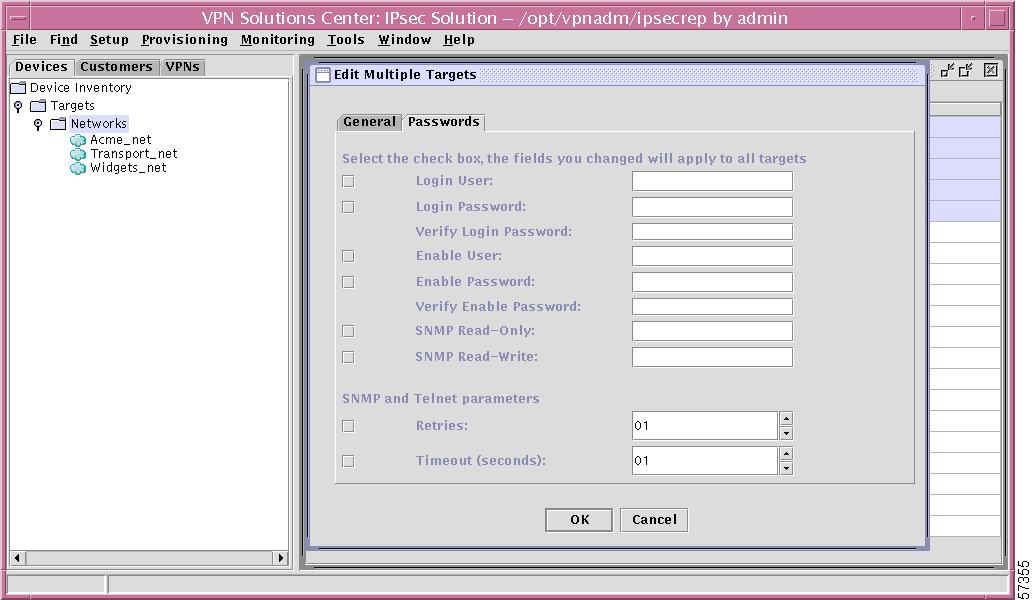
–
Edit Existing Passwords
When you make this selection, a window as shown in Figure 12-20, "Edit Multiple Targets—Passwords Tab," appears. Click on one or more of the check boxes and change that setting. Then click OK. These changes will be made for all the targets highlighted in Step 1.
You can also choose the General tab, which is explained in the "Edit General Parameters" section.

Note
For an explanation of each category, refer to the "New Target" section, Step 5.
Figure 12-20 Edit Multiple Targets—Passwords Tab
–
Delete All IP Addresses
When you make this selection, a window as shown in Figure 12-21, "Edit Multiple Targets—Delete All IP Addresses," appears. If you want to delete all IP addresses for the targets selected in Step 1, click Yes. Otherwise, click No.
For more information about the IP addresses, refer to the "New Target" section, Step 7 and Step 8.
Figure 12-21 Edit Multiple Targets—Delete All IP Addresses
•
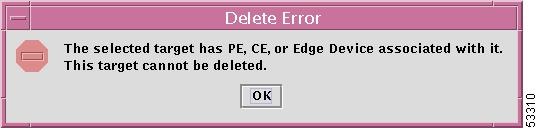
Delete Targets When you make this selection, if the target you are trying to delete has CPEs associated with it, the target cannot be deleted, as explained in the error message shown in Figure 12-22, "Delete Error—Attempting to Delete a Target."
Click OK and you will return to the location before you attempted this unacceptable attempt to delete a target.
Figure 12-22 Delete Error—Attempting to Delete a Target
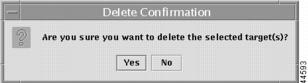
When you have chosen a target, which can successfully be deleted, you will receive a message as shown in Figure 12-23, "Delete Confirmation—Attempting to Delete a Target."
Click Yes if you want to delete the selected target or targets; or click No if you have decided not to delete the selected target or targets.
Figure 12-23 Delete Confirmation—Attempting to Delete a Target
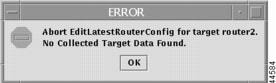
•
Edit Latest Configuration File When you make this selection, if no collected target data is found, you will receive a message as shown in Figure 12-24, "Error—No Collected Target Data Found."
Click OK and you will return to the location before you attempted this unacceptable attempt to edit a configuration file.
Figure 12-24 Error—No Collected Target Data Found
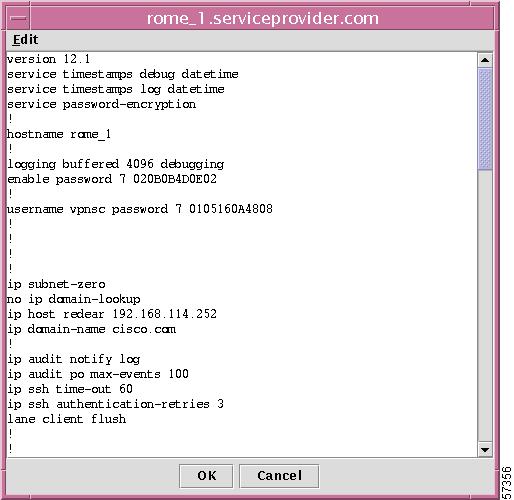
When you make this selection and collected target data is found, you will receive a window as shown in Figure 12-25, "Editing Latest Configuration File."
Figure 12-25 Editing Latest Configuration File
You can position your cursor anywhere within the file and make changes or you can click on Edit to get access to standard editing tasks, as shown in Figure 12-26, "Editing Functions for Editing Latest Configuration File."
Figure 12-26 Editing Functions for Editing Latest Configuration File
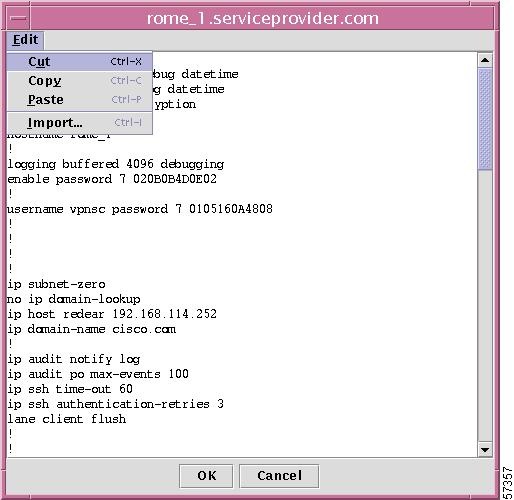
Once you have completed your editing, choose the OK or Cancel button. This gives you the opportunity to confirm your decision to save the edits, as shown in Figure 12-27, "Confirmation of Saving Editing Changes."
Figure 12-27 Confirmation of Saving Editing Changes
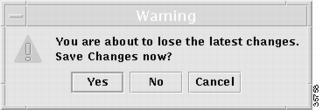
From this confirmation window, choose one of the following:
•
Yes Click Yes to save the editing changes you made.
•
No Click No when you choose not to save the editing changes you made and return to a window prior to editing.
•
Cancel Click Cancel when you choose not to save the editing changes you made and return to the editing window.
Network Window—View
Step 1
In the network window created in the "Open Networks" section, in Figure 12-16, "Network—Actions and View," you can click View. A window as shown in Figure 12-28, "Network—View," appears.
Figure 12-28 Network—View
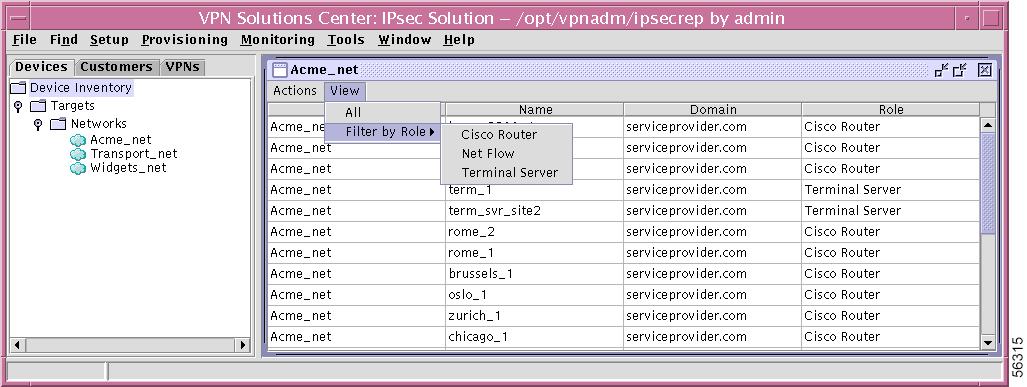
Step 2
Select one of the following:
•
All This lists the entries for all the Roles (Cisco Router and Terminal Server).

Note
If you click on the Role column header, the entries are sorted with all the Cisco Router entries first and all the Terminal Server entries last. Additionally, you can also click on the Name column header and sort alphabetically by Target Name.
•
Filter by Role From this choice you can choose one of the following:
•
Cisco Router This lists only the entries for which the Role is Cisco Router.
•
Terminal Server This lists only the entries for which the Role is Terminal Server.
Customers
In the hierarchy pane of the VPN Console window, you can click the Customers tab and then completely expand Customer Inventory. This shows all created Customers, Sites, Edge Devices (by Site), Policies, VPNs, Service Requests, Tunnels, and Edge Devices, as shown in Figure 12-29, "Customers Expanded."
Figure 12-29 Customers Expanded
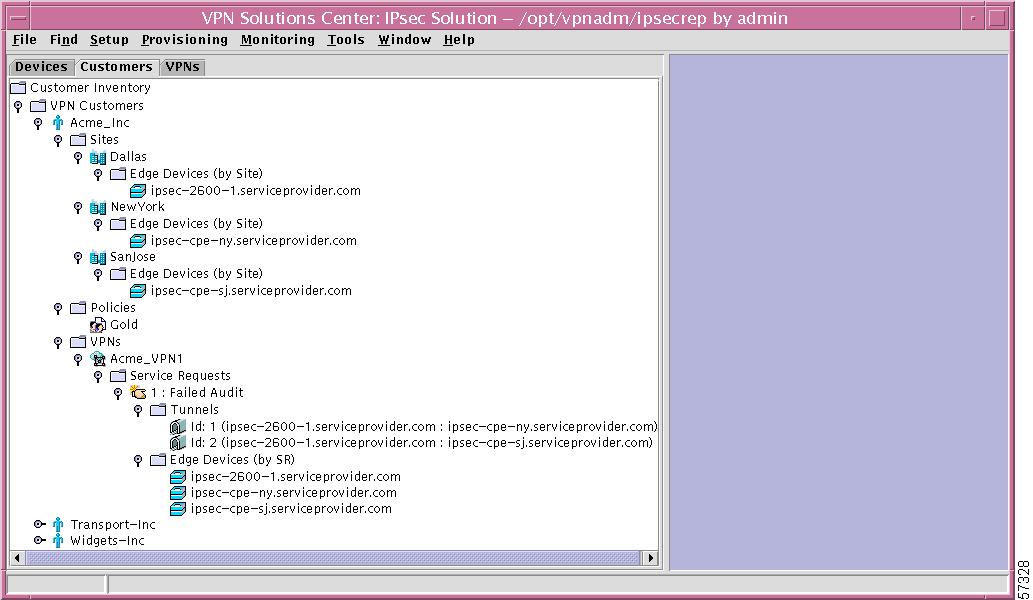
This section is explained in detail in the following subsections:
•
Specific Edge Device (by Site)
•
VPNs
The explanations are mapped to menu task bar explanations in other chapters.
VPN Customers
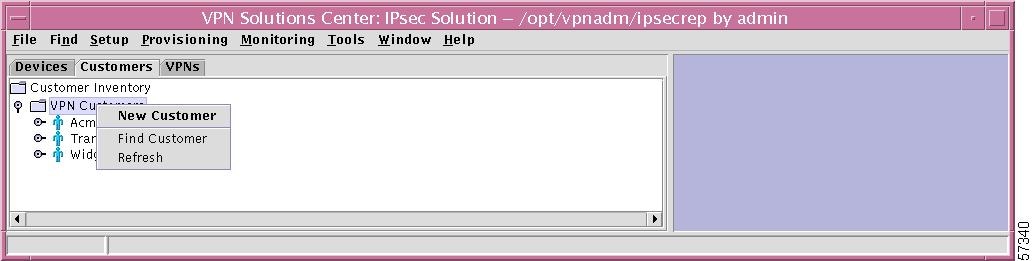
If you right-click on VPN Customers in the hierarchy pane, you get a window as shown in Figure 12-30, "VPN Customers Choices," which gives you the opportunity to do the following:
•
New Customer Left-click on New Customer. This allows you to create a new customer, as explained in the "New VPN Customer" section, Step 2.
•
Find Customer Left-click on Find Customer. The results are the same as explained in the "Find Customer" section.
•
Refresh Left-click on Refresh to refresh the hierarchy tree with the most current information.
Figure 12-30 VPN Customers Choices
Specific Customer
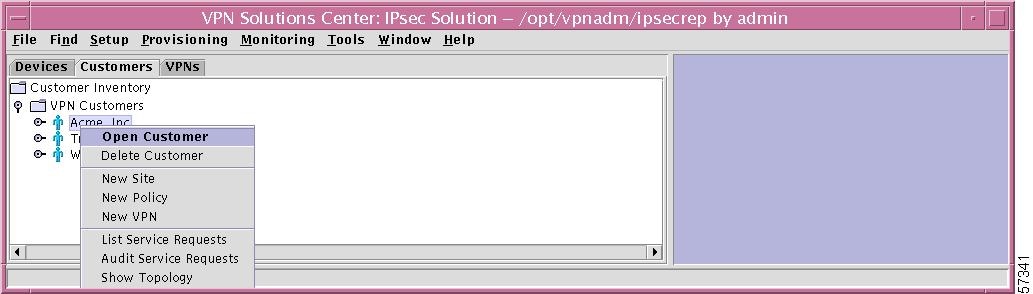
If you right-click on a specific Customer in the hierarchy pane, you get a window as shown in Figure 12-31, "Specific Customer Choices," which gives you the opportunity to do the following:
•
Open Customer Left-click on Open Customer. This allows you to edit this specific Customer, as explained in the "New VPN Customer" section, Step 3.
•
Delete Customer Left-click on Delete Customer. You are asked to confirm whether you are sure you want to delete this customer. Answer Yes to delete the customer; or answer No not to delete the customer.
•
New Site Left-click on New Site, which gives you the opportunity to enter a unique name for this customer site. After you enter a unique site name (the first character must be alphabetic and the remaining characters can be letters, numbers, periods, underscores, and dashes), click the OK button; otherwise click the Cancel button to cancel this process. This procedure is explained in detail in the "New Site" section.
•
New Policy Left-click on New Policy, which gives you the opportunity to enter a unique name for this policy. After you enter a unique policy name (the first character must be alphabetic and the remaining characters can be letters, numbers, periods, underscores, and dashes), click the OK button; otherwise click the Cancel button to cancel this process. This procedure is explained in detail in the "New Policy" section.
•
New VPN Left-click on New VPN, which gives you the opportunity to enter a unique name for this VPN. After you enter a unique VPN name (the first character must be alphabetic and the remaining characters can be letters, numbers, periods, underscores, and dashes), click the OK button; otherwise click the Cancel button to cancel this process. This procedure is explained in detail in the "New VPN" section.
•
List Service Requests Left-click on List Service Requests, which gives you a report as shown in the List All Service Requests section in Chapter 7 but which is specific to this customer.
•
Audit Service Requests Left click on Audit Service Requests, which is explained in the "Audit Service Requests" section.
•
Show Topology Left-click on Show Topology, which gives you topology information specific to this customer. For more generic information about topologies, refer to Chapter 15, "Topology."
Figure 12-31 Specific Customer Choices
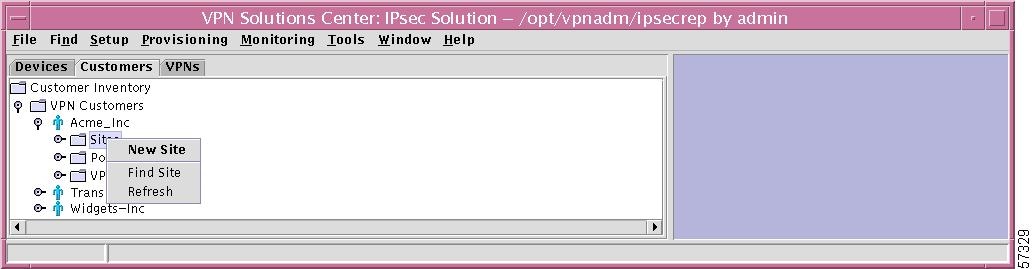
Sites
If you right-click on Sites in the hierarchy pane, you get a window as shown in Figure 12-32, "Site Choices," which gives you the opportunity to do the following:
•
New Site Left-click on New Site, which gives you the opportunity to enter a unique name for this customer site. After you enter a unique site name (the first character must be alphabetic and the remaining characters can be letters, numbers, periods, underscores, and dashes), click the OK button; otherwise click the Cancel button to cancel this process. This procedure is explained in detail in the "New Site" section.
•
Find Site Left-click on Find Site. The results are the same as explained in the "Find Customer Site" section.
•
Refresh Left-click on Refresh to refresh the screen with the most current information.
Figure 12-32 Site Choices
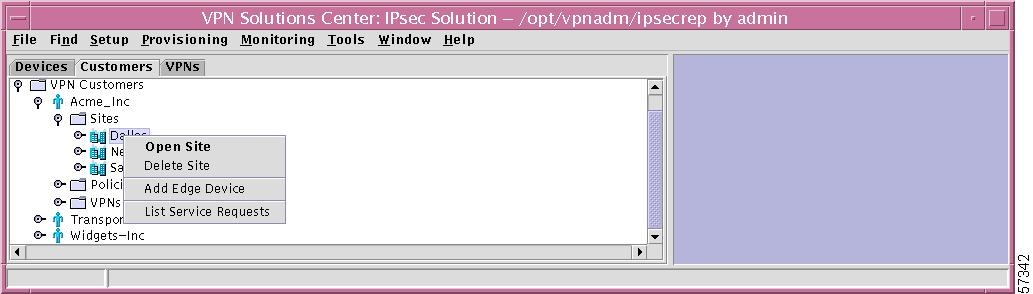
Specific Site
If you right-click on a specific Site in the hierarchy pane, you get a window as shown in Figure 12-33, "Specific Site Choices," which gives you the opportunity to do the following:
•
Open Site Left-click on Open Site. This allows you to edit this specific Site. The process is explained in detail in the "New Site" section, Step 3.
•
Delete Site Left-click on Delete Site. You are asked to confirm whether you are sure you want to delete this site. Answer Yes to delete the site; or answer No not to delete the site.
•
Add Edge Device Left-click on Add Edge Device. This process is explained in detail in the "Add Edge Device" section, Step 2.
•
List Service Requests Left-click on List Service Requests, which gives you a report as shown in the List All Service Requests section in Chapter 7 but which is specific to this site.
Figure 12-33 Specific Site Choices
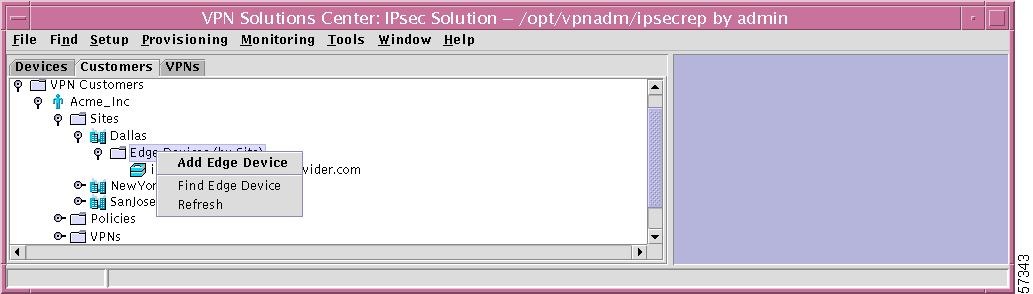
Edge Devices (by Site)
If you right-click on the selection Edge Devices (by Site) in the hierarchy pane, you get a window as shown in Figure 12-34, "Edge Devices (by Site) Choices," which gives you the opportunity to do the following:
•
Add Edge Device Left-click on Add Edge Device. This process is explained in detail in the "Add Edge Device" section, Step 2.
•
Find Edge Device Left-click on Find Edge Device. The results are the same as explained in the "Find Edge Device" section.
•
Refresh Left-click on Refresh to refresh the hierarchy tree with the most current information.
Figure 12-34 Edge Devices (by Site) Choices
Specific Edge Device (by Site)
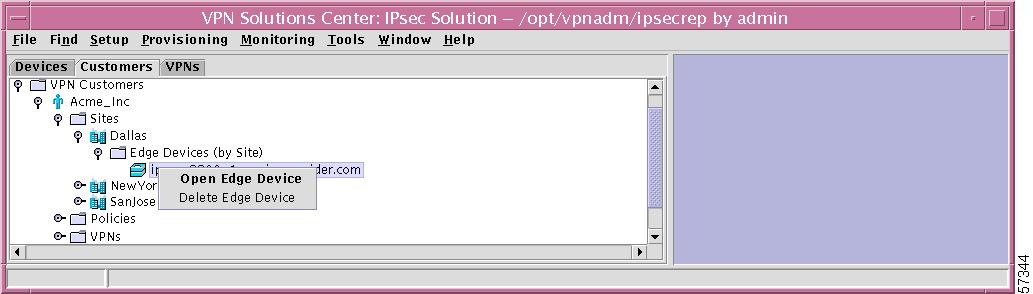
If you right-click on a specific Edge Device in the hierarchy pane, you get a window as shown in Figure 12-35, "Specific Edge Device Choices," which gives you the opportunity to do the following:
•
Open Edge Device Left-click on Open Edge Device. This process is explained in detail in the "Add Edge Device" section, Step 4.
•
Delete Edge Device Left-click on Delete Edge Device. You are asked to confirm whether you are sure you want to delete this edge device. Answer Yes to delete the edge device; or answer No not to delete the edge device.

Note
An alternative to a right-click on any of the edge devices listed under Edge Devices (by Site) and then a left-click of Open Edge Device is to double left-click on any of the edge devices listed under Edge Devices (by Site).
Figure 12-35 Specific Edge Device Choices
Policies
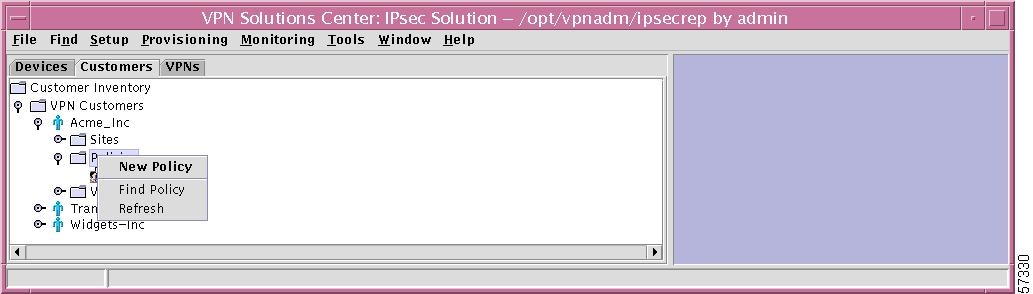
If you right-click on the selection Policies in the hierarchy pane, you get a window as shown in Figure 12-36, "Policies Choices," which gives you the opportunity to do the following:
•
New Policy Left-click on New Policy. This process is explained in detail in the "New Policy" section.
•
Find Policy Left-click on Find Policy. The results are the same as explained in the "Find Policy" section.
•
Refresh Left-click on Refresh to refresh the hierarchy tree with the most current information.
Figure 12-36 Policies Choices
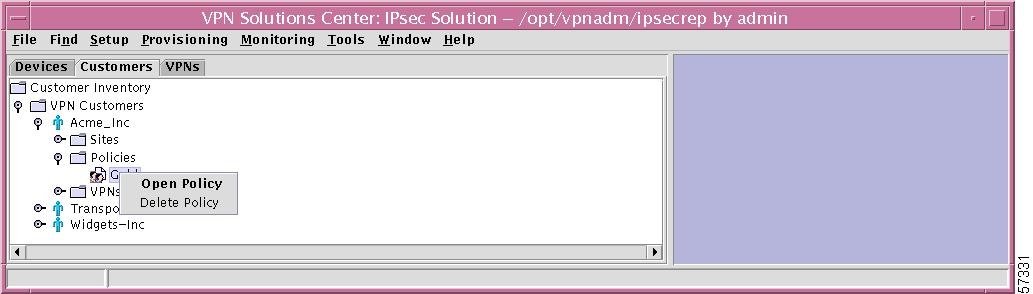
Specific Policy
If you right-click on a specific Policy in the hierarchy pane, you get a window as shown in Figure 12-37, "Specific Policy Choices," which gives you the opportunity to do the following:
•
Open Policy Left-click on Open Policy. This process is explained in detail in the "New Policy" section, Step 3.
•
Delete Policy Left-click on Delete Policy. You are asked to confirm whether you are sure you want to delete this policy. Answer Yes to delete the policy; or answer No not to delete the policy.
Figure 12-37 Specific Policy Choices
VPNs
If you right-click on VPNs in the hierarchy pane, you get a window as shown in Figure 12-38, "VPNs Choices," which gives you the opportunity to do the following:
•
New VPN Left-click on New VPN. This process is explained in detail in the "New VPN" section.
•
Find VPN Left-click on Find VPN. The results are the same as explained in the "Find VPN" section.
•
Refresh Left-click on Refresh, which refreshes the hierarchy tree with the most current information.
Figure 12-38 VPNs Choices
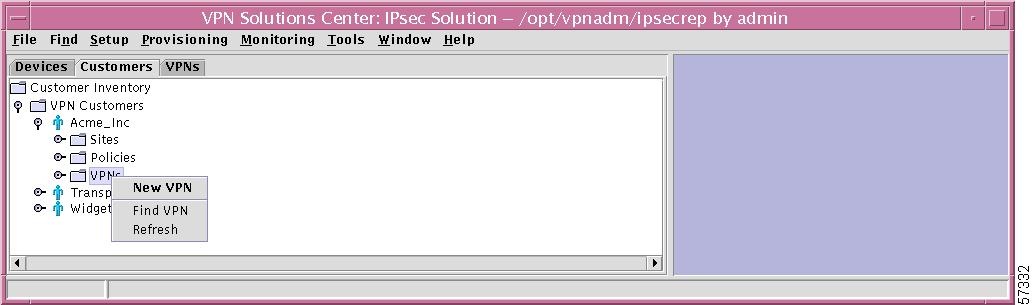
Specific VPN
If you right-click on a specific VPN in the hierarchy pane, you get a window as shown in Figure 12-39, "Specific VPN Choices," which gives you the opportunity to do the following:
•
Open VPN Left-click on Open VPN. This allows you to edit this specific VPN. This process is explained in detail in the "New VPN" section, Step 3.
•
Delete VPN Left-click on Delete VPN. You are asked to confirm whether you are sure you want to delete this VPN. Answer Yes to delete the VPN; or answer No not to delete the VPN.
•
List Service Requests Left-click on List Service Requests, which gives you a report as shown in the List All Service Requests, but which is specific to this VPN.
•
Audit Service Requests Left-click on Audit Service Requests, which is explained in the "Audit Service Requests" section.
•
Show Topology Left-click on Show Topology, which gives you topology information specific to this VPN. For more generic information about topologies, refer to Chapter 15, "Topology."
Figure 12-39 Specific VPN Choices

Service Requests
If you right-click on Service Requests in the hierarchy pane, you get a window as shown in Figure 12-40, "Service Requests Choices," which gives you the opportunity to do the following:
•
New Service Request Left-click on New Service Request. The process is explained in detail in the "Add Service Request" section.
•
Find Service Request Left-click on Find Service Request. The results are the same as explained in the "Find Service Request" section.
•
Refresh Left-click on Refresh, which refreshes the hierarchy tree with the most current information.
Figure 12-40 Service Requests Choices
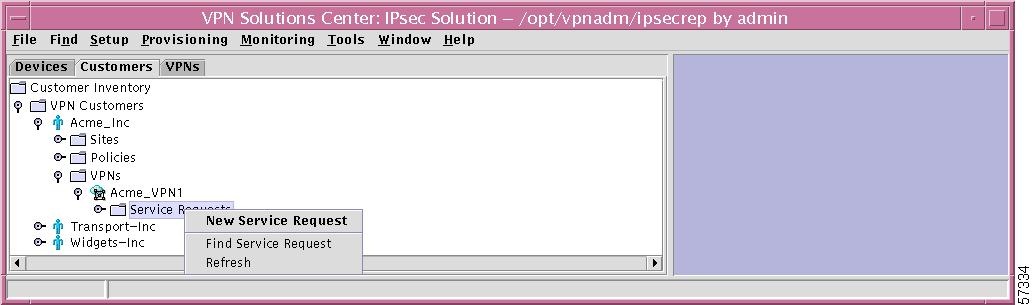
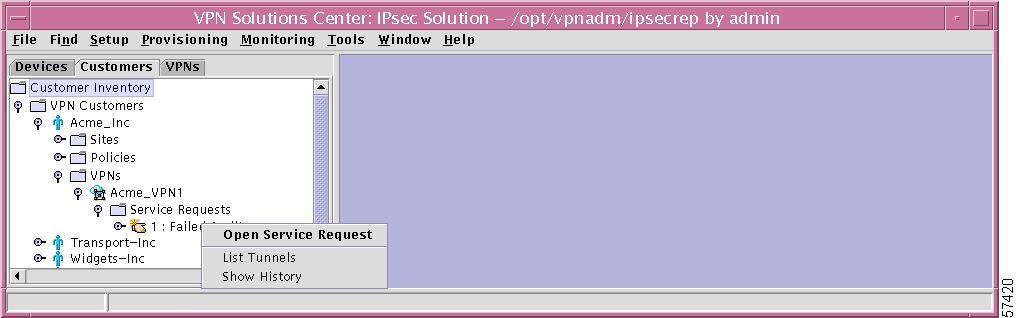
Specific Service Request
If you right-click on a specific Service Request in the hierarchy pane, you get a window as shown in Figure 12-41, "Specific Service Request Details," which gives you the opportunity to do the following:
•
Open Service Request Left-click on Open Service Request. The process is explained in detail in the "Add Service Request" section.
•
List Tunnels Left-click on List Tunnels. This gives you a report as shown in the "Tunnel List Report" section.
•
Show History Left-click on Show History. The resulting report is explained in detail in the "History Report" section.
Figure 12-41 Specific Service Request Details
Tunnels
If you right-click on Tunnels in the hierarchy pane, you get a window as shown in Figure 12-42, "Tunnels Choices," which gives you the opportunity to do the following:
•
Find Tunnel Left-click on Find Tunnel. The results are the same as explained in the "Find Tunnel" section.
•
Refresh Left-click on Refresh, which refreshes the hierarchy tree with the most current information.
Figure 12-42 Tunnels Choices
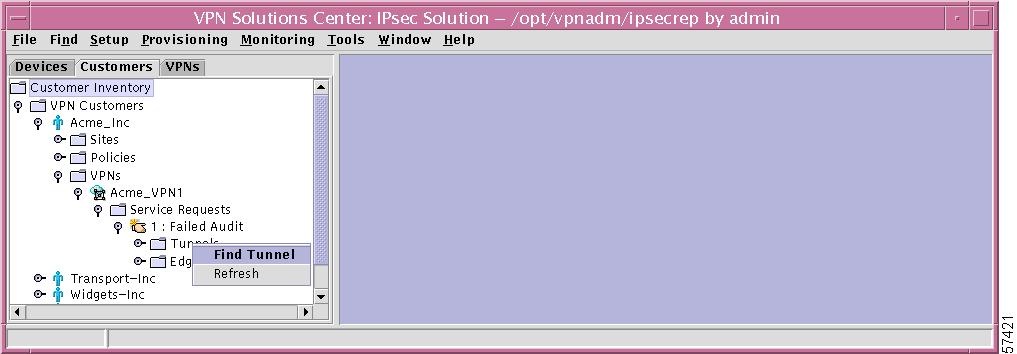
Specific Tunnel
If you right-click on a specific Tunnel in the hierarchy pane, you get a window as shown in Figure 12-43, "Specific Tunnel Choices," which gives you the opportunity to do the following:
•
Show Tunnel Report Left-click on Show Tunnel Report. This gives you a report as shown in the "Tunnel List Report" section, Step 2.

Note
An alternative to a right-click on any of the tunnels listed under Tunnels and then a left-click of Show Tunnel Report is to double left-click on any of the tunnels listed under Tunnels.
Figure 12-43 Specific Tunnel Choices
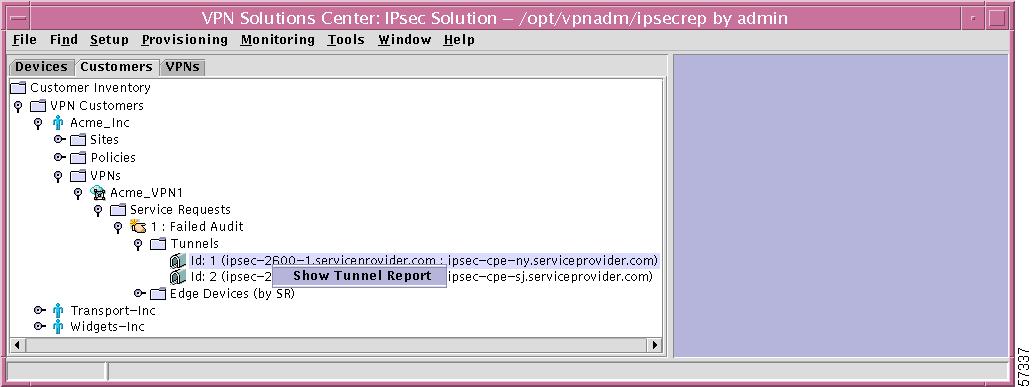
Edge Devices (by SR)
If you right-click on Edge Devices in the hierarchy pane, you get a window as shown in Figure 12-44, "Edge Devices Choices," which gives you the opportunity to do the following:
•
Find Edge Device Left-click on Find Edge Device. The results are the same as explained in the "Find Edge Device" section.
•
Refresh Left-click on Refresh, which refreshes the hierarchy tree with the most current information.
Figure 12-44 Edge Devices Choices
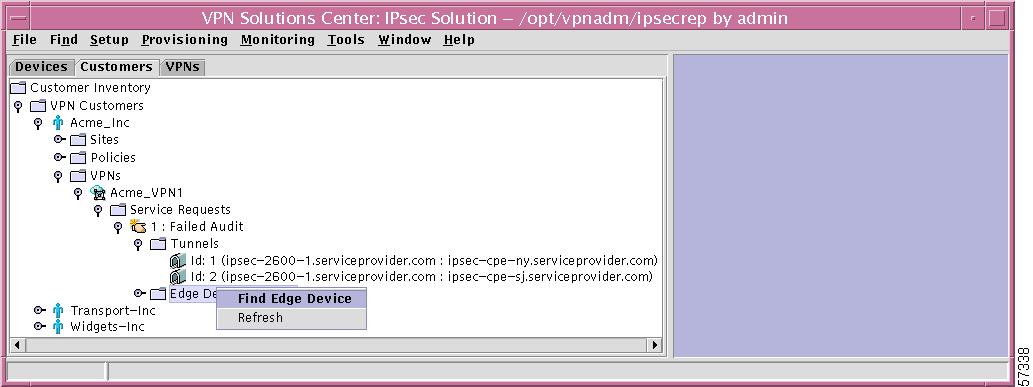
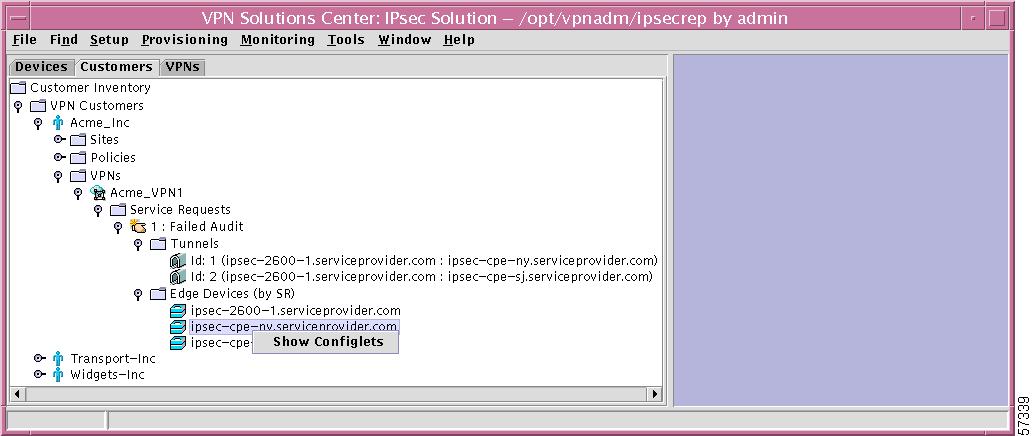
Specific Edge Device (by SR)
If you right-click on a specific Edge Device in the hierarchy pane, you get a window as shown in Figure 12-45, "Specific Edge Device Choices," which gives you the opportunity to do the following:
•
Show Configlets Left-click on Show Configlets. This gives you an Edge Device Configlets Report.

Note
An alternative to a right-click on any of the edge devices listed under Edge Devices (by SR) and then a left-click of Show Configlets is to double left-click on any of the edge devices listed under Edge Devices (by SR).
Figure 12-45 Specific Edge Device Choices
VPNs
In the hierarchy pane of the VPN Console window, you can click the VPNs tab and then completely expand VPNs. This shows all created VPNs, Service Requests, Tunnels, and Edge Devices, as shown in Figure 12-46, "VPNs Expanded."
Figure 12-46 VPNs Expanded
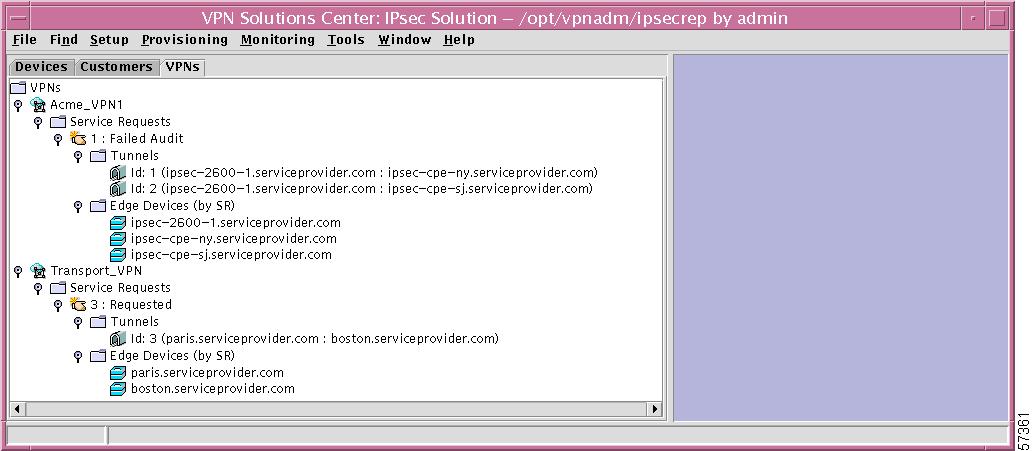
This section is explained in detail in the following subsections:
•
VPNs
The explanations are mapped to menu task bar explanations in other chapters.
VPNs
If you right-click on VPN s in the hierarchy pane, you get a window as shown in Figure 12-47, "VPNs Choices," which gives you the opportunity to do the following:
•
Find VPN Left-click on Find VPN. The results are the same as explained in the "Find VPN" section.
•
Refresh Left-click on Refresh to refresh the hierarchy tree with the most current information.
Figure 12-47 VPNs Choices
Specific VPN
If you right-click on a specific VPN in the hierarchy pane, you get a window as shown in Figure 12-48, "Specific VPN Choices," which gives you the opportunity to do the following:
•
Open VPN Left-click on Open VPN. This allows you to edit this specific VPN. This process is explained in detail in the "New VPN" section, Step 3.
•
Delete VPN Left-click on Delete VPN. You are asked to confirm whether you are sure you want to delete this VPN. Answer Yes to delete the VPN; or answer No not to delete the VPN.
•
List Service Requests Left-click on List Service Requests, which gives you a report as shown in the List All Service Requests, but which is specific to this VPN.
•
Audit Service Requests Left-click on Audit Service Requests, which is explained in the "Audit Service Requests" section.
•
Show Topology Left-click on Show Topology, which gives you topology information specific to this VPN. For more generic information about topologies, refer to Chapter 15, "Topology."
Figure 12-48 Specific VPN Choices
Service Requests
If you right-click on Service Requests in the hierarchy pane, you get a window as shown in Figure 12-49, "Service Requests Choices," which gives you the opportunity to do the following:
•
New Service Request Left-click on New Service Request. The process is explained in detail in the "Add Service Request" section.
•
Find Service Request Left-click on Find Service Request. The results are the same as explained in the "Find Service Request" section.
•
Refresh Left-click on Refresh, which refreshes the screen with the most current information.
Figure 12-49 Service Requests Choices
Specific Service Request
If you right-click on a specific Service Request in the hierarchy pane, you get a window as shown in Figure 12-50, "Specific Service Request Details," which gives you the opportunity to do the following:
•
Open Service Request Left-click on Open Service Request. The process is explained in detail in the "Add Service Request" section.
•
List Tunnels Left-click on List Tunnels. This gives you a report as shown in the "Tunnel List Report" section.
•
Show History Left-click on Show History. The resulting report is explained in detail in the "History Report" section.
Figure 12-50 Specific Service Request Details
Tunnels
If you right-click on Tunnels in the hierarchy pane, you get a window as shown in Figure 12-51, "Tunnels Choices," which gives you the opportunity to do the following:
•
Find Tunnel Left-click on Find Tunnel. The results are the same as explained in the "Find Tunnel" section.
•
Refresh Left-click on Refresh, which refreshes the hierarchy tree with the most current information.

Note
An alternative to a right-click on any of the tunnels listed under Tunnels and then a left-click of Show Tunnel Report is to double left-click on any of the tunnels listed under Tunnels.
Figure 12-51 Tunnels Choices
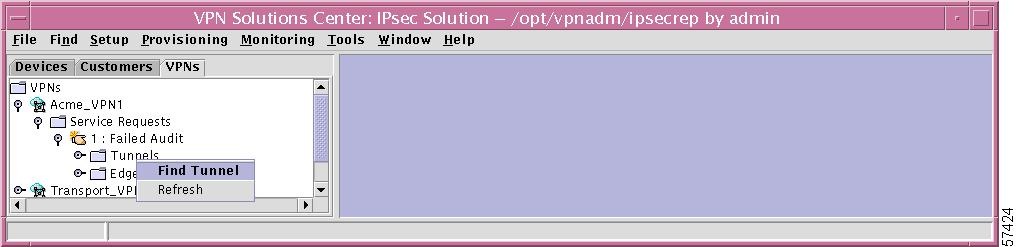
Specific Tunnel
If you right-click on a specific Tunnel in the hierarchy pane, you get a window as shown in Figure 12-52, "Specific Tunnel Choices," which gives you the opportunity to do the following:
•
Show Tunnel Report Left-click on Show Tunnel Report. This gives you a report as shown in the "Tunnel List Report" section, Step 2.
Figure 12-52 Specific Tunnel Choices
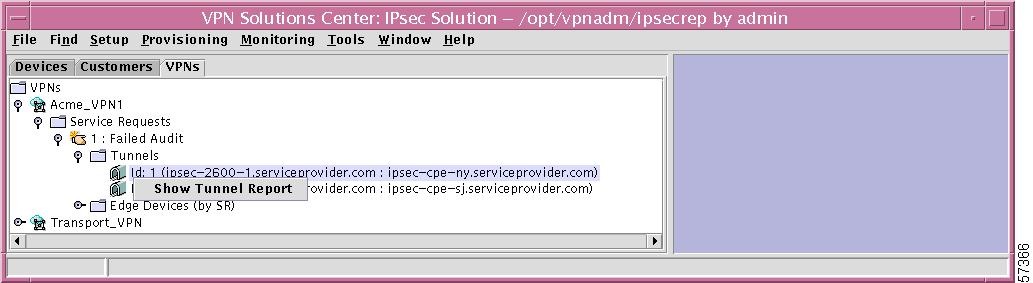
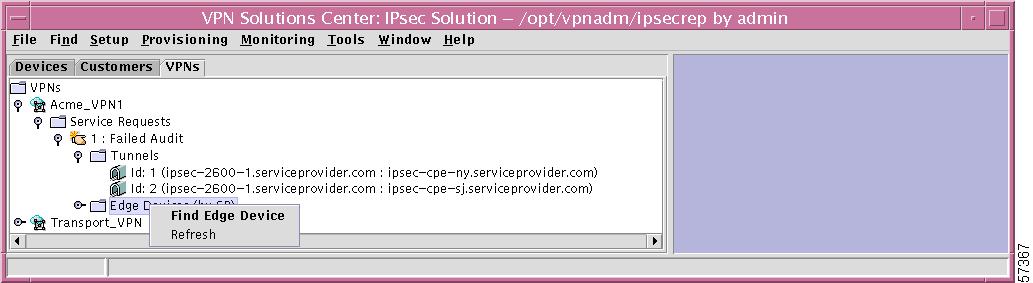
Edge Devices
If you right-click on Edge Devices in the hierarchy pane, you get a window as shown in Figure 12-53, "Edge Devices Choices," which gives you the opportunity to do the following:
•
Find Edge Device Left-click on Find Edge Device. The results are the same as explained in the "Find Edge Device" section.
•
Refresh Left-click on Refresh, which refreshes the hierarchy tree with the most current information.
Figure 12-53 Edge Devices Choices
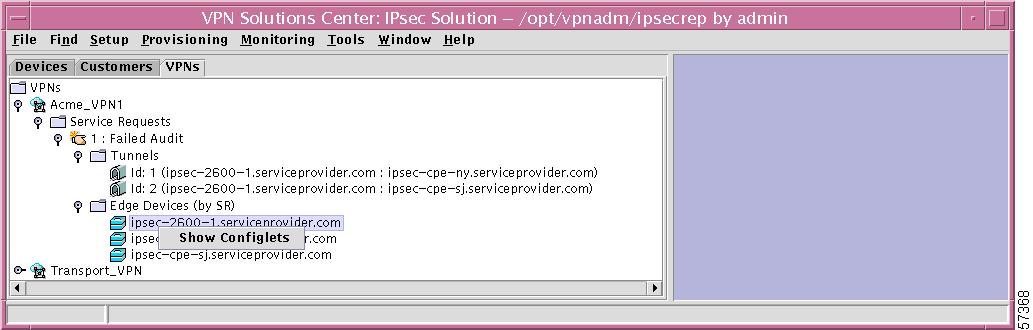
Specific Edge Device
If you right-click on a specific Edge Device in the hierarchy pane, you get a window as shown in Figure 12-54, "Specific Edge Device Choices," which gives you the opportunity to do the following:
•
Show Configlets Left-click on Show Configlets. This gives you an Edge Device Configlets Report.

Note
An alternative to a right-click on any of the edge devices listed under Edge Devices (by SR) and then a left-click of Show Configlets is to double left-click on any of the edge devices listed under Edge Devices (by SR).
Figure 12-54 Specific Edge Device Choices
Audit Service Requests
The Auditor verifies that a Service Request is correctly deployed or still exists on the router.
At the time of creation, the state transitions of a Service Request are performed by the provisioning system. This continues until the pending state. Beyond that it is the auditor's task to make the state transitions. It is a mechanism to monitor and report the current state of a VPN service request over its lifetime. It also provides the reasons why the service request is in its current state (audit detail). The Auditor also saves the state transition (if any) into the VPN Inventory Repository, known as the Repository. The lifetime of a VPN service request spans from the requested state to the closed state.
The valid states are: requested; pending; invalid; failed deploy; deployed; failed audit; lost; closed.
Table 12-1 describes each VPN Solutions Center service request state. They are listed in alphabetical order.
You can audit Service Requests through the following paths:
•
Audit Service Requests—for Specific Customer
•
Audit Service Requests—for Specific VPN (Customer Tab)
•
Audit Service Requests—for Specific VPN (VPN Tab)
Audit Service Requests—for Specific Customer
The Auditor verifies that a Service Request for a specific customer is correctly deployed.
Step 1
If you right-click on a specific Customer in the hierarchy pane, you get a window as shown in Figure 12-55, "Audit Service Requests—for Specific Customer."
Figure 12-55 Audit Service Requests—for Specific Customer
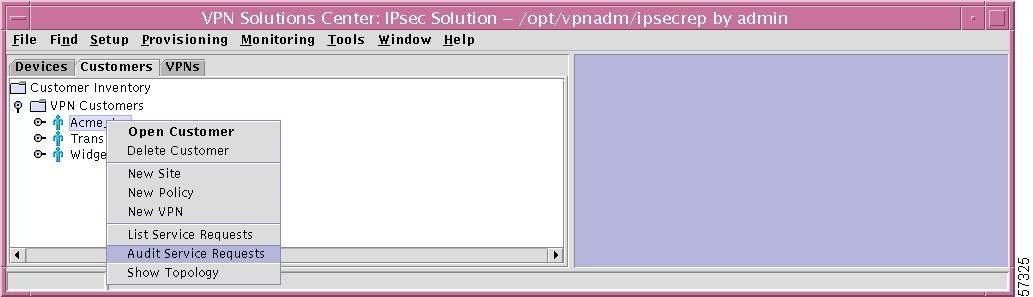
Step 2
Left click on Audit Service Requests and you will navigate to the Options tab window as shown in Figure 12-56, "Audit Specific Customer—Options Tab."
Figure 12-56 Audit Specific Customer—Options Tab

In this window, make the following choices:
•
Choose one of the three radio buttons that allows you to choose the service request(s) that you want to audit, as follows:
–
All service requests This selection will audit all service requests for this specific customer.
–
My own service request(s) only This selection will audit only the service requests created by the current user for this specific customer.
–
Selective service request(s) When you choose this radio button, press the Select button and you will receive a list of all the service requests from which you can select. Highlight the service requests you want to audit and click the OK button. If you decide not to make selections, click the Cancel button.
•
Choose whether to perform a just-in-time (jit) collection of router configurations before audit. This means the Auditor collects router configuration files in real time. There is no need to perform a scheduled collection before you run the Auditor.
Click the Yes radio button if you want to upload the configuration file from the router.
Click the No radio button if you want to use configuration files from the Repository.•
Click OK to choose the specified service requests. Click Cancel to exit this function
Step 3
Select the Schedule tab and you will navigate to the window as shown in Figure 12-57, "Audit Specific Customer—Schedule Tab."
Figure 12-57 Audit Specific Customer—Schedule Tab

In this window, follow this procedure:
a.
Enter an Unique Task Name In this field enter a unique task name. If you enter a duplicate name, you will receive an error message.
b.
The first time, click Add to add an entry for scheduling. The Schedule information then appears in the pane with the Status.
c.
Repeat the sequence of Enter an Unique Task Name and then clicking Add until all the tasks you want are in the pane.
d.
Once entries exist in the pane, you can select one or more of the entries and delete them by clicking Delete.
e.
For directions on how to specify the Schedule Information and Set Defaults, refer to Chapter 13, "Scheduling."
f.
Click OK to schedule the created tasks or click Cancel to exit the function.

Note
To view the Audit Reports, navigate from the menu task bar Provisioning > List All Service Requests > Tunnel List Report (bottom bar) > Tunnel Detail (bottom bar) > Audit Detail (bottom bar).
Errors and warnings are highlighted in yellow.
Audit Service Requests—for Specific VPN (Customer Tab)
The Auditor verifies that a Service Request for a specific VPN in the Customer tab is correctly deployed.
Step 1
If you right-click on a specific VPN from the VPN tab in the hierarchy pane, you get a window as shown in Figure 12-58, "Audit Service Requests—for Specific VPN (Customer Tab)."
Figure 12-58 Audit Service Requests—for Specific VPN (Customer Tab)
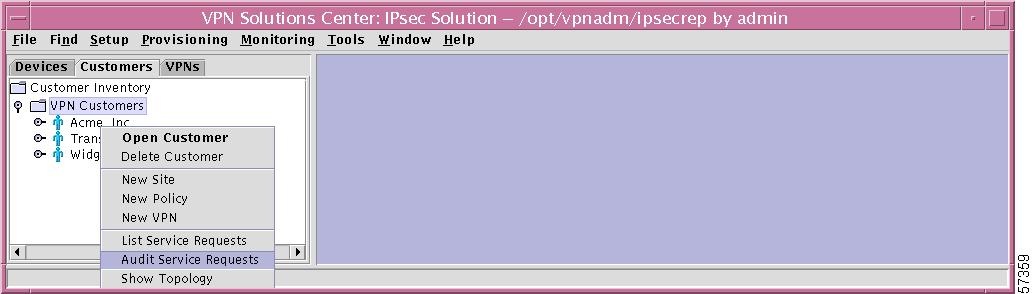
Step 2
Left click on Audit Service Requests and you will navigate to the Options tab window as shown in Figure 12-59, "Audit Specific VPN (Customer Tab)—Options Tab."
Figure 12-59 Audit Specific VPN (Customer Tab)—Options Tab
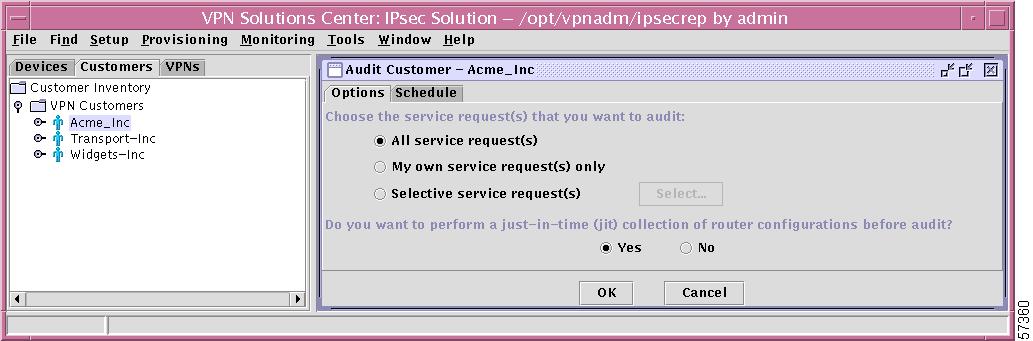
In this window, make the following choices:
•
Choose one of the three radio buttons that allows you to choose the service request(s) that you want to audit, as follows:
–
All service requests This selection will audit all service requests for this specific VPN.
–
My own service request(s) only This selection will audit only the service requests created by the current user for this specific VPN.
–
Selective service request(s) When you choose this radio button, press the Select button and you will receive a list of all the service requests from which you can select. Highlight the service requests you want to audit and click the OK button. If you decide not to make selections, click the Cancel button.
•
Choose whether to perform a just-in-time (jit) collection of router configurations before audit. This means the Auditor collects router configuration files in real time. There is no need to perform a scheduled collection before you run the Auditor.
Click the Yes radio button if you want to upload the configuration file from the router.
Click the No radio button if you want to use configuration files from the Repository.
•
Click OK to choose the specified service requests and method of audit routing, if any. Click Cancel to exit this function
Step 3
Select the Schedule tab and you will navigate to the window as shown in Figure 12-60, "Audit Specific VPN (Customer Tab)—Schedule Tab."
Figure 12-60 Audit Specific VPN (Customer Tab)—Schedule Tab

In this window, follow this procedure:
a.
Enter an Unique Task Name In this field enter a unique task name. If you enter a duplicate name, you will receive an error message.
b.
The first time, click Add to add an entry for scheduling. The Schedule information then appears in the pane with the Status.
c.
Repeat the sequence of Enter an Unique Task Name and then clicking Add until all the tasks you want are in the pane.
d.
Once entries exist in the pane, you can select one or more of the entries and delete them by clicking Delete.
e.
For directions on how to specify the Schedule Information and Set Defaults, refer to Chapter 13, "Scheduling."
f.
Click OK to schedule the created tasks or click Cancel to exit the function.

Note
To view the Audit Reports, navigate from the menu task bar Provisioning > List All Service Requests > Tunnel List Report (bottom bar) > Tunnel Detail (bottom bar) > Audit Detail (bottom bar).
Errors and warnings are highlighted in yellow.
Audit Service Requests—for Specific VPN (VPN Tab)
The Auditor verifies that a Service Request for a specific VPN in the VPN tab is correctly deployed.
Step 1
If you right-click on a specific VPN from the Customer tab in the hierarchy pane, you get a window as shown in Figure 12-61, "Audit Service Requests—for Specific VPN (VPN Tab)."
Figure 12-61 Audit Service Requests—for Specific VPN (VPN Tab)
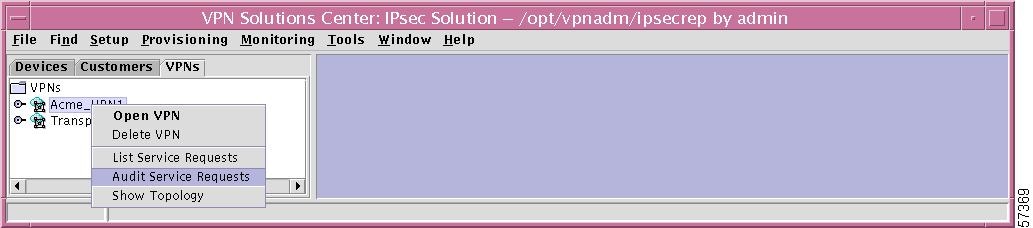
Step 2
Left click on Audit Service Requests and you will navigate to the Options tab window as shown in Figure 12-62, "Audit Specific VPN (VPN Tab)—Options Tab."
Figure 12-62 Audit Specific VPN (VPN Tab)—Options Tab
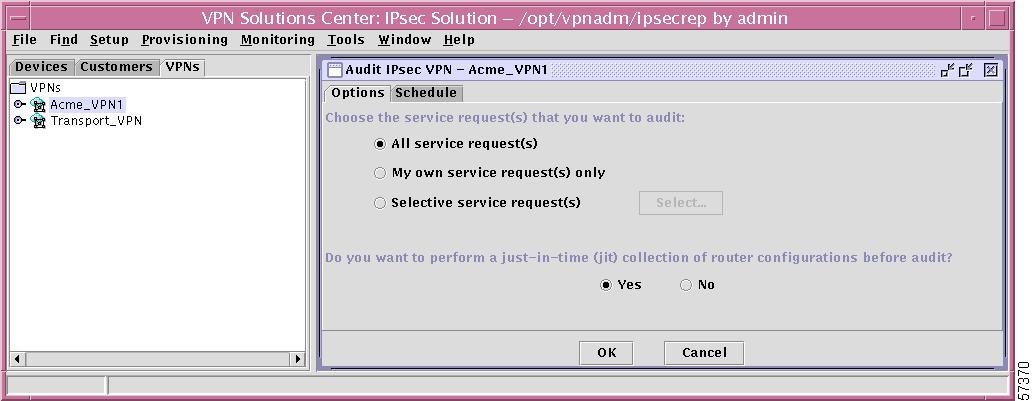
In this window, make the following choices:
•
Choose one of the three radio buttons that allows you to choose the service request(s) that you want to audit, as follows:
–
All service requests This selection will audit all service requests for this specific VPN.
–
My own service request(s) only This selection will audit only the service requests created by the current user for this specific VPN.
–
Selective service request(s) When you choose this radio button, press the Select button and you will receive a list of all the service requests from which you can select. Highlight the service requests you want to audit and click the OK button. If you decide not to make selections, click the Cancel button.
•
Choose whether to perform a just-in-time (jit) collection of router configurations before audit. This means the Auditor collects router configuration files in real time. There is no need to perform a scheduled collection before you run the Auditor.
Click the Yes radio button if you want to upload the configuration file from the router.
Click the No radio button if you want to use configuration files from the Repository.
•
Click OK to choose the specified service requests. Click Cancel to exit this function
Step 3
Select the Schedule tab and you will navigate to the window as shown in Figure 12-63, "Audit Specific VPN (VPN Tab)—Schedule Tab."
Figure 12-63 Audit Specific VPN (VPN Tab)—Schedule Tab
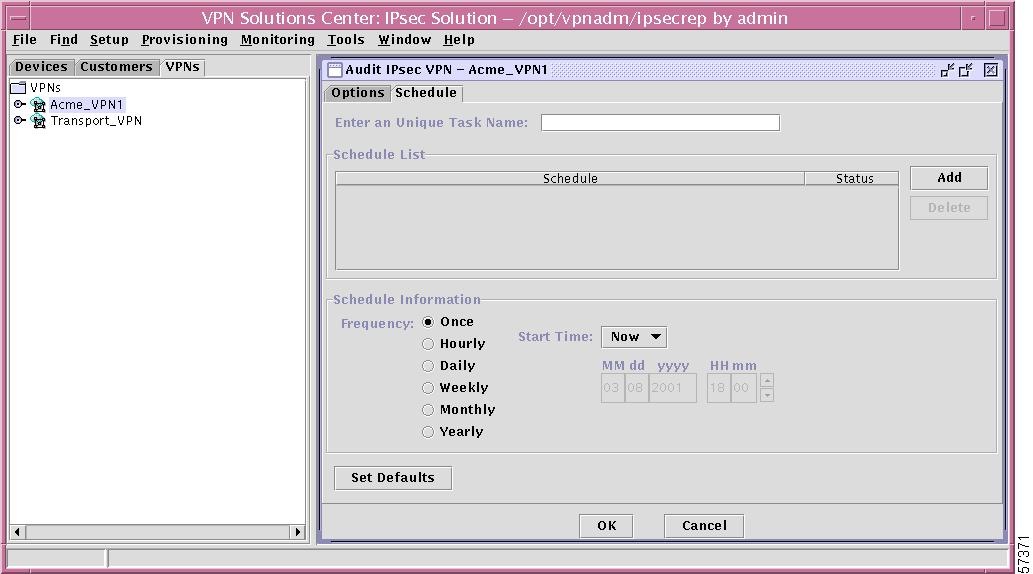
In this window, follow this procedure:
a.
Enter an Unique Task Name In this field enter a unique task name. If you enter a duplicate name, you will receive an error message.
b.
The first time, click Add to add an entry for scheduling. The Schedule information then appears in the pane with the Status.
c.
Repeat the sequence of Enter an Unique Task Name and then clicking Add until all the tasks you want are in the pane.
d.
Once entries exist in the pane, you can select one or more of the entries and delete them by clicking Delete.
e.
For directions on how to specify the Schedule Information and Set Defaults, refer to Chapter 13, "Scheduling."
f.
Click OK to schedule the created tasks or click Cancel to exit the function.

Note
To view the Audit Reports, navigate from the menu task bar Provisioning > List All Service Requests > Tunnel List Report (bottom bar) > Tunnel Detail (bottom bar) > Audit Detail (bottom bar).
Errors and warnings are highlighted in yellow.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback