RADIUS NAS-IP-Address Configurability
Available Languages
Table Of Contents
RADIUS NAS-IP-Address Attribute Configurability
Prerequisites for RADIUS NAS-IP-Address Attribute Configurability
Restrictions for RADIUS NAS-IP-Address Attribute Configurability
Information About RADIUS NAS-IP-Address Attribute Configurability
Problem Definition and Solution Background Information
Using the RADIUS NAS-IP-Address Attribute Configurability Feature
How to Configure RADIUS NAS-IP-Address Attribute Configurability
Configuring a RADIUS NAS-IP-Address Attribute Configurability
Monitoring and Maintaining RADIUS NAS-IP-Address Attribute Configurability
Configuration Examples for RADIUS NAS-IP-Address Attribute Configurability
Configuring a RADIUS NAS-IP-Address Attribute Configurability: Example
RADIUS NAS-IP-Address Attribute Configurability
The RADIUS NAS-IP-Address Attribute Configurability feature allows you to configure an arbitrary IP address to be used as RADIUS attribute 4, NAS-IP-Address, without changing the source IP address in the IP header of the RADIUS packets. This feature may be used for situations in which service providers are using a cluster of small network access servers (NASs) to simulate a large NAS to improve scalability. This feature allows the NASs to behave as a single RADIUS client from the perspective of the RADIUS server.
Feature History for RADIUS NAS-IP-Address Attribute Configurability
Finding Support Information for Platforms and Cisco IOS Software Images
Use Cisco Feature Navigator to find information about platform support and Cisco IOS software image support. Access Cisco Feature Navigator at http://www.cisco.com/go/fn. You must have an account on Cisco.com. If you do not have an account or have forgotten your username or password, click Cancel at the login dialog box and follow the instructions that appear.
Contents
•
Prerequisites for RADIUS NAS-IP-Address Attribute Configurability
•
Restrictions for RADIUS NAS-IP-Address Attribute Configurability
•
Information About RADIUS NAS-IP-Address Attribute Configurability
•
How to Configure RADIUS NAS-IP-Address Attribute Configurability
•
Configuration Examples for RADIUS NAS-IP-Address Attribute Configurability
Prerequisites for RADIUS NAS-IP-Address Attribute Configurability
•
You must be familiar with IP Security (IPSec).
•
You must be familiar with configuring both RADIUS servers and authentication, authorization, and accounting (AAA). Before configuring this feature, you must first set up the RADIUS server and the AAA lists.
Restrictions for RADIUS NAS-IP-Address Attribute Configurability
The following restrictions apply if a cluster of RADIUS clients are being used to simulate a single RADIUS client for scalability. Solutions, or workarounds, to the restrictions are also provided.
•
RADIUS attribute 44, Acct-Session-Id, may overlap among sessions from different NASs.
There are two solutions. Either the radius-server attribute 44 extend-with-addr or radius-server unique-ident command can be used on NAS routers to specify different prepending numbers for different NAS routers.
•
RADIUS server-based IP address pool for different NASs must be managed.
The solution is to configure different IP address pool profiles for different NASs on the RADIUS server. Different NASs use different pool usernames to retrieve them.
•
RADIUS request message for sessions from different NASs must be differentiated.
One of the solutions is to configure different format strings for RADIUS attribute 32, NAS-Identifier, using the radius-server attribute 32 include-in-access-req command on different NASs.
Information About RADIUS NAS-IP-Address Attribute Configurability
To configure the RADIUS NAS-IP-Address Attribute Configurability feature, you should understand the following concepts:
•
Problem Definition and Solution Background Information
•
Using the RADIUS NAS-IP-Address Attribute Configurability Feature
Problem Definition and Solution Background Information
To simulate a large NAS RADIUS client using a cluster of small NAS RADIUS clients, as shown in Figure 1, a Network Address Translation (NAT) or Port Address Translation (PAT) device is inserted in a network. The device is placed between a cluster of NASs and the IP cloud that is connected to a RADIUS server. When RADIUS traffic from different NASs goes through the NAT or PAT device, the source IP addresses of the RADIUS packets are translated to a single IP address, most likely an IP address on a loopback interface on the NAT or PAT device. Different User Datagram Protocol (UDP) source ports are assigned to RADIUS packets from different NASs. When the RADIUS reply comes back from the server, the NAT or PAT device receives it, uses the destination UDP port to translate the destination IP address back to the IP address of the NAS, and forwards the reply to the corresponding NAS.
Figure 1 demonstrates how the source IP addresses of several NASs are translated to a single IP address as they pass through the NAT or PAT device on the way to the IP cloud.
Figure 1 NAS Addresses Translated to a Single IP Address
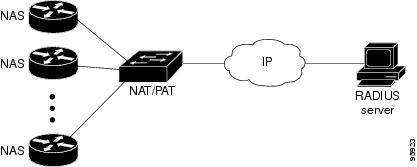
RADIUS servers normally check the source IP address in the IP header of the RADIUS packets to track the source of the RADIUS requests and to maintain security. The NAT or PAT solution satisfies these requirements because only a single source IP address is used even though RADIUS packets come from different NAS routers.
However, when retrieving accounting records from the RADIUS database, some billing systems use RADIUS attribute 4, NAS-IP-Address, in the accounting records. The value of this attribute is recorded on the NAS routers as their own IP addresses. The NAS routers are not aware of the NAT or PAT that runs between them and the RADIUS server; therefore, different RADIUS attribute 4 addresses will be recorded in the accounting records for users from the different NAS routers. These addresses eventually expose different NAS routers to the RADIUS server and to the corresponding billing systems.
Using the RADIUS NAS-IP-Address Attribute Configurability Feature
The RADIUS NAS-IP-Address Attribute Configurability feature allows you to freely configure an arbitrary IP address as RADIUS NAS-IP-Address, RADIUS attribute 4. By manually configuring the same IP address, most likely the IP address on the loopback interface of the NAT or PAT device, for all the routers, you can hide a cluster of NAS routers behind the NAT or PAT device from the RADIUS server.
How to Configure RADIUS NAS-IP-Address Attribute Configurability
This section contains the following procedures:
•
Configuring a RADIUS NAS-IP-Address Attribute Configurability
•
Monitoring and Maintaining RADIUS NAS-IP-Address Attribute Configurability
Configuring a RADIUS NAS-IP-Address Attribute Configurability
Before configuring the RADIUS NAS-IP-Address Attribute Configurability feature, you must have configured the RADIUS servers or server groups and AAA method lists.
To configure the RADIUS NAS-IP-Address Attribute Configurability feature, perform the following steps.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
radius-server attribute 4 ip-address
DETAILED STEPS
Monitoring and Maintaining RADIUS NAS-IP-Address Attribute Configurability
To monitor the RADIUS attribute 4 address that is being used inside the RADIUS packets, use the debug radius command.
SUMMARY STEPS
1.
enable
2.
debug radius
DETAILED STEPS
Examples
The following sample output is from the debug radius command:
Router# debug radiusRADIUS/ENCODE(0000001C): acct_session_id: 29RADIUS(0000001C): sendingRADIUS(0000001C): Send Access-Request to 10.0.0.10:1645 id 21645/17, len 81RADIUS: authenticator D0 27 34 C0 F0 C4 1C 1B - 3C 47 08 A2 7E E1 63 2FRADIUS: Framed-Protocol [7] 6 PPP [1]RADIUS: User-Name [1] 18 "shashi@pepsi.com"RADIUS: CHAP-Password [3] 19 *RADIUS: NAS-Port-Type [61] 6 Virtual [5]RADIUS: Service-Type [6] 6 Framed [2]RADIUS: NAS-IP-Address [4] 6 10.0.0.21UDP: sent src=10.1.1.1(21645), dst=10.0.0.10(1645), length=109UDP: rcvd src=10.0.0.10(1645), dst=10.1.1.1(21645), length=40RADIUS: Received from id 21645/17 10.0.0.10:1645, Access-Accept, len 32RADIUS: authenticator C6 99 EC 1A 47 0A 5F F2 - B8 30 4A 4C FF 4B 1D F0RADIUS: Service-Type [6] 6 Framed [2]RADIUS: Framed-Protocol [7] 6 PPP [1]RADIUS(0000001C): Received from id 21645/17Configuration Examples for RADIUS NAS-IP-Address Attribute Configurability
This section provides the following configuration example:
•
Configuring a RADIUS NAS-IP-Address Attribute Configurability: Example
Configuring a RADIUS NAS-IP-Address Attribute Configurability: Example
The following example shows that IP address 10.0.0.21 has been configured as the RADIUS NAS-IP-Address attribute:
radius-server attribute 4 10.0.0.21radius-server host 10.0.0.10 auth-port 1645 acct-port 1646 key ciscoAdditional References
The following sections provide references related to RADIUS NAS-IP-Address Attribute Configurability.
Related Documents
Configuring AAA
"Authentication, Authorization, and Accounting (AAA)" section of Cisco IOS Security Configuration Guide
Configuring RADIUS
"Configuring RADIUS" chapter of Cisco IOS Security Configuration Guide
RADIUS commands
Cisco IOS Security Command Reference, Release 12.3 T
Other security commands
Cisco IOS Security Command Reference, Release 12.3 T
Standards
MIBs
RFCs
Technical Assistance
Command Reference
This section documents the following new command.
radius-server attribute 4
To configure an IP address for the RADIUS attribute 4 address, use the radius-server attribute 4 command in global configuration mode. To delete an IP address as the RADIUS attribute 4 address, use the no form of this command.
radius-server attribute 4 ip-address
no radius-server attribute 4 ip-address
Syntax Description
Defaults
If this command is not configured, the RADIUS NAS-IP-Address attribute will be the IP address on the interface that connects the network access server (NAS) to the RADIUS server.
Command Modes
Global configuration
Command History
Usage Guidelines
Normally, when the ip radius-source interface command is configured, the IP address on the interface that is specified in the command is used as the IP address in the IP headers of the RADIUS packets and as the RADIUS attribute 4 address inside the RADIUS packets.
However, when the radius-server attribute 4 command is configured, the IP address in the command is used as the RADIUS attribute 4 address inside the RADIUS packets. There is no impact on the IP address in the IP headers of the RADIUS packets.
If both commands are configured, the IP address that is specified in the radius-server attribute 4 command is used as the RADIUS attribute 4 address inside the RADIUS packets. The IP address on the interface that is specified in the ip radius-source interface command is used as the IP address in the IP headers of the RADIUS packets.
Some authentication, authorization, and accounting (AAA) clients (such as PPP, virtual private dial-up network [VPDN] or Layer 2 Tunneling Protocol [L2TP], Voice over IP [VoIP], or Service Selection Gateway [SSG]) may try to set the RADIUS attribute 4 address using client-specific values. For example, on an L2TP network server (LNS), the IP address of the L2TP access concentrator (LAC) could be specified as the RADIUS attribute 4 address using a VPDN or L2TP command. When the radius-server attribute 4 command is configured, the IP address specified in the command takes precedence over all IP addresses from AAA clients.
During RADIUS request retransmission and during RADIUS server failover, the specified IP address is always chosen as the value of the RADIUS attribute 4 address.
Examples
The following example shows that the IP address 10.0.0.21 has been configured as the RADIUS NAS-IP-Address attribute:
radius-server attribute 4 10.0.0.21radius-server host 10.0.0.10 auth-port 1645 acct-port 1646 key ciscoThe following debug radius command output shows that 10.0.0.21 has been successfully configured.
Router# debug radiusRADIUS/ENCODE(0000001C): acct_session_id: 29RADIUS(0000001C): sendingRADIUS(0000001C): Send Access-Request to 10.0.0.10:1645 id 21645/17, len 81RADIUS: authenticator D0 27 34 C0 F0 C4 1C 1B - 3C 47 08 A2 7E E1 63 2FRADIUS: Framed-Protocol [7] 6 PPP [1]RADIUS: User-Name [1] 18 "shashi@pepsi.com"RADIUS: CHAP-Password [3] 19 *RADIUS: NAS-Port-Type [61] 6 Virtual [5]RADIUS: Service-Type [6] 6 Framed [2]RADIUS: NAS-IP-Address [4] 6 10.0.0.21UDP: sent src=11.1.1.1(21645), dst=10.0.0.10(1645), length=109UDP: rcvd src=10.0.0.10(1645), dst=10.1.1.1(21645), length=40RADIUS: Received from id 21645/17 10.0.0.10:1645, Access-Accept, len 32RADIUS: authenticator C6 99 EC 1A 47 0A 5F F2 - B8 30 4A 4C FF 4B 1D F0RADIUS: Service-Type [6] 6 Framed [2]RADIUS: Framed-Protocol [7] 6 PPP [1]RADIUS(0000001C): Received from id 21645/17Related Commands
ip radius-source interface
Forces RADIUS to use the IP address of a specified interface for all outgoing RADIUS packets.

Copyright © 2003-2005 Cisco Systems, Inc. All rights reserved
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback