Subscriber Service Switch
Available Languages
Table Of Contents
Restrictions for Subscriber Service Switch
Information About Subscriber Service Switch
Benefits of Subscriber Service Switch
How to Use Subscriber Service Switch
Enabling Domain Preauthorization on a LAC
Creating a RADIUS User Profile for Domain Preauthorization
Enabling Subscriber Service Switch Preauthorization
Verifying Subscriber Service Switch Call Operation
Troubleshooting the Subscriber Service Switch
Debug Commands Available for Subscriber Service Switch
Troubleshoot the Subscriber Service Switch
Configuration Examples for Subscriber Service Switch
Enable LAC Domain Authorization Example
Domain Preauthorization RADIUS User Profile Example
Enable Subscriber Service Switch Preauthorization Example
Verify Subscriber Service Switch Call Operation Example
Troubleshoot Subscriber Service Switch Examples
Troubleshoot the Subscriber Service Switch Operation Example
Troubleshoot the Subscriber Service Switch on the LAC—Normal Operation Example
Troubleshoot the Subscriber Service Switch on the LAC—Authorization Failure Example
Troubleshoot the Subscriber Service Switch on the LAC—Authentication Failure Example
Troubleshoot the Subscriber Service Switch at the LNS—Normal Operation Example
Troubleshoot the Subscriber Service Switch at the LNS—Tunnel Failure Example
debug sss aaa authorization event
debug sss aaa authorization fsm
subscriber authorization enable
Subscriber Service Switch
The Subscriber Service Switch provides flexibility on where and how many subscribers are connected to available services and how those services are defined. The primary focus of Subscriber Service Switch is to direct PPP from one point to another using a Layer 2 subscriber policy. The policy will manage tunneling of PPP in a policy-based bridging fashion.
Feature Specifications for the Subscriber Service Switch Feature
12.2(13)T
This feature was introduced.
12.2(27)SBA
This feature was integrated into Cisco IOS Release 12.2(27)SBA.
Finding Support Information for Platforms and Cisco IOS Software Images
Use Cisco Feature Navigator to find information about platform support and Cisco IOS software image support. Access Cisco Feature Navigator at http://www.cisco.com/go/fn. You must have an account on Cisco.com. If you do not have an account or have forgotten your username or password, click Cancel at the login dialog box and follow the instructions that appear.
Contents
•
Restrictions for Subscriber Service Switch
•
Information About Subscriber Service Switch
•
How to Use Subscriber Service Switch
•
Configuration Examples for Subscriber Service Switch
Restrictions for Subscriber Service Switch
Subscriber Service Switch provides the framework for the management and scalability of PPP sessions that are switched from one virtual PPP link to another. Subscriber Service Switch will provide the infrastructure for any protocol to plug into, but the initial focus will be on switching PPP over Ethernet (PPPoE) and PPP over ATM (PPPoA) sessions to a Layer 2 Tunneling Protocol (L2TP) devices such as an L2TP access concentrator (LAC) switch, and switching L2TP sessions to an L2TP tunnel switch.
Information About Subscriber Service Switch
To configure Subscriber Service Switch, you need to understand the following concepts:
•
Benefits of Subscriber Service Switch
Benefits of Subscriber Service Switch
The Subscriber Service Switch was developed in response to a need by Internet service providers for increased scalability and extensibility for remote access service selection and Layer 2 subscriber policy management. This Layer 2 subscriber policy is needed to manage tunneling of PPP in a policy-based bridging fashion.
Subscriber Service Switch provides flexibility on where and how many subscribers are connected to available services and how those services are defined. In the past, remote access service selection was largely determined by the telephone number dialed or the PPP username and password entered during a PPP authentication cycle. However, emerging broadband, cable, Virtual Private Network (VPN), and wireless access methods have created an environment where PPP sessions may be tunneled over a variety of protocols and media. The multitude of protocols, management domains, network infrastructure, and variety of services has created a complex environment for directing a subscriber to a given service or application. The problem is further augmented by the much greater density of total PPP sessions that can be transported over shared media versus traditional point-to-point links. Subscriber Service Switch can provide a flexible and extensible decision point linking an incoming subscriber (typically a PPP session over some physical or virtual link) to another tunneled link or local termination for Layer 3 processing.
Subscriber Service Switch is also scalable in situations where a subscriber's Layer 2 service is switched across virtual links. Examples include switching between PPPoA, PPPoE, L2TP, Layer 2 Forwarding Protocol (L2F), Point-to-Point Tunneling Protocol (PPTP), generic routing encapsulation (GRE) and General Packet Radio Service (GPRS) Tunneling Protocol (GTP wireless data standard).
Figure 1 shows how Subscriber Service Switch provides its own centralized switching path that bypasses the virtual access-based switching available in software prior to Cisco IOS Release 12.2(13)T. In the figure, Subscriber Service Switch is switching data traffic from personal computers in a home and corporate office, and from a wireless user.
Figure 1 BASIC Subscriber Service Switch Operation
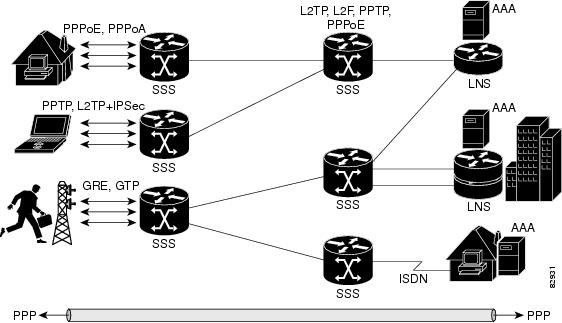
Protocols that register with the Subscriber Service Switch application programming interface (API) can take advantage of this new switching path. Bypassing the virtual access interface in this manner helps the Cisco IOS software to scale to the increased number of sessions that the market demands today. Subscriber Service Switch also markedly improves network performance, too. For example, benchmark testing indicates that performance of L2TP multihop tasks occurs twice as fast in networks with Subscriber Service Switch versus networks without it.
Backward Compatibility
All of the current virtual private dialup network (VPDN), Multichassis Multilink PPP (MMLP), and local termination policies and configurations will be maintained in this implementation of Subscriber Service Switch; however, default policies may be overridden by the following configurations or events:
•
Resource Manager (RM) VPDN authorization is attempted before VPDN authorization.
•
VPDN authorization is attempted before Stack Group Forwarding (SGF) MMLP.
•
VPDN service authorization is attempted only when the vpdn enable command is configured.
•
RM VPDN service authorization is attempted only if RM is enabled.
•
SGF authorization is attempted only when the sgbp member command is configured and one or both of the following service keys are available from the subscriber: unauthenticated PPP name and endpoint discriminator.
•
The dnis and domain service keys, in that order, are used to authorize VPDN service, provided that VPDN service is enabled. The order may be changed with the vpdn search-order global command, which may include multihop-hostname as a service key.
•
An unauthenticated PPP name is always reduced to a domain name by taking all characters from the right of the PPP name up to a configurable delimiter character (default is the @ character). Only the domain portion is used to locate a service.
•
If the vpdn authen-before-forward command is configured as a global configuration command, the authenticated PPP name is used to authorize VPDN service.
•
The configuration defined by the vpdn-group command can specify four things:
1.
Authorization for VPDN call termination (using the accept-dialin and accept-dialout keywords).
2.
Authorization for VPDN subscriber service (using the request-dialin and request-dialout keywords).
3.
A directive to collect further service keys and reauthorize (using the authen-before-forward keyword).
4.
A tunnel configuration.
Subscriber Service Switch adds a general configuration framework to replace the first three aspects of a VPDN group.
•
If VPDN and SGF services either are not configured or cannot be authorized, local PPP termination service is selected. Further PPP authorization is still required to complete local termination.
•
A two-phase authorization scheme is enabled by the vpn domain authorization command. An NAS-Port-ID (NAS port identifier) key is used to locate the first service record, which contains a restricted set of values for the domain substring of the unauthenticated PPP name. This filtered service key then locates the final service. Cisco refers to this scheme as domain preauthorization.
•
Domain preauthorization will occur only when the NAS-Port-ID key is available.
•
When domain preauthorization is enabled, both authenticated and unauthenticated domain names are checked for restrictions.
•
It is possible to associate a fixed service with an ATM permanent virtual circuit (PVC), thus affecting any subscribers carried by the PVC. The vpn service command, in ATM VC or VC class configuration mode, and the associated key make up the generic service key.
•
When the generic service key is available, it will be used for authorization instead of the unauthenticated domain name.
•
If either the vpdn authen-before-forward or per vpdn-group authen-before-forward command is configured, the authenticated username is required and will be used to authorize VPDN service.
•
To determine whether the authen-before-forward command is configured in a VPDN group (using the vpdn-group command), an unauthenticated username or the generic service key is required as the initial-want key set.
•
When the global vpdn authen-before-forward command is not configured, the generic service key, if one is available, is used to determine whether the authen-before-forward function is configured in the VPDN group (using the vpdn-group command). If the generic service key is not available, the unauthenticated username will be used.
•
If an accounting-enabled key is available, the unauthenticated username is required.
•
VPDN multihop is allowed only when VPDN multihop is enabled.
•
SGF on the L2TP network server (LNS) is allowed only when VPDN multihop is enabled on the LNS.
•
Forwarding of SGF calls on the LAC is only allowed if VPDN multihop is enabled on the LAC.
•
SGF-to-SGF multihop is not allowed.
•
When PPP forwarding is configured, both MLP and non-MLP calls are forwarded to the winner of the Stack Group Bidding Protocol (SGBP) bid.
•
Authentication is always required for forwarded Packet Data Serving Node (PDSN) calls.
•
When the directed-request function is enabled and activated using the ip host command (legacy behavior), VPDN service authorization occurs only when the vpdn authorize directed-request function is enabled.
•
Fixed legacy policy is still maintained for RM.
How to Use Subscriber Service Switch
The Subscriber Service Switch architecture is transparent, and existing PPP, VPDN, PPPoE, PPPoA, and authentication, authorization, and accounting (AAA) call configurations will continue to work in this new environment. You can, however, enable Subscriber Service Switch preauthorization and Subscriber Service Switch type authorization. You may also find it helpful to verify Subscriber Service Switch call operation.
This section contains the following optional procedures:
•
Enabling Domain Preauthorization on a LAC (optional)
•
Enabling Subscriber Service Switch Preauthorization(optional)
•
Verifying Subscriber Service Switch Call Operation (optional)
•
Troubleshooting the Subscriber Service Switch (optional)
Enabling Domain Preauthorization on a LAC
To enable the LAC to perform domain authorization before tunneling, perform the following steps:
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
vpdn authorize domain
4.
exit
5.
show running-config
6.
Create a RADIUS user profile for domain preauthorization
DETAILED STEPS
What to Do Next
See the next section and the "Domain Preauthorization RADIUS User Profile Example" on page 11.
Creating a RADIUS User Profile for Domain Preauthorization
Table 1 lists the attributes to enable domain preauthorization in a RADIUS user profile. Refer to the Cisco IOS Security Configuration Guide, Release 12.2, for information about creating a RADIUS user profile.
Enabling Subscriber Service Switch Preauthorization
When Subscriber Service Switch preauthorization is enabled on a LAC, local configurations for session limit per VC and per VLAN are overwritten by the per-NAS-port session limit downloaded from the server. To enable this preauthorization, perform the following steps:
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
subscriber access {pppoe | pppoa} pre-authorize nas-port-id [aaa-method-list]
4.
exit
DETAILED STEPS
Verifying Subscriber Service Switch Call Operation
To verify that the Subscriber Service Switch is working, perform the following optional steps:
SUMMARY STEPS
1.
enable
2.
show sss session [all]
DETAILED STEPS
What to Do Next
Information about troubleshooting a network running the Subscriber Service Switch can be found in the following "Troubleshooting the Subscriber Service Switch section.
Troubleshooting the Subscriber Service Switch
This section provides troubleshooting tips for the Subscriber Service Switch. Examples of normal and failure operations can be found in "Troubleshoot Subscriber Service Switch Examples" section on page 14. Reports from debug commands should be sent to technical personnel at Cisco Systems for evaluation.
Debug Commands Available for Subscriber Service Switch
The Subscriber Service Switch feature introduces five new EXEC mode debug commands to enable diagnostic output about Subscriber Service Switch call operation, as follows:
•
debug sss event—Displays diagnostic information about Subscriber Service Switch call setup events.
•
debug sss error—Displays diagnostic information about errors that may occur during Subscriber Service Switch call setup.
•
debug sss fsm—Displays diagnostic information about the Subscriber Service Switch call setup state.
•
debug sss aaa authorization event—Displays messages about AAA authorization events that are part of normal call establishment.
•
debug sss aaa authorization fsm—Displays messages about AAA authorization state changes.
These commands were designed to be used with Cisco IOS debug commands that exist for troubleshooting PPP and other Layer 2 call operations. Table 2 lists some of these debug commands.

Note
The commands are intended only for troubleshooting purposes, because the volume of output generated by the software can result in severe performance degradation on the router.
Troubleshoot the Subscriber Service Switch
To troubleshoot a network running the Subscriber Service Switch, perform the following steps:
SUMMARY STEPS
1.
Attach a console directly to a router running the Cisco IOS Release 12.2(13)T or a later release.
2.
enable
3.
configure terminal
4.
no logging console
5.
Use Telnet to access a router port and repeat Steps 2 and 3.
6.
terminal monitor
7.
exit
8.
debug command
9.
configure {terminal | memory | network}
10.
no terminal monitor
11.
exit
DETAILED STEPS
Configuration Examples for Subscriber Service Switch
This section provides the following configuration examples:
•
Enable LAC Domain Authorization Example
•
Domain Preauthorization RADIUS User Profile Example
•
Enable Subscriber Service Switch Preauthorization Example
•
Verify Subscriber Service Switch Call Operation Example
•
Troubleshoot Subscriber Service Switch Examples
Enable LAC Domain Authorization Example
The following example shows the configuration necessary for the LAC to participate in domain preauthorization:
!aaa new-modelaaa authorization network default local group radius!vpdn authorize domain!radius-server host 10.9.9.9 auth-port 1645 acct-port 1646radius-server attribute nas-port format dradius-server key MyKeyradius-server vsa send authentication!Domain Preauthorization RADIUS User Profile Example
The following example shows a typical domain preauthorization RADIUS user profile:
user = nas-port:10.9.9.9:0/0/0/30.33{profile_id = 826profile_cycle = 1radius=Cisco {check_items= {2=cisco}reply_attributes= {9,1="vpdn:vpn-domain-list=net1.com,net2.com"6=5}}}Enable Subscriber Service Switch Preauthorization Example
The following partial example signals Subscriber Service Switch to preauthorize the NAS-Port-ID string before authorizing the domain name. This policy applies only to all sessions with a PPPoE access type.
vpdn-group 3accept dialinprotocol pppoevirtual-template 1!! Signals Subscriber Service Switch to preauthorize the NAS-Port-ID string before! authorizing the domain name.subscriber access pppoe pre-authorize nas-port-id mlist_llid!Verify Subscriber Service Switch Call Operation Example
The following example command output from the show sss session all command provides an extensive report of Subscriber Service Switch session activity. The text in bold shows the unique identifier for each session, which can be used to correlate that particular session with the session information retrieved from other show commands or debug command traces. See the following show vpdn session command output for an example of this unique ID correlation.
Router# show sss session allCurrent SSS Information: Total sessions 9SSS session handle is 40000013, state is connected, service is VPDNUnique ID is 9SIP subscriber access type(s) are PPPoE/PPPIdentifier is nobody3@xyz.comLast Changed 00:02:49Root SIP Handle is DF000010, PID is 49AAA unique ID is 10Current SIP options are Req Fwding/Req FwdedSSS session handle is B0000017, state is connected, service is VPDNUnique ID is 10SIP subscriber access type(s) are PPPoE/PPPIdentifier is nobody3@xyz.comLast Changed 00:02:05Root SIP Handle is B9000015, PID is 49AAA unique ID is 11Current SIP options are Req Fwding/Req FwdedSSS session handle is D6000019, state is connected, service is VPDNUnique ID is 11SIP subscriber access type(s) are PPPoE/PPPIdentifier is nobody3@xyz.comLast Changed 00:02:13Root SIP Handle is D0000016, PID is 49AAA unique ID is 12Current SIP options are Req Fwding/Req FwdedSSS session handle is 8C000003, state is connected, service is VPDNUnique ID is 3SIP subscriber access type(s) are PPPoE/PPPIdentifier is user3@domain.comLast Changed 2d21hRoot SIP Handle is D3000002, PID is 49AAA unique ID is 3Current SIP options are Req Fwding/Req FwdedSSS session handle is BE00000B, state is connected, service is Local TermUnique ID is 6SIP subscriber access type(s) are PPPoE/PPPIdentifier is user1Last Changed 00:03:56Root SIP Handle is A9000009, PID is 49AAA unique ID is 7Current SIP options are Req Fwding/Req FwdedSSS session handle is DC00000D, state is connected, service is Local TermUnique ID is 7SIP subscriber access type(s) are PPPoE/PPPIdentifier is user2Last Changed 00:03:57Root SIP Handle is 2C00000A, PID is 49AAA unique ID is 8Current SIP options are Req Fwding/Req FwdedSSS session handle is DB000011, state is connected, service is VPDNUnique ID is 8SIP subscriber access type(s) are PPPoE/PPPIdentifier is nobody3@xyz.comLast Changed 00:02:58Root SIP Handle is 1000000F, PID is 49AAA unique ID is 9Current SIP options are Req Fwding/Req FwdedSSS session handle is 3F000007, state is connected, service is Local TermUnique ID is 2SIP subscriber access type(s) are PPPIdentifier is useruserLast Changed 00:05:30Root SIP Handle is 8A000009, PID is 92AAA unique ID is 1Current SIP options are Req Fwding/Req FwdedSSS session handle is 97000005, state is connected, service is VPDNUnique ID is 4SIP subscriber access type(s) are PPPIdentifier is nobody2@<domain>.comLast Changed 00:07:16Root SIP Handle is 32000000, PID is 92AAA unique ID is 5Current SIP options are Req Fwding/Req FwdedCorrelating the Unique ID in show vpdn session all Command Output
The following partial sample output from the show vpdn session all command provides extensive reports on call activity for all L2TP, L2F, and PPPoE sessions, and identifies the unique ID for each session.
Router# show vpdn session allL2TP Session Information Total tunnels 1 sessions 4Session id 5 is up, tunnel id 13695Call serial number is 3355500002Remote tunnel name is User03Internet address is 10.0.0.63Session state is established, time since change 00:03:5352 Packets sent, 52 received2080 Bytes sent, 1316 receivedLast clearing of "show vpdn" counters neverSession MTU is 1464 bytesSession username is nobody3@xyz.comInterfaceRemote session id is 692, remote tunnel id 58582UDP checksums are disabledSSS switching enabledNo FS cached header information availableSequencing is offUnique ID is 8Session id 6 is up, tunnel id 13695Call serial number is 3355500003Remote tunnel name is User03Internet address is 10.0.0.63Session state is established, time since change 00:04:2252 Packets sent, 52 received2080 Bytes sent, 1316 receivedLast clearing of "show vpdn" counters neverSession MTU is 1464 bytesSession username is nobody3@xyz.comInterfaceRemote session id is 693, remote tunnel id 58582UDP checksums are disabledSSS switching enabledNo FS cached header information availableSequencing is offUnique ID is 9...Troubleshoot Subscriber Service Switch Examples
This section provides the following debugging session examples for a network running the Subscriber Service Switch:
•
Troubleshoot the Subscriber Service Switch Operation Example
•
Troubleshoot the Subscriber Service Switch on the LAC—Normal Operation Example
•
Troubleshoot the Subscriber Service Switch on the LAC—Authorization Failure Example
•
Troubleshoot the Subscriber Service Switch on the LAC—Authentication Failure Example
•
Troubleshoot the Subscriber Service Switch at the LNS—Normal Operation Example
•
Troubleshoot the Subscriber Service Switch at the LNS—Tunnel Failure Example

Note
Reports from debug commands should be sent to technical personnel at Cisco Systems for evaluation.
Troubleshoot the Subscriber Service Switch Operation Example
The following example shows the debug commands used and sample output for debugging Subscriber Service Switch operation:
Router# debug sss eventRouter# debug sss errorRouter# debug sss stateRouter# debug sss aaa authorization eventRouter# debug sss aaa authorization fsmSSS:SSS events debugging is onSSS error debugging is onSSS fsm debugging is onSSS AAA authorization event debugging is onSSS AAA authorization FSM debugging is on*Mar 4 21:33:18.248: SSS INFO: Element type is Access-Type, long value is 3*Mar 4 21:33:18.248: SSS INFO: Element type is Switch-Id, long value is -1509949436*Mar 4 21:33:18.248: SSS INFO: Element type is Nasport, ptr value is 6396882C*Mar 4 21:33:18.248: SSS INFO: Element type is AAA-Id, long value is 7*Mar 4 21:33:18.248: SSS INFO: Element type is AAA-ACCT_ENBL, long value is 1*Mar 4 21:33:18.248: SSS INFO: Element type is AccIe-Hdl, ptr value is 78000006*Mar 4 21:33:18.248: SSS MGR [uid:7]: Event service-request, state changed from wait-for-req to wait-for-auth*Mar 4 21:33:18.248: SSS MGR [uid:7]: Handling Policy Authorize (1 pending sessions)*Mar 4 21:33:18.248: SSS PM [uid:7]: Need the following key: Unauth-User*Mar 4 21:33:18.248: SSS PM [uid:7]: Received Service Request*Mar 4 21:33:18.248: SSS PM [uid:7]: Event <need keys>, State: initial-req to need-init-keys*Mar 4 21:33:18.248: SSS PM [uid:7]: Policy reply - Need more keys*Mar 4 21:33:18.248: SSS MGR [uid:7]: Got reply Need-More-Keys from PM*Mar 4 21:33:18.248: SSS MGR [uid:7]: Event policy-or-mgr-more-keys, state changed from wait-for-auth to wait-for-req*Mar 4 21:33:18.248: SSS MGR [uid:7]: Handling More-Keys event*Mar 4 21:33:20.256: SSS INFO: Element type is Unauth-User, string value is nobody@xyz.com*Mar 4 21:33:20.256: SSS INFO: Element type is AccIe-Hdl, ptr value is 78000006*Mar 4 21:33:20.256: SSS INFO: Element type is AAA-Id, long value is 7*Mar 4 21:33:20.256: SSS INFO: Element type is Access-Type, long value is 0*Mar 4 21:33:20.256: SSS MGR [uid:7]: Event service-request, state changed from wait-for-req to wait-for-auth*Mar 4 21:33:20.256: SSS MGR [uid:7]: Handling Policy Authorize (1 pending sessions)*Mar 4 21:33:20.256: SSS PM [uid:7]: Received More Initial Keys*Mar 4 21:33:20.256: SSS PM [uid:7]: Event <rcvd keys>, State: need-init-keys to check-auth-needed*Mar 4 21:33:20.256: SSS PM [uid:7]: Handling Authorization Check*Mar 4 21:33:20.256: SSS PM [uid:7]: Event <send auth>, State: check-auth-needed to authorizing*Mar 4 21:33:20.256: SSS PM [uid:7]: Handling AAA service Authorization*Mar 4 21:33:20.256: SSS PM [uid:7]: Sending authorization request for 'xyz.com'*Mar 4 21:33:20.256: SSS AAA AUTHOR [uid:7]:Event <make request>, state changed from idle to authorizing*Mar 4 21:33:20.256: SSS AAA AUTHOR [uid:7]:Authorizing key xyz.com*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:AAA request sent for key xyz.com*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Received an AAA pass*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Event <found service>, state changed from authorizing to complete*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Found service info for key xyz.com*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Event <free request>, state changed from complete to terminal*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Free request*Mar 4 21:33:20.264: SSS PM [uid:7]: Event <found>, State: authorizing to end*Mar 4 21:33:20.264: SSS PM [uid:7]: Handling Service Direction*Mar 4 21:33:20.264: SSS PM [uid:7]: Policy reply - Forwarding*Mar 4 21:33:20.264: SSS MGR [uid:7]: Got reply Forwarding from PM*Mar 4 21:33:20.264: SSS MGR [uid:7]: Event policy-start-service-fsp, state changed from wait-for-auth to wait-for-service*Mar 4 21:33:20.264: SSS MGR [uid:7]: Handling Connect-Forwarding-Service event*Mar 4 21:33:20.272: SSS MGR [uid:7]: Event service-fsp-connected, state changed from wait-for-service to connected*Mar 4 21:33:20.272: SSS MGR [uid:7]: Handling Forwarding-Service-Connected eventTroubleshoot the Subscriber Service Switch on the LAC—Normal Operation Example
The following example shows the debug commands used and sample output indicating normal operation of the Subscriber Service Switch on the LAC:
Router# debug sss eventRouter# debug sss errorRouter# debug sss aaa authorization eventRouter# debug sss aaa authorization fsmRouter# debug pppoe eventsRouter# debug pppoe errorsRouter# debug ppp negotiationRouter# debug vpdn l2x-eventsRouter# debug vpdn l2x-errorsRouter# debug vpdn sss eventsRouter# debug vpdn sss errorsRouter# debug vpdn call eventsRouter# debug vpdn call fsmRouter# debug vpdn eventsRouter# debug vpdn errorsSSS:SSS events debugging is onSSS error debugging is onSSS AAA authorization event debugging is onSSS AAA authorization FSM debugging is onPPPoE:PPPoE protocol events debugging is onPPPoE protocol errors debugging is onPPP:PPP protocol negotiation debugging is onVPN:L2X protocol events debugging is onL2X protocol errors debugging is onVPDN SSS events debugging is onVPDN SSS errors debugging is onVPDN call event debugging is onVPDN call FSM debugging is onVPDN events debugging is onVPDN errors debugging is on*Nov 15 12:23:52.523: PPPoE 0: I PADI R:0000.0c14.71d0 L:ffff.ffff.ffff 1/32ATM4/0.132*Nov 15 12:23:52.523: PPPoE 0: O PADO R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:23:52.527: PPPoE 0: I PADR R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:23:52.527: PPPoE : encap string prepared*Nov 15 12:23:52.527: [13]PPPoE 10: Access IE handle allocated*Nov 15 12:23:52.527: [13]PPPoE 10: pppoe SSS switch updated*Nov 15 12:23:52.527: [13]PPPoE 10: Service request sent to SSS*Nov 15 12:23:52.527: [13]PPPoE 10: Created R:00b0.c2e9.c870 L:0000.0c14.71d0 1/32ATM4/0.132*Nov 15 12:23:52.547: SSS INFO: Element type is Access-Type, long value is 3*Nov 15 12:23:52.547: SSS INFO: Element type is Switch-Id, long value is 2130706444*Nov 15 12:23:52.547: SSS INFO: Element type is Nasport, ptr value is 63C07288*Nov 15 12:23:52.547: SSS INFO: Element type is AAA-Id, long value is 14*Nov 15 12:23:52.547: SSS INFO: Element type is AccIe-Hdl, ptr value is B200000C*Nov 15 12:23:52.547: SSS MGR [uid:13]: Handling Policy Authorize (1 pendingsessions)*Nov 15 12:23:52.547: SSS PM [uid:13]: RM/VPDN disabled: RM/VPDN author not needed*Nov 15 12:23:52.547: SSS PM [uid:13]: Received Service Request*Nov 15 12:23:52.547: SSS PM [uid:13]: Handling Authorization Check*Nov 15 12:23:52.547: SSS PM [uid:13]: Policy requires 'Unauth-User' key*Nov 15 12:23:52.547: SSS PM [uid:13]: Policy reply - Need more keys*Nov 15 12:23:52.547: SSS MGR [uid:13]: Got reply Need-More-Keys from PM*Nov 15 12:23:52.547: SSS MGR [uid:13]: Handling More-Keys event*Nov 15 12:23:52.547: [13]PPPoE 10: State REQ_NASPORT Event MORE_KEYS*Nov 15 12:23:52.547: [13]PPPoE 10: O PADS R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:23:52.547: ppp13 PPP: Using default call direction*Nov 15 12:23:52.547: ppp13 PPP: Treating connection as a dedicated line*Nov 15 12:23:52.547: ppp13 PPP: Phase is ESTABLISHING, Active Open*Nov 15 12:23:52.547: ppp13 LCP: O CONFREQ [Closed] id 1 len 19*Nov 15 12:23:52.547: ppp13 LCP: MRU 1492 (0x010405D4)*Nov 15 12:23:52.547: ppp13 LCP: AuthProto CHAP (0x0305C22305)*Nov 15 12:23:52.547: ppp13 LCP: MagicNumber 0xB0EC4557 (0x0506B0EC4557)*Nov 15 12:23:52.547: [13]PPPoE 10: State START_PPP Event DYN_BIND*Nov 15 12:23:52.547: [13]PPPoE 10: data path set to PPP*Nov 15 12:23:52.571: ppp13 LCP: I CONFREQ [REQsent] id 1 len 14*Nov 15 12:23:52.571: ppp13 LCP: MRU 1492 (0x010405D4)*Nov 15 12:23:52.571: ppp13 LCP: MagicNumber 0x0017455D (0x05060017455D)*Nov 15 12:23:52.571: ppp13 LCP: O CONFACK [REQsent] id 1 len 14*Nov 15 12:23:52.571: ppp13 LCP: MRU 1492 (0x010405D4)*Nov 15 12:23:52.571: ppp13 LCP: MagicNumber 0x0017455D (0x05060017455D)*Nov 15 12:23:54.543: ppp13 LCP: TIMEout: State ACKsent*Nov 15 12:23:54.543: ppp13 LCP: O CONFREQ [ACKsent] id 2 len 19*Nov 15 12:23:54.543: ppp13 LCP: MRU 1492 (0x010405D4)*Nov 15 12:23:54.543: ppp13 LCP: AuthProto CHAP (0x0305C22305)*Nov 15 12:23:54.543: ppp13 LCP: MagicNumber 0xB0EC4557 (0x0506B0EC4557)*Nov 15 12:23:54.543: ppp13 LCP: I CONFACK [ACKsent] id 2 len 19*Nov 15 12:23:54.543: ppp13 LCP: MRU 1492 (0x010405D4)*Nov 15 12:23:54.543: ppp13 LCP: AuthProto CHAP (0x0305C22305)*Nov 15 12:23:54.543: ppp13 LCP: MagicNumber 0xB0EC4557 (0x0506B0EC4557)*Nov 15 12:23:54.543: ppp13 LCP: State is Open*Nov 15 12:23:54.543: ppp13 PPP: Phase is AUTHENTICATING, by this end*Nov 15 12:23:54.543: ppp13 CHAP: O CHALLENGE id 1 len 25 from "7200"*Nov 15 12:23:54.547: ppp13 CHAP: I RESPONSE id 1 len 38 from "nobody@xyz.com"*Nov 15 12:23:54.547: ppp13 PPP: Phase is FORWARDING, Attempting Forward*Nov 15 12:23:54.547: SSS INFO: Element type is Unauth-User, string value isnobody@xyz.com*Nov 15 12:23:54.547: SSS INFO: Element type is AccIe-Hdl, ptr value is B200000C*Nov 15 12:23:54.547: SSS INFO: Element type is AAA-Id, long value is 14*Nov 15 12:23:54.547: SSS INFO: Element type is Access-Type, long value is 0*Nov 15 12:23:54.547: SSS MGR [uid:13]: Handling Policy Authorize (1 pendingsessions)*Nov 15 12:23:54.547: SSS PM [uid:13]: Received More Keys*Nov 15 12:23:54.547: SSS PM [uid:13]: Handling Authorization Check*Nov 15 12:23:54.547: SSS PM [uid:13]: Handling AAA service Authorization*Nov 15 12:23:54.547: SSS PM [uid:13]: Sending authorization request for 'xyz.com'*Nov 15 12:23:54.547: SSS AAA AUTHOR [uid:13]:Event <make request>, state changedfrom idle to authorizing*Nov 15 12:23:54.547: SSS AAA AUTHOR [uid:13]:Authorizing key xyz.com*Nov 15 12:23:54.547: SSS AAA AUTHOR [uid:13]:AAA request sent for key xyz.com*Nov 15 12:23:54.551: SSS AAA AUTHOR [uid:13]:Received an AAA pass*Nov 15 12:23:54.551: SSS AAA AUTHOR [uid:13]:Event <found service>, state changedfrom authorizing to complete*Nov 15 12:23:54.551: SSS AAA AUTHOR [uid:13]:Found service info for key xyz.com*Nov 15 12:23:54.551: SSS AAA AUTHOR [uid:13]:Event <free request>, state changedfrom complete to terminal*Nov 15 12:23:54.551: SSS AAA AUTHOR [uid:13]:Free request*Nov 15 12:23:54.551: SSS PM [uid:13]: Handling Service Direction*Nov 15 12:23:54.551: SSS PM [uid:13]: Policy reply - Forwarding*Nov 15 12:23:54.551: SSS MGR [uid:13]: Got reply Forwarding from PM*Nov 15 12:23:54.551: SSS MGR [uid:13]: Handling Connect-Service event*Nov 15 12:23:54.551: VPDN CALL [uid:13]: Event connect req, state changed from idleto connecting*Nov 15 12:23:54.551: VPDN CALL [uid:13]: Requesting connection*Nov 15 12:23:54.551: VPDN CALL [uid:13]: Call request sent*Nov 15 12:23:54.551: VPDN MGR [uid:13]: Event client connect, state changed fromidle to connecting*Nov 15 12:23:54.551: VPDN MGR [uid:13]: Initiating compulsory connection to199.11.8.2*Nov 15 12:23:54.551: Tnl/Sn61510/7 L2TP: Session FS enabled*Nov 15 12:23:54.551: Tnl/Sn61510/7 L2TP: Session state change from idle towait-for-tunnel*Nov 15 12:23:54.551: uid:13 Tnl/Sn61510/7 L2TP: Create session*Nov 15 12:23:54.551: uid:13 Tnl/Sn61510/7 L2TP: O ICRQ to rp1 9264/0*Nov 15 12:23:54.551: [13]PPPoE 10: Access IE nas port called*Nov 15 12:23:54.555: Tnl61510 L2TP: Control channel retransmit delay set to 1seconds*Nov 15 12:23:54.555: uid:13 Tnl/Sn61510/7 L2TP: Session state change fromwait-for-tunnel to wait-reply*Nov 15 12:23:54.555: [13]PPPoE 10: State LCP_NEGO Event PPP_FWDING*Nov 15 12:23:54.559: uid:13 Tnl/Sn61510/7 L2TP: O ICCN to rp1 9264/13586*Nov 15 12:23:54.559: Tnl61510 L2TP: Control channel retransmit delay set to 1seconds*Nov 15 12:23:54.559: uid:13 Tnl/Sn61510/7 L2TP: Session state change fromwait-reply to established*Nov 15 12:23:54.559: uid:13 Tnl/Sn61510/7 L2TP: VPDN session up*Nov 15 12:23:54.559: VPDN MGR [uid:13]: Event peer connected, state changed fromconnecting to connected*Nov 15 12:23:54.559: VPDN MGR [uid:13]: Succeed to forward nobody@xyz.com*Nov 15 12:23:54.559: VPDN MGR [uid:13]: accounting start sent*Nov 15 12:23:54.559: VPDN CALL [uid:13]: Event connect ok, state changed fromconnecting to connected*Nov 15 12:23:54.559: VPDN CALL [uid:13]: Connection succeeded*Nov 15 12:23:54.559: SSS MGR [uid:13]: Handling Service-Connected event*Nov 15 12:23:54.559: ppp13 PPP: Phase is FORWARDED, Session Forwarded*Nov 15 12:23:54.559: [13]PPPoE 10: State LCP_NEGO Event PPP_FWDED*Nov 15 12:23:54.563: [13]PPPoE 10: data path set to SSS Switch*Nov 15 12:23:54.563: [13]PPPoE 10: Connected ForwardedTroubleshoot the Subscriber Service Switch on the LAC—Authorization Failure Example
The following is sample output indicating call failure due to authorization failure:
*Nov 15 12:37:24.535: PPPoE 0: I PADI R:0000.0c14.71d0 L:ffff.ffff.ffff 1/32ATM4/0.132*Nov 15 12:37:24.535: PPPoE 0: O PADO R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:37:24.539: PPPoE 0: I PADR R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:37:24.539: PPPoE : encap string prepared*Nov 15 12:37:24.539: [18]PPPoE 15: Access IE handle allocated*Nov 15 12:37:24.539: [18]PPPoE 15: pppoe SSS switch updated*Nov 15 12:37:24.539: PPPoE 15: AAA pppoe_aaa_acct_get_retrieved_attrs*Nov 15 12:37:24.539: [18]PPPoE 15: AAA pppoe_aaa_acct_get_nas_port_details*Nov 15 12:37:24.539: [18]PPPoE 15: AAA pppoe_aaa_acct_get_dynamic_attrs*Nov 15 12:37:24.539: [18]PPPoE 15: AAA pppoe_aaa_acct_get_dynamic_attrs*Nov 15 12:37:24.539: [18]PPPoE 15: AAA unique ID allocated*Nov 15 12:37:24.539: [18]PPPoE 15: No AAA accounting method list*Nov 15 12:37:24.539: [18]PPPoE 15: Service request sent to SSS*Nov 15 12:37:24.539: [18]PPPoE 15: Created R:00b0.c2e9.c870 L:0000.0c14.71d0 1/32ATM4/0.132*Nov 15 12:37:24.559: SSS INFO: Element type is Access-Type, long value is 3*Nov 15 12:37:24.559: SSS INFO: Element type is Switch-Id, long value is -738197487*Nov 15 12:37:24.559: SSS INFO: Element type is Nasport, ptr value is 63C0E590*Nov 15 12:37:24.559: SSS INFO: Element type is AAA-Id, long value is 19*Nov 15 12:37:24.559: SSS INFO: Element type is AccIe-Hdl, ptr value is 5B000011*Nov 15 12:37:24.559: SSS MGR [uid:18]: Handling Policy Authorize (1 pendingsessions)*Nov 15 12:37:24.559: SSS PM [uid:18]: RM/VPDN disabled: RM/VPDN author not needed*Nov 15 12:37:24.559: SSS PM [uid:18]: Received Service Request*Nov 15 12:37:24.559: SSS PM [uid:18]: Handling Authorization Check*Nov 15 12:37:24.559: SSS PM [uid:18]: Policy requires 'Unauth-User' key*Nov 15 12:37:24.559: SSS PM [uid:18]: Policy reply - Need more keys*Nov 15 12:37:24.559: SSS MGR [uid:18]: Got reply Need-More-Keys from PM*Nov 15 12:37:24.559: SSS MGR [uid:18]: Handling More-Keys event*Nov 15 12:37:24.559: [18]PPPoE 15: State REQ_NASPORT Event MORE_KEYS*Nov 15 12:37:24.559: [18]PPPoE 15: O PADS R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:37:24.559: ppp18 PPP: Using default call direction*Nov 15 12:37:24.559: ppp18 PPP: Treating connection as a dedicated line*Nov 15 12:37:24.559: ppp18 PPP: Phase is ESTABLISHING, Active Open*Nov 15 12:37:24.559: ppp18 LCP: O CONFREQ [Closed] id 1 len 19*Nov 15 12:37:24.559: ppp18 LCP: MRU 1492 (0x010405D4)*Nov 15 12:37:24.559: ppp18 LCP: AuthProto CHAP (0x0305C22305)*Nov 15 12:37:24.559: ppp18 LCP: MagicNumber 0xB0F8A971 (0x0506B0F8A971)*Nov 15 12:37:24.559: [18]PPPoE 15: State START_PPP Event DYN_BIND*Nov 15 12:37:24.559: [18]PPPoE 15: data path set to PPP*Nov 15 12:37:24.563: ppp18 LCP: I CONFREQ [REQsent] id 1 len 14*Nov 15 12:37:24.563: ppp18 LCP: MRU 1492 (0x010405D4)*Nov 15 12:37:24.563: ppp18 LCP: MagicNumber 0x0023A93E (0x05060023A93E)*Nov 15 12:37:24.563: ppp18 LCP: O CONFACK [REQsent] id 1 len 14*Nov 15 12:37:24.563: ppp18 LCP: MRU 1492 (0x010405D4)*Nov 15 12:37:24.563: ppp18 LCP: MagicNumber 0x0023A93E (0x05060023A93E)*Nov 15 12:37:26.523: ppp18 LCP: I CONFREQ [ACKsent] id 2 len 14*Nov 15 12:37:26.523: ppp18 LCP: MRU 1492 (0x010405D4)*Nov 15 12:37:26.523: ppp18 LCP: MagicNumber 0x0023A93E (0x05060023A93E)*Nov 15 12:37:26.523: ppp18 LCP: O CONFACK [ACKsent] id 2 len 14*Nov 15 12:37:26.527: ppp18 LCP: MRU 1492 (0x010405D4)*Nov 15 12:37:26.527: ppp18 LCP: MagicNumber 0x0023A93E (0x05060023A93E)*Nov 15 12:37:26.575: ppp18 LCP: TIMEout: State ACKsent*Nov 15 12:37:26.575: ppp18 LCP: O CONFREQ [ACKsent] id 2 len 19*Nov 15 12:37:26.575: ppp18 LCP: MRU 1492 (0x010405D4)*Nov 15 12:37:26.575: ppp18 LCP: AuthProto CHAP (0x0305C22305)*Nov 15 12:37:26.575: ppp18 LCP: MagicNumber 0xB0F8A971 (0x0506B0F8A971)*Nov 15 12:37:26.575: ppp18 LCP: I CONFACK [ACKsent] id 2 len 19*Nov 15 12:37:26.575: ppp18 LCP: MRU 1492 (0x010405D4)*Nov 15 12:37:26.575: ppp18 LCP: AuthProto CHAP (0x0305C22305)*Nov 15 12:37:26.575: ppp18 LCP: MagicNumber 0xB0F8A971 (0x0506B0F8A971)*Nov 15 12:37:26.575: ppp18 LCP: State is Open*Nov 15 12:37:26.575: ppp18 PPP: Phase is AUTHENTICATING, by this end*Nov 15 12:37:26.575: ppp18 CHAP: O CHALLENGE id 1 len 25 from "7200"*Nov 15 12:37:26.579: ppp18 CHAP: I RESPONSE id 1 len 38 from "nobody@xyz.com"*Nov 15 12:37:26.579: ppp18 PPP: Phase is FORWARDING, Attempting Forward*Nov 15 12:37:26.579: SSS INFO: Element type is Unauth-User, string value isnobody@xyz.com*Nov 15 12:37:26.579: SSS INFO: Element type is AccIe-Hdl, ptr value is 5B000011*Nov 15 12:37:26.579: SSS INFO: Element type is AAA-Id, long value is 19*Nov 15 12:37:26.579: SSS INFO: Element type is Access-Type, long value is 0*Nov 15 12:37:26.579: SSS MGR [uid:18]: Handling Policy Authorize (1 pendingsessions)*Nov 15 12:37:26.579: SSS PM [uid:18]: Received More Keys*Nov 15 12:37:26.579: SSS PM [uid:18]: Handling Authorization Check*Nov 15 12:37:26.579: SSS PM [uid:18]: Handling AAA service Authorization*Nov 15 12:37:26.579: SSS PM [uid:18]: Sending authorization request for 'xyz.com'*Nov 15 12:37:26.579: SSS AAA AUTHOR [uid:18]:Event <make request>, state changedfrom idle to authorizing*Nov 15 12:37:26.579: SSS AAA AUTHOR [uid:18]:Authorizing key xyz.com*Nov 15 12:37:26.579: SSS AAA AUTHOR [uid:18]:AAA request sent for key xyz.com*Nov 15 12:37:26.587: SSS AAA AUTHOR [uid:18]:Received an AAA failure*Nov 15 12:37:26.587: SSS AAA AUTHOR [uid:18]:Event <service not found>, statechanged from authorizing to complete*Nov 15 12:37:26.587: SSS AAA AUTHOR [uid:18]:No service authorization info found*Nov 15 12:37:26.587: SSS AAA AUTHOR [uid:18]:Event <free request>, state changedfrom complete to terminal*Nov 15 12:37:26.587: SSS AAA AUTHOR [uid:18]:Free request*Nov 15 12:37:26.587: SSS PM [uid:18]: Handling Next Authorization Check*Nov 15 12:37:26.587: SSS PM [uid:18]: Default policy: SGF author not needed*Nov 15 12:37:26.587: SSS PM [uid:18]: Handling Default Service*Nov 15 12:37:26.587: SSS PM [uid:18]: Policy reply - Local terminate*Nov 15 12:37:26.591: SSS MGR [uid:18]: Got reply Local-Term from PM*Nov 15 12:37:26.591: SSS MGR [uid:18]: Handling Send-Client-Local-Term event*Nov 15 12:37:26.591: ppp18 PPP: Phase is AUTHENTICATING, Unauthenticated User*Nov 15 12:37:26.595: ppp18 CHAP: O FAILURE id 1 len 25 msg is "Authenticationfailed"*Nov 15 12:37:26.599: ppp18 PPP: Sending Acct Event[Down] id[13]*Nov 15 12:37:26.599: ppp18 PPP: Phase is TERMINATING*Nov 15 12:37:26.599: ppp18 LCP: O TERMREQ [Open] id 3 len 4*Nov 15 12:37:26.599: ppp18 LCP: State is Closed*Nov 15 12:37:26.599: ppp18 PPP: Phase is DOWN*Nov 15 12:37:26.599: ppp18 PPP: Phase is TERMINATING*Nov 15 12:37:26.599: [18]PPPoE 15: State LCP_NEGO Event PPP_DISCNCT*Nov 15 12:37:26.599: [18]PPPoE 15: O PADT R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:37:26.599: [18]PPPoE 15: Destroying R:0000.0c14.71d0 L:00b0.c2e9.c8701/32 ATM4/0.132*Nov 15 12:37:26.599: [18]PPPoE 15: AAA account stopped*Nov 15 12:37:26.599: SSS MGR [uid:18]: Processing a client disconnect*Nov 15 12:37:26.599: SSS MGR [uid:18]: Handling Send-Service-Disconnect eventTroubleshoot the Subscriber Service Switch on the LAC—Authentication Failure Example
The following is sample output indicating call failure due to authentication failure at the LNS:
*Nov 15 12:45:02.067: PPPoE 0: I PADI R:0000.0c14.71d0 L:ffff.ffff.ffff 1/32ATM4/0.132*Nov 15 12:45:02.071: PPPoE 0: O PADO R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:45:02.071: PPPoE 0: I PADR R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:45:02.071: PPPoE : encap string prepared*Nov 15 12:45:02.071: [21]PPPoE 18: Access IE handle allocated*Nov 15 12:45:02.071: [21]PPPoE 18: pppoe SSS switch updated*Nov 15 12:45:02.071: PPPoE 18: AAA pppoe_aaa_acct_get_retrieved_attrs*Nov 15 12:45:02.071: [21]PPPoE 18: AAA pppoe_aaa_acct_get_nas_port_details*Nov 15 12:45:02.071: [21]PPPoE 18: AAA pppoe_aaa_acct_get_dynamic_attrs*Nov 15 12:45:02.071: [21]PPPoE 18: AAA pppoe_aaa_acct_get_dynamic_attrs*Nov 15 12:45:02.071: [21]PPPoE 18: AAA unique ID allocated*Nov 15 12:45:02.071: [21]PPPoE 18: No AAA accounting method list*Nov 15 12:45:02.071: [21]PPPoE 18: Service request sent to SSS*Nov 15 12:45:02.071: [21]PPPoE 18: Created R:00b0.c2e9.c870 L:0000.0c14.71d0 1/32ATM4/0.132*Nov 15 12:45:02.091: SSS INFO: Element type is Access-Type, long value is 3*Nov 15 12:45:02.091: SSS INFO: Element type is Switch-Id, long value is 1946157076*Nov 15 12:45:02.091: SSS INFO: Element type is Nasport, ptr value is 63B34170*Nov 15 12:45:02.091: SSS INFO: Element type is AAA-Id, long value is 22*Nov 15 12:45:02.091: SSS INFO: Element type is AccIe-Hdl, ptr value is 71000014*Nov 15 12:45:02.091: SSS MGR [uid:21]: Handling Policy Authorize (1 pendingsessions)*Nov 15 12:45:02.091: SSS PM [uid:21]: RM/VPDN disabled: RM/VPDN author not needed*Nov 15 12:45:02.091: SSS PM [uid:21]: Received Service Request*Nov 15 12:45:02.091: SSS PM [uid:21]: Handling Authorization Check*Nov 15 12:45:02.091: SSS PM [uid:21]: Policy requires 'Unauth-User' key*Nov 15 12:45:02.091: SSS PM [uid:21]: Policy reply - Need more keys*Nov 15 12:45:02.091: SSS MGR [uid:21]: Got reply Need-More-Keys from PM*Nov 15 12:45:02.091: SSS MGR [uid:21]: Handling More-Keys event*Nov 15 12:45:02.091: [21]PPPoE 18: State REQ_NASPORT Event MORE_KEYS*Nov 15 12:45:02.091: [21]PPPoE 18: O PADS R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:45:02.091: ppp21 PPP: Using default call direction*Nov 15 12:45:02.091: ppp21 PPP: Treating connection as a dedicated line*Nov 15 12:45:02.091: ppp21 PPP: Phase is ESTABLISHING, Active Open*Nov 15 12:45:02.091: ppp21 LCP: O CONFREQ [Closed] id 1 len 19*Nov 15 12:45:02.091: ppp21 LCP: MRU 1492 (0x010405D4)*Nov 15 12:45:02.091: ppp21 LCP: AuthProto CHAP (0x0305C22305)*Nov 15 12:45:02.091: ppp21 LCP: MagicNumber 0xB0FFA4D8 (0x0506B0FFA4D8)*Nov 15 12:45:02.091: [21]PPPoE 18: State START_PPP Event DYN_BIND*Nov 15 12:45:02.091: [21]PPPoE 18: data path set to PPP*Nov 15 12:45:02.095: ppp21 LCP: I CONFREQ [REQsent] id 1 len 14*Nov 15 12:45:02.095: ppp21 LCP: MRU 1492 (0x010405D4)*Nov 15 12:45:02.095: ppp21 LCP: MagicNumber 0x002AA481 (0x0506002AA481)*Nov 15 12:45:02.095: ppp21 LCP: O CONFACK [REQsent] id 1 len 14*Nov 15 12:45:02.095: ppp21 LCP: MRU 1492 (0x010405D4)*Nov 15 12:45:02.095: ppp21 LCP: MagicNumber 0x002AA481 (0x0506002AA481)*Nov 15 12:45:02.315: Tnl41436 L2TP: I StopCCN from rp1 tnl 31166*Nov 15 12:45:02.315: Tnl41436 L2TP: Shutdown tunnel*Nov 15 12:45:02.315: Tnl41436 L2TP: Tunnel state change from no-sessions-left toidle*Nov 15 12:45:04.055: ppp21 LCP: I CONFREQ [ACKsent] id 2 len 14*Nov 15 12:45:04.055: ppp21 LCP: MRU 1492 (0x010405D4)*Nov 15 12:45:04.059: ppp21 LCP: MagicNumber 0x002AA481 (0x0506002AA481)*Nov 15 12:45:04.059: ppp21 LCP: O CONFACK [ACKsent] id 2 len 14*Nov 15 12:45:04.059: ppp21 LCP: MRU 1492 (0x010405D4)*Nov 15 12:45:04.059: ppp21 LCP: MagicNumber 0x002AA481 (0x0506002AA481)*Nov 15 12:45:04.079: ppp21 LCP: TIMEout: State ACKsent*Nov 15 12:45:04.079: ppp21 LCP: O CONFREQ [ACKsent] id 2 len 19*Nov 15 12:45:04.079: ppp21 LCP: MRU 1492 (0x010405D4)*Nov 15 12:45:04.079: ppp21 LCP: AuthProto CHAP (0x0305C22305)*Nov 15 12:45:04.079: ppp21 LCP: MagicNumber 0xB0FFA4D8 (0x0506B0FFA4D8)*Nov 15 12:45:04.079: ppp21 LCP: I CONFACK [ACKsent] id 2 len 19*Nov 15 12:45:04.079: ppp21 LCP: MRU 1492 (0x010405D4)*Nov 15 12:45:04.079: ppp21 LCP: AuthProto CHAP (0x0305C22305)*Nov 15 12:45:04.079: ppp21 LCP: MagicNumber 0xB0FFA4D8 (0x0506B0FFA4D8)*Nov 15 12:45:04.079: ppp21 LCP: State is Open*Nov 15 12:45:04.079: ppp21 PPP: Phase is AUTHENTICATING, by this end*Nov 15 12:45:04.079: ppp21 CHAP: O CHALLENGE id 1 len 25 from "7200"*Nov 15 12:45:04.083: ppp21 CHAP: I RESPONSE id 1 len 38 from "nobody@xyz.com"*Nov 15 12:45:04.083: ppp21 PPP: Phase is FORWARDING, Attempting Forward*Nov 15 12:45:04.083: SSS INFO: Element type is Unauth-User, string value isnobody@xyz.com*Nov 15 12:45:04.083: SSS INFO: Element type is AccIe-Hdl, ptr value is 71000014*Nov 15 12:45:04.083: SSS INFO: Element type is AAA-Id, long value is 22*Nov 15 12:45:04.083: SSS INFO: Element type is Access-Type, long value is 0*Nov 15 12:45:04.083: SSS MGR [uid:21]: Handling Policy Authorize (1 pendingsessions)*Nov 15 12:45:04.083: SSS PM [uid:21]: Received More Keys*Nov 15 12:45:04.083: SSS PM [uid:21]: Handling Authorization Check*Nov 15 12:45:04.083: SSS PM [uid:21]: Handling AAA service Authorization*Nov 15 12:45:04.083: SSS PM [uid:21]: Sending authorization request for 'xyz.com'*Nov 15 12:45:04.083: SSS AAA AUTHOR [uid:21]:Event <make request>, state changedfrom idle to authorizing*Nov 15 12:45:04.083: SSS AAA AUTHOR [uid:21]:Authorizing key xyz.com*Nov 15 12:45:04.083: SSS AAA AUTHOR [uid:21]:AAA request sent for key xyz.com*Nov 15 12:45:04.095: SSS AAA AUTHOR [uid:21]:Received an AAA pass*Nov 15 12:45:04.095: SSS AAA AUTHOR [uid:21]:Event <found service>, state changedfrom authorizing to complete*Nov 15 12:45:04.095: SSS AAA AUTHOR [uid:21]:Found service info for key xyz.com*Nov 15 12:45:04.095: SSS AAA AUTHOR [uid:21]:Event <free request>, state changedfrom complete to terminal*Nov 15 12:45:04.095: SSS AAA AUTHOR [uid:21]:Free request*Nov 15 12:45:04.095: SSS PM [uid:21]: Handling Service Direction*Nov 15 12:45:04.095: SSS PM [uid:21]: Policy reply - Forwarding*Nov 15 12:45:04.095: SSS MGR [uid:21]: Got reply Forwarding from PM*Nov 15 12:45:04.099: SSS MGR [uid:21]: Handling Connect-Service event*Nov 15 12:45:04.099: VPDN CALL [uid:21]: Event connect req, state changed from idleto connecting*Nov 15 12:45:04.099: VPDN CALL [uid:21]: Requesting connection*Nov 15 12:45:04.099: VPDN CALL [uid:21]: Call request sent*Nov 15 12:45:04.099: VPDN MGR [uid:21]: Event client connect, state changed fromidle to connecting*Nov 15 12:45:04.099: VPDN MGR [uid:21]: Initiating compulsory connection to199.11.8.2*Nov 15 12:45:04.099: Tnl/Sn31399/10 L2TP: Session FS enabled*Nov 15 12:45:04.099: Tnl/Sn31399/10 L2TP: Session state change from idle towait-for-tunnel*Nov 15 12:45:04.099: uid:21 Tnl/Sn31399/10 L2TP: Create session*Nov 15 12:45:04.099: Tnl31399 L2TP: SM State idle*Nov 15 12:45:04.099: Tnl31399 L2TP: O SCCRQ*Nov 15 12:45:04.099: Tnl31399 L2TP: Control channel retransmit delay set to 1seconds*Nov 15 12:45:04.099: Tnl31399 L2TP: Tunnel state change from idle towait-ctl-reply*Nov 15 12:45:04.099: Tnl31399 L2TP: SM State wait-ctl-reply*Nov 15 12:45:04.099: [21]PPPoE 18: State LCP_NEGO Event PPP_FWDING*Nov 15 12:45:04.107: Tnl31399 L2TP: I SCCRP from rp1*Nov 15 12:45:04.107: Tnl31399 L2TP: Got a challenge from remote peer, rp1*Nov 15 12:45:04.107: Tnl31399 L2TP: Got a response from remote peer, rp1*Nov 15 12:45:04.107: Tnl31399 L2TP: Tunnel Authentication success*Nov 15 12:45:04.107: Tnl31399 L2TP: Tunnel state change from wait-ctl-reply toestablished*Nov 15 12:45:04.107: Tnl31399 L2TP: O SCCCN to rp1 tnlid 9349*Nov 15 12:45:04.107: Tnl31399 L2TP: Control channel retransmit delay set to 1seconds*Nov 15 12:45:04.107: Tnl31399 L2TP: SM State established*Nov 15 12:45:04.107: uid:21 Tnl/Sn31399/10 L2TP: O ICRQ to rp1 9349/0*Nov 15 12:45:04.107: [21]PPPoE 18: Access IE nas port called*Nov 15 12:45:04.107: uid:21 Tnl/Sn31399/10 L2TP: Session state change fromwait-for-tunnel to wait-reply*Nov 15 12:45:04.115: uid:21 Tnl/Sn31399/10 L2TP: O ICCN to rp1 9349/13589*Nov 15 12:45:04.115: Tnl31399 L2TP: Control channel retransmit delay set to 1seconds*Nov 15 12:45:04.115: uid:21 Tnl/Sn31399/10 L2TP: Session state change fromwait-reply to established*Nov 15 12:45:04.115: uid:21 Tnl/Sn31399/10 L2TP: VPDN session up*Nov 15 12:45:04.115: VPDN MGR [uid:21]: Event peer connected, state changed fromconnecting to connected*Nov 15 12:45:04.115: VPDN MGR [uid:21]: Succeed to forward nobody@xyz.com*Nov 15 12:45:04.115: VPDN MGR [uid:21]: accounting start sent*Nov 15 12:45:04.115: [21]PPPoE 18: AAA pppoe_aaa_acct_get_dynamic_attrs*Nov 15 12:45:04.115: [21]PPPoE 18: AAA pppoe_aaa_acct_get_dynamic_attrs*Nov 15 12:45:04.115: VPDN CALL [uid:21]: Event connect ok, state changed fromconnecting to connected*Nov 15 12:45:04.115: VPDN CALL [uid:21]: Connection succeeded*Nov 15 12:45:04.115: SSS MGR [uid:21]: Handling Service-Connected event*Nov 15 12:45:04.115: ppp21 PPP: Phase is FORWARDED, Session Forwarded*Nov 15 12:45:04.115: [21]PPPoE 18: State LCP_NEGO Event PPP_FWDED*Nov 15 12:45:04.115: [21]PPPoE 18: data path set to SSS Switch*Nov 15 12:45:04.119: [21]PPPoE 18: Connected Forwarded*Nov 15 12:45:04.119: ppp21 PPP: Process pending packets*Nov 15 12:45:04.139: uid:21 Tnl/Sn31399/10 L2TP: Result code(2): 2: Calldisconnected, refer to error msg*Nov 15 12:45:04.139: Error code(6): Vendor specific*Nov 15 12:45:04.139: Optional msg: Locally generated disconnect*Nov 15 12:45:04.139: uid:21 Tnl/Sn31399/10 L2TP: I CDN from rp1 tnl 9349, cl1358901:06:21: %VPDN-6-CLOSED: L2TP LNS 199.11.8.2 closed user nobody@xyz.com; Result2, Error 6, Locally generated disconnect*Nov 15 12:45:04.139: uid:21 Tnl/Sn31399/10 L2TP: disconnect (L2X) IETF:18/host-request Ascend: 66/VPDN Local PPP Disconnect*Nov 15 12:45:04.139: uid:21 Tnl/Sn31399/10 L2TP: Destroying session*Nov 15 12:45:04.139: uid:21 Tnl/Sn31399/10 L2TP: Session state change fromestablished to idle*Nov 15 12:45:04.139: VPDN MGR [uid:21]: Event peer disconnect, state changed fromconnected to disconnected*Nov 15 12:45:04.139: VPDN MGR [uid:21]: Remote disconnected nobody@xyz.com*Nov 15 12:45:04.139: VPDN MGR [uid:21]: accounting stop sent*Nov 15 12:45:04.139: Tnl31399 L2TP: Tunnel state change from established tono-sessions-left*Nov 15 12:45:04.143: Tnl31399 L2TP: No more sessions in tunnel, shutdown (likely)in 15 seconds*Nov 15 12:45:04.143: VPDN CALL [uid:21]: Event server disc, state changed fromconnected to disconnected*Nov 15 12:45:04.143: VPDN CALL [uid:21]: Server disconnected call*Nov 15 12:45:04.143: VPDN CALL [uid:21]: Event free req, state changed fromdisconnected to terminal*Nov 15 12:45:04.143: VPDN CALL [uid:21]: Free request*Nov 15 12:45:04.143: SSS MGR [uid:21]: Handling Send Client Disconnect*Nov 15 12:45:04.143: [21]PPPoE 18: State CNCT_FWDED Event SSS_DISCNCT*Nov 15 12:45:04.143: ppp21 PPP: Sending Acct Event[Down] id[16]*Nov 15 12:45:04.143: ppp21 PPP: Phase is TERMINATING*Nov 15 12:45:04.143: ppp21 LCP: State is Closed*Nov 15 12:45:04.143: ppp21 PPP: Phase is DOWN*Nov 15 12:45:04.143: [21]PPPoE 18: O PADT R:0000.0c14.71d0 L:00b0.c2e9.c870 1/32ATM4/0.132*Nov 15 12:45:04.143: [21]PPPoE 18: Destroying R:0000.0c14.71d0 L:00b0.c2e9.c8701/32 ATM4/0.132*Nov 15 12:45:04.143: [21]PPPoE 18: AAA pppoe_aaa_acct_get_dynamic_attrs*Nov 15 12:45:04.143: [21]PPPoE 18: AAA pppoe_aaa_acct_get_dynamic_attrs*Nov 15 12:45:04.143: [21]PPPoE 18: AAA account stopped*Nov 15 12:45:14.139: Tnl31399 L2TP: I StopCCN from rp1 tnl 9349*Nov 15 12:45:14.139: Tnl31399 L2TP: Shutdown tunnel*Nov 15 12:45:14.139: Tnl31399 L2TP: Tunnel state change from no-sessions-leftTroubleshoot the Subscriber Service Switch at the LNS—Normal Operation Example
The following example shows the debug commands used and sample output indicating normal operation of the Subscriber Service Switch on the LNS:
Router# debug sss eventRouter# debug sss errorRouter# debug sss fsmRouter# debug ppp negotiationRouter# debug vpdn l2x-eventsRouter# debug vpdn l2x-errorsRouter# debug vpdn sss eventsRouter# debug vpdn sss errorsRouter# debug vpdn sss fsmSSS:SSS events debugging is onSSS error debugging is onSSS fsm debugging is onPPP:PPP protocol negotiation debugging is onVPN:L2X protocol events debugging is onL2X protocol errors debugging is onVPDN SSS events debugging is onVPDN SSS errors debugging is onVPDN SSS FSM debugging is on3d17h: Tnl9264 L2TP: I ICRQ from server1 tnl 615103d17h: Tnl/Sn9264/13586 L2TP: Session FS enabled3d17h: Tnl/Sn9264/13586 L2TP: Session state change from idle to wait-connect3d17h: Tnl/Sn9264/13586 L2TP: New session created3d17h: Tnl/Sn9264/13586 L2TP: O ICRP to server1 61510/73d17h: Tnl9264 L2TP: Control channel retransmit delay set to 1 seconds3d17h: Tnl/Sn9264/13586 L2TP: I ICCN from server1 tnl 61510, cl 73d17h: nobody@xyz.com Tnl/Sn9264/13586 L2TP: Session state change fromwait-connect to wait-for-service-selection3d17h: VPDN SSS []: Event start sss, state changed from IDLE to SSS3d17h: VPDN SSS [uid:707]: Service request sent to SSS3d17h: SSS INFO: Element type is Access-Type, long value is 43d17h: SSS INFO: Element type is Switch-Id, long value is 14931725613d17h: SSS INFO: Element type is Tunnel-Name, string value is server13d17h: SSS INFO: Element type is Can-SIP-Redirect, long value is 13d17h: SSS INFO: Element type is AAA-Id, long value is 167263d17h: SSS INFO: Element type is AccIe-Hdl, ptr value is D10001673d17h: SSS MGR [uid:707]: Event service-request, state changed from wait-for-req towait-for-auth3d17h: SSS MGR [uid:707]: Handling Policy Authorize (1 pending sessions)3d17h: SSS PM [uid:707]: RM/VPDN disabled: RM/VPDN author not needed3d17h: SSS PM [uid:707]: Multihop disabled: AAA author not needed3d17h: SSS PM [uid:707]: Multihop disabled: SGF author not needed3d17h: SSS PM [uid:707]: No more authorization methods left to try, providingdefault service3d17h: SSS PM [uid:707]: Received Service Request3d17h: SSS PM [uid:707]: Event <found>, State: initial-req to end3d17h: SSS PM [uid:707]: Handling Service Direction3d17h: SSS PM [uid:707]: Policy reply - Local terminate3d17h: SSS MGR [uid:707]: Got reply Local-Term from PM3d17h: SSS MGR [uid:707]: Event policy-connect local, state changed fromwait-for-auth to connected3d17h: SSS MGR [uid:707]: Handling Send-Client-Local-Term event3d17h: VPDN SSS [uid:707]: Event connect local, state changed from SSS to PPP3d17h: ppp707 PPP: Phase is ESTABLISHING3d17h: ppp707 LCP: I FORCED rcvd CONFACK len 153d17h: ppp707 LCP: MRU 1492 (0x010405D4)3d17h: ppp707 LCP: AuthProto CHAP (0x0305C22305)3d17h: ppp707 LCP: MagicNumber 0xB0EC4557 (0x0506B0EC4557)3d17h: ppp707 LCP: I FORCED sent CONFACK len 103d17h: ppp707 LCP: MRU 1492 (0x010405D4)3d17h: ppp707 LCP: MagicNumber 0x0017455D (0x05060017455D)3d17h: ppp707 PPP: Phase is FORWARDING, Attempting Forward3d17h: VPDN SSS [uid:707]: Event dyn bind resp, state changed from PPP to PPP3d17h: ppp707 PPP: Phase is AUTHENTICATING, Unauthenticated User3d17h: ppp707 PPP: Phase is FORWARDING, Attempting Forward3d17h: VPDN SSS [uid:707]: Event connect local, state changed from PPP to PPP3d17h: VPDN SSS [Vi4.2]: Event vaccess resp, state changed from PPP to PPP3d17h: VPDN SSS [Vi4.2]: Event stat bind resp, state changed from PPP to CNCT3d17h: Vi4.2 Tnl/Sn9264/13586 L2TP: Session state change fromwait-for-service-selection to established3d17h: Vi4.2 PPP: Phase is AUTHENTICATING, Authenticated User3d17h: Vi4.2 CHAP: O SUCCESS id 1 len 43d17h: Vi4.2 PPP: Phase is UP3d17h: Vi4.2 IPCP: O CONFREQ [Closed] id 1 len 103d17h: Vi4.2 IPCP: Address 172.18.0.0 (0x030681010000)3d17h: Vi4.2 PPP: Process pending packets3d17h: Vi4.2 IPCP: I CONFREQ [REQsent] id 1 len 103d17h: Vi4.2 IPCP: Address 0.0.0.0 (0x030600000000)3d17h: Vi4.2 AAA/AUTHOR/IPCP: Start. Her address 0.0.0.0, we want 0.0.0.03d17h: Vi4.2 AAA/AUTHOR/IPCP: Done. Her address 0.0.0.0, we want 0.0.0.03d17h: Vi4.2 IPCP: Pool returned 10.1.1.33d17h: Vi4.2 IPCP: O CONFNAK [REQsent] id 1 len 103d17h: Vi4.2 IPCP: Address 10.1.1.3 (0x03065B010103)3d17h: Vi4.2 IPCP: I CONFACK [REQsent] id 1 len 103d17h: Vi4.2 IPCP: Address 172.18.0.0 (0x030681010000)3d17h: Vi4.2 IPCP: I CONFREQ [ACKrcvd] id 2 len 103d17h: Vi4.2 IPCP: Address 10.1.1.3 (0x03065B010103)3d17h: Vi4.2 IPCP: O CONFACK [ACKrcvd] id 2 len 103d17h: Vi4.2 IPCP: Address 10.1.1.3 (0x03065B010103)3d17h: Vi4.2 IPCP: State is Open3d17h: Vi4.2 IPCP: Install route to 10.1.1.3Troubleshoot the Subscriber Service Switch at the LNS—Tunnel Failure Example
The following is sample output indicating tunnel failure on the LNS:
3d17h: L2TP: I SCCRQ from server1 tnl 313993d17h: Tnl9349 L2TP: Got a challenge in SCCRQ, server13d17h: Tnl9349 L2TP: New tunnel created for remote server1, address 199.11.8.13d17h: Tnl9349 L2TP: O SCCRP to server1 tnlid 313993d17h: Tnl9349 L2TP: Control channel retransmit delay set to 1 seconds3d17h: Tnl9349 L2TP: Tunnel state change from idle to wait-ctl-reply3d17h: Tnl9349 L2TP: I SCCCN from server1 tnl 313993d17h: Tnl9349 L2TP: Got a Challenge Response in SCCCN from server13d17h: Tnl9349 L2TP: Tunnel Authentication success3d17h: Tnl9349 L2TP: Tunnel state change from wait-ctl-reply to established3d17h: Tnl9349 L2TP: SM State established3d17h: Tnl9349 L2TP: I ICRQ from server1 tnl 313993d17h: Tnl/Sn9349/13589 L2TP: Session FS enabled3d17h: Tnl/Sn9349/13589 L2TP: Session state change from idle to wait-connect3d17h: Tnl/Sn9349/13589 L2TP: New session created3d17h: Tnl/Sn9349/13589 L2TP: O ICRP to server1 31399/103d17h: Tnl9349 L2TP: Control channel retransmit delay set to 1 seconds3d17h: Tnl/Sn9349/13589 L2TP: I ICCN from server1 tnl 31399, cl 103d17h: nobody@xyz.com Tnl/Sn9349/13589 L2TP: Session state change fromwait-connect to wait-for-service-selection3d17h: VPDN SSS []: Event start sss, state changed from IDLE to SSS3d17h: VPDN SSS [uid:709]: Service request sent to SSS3d17h: SSS INFO: Element type is Access-Type, long value is 43d17h: SSS INFO: Element type is Switch-Id, long value is -19126022843d17h: SSS INFO: Element type is Tunnel-Name, string value is server13d17h: SSS INFO: Element type is Can-SIP-Redirect, long value is 13d17h: SSS INFO: Element type is AAA-Id, long value is 167293d17h: SSS INFO: Element type is AccIe-Hdl, ptr value is 8D00016A3d17h: SSS MGR [uid:709]: Event service-request, state changed from wait-for-req towait-for-auth3d17h: SSS MGR [uid:709]: Handling Policy Authorize (1 pending sessions)3d17h: SSS PM [uid:709]: RM/VPDN disabled: RM/VPDN author not needed3d17h: SSS PM [uid:709]: Multihop disabled: AAA author not needed3d17h: SSS PM [uid:709]: Multihop disabled: SGF author not needed3d17h: SSS PM [uid:709]: No more authorization methods left to try, providing default service3d17h: SSS PM [uid:709]: Received Service Request3d17h: SSS PM [uid:709]: Event <found>, State: initial-req to end3d17h: SSS PM [uid:709]: Handling Service Direction3d17h: SSS PM [uid:709]: Policy reply - Local terminate3d17h: SSS MGR [uid:709]: Got reply Local-Term from PM3d17h: SSS MGR [uid:709]: Event policy-connect local, state changed fromwait-for-auth to connected3d17h: SSS MGR [uid:709]: Handling Send-Client-Local-Term event3d17h: VPDN SSS [uid:709]: Event connect local, state changed from SSS to PPP3d17h: ppp709 PPP: Phase is ESTABLISHING3d17h: ppp709 LCP: I FORCED rcvd CONFACK len 153d17h: ppp709 LCP: MRU 1492 (0x010405D4)3d17h: ppp709 LCP: AuthProto CHAP (0x0305C22305)3d17h: ppp709 LCP: MagicNumber 0xB0FFA4D8 (0x0506B0FFA4D8)3d17h: ppp709 LCP: I FORCED sent CONFACK len 103d17h: ppp709 LCP: MRU 1492 (0x010405D4)3d17h: ppp709 LCP: MagicNumber 0x002AA481 (0x0506002AA481)3d17h: ppp709 PPP: Phase is FORWARDING, Attempting Forward3d17h: VPDN SSS [uid:709]: Event dyn bind resp, state changed from PPP to PPP3d17h: ppp709 PPP: Phase is AUTHENTICATING, Unauthenticated User3d17h: ppp709 CHAP: O FAILURE id 1 len 25 msg is "Authentication failed"3d17h: ppp709 PPP: Sending Acct Event[Down] id[4159]3d17h: ppp709 PPP: Phase is TERMINATING3d17h: ppp709 LCP: O TERMREQ [Open] id 1 len 43d17h: ppp709 LCP: State is Closed3d17h: ppp709 PPP: Phase is DOWN3d17h: ppp709 PPP: Phase is TERMINATING3d17h: VPDN SSS [uid:709]: Event peer disc, state changed from PPP to DSC3d17h: nobody@xyz.com Tnl/Sn9349/13589 L2TP: disconnect (AAA) IETF:17/user-error Ascend: 26/PPP CHAP Fail3d17h: nobody@xyz.com Tnl/Sn9349/13589 L2TP: O CDN to server1 31399/103d17h: Tnl9349 L2TP: Control channel retransmit delay set to 1 seconds3d17h: nobody@xyz.com Tnl/Sn9349/13589 L2TP: Destroying session3d17h: nobody@xyz.com Tnl/Sn9349/13589 L2TP: Session state change fromwait-for-service-selection to idle3d17h: VPDN SSS [uid:709]: Event vpdn disc, state changed from DSC to END3d17h: Tnl9349 L2TP: Tunnel state change from established to no-sessions-left3d17h: Tnl9349 L2TP: No more sessions in tunnel, shutdown (likely) in 10 seconds3d17h: SSS MGR [uid:709]: Processing a client disconnect3d17h: SSS MGR [uid:709]: Event client-disconnect, state changed from connected toend3d17h: SSS MGR [uid:709]: Handling Send-Service-Disconnect event3d17h: Tnl9349 L2TP: O StopCCN to server1 tnlid 313993d17h: Tnl9349 L2TP: Control channel retransmit delay set to 1 seconds3d17h: Tnl9349 L2TP: Tunnel state change from no-sessions-left to shutting-down3d17h: Tnl9349 L2TP: Shutdown tunnelAdditional References
For additional information related to Subscriber Service Switch, refer to the following references:
Related Documents
"Virtual Templates, Profiles, and Networks" chapter
"PPP Configuration" chapter
•
Cisco IOS Dial Technologies Configuration Guide, Release 12.2
VPDN and PPP commands: complete command syntax, command mode, defaults, usage guidelines, and examples
•
Cisco IOS Dial Technologies Command Reference, Release 12.2
"Authentication, Authorization, and Accounting (AAA)" chapter
•
Cisco IOS Security Configuration Guide, Release 12.2
AAA commands: complete command syntax, command mode, defaults, usage guidelines, and examples
•
Cisco IOS Security Command Reference, Release 12.2
"Configuring Broadband Access: PPP and Routed Bridging Encapsulations" chapter
•
Cisco IOS Wide-Area Networking Configuration Guide, Release 12.2
PPPoE and PPPoA commands: complete command syntax, command mode, defaults, usage guidelines, and examples
•
Cisco IOS Wide-Area Networking Command Reference, Release 12.2
L2TP tunnel service authorization
LLID feature
Standards
MIBs
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL:
http://tools.cisco.com/ITDIT/MIBS/servlet/index
If Cisco MIB Locator does not support the MIB information that you need, you can also obtain a list of supported MIBs and download MIBs from the Cisco MIBs page at the following URL:
http://www.cisco.com/public/sw-center/netmgmt/cmtk/mibs.shtml
To access Cisco MIB Locator, you must have an account on Cisco.com. If you have forgotten or lost your account information, send a blank e-mail to cco-locksmith@cisco.com. An automatic check will verify that your e-mail address is registered with Cisco.com. If the check is successful, account details with a new random password will be e-mailed to you. Qualified users can establish an account on Cisco.com by following the directions found at this URL:
RFCs
RFC 2341
Cisco Layer Two Forwarding (Protocol) L2F
RFC2661
Layer Two Tunneling Protocol L2TP
RFC 2516
A Method for Transmitting PPP Over Ethernet (PPPoE) (PPPoE Discovery)
1 Not all supported RFCs are listed.
Technical Assistance
Command Reference
This section documents new and modified commands.
•
debug sss aaa authorization event
•
debug sss aaa authorization fsm
•
subscriber authorization enable
atm pppatm passive
To place an ATM subinterface in passive mode, use the atm pppatm passive command in ATM subinterface configuration mode. To change the configuration back to the default (active) mode, use the no form of this command.
atm pppatm passive
no atm pppatm passive
Syntax Description
This command has no arguments or keywords.
Defaults
Active mode
Command Modes
ATM subinterface configuration
Command History
12.2(13)T
This feature was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Usage Guidelines
The atm pppatm passive command places PPP over ATM (PPPoA) sessions on an ATM subinterface in "listening" mode. Rather than trying to establish the sessions actively by sending out Link Control Protocol (LCP) packets, these sessions listen to the incoming LCP packets and become active only after they have received their first LCP packet. This feature is useful for L2TP access concentrators (LACs) in the broadband access deployments where thousands of PPPoA sessions are configured on LACs. When PPPoA is in the passive mode, the LAC will bring up the sessions only when the subscribers become active and not waste its processing power on polling all the sessions.
For better scalability and faster convergence of PPP sessions, Cisco recommends setting the PPPoA sessions to passive mode at the LAC.
Examples
The following example configures the passive mode for the PPPoA sessions on an ATM subinterface:
interface atm 1/0.1 multipointatm pppatm passiverange range-pppoa-1 pvc 100 199protocol ppp virtual-template 1clear pppatm interface atm
To clear PPP ATM sessions on an ATM interface, use the clear pppatm interface atm command in privileged EXEC mode.
clear pppatm interface atm interface-number[.subinterface-number] [vc {[vpi/]vci | virtual-circuit-name}]
Syntax Description
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Usage Guidelines
This command clears the PPP over ATM (PPPoA) sessions in an interface, or in a VC when the VC is specified.
When the clear pppatm interface atm command is used to clear sessions on an interface, PPP keepalives continue to work and can be used to detect a broken link.
Examples
The following example clears a PPP ATM session on ATM interface 1/0.10:
Router# clear pppatm interface atm 1/0.10Related Commands
debug pppatm
Enables reports for PPPoA events, errors, and states either globally or conditionally on an interface or VC.
show pppatm summary
Displays PPPoA session counts.
clear pppoe
To clear PPP over Ethernet (PPPoE) sessions, use the clear pppoe command in privileged EXEC mode.
clear pppoe {interface type number [vc {[vpi/]vci | vc-name}] [vlan vlan-id] | rmac mac-address [sid session-id] | all}
Syntax Description
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.3(2)T
The vlan vlan-id keyword and argument were added.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Usage Guidelines
Use the clear pppoe all command to clear all PPPoE sessions.
Use the interface keyword and arguments and the vlan keyword and argument to clear PPPoE sessions on a specific Ethernet 802.1Q VLAN.
Use the interface, vc, and vlan keywords and arguments to clear PPPoE over 802.1Q VLAN sessions on an ATM PVC.
Examples
The following example clears all PPPoE sessions:
Router# clear pppoe alldebug pppatm
To enable debug reports for PPP over ATM (PPPoA) events, errors, and states, either globally or conditionally, on an interface or virtual circuit (VC), use the debug pppatm command in privileged EXEC mode. To disable debugging output, use the no form of this command.
debug pppatm {event | error | state} [interface atm interface-number [subinterface-number]] vc {[vpi/vci]vci | virtual-circuit-name}
no debug pppatm {event | error | state} [interface atm interface-number [subinterface-number] vc {[vpi/]vci | virtual-circuit-name}
Syntax Description
Defaults
No default behavior or values
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Usage Guidelines
Each specific PPPoA debug report must be requested on a separate command line; see the "Examples" section.
Examples
The following is example output of a PPPoA session with event, error, and state debug reports enabled on ATM interface 1/0.10:
Router# debug pppatm event interface atm1/0.10Router# debug pppatm error interface atm1/0.10Router# debug pppatm state interface atm1/0.1000:03:08: PPPATM: ATM1/0.10 0/101 [1], Event = Clear Session00:03:08: PPPATM: ATM1/0.10 0/101 [1], Event = Disconnecting00:03:08: PPPATM: ATM1/0.10 0/101 [1], Event = AAA gets dynamic attrs00:03:08: PPPATM: ATM1/0.10 0/101 [1], Event = AAA gets dynamic attrs00:03:08: PPPATM: ATM1/0.10 0/101 [1], Event = SSS Cleanup00:03:08: PPPATM: ATM1/0.10 0/101 [0], State = DOWN00:03:08: PPPATM: ATM1/0.10 0/101 [0], Event = Up Pending00:03:16: PPPATM: ATM1/0.10 0/101 [0], Event = Up Dequeued00:03:16: PPPATM: ATM1/0.10 0/101 [0], Event = Processing Up00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = Access IE allocated00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = Set Pkts to SSS00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = AAA gets retrived attrs00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = AAA gets nas port details00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = AAA gets dynamic attrs00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = AAA gets dynamic attrs00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = AAA unique id allocated00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = No AAA method list set00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = SSS Request00:03:16: PPPATM: ATM1/0.10 0/101 [2], State = NAS_PORT_POLICY_INQUIRY00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = SSS Msg Received = 100:03:16: PPPATM: ATM1/0.10 0/101 [2], State = PPP_START00:03:16: PPPATM: ATM1/0.10 0/101 [2], Event = PPP Msg Received = 100:03:16: PPPATM: ATM1/0.10 0/101 [2], State = LCP_NEGOTIATION00:03:27: PPPATM: ATM1/0.10 0/101 [2], Event = PPP Msg Received = 400:03:27: PPPATM: ATM1/0.10 0/101 [2], Event = HW Switch support FORW = 000:03:27: PPPATM: ATM1/0.10 0/101 [2], Event = Access IE get nas port00:03:27: PPPATM: ATM1/0.10 0/101 [2], Event = AAA gets dynamic attrs00:03:27: PPPATM: ATM1/0.10 0/101 [2], Event = AAA gets dynamic attrs00:03:27: PPPATM: ATM1/0.10 0/101 [2], Event = PPP Msg Received = 500:03:27: PPPATM: ATM1/0.10 0/101 [2], Event = Set Pkts to SSS00:03:27: PPPATM: ATM1/0.10 0/101 [2], State = FORWARDEDTable 1 describes the significant fields shown in the display.
Related Commands
atm pppatm passive
Places an ATM subinterface into passive mode.
show pppatm summary
Displays PPPoA session counts.
debug sss aaa authorization event
To display messages about authentication, authorization, and accounting (AAA) authorization events that are part of normal call establishment, use the debug sss aaa authorization event command in privileged EXEC mode. To disable debugging output, use the no form of this command.
debug sss aaa authorization event
no debug sss aaa authorization event
Syntax Description
This command has no arguments or keywords.
Defaults
No default behavior or values
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Examples
The following is sample output of several Subscriber Service Switch (SSS) debug commands including the debug sss aaa authorization event command. The reports from these commands should be sent to technical personnel at Cisco Systems for evaluation.
Router# debug sss eventRouter# debug sss errorRouter# debug sss stateRouter# debug sss aaa authorization eventRouter# debug sss aaa authorization fsmSSS:SSS events debugging is onSSS error debugging is onSSS fsm debugging is onSSS AAA authorization event debugging is onSSS AAA authorization FSM debugging is on*Mar 4 21:33:18.248: SSS INFO: Element type is Access-Type, long value is 3*Mar 4 21:33:18.248: SSS INFO: Element type is Switch-Id, long value is -1509949436*Mar 4 21:33:18.248: SSS INFO: Element type is Nasport, ptr value is 6396882C*Mar 4 21:33:18.248: SSS INFO: Element type is AAA-Id, long value is 7*Mar 4 21:33:18.248: SSS INFO: Element type is AAA-ACCT_ENBL, long value is 1*Mar 4 21:33:18.248: SSS INFO: Element type is AccIe-Hdl, ptr value is 78000006*Mar 4 21:33:18.248: SSS MGR [uid:7]: Event service-request, state changed from wait-for-req to wait-for-auth*Mar 4 21:33:18.248: SSS MGR [uid:7]: Handling Policy Authorize (1 pending sessions)*Mar 4 21:33:18.248: SSS PM [uid:7]: Need the following key: Unauth-User*Mar 4 21:33:18.248: SSS PM [uid:7]: Received Service Request*Mar 4 21:33:18.248: SSS PM [uid:7]: Event <need keys>, State: initial-req to need-init-keys*Mar 4 21:33:18.248: SSS PM [uid:7]: Policy reply - Need more keys*Mar 4 21:33:18.248: SSS MGR [uid:7]: Got reply Need-More-Keys from PM*Mar 4 21:33:18.248: SSS MGR [uid:7]: Event policy-or-mgr-more-keys, state changed from wait-for-auth to wait-for-req*Mar 4 21:33:18.248: SSS MGR [uid:7]: Handling More-Keys event*Mar 4 21:33:20.256: SSS INFO: Element type is Unauth-User, string value is nobody2@xyz.com*Mar 4 21:33:20.256: SSS INFO: Element type is AccIe-Hdl, ptr value is 78000006*Mar 4 21:33:20.256: SSS INFO: Element type is AAA-Id, long value is 7*Mar 4 21:33:20.256: SSS INFO: Element type is Access-Type, long value is 0*Mar 4 21:33:20.256: SSS MGR [uid:7]: Event service-request, state changed from wait-for-req to wait-for-auth*Mar 4 21:33:20.256: SSS MGR [uid:7]: Handling Policy Authorize (1 pending sessions)*Mar 4 21:33:20.256: SSS PM [uid:7]: Received More Initial Keys*Mar 4 21:33:20.256: SSS PM [uid:7]: Event <rcvd keys>, State: need-init-keys to check-auth-needed*Mar 4 21:33:20.256: SSS PM [uid:7]: Handling Authorization Check*Mar 4 21:33:20.256: SSS PM [uid:7]: Event <send auth>, State: check-auth-needed to authorizing*Mar 4 21:33:20.256: SSS PM [uid:7]: Handling AAA service Authorization*Mar 4 21:33:20.256: SSS PM [uid:7]: Sending authorization request for 'xyz.com'*Mar 4 21:33:20.256: SSS AAA AUTHOR [uid:7]:Event <make request>, state changed from idle to authorizing*Mar 4 21:33:20.256: SSS AAA AUTHOR [uid:7]:Authorizing key xyz.com*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:AAA request sent for key xyz.com*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Received an AAA pass*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Event <found service>, state changed from authorizing to complete*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Found service info for key xyz.com*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Event <free request>, state changed from complete to terminal*Mar 4 21:33:20.260: SSS AAA AUTHOR [uid:7]:Free request*Mar 4 21:33:20.264: SSS PM [uid:7]: Event <found>, State: authorizing to end*Mar 4 21:33:20.264: SSS PM [uid:7]: Handling Service Direction*Mar 4 21:33:20.264: SSS PM [uid:7]: Policy reply - Forwarding*Mar 4 21:33:20.264: SSS MGR [uid:7]: Got reply Forwarding from PM*Mar 4 21:33:20.264: SSS MGR [uid:7]: Event policy-start-service-fsp, state changed from wait-for-auth to wait-for-service*Mar 4 21:33:20.264: SSS MGR [uid:7]: Handling Connect-Forwarding-Service event*Mar 4 21:33:20.272: SSS MGR [uid:7]: Event service-fsp-connected, state changed from wait-for-service to connected*Mar 4 21:33:20.272: SSS MGR [uid:7]: Handling Forwarding-Service-Connected eventRelated Commands
debug sss aaa authorization fsm
To display information about authentication, authorization, and accounting (AAA) authorization state changes, use the debug sss aaa authorization fsm command in privileged EXEC mode. To disable debugging output, use the no form of this command.
debug sss aaa authorization fsm
no debug sss aaa authorization fsm
Syntax Description
This command has no arguments or keywords.
Defaults
No default behavior or values
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Examples
The following example shows how to enter this command. See the "Examples" section of the debug ssg transparent login command page for an example of output.
Router# debug sss aaa authorization fsmRelated Commands
debug sss error
To display diagnostic information about errors that may occur during Subscriber Service Switch (SSS) call setup, use the debug sss error command in privileged EXEC mode. To disable debugging output, use the no form of this command.
debug sss error
no debug sss error
Syntax Description
This command has no arguments or keywords.
Defaults
No default behavior or values
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Examples
The following example shows how to enter this command. See the "Examples" section of the debug ssg transparent login command page for an example of output.
Router# debug sss errorRelated Commands
debug sss event
To display diagnostic information about Subscriber Service Switch (SSS) call setup events, use the debug sss event command in privileged EXEC mode. To disable debugging output, use the no form of this command.
debug sss event
no debug sss event
Syntax Description
This command has no arguments or keywords.
Defaults
No default behavior or values
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Examples
The following example shows how to enter this command. See the "Examples" section of the debug ssg transparent login command page for an example of output.
Router# debug sss eventRelated Commands
debug sss fsm
To display diagnostic information about the Subscriber Service Switch (SSS) call setup state, use the debug sss fsm command in privileged EXEC mode. To disable debugging output, use the no form of this command.
debug sss fsm
no debug sss fsm
Syntax Description
This command has no arguments or keywords.
Defaults
No default behavior or values
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Examples
The following example shows how to enter this command. See the "Examples" section of the debug ssg transparent login command page for an example of output.
Router# debug sss fsmmultihop hostname
To enable the Layer 2 Tunnel Protocol (L2TP) tunnel switch to initiate a tunnel based on the L2TP access concentrator (LAC) host name or ingress tunnel ID, use the multihop hostname command in VPDN request-dialin group configuration mode. To disable this option, use the no form of this command.
multihop hostname ingress-tunnel-name
no multihop hostname ingress-tunnel-name
Syntax Description
Defaults
No default behavior or values.
Command Modes
VPDN request-dialin group configuration.
Command History
Examples
The following example enables the L2TP tunnel switch to forward sessions from LAC-1 through an outgoing tunnel to IP address 10.3.3.3 using a virtual private dialup network (VPDN) group:
vpdn-group 11request-dialinprotocol l2tpmultihop hostname LAC-1initiate-to ip 10.3.3.3local name Tunnel-SwitchRelated Commands
show pppatm summary
To display PPP over ATM (PPPoA) session counts, use the show pppatm summary command in EXEC mode.
show pppatm summary [interface atm interface-number.[subinterface-number]]
Syntax Description
Command Modes
EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Usage Guidelines
This command is useful for obtaining session counts, the state of the PPPoA sessions, and the interfaces on which they are running.
This command gives a summary of the number of PPPoA sessions in each state and the session information of each individual session. If a subinterface number is given in the command, the output is a summary report of the PPPoA sessions in the subinterface. If a main interface number is given, the output will have the summary reports for each individual subinterface of that main interface as shown in the example that follows. If no interface is given, the output will contain the summary reports for each ATM interface on the router.
Examples
The following example displays PPPoA session counts and states for ATM interface 5/0:
Router# show pppatm summary interface atm 5/0ATM5/0.3:0 sessions totalATM5/0.6:1 in PTA (PTA) State1 sessions totalVPI VCI Conn ID PPPoA ID SSS ID PPP ID AAA ID VT VA/SID State6 101 11 DA000009 BB000013 E5000017 C 1 1.1 PTAMost of the messages displayed by the show pppatm summary command are self-explanatory. Table 4 describes the significant fields shown in the displays. Any data not described in Table 4 is used for internal debugging purposes.
Related Commands
show pppatm trace
To display a sequence of PPP over ATM (PPPoA) events, errors, and state changes when the debug pppatm command is enabled, use the show pppatm trace command in privileged EXEC mode.
show pppatm trace [error | event | state] interface atm interface-number.[subinterface-number] vc {[vpi/]vci | virtual-circuit-name}
Syntax Description
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Usage Guidelines
When the debug pppatm command has been enabled, this command displays messages from the specified permanent virtual circuit (PVC). If only one debug pppatm command keyword is supplied in the command, the report will display only the sequence of events for that particular debug type.
Examples
The following example traces the debugging messages supplied by the debug pppatm command on PVC 101. The report is used by Cisco technical personnel for diagnosing system problems.
Router# debug pppatm trace interface atm 1/0.10 vc 101Router# debug pppatm state interface atm 1/0.10 vc 101Router# debug pppatm event interface atm 1/0.10 vc 101Router# show pppatm trace interface atm 1/0.10 vc 101Event = DisconnectingEvent = AAA gets dynamic attrsEvent = AAA gets dynamic attrsEvent = SSS CleanupState = DOWNEvent = Up PendingEvent = Up DequeuedEvent = Processing UpEvent = Access IE allocatedEvent = Set Pkts to SSSEvent = AAA gets retrieved attrsEvent = AAA gets nas port detailsEvent = AAA gets dynamic attrsEvent = AAA gets dynamic attrsEvent = AAA unique id allocatedEvent = No AAA method list setEvent = SSS RequestState = NAS_PORT_POLICY_INQUIRYEvent = SSS MsgState = PPP_STARTEvent = PPP MsgState = LCP_NEGOTIATIONEvent = PPP MsgEvent = Access IE get nas portEvent = AAA gets dynamic attrsEvent = AAA gets dynamic attrsEvent = PPP MsgEvent = Set Pkts to SSSState = FORWARDEDRelated Commands
show sss session
To display Subscriber Service Switch session status, use the show sss session command in privileged EXEC mode.
show sss session [all]
Syntax Description
Command Modes
Privileged EXEC
Command History
12.2(13)T
This command was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Usage Guidelines
Use this command to verify correct operation of PPP connections in the Subscriber Service Switch environment.
Examples
The following sample output from the show sss session command provides a basic report of Subscriber Service Switch session activity:
Router# show sss sessionCurrent SSS Information: Total sessions 9Uniq ID Type State Service Identifier Last Chg9 PPPoE/PPP connected VPDN nobody3@<domain>.com 00:02:3610 PPPoE/PPP connected VPDN nobody3@<domain>.com 00:01:5211 PPPoE/PPP connected VPDN nobody3@<domain>.com 00:01:523 PPPoE/PPP connected VPDN user3@<domain>.com 2d21h6 PPPoE/PPP connected Local Term user1 00:03:357 PPPoE/PPP connected Local Term user2 00:03:358 PPPoE/PPP connected VPDN nobody3@<domain>.com 00:02:362 PPP connected Local Term user 00:05:064 PPP connected VPDN nobody2@<domain>.com 00:06:52The following sample output from the show sss session all command provides a more extensive report of Subscriber Service Switch session activity:
Router# show sss session allCurrent SSS Information: Total sessions 9SSS session handle is 40000013, state is connected, service is VPDNUnique ID is 9SIP subscriber access type(s) are PPPoE/PPPIdentifier is nobody3@<domain>.comLast Changed 00:02:49Root SIP Handle is DF000010, PID is 49AAA unique ID is 10Current SIP options are Req Fwding/Req FwdedSSS session handle is B0000017, state is connected, service is VPDNUnique ID is 10SIP subscriber access type(s) are PPPoE/PPPIdentifier is nobody3@<domain>.comLast Changed 00:02:05Root SIP Handle is B9000015, PID is 49AAA unique ID is 11Current SIP options are Req Fwding/Req FwdedSSS session handle is D6000019, state is connected, service is VPDNUnique ID is 11SIP subscriber access type(s) are PPPoE/PPPIdentifier is nobody3@<domain>.comLast Changed 00:02:13Root SIP Handle is D0000016, PID is 49AAA unique ID is 12Current SIP options are Req Fwding/Req FwdedSSS session handle is 8C000003, state is connected, service is VPDNUnique ID is 3SIP subscriber access type(s) are PPPoE/PPPIdentifier is user3@<domain>.comLast Changed 2d21hRoot SIP Handle is D3000002, PID is 49AAA unique ID is 3Current SIP options are Req Fwding/Req FwdedSSS session handle is BE00000B, state is connected, service is Local TermUnique ID is 6SIP subscriber access type(s) are PPPoE/PPPIdentifier is user1Last Changed 00:03:56Root SIP Handle is A9000009, PID is 49AAA unique ID is 7Current SIP options are Req Fwding/Req FwdedSSS session handle is DC00000D, state is connected, service is Local TermUnique ID is 7SIP subscriber access type(s) are PPPoE/PPPIdentifier is user2Last Changed 00:03:57Root SIP Handle is 2C00000A, PID is 49AAA unique ID is 8Current SIP options are Req Fwding/Req FwdedSSS session handle is DB000011, state is connected, service is VPDNUnique ID is 8SIP subscriber access type(s) are PPPoE/PPPIdentifier is nobody3@<domain>.comLast Changed 00:02:58Root SIP Handle is 1000000F, PID is 49AAA unique ID is 9Current SIP options are Req Fwding/Req FwdedSSS session handle is 3F000007, state is connected, service is Local TermUnique ID is 2SIP subscriber access type(s) are PPPIdentifier is userLast Changed 00:05:30Root SIP Handle is 8A000009, PID is 92AAA unique ID is 1Current SIP options are Req Fwding/Req FwdedSSS session handle is 97000005, state is connected, service is VPDNUnique ID is 4SIP subscriber access type(s) are PPPIdentifier is nobody2@<domain>.comLast Changed 00:07:16Root SIP Handle is 32000000, PID is 92AAA unique ID is 5Current SIP options are Req Fwding/Req FwdedMost of the messages displayed by the show sss session and show sss session all commands are self-explanatory. Table 5 describes the significant fields shown in the displays. Any data not described in Table 5 is used for internal debugging purposes.
Related Commands
show vpdn session
Displays session information about the L2TP and L2F protocols, and PPPoE tunnels in a VPDN.
show vpdn session
To display session information about Layer 2 Tunneling Protocol (L2TP), Layer 2 Forwarding (L2F) protocol, and PPP over Ethernet (PPPoE) tunnels in a virtual private dialup network (VPDN), use the show vpdn session command in privileged EXEC mode.
show vpdn session [all | packets | sequence | state]
Syntax Description
Command Modes
Privileged EXEC
Command History
Usage Guidelines
PPPoE is supported on ATM permanent virtual connections (PVCs) compliant with RFC 1483 only. PPPoE is not supported on Frame Relay and any other LAN interfaces such as FDDI and Token Ring.
Reports and options for this command depend upon the configuration in which it is used. Use the command-line question mark (?) help function to display options available with the show vpdn session command.
Examples
The following is sample output from the show vpdn session command. It provides reports on call activity for the current L2TP, L2F, and PPPoE sessions.
Router# show vpdn sessionL2TP Session Information Total tunnels 1 sessions 4LocID RemID TunID Intf Username State Last Chg Uniq ID4 691 13695 Se0/0 nobody2@xyz.com est 00:06:00 45 692 13695 SSS Circuit nobody1@xyz.com est 00:01:43 86 693 13695 SSS Circuit nobody1@xyz.com est 00:01:43 93 690 13695 SSS Circuit nobody3@xyz.com est 2d21h 3L2F Session Information Total tunnels 1 sessions 2CLID MID Username Intf State Uniq ID1 2 nobody@xyz.com SSS Circuit open 101 3 nobody@xyz.com SSS Circuit open 11%No active PPTP tunnelsPPPoE Session Information Total tunnels 1 sessions 7PPPoE Session InformationUID SID RemMAC OIntf Intf SessionLocMAC VASt state3 1 0030.949b.b4a0 Fa2/0 N/A CNCT_FWDED0010.7b90.08406 2 0030.949b.b4a0 Fa2/0 Vi1.1 CNCT_PTA0010.7b90.0840 UP7 3 0030.949b.b4a0 Fa2/0 Vi1.2 CNCT_PTA0010.7b90.0840 UP8 4 0030.949b.b4a0 Fa2/0 N/A CNCT_FWDED0010.7b90.08409 5 0030.949b.b4a0 Fa2/0 N/A CNCT_FWDED0010.7b90.084010 6 0030.949b.b4a0 Fa2/0 N/A CNCT_FWDED0010.7b90.084011 7 0030.949b.b4a0 Fa2/0 N/A CNCT_FWDED0010.7b90.0840The following is sample output from the show vpdn session all command. It provides extensive reports on call activity for all L2TP, L2F, and PPPoE sessions.
Router# show vpdn session allL2TP Session Information Total tunnels 1 sessions 4Session id 5 is up, tunnel id 13695Call serial number is 3355500002Remote tunnel name is User03Internet address is 10.0.0.63Session state is established, time since change 00:03:5352 Packets sent, 52 received2080 Bytes sent, 1316 receivedLast clearing of "show vpdn" counters neverSession MTU is 1464 bytesSession username is nobody@xyz.comInterfaceRemote session id is 692, remote tunnel id 58582UDP checksums are disabledSSS switching enabledNo FS cached header information availableSequencing is offUnique ID is 8Session id 6 is up, tunnel id 13695Call serial number is 3355500003Remote tunnel name is User03Internet address is 10.0.0.63Session state is established, time since change 00:04:2252 Packets sent, 52 received2080 Bytes sent, 1316 receivedLast clearing of "show vpdn" counters neverSession MTU is 1464 bytesSession username is nobody@xyz.comInterfaceRemote session id is 693, remote tunnel id 58582UDP checksums are disabledSSS switching enabledNo FS cached header information availableSequencing is offUnique ID is 9Session id 3 is up, tunnel id 13695Call serial number is 3355500000Remote tunnel name is User03Internet address is 10.0.0.63Session state is established, time since change 2d21h48693 Packets sent, 48692 received1947720 Bytes sent, 1314568 receivedLast clearing of "show vpdn" counters neverSession MTU is 1464 bytesSession username is nobody2@xyz.comInterfaceRemote session id is 690, remote tunnel id 58582UDP checksums are disabledSSS switching enabledNo FS cached header information availableSequencing is offUnique ID is 3Session id 4 is up, tunnel id 13695Call serial number is 3355500001Remote tunnel name is User03Internet address is 10.0.0.63Session state is established, time since change 00:08:40109 Packets sent, 3 received1756 Bytes sent, 54 receivedLast clearing of "show vpdn" counters neverSession MTU is 1464 bytesSession username is nobody@xyz.comInterface Se0/0Remote session id is 691, remote tunnel id 58582UDP checksums are disabledIDB switching enabledFS cached header information:encap size = 36 bytes4500001C BDDC0000 FF11E977 0A00003E0A00003F 06A506A5 00080000 0202E4D602B30000Sequencing is offUnique ID is 4L2F Session Information Total tunnels 1 sessions 2MID: 2User: nobody@xyz.comInterface:State: openPackets out: 53Bytes out: 2264Packets in: 51Bytes in: 1274Unique ID: 10Last clearing of "show vpdn" counters neverMID: 3User: nobody@xyz.comInterface:State: openPackets out: 53Bytes out: 2264Packets in: 51Bytes in: 1274Unique ID: 11Last clearing of "show vpdn" counters never%No active PPTP tunnelsPPPoE Session Information Total tunnels 1 sessions 7PPPoE Session InformationSID Pkts-In Pkts-Out Bytes-In Bytes-Out1 48696 48696 681765 13146572 71 73 1019 10433 71 73 1019 10434 61 62 879 15675 61 62 879 15676 55 55 791 13637 55 55 795 1363The messages displayed by the show vpdn session and show vpdn session all commands are self-explanatory. Table 6 describes the significant fields shown in the displays. Any fields not described in Table 6 are used for internal debugging purposes.
The following is sample output from the show vpdn session packets command for a PPPoE session:
Router# show vpdn session packets%No active L2TP tunnels%No active L2F tunnelsPPPoE Session Information Total tunnels 1 sessions 1PPPoE Session InformationSID Pkts-In Pkts-Out Bytes-In Bytes-Out1 202333 202337 2832652 2832716Table 7 describes the significant fields shown in the show vpdn session packets command display.
Related Commands
subscriber access
To configure an L2TP access concentrator (LAC) to enable Subscriber Service Switch (SSS) to preauthorize the network access server (NAS) port identifier (NAS-Port-ID) string before authorizing the domain name, use the subscriber access command in global configuration mode. To disable SSS preauthorization, use the no form of this command.
subscriber access {pppoe | pppoa} pre-authorize nas-port-id [aaa-method-list]
no subscriber access {pppoe | pppoa} pre-authorize nas-port-id [aaa-method-list]
Syntax Description
Defaults
Preauthorization is disabled.
Command Modes
Global configuration
Command History
Usage Guidelines
The NAS-Port-ID string is used to locate the first service record, which may contain one of three attributes, as follows:
•
A restricted set of values for the domain substring of the unauthenticated PPP name.
This filtered service key then locates the final service. See the vpdn authorize domain command for more information.
•
PPPoE session limit.
•
The logical line ID (LLID).
Once NAS port authorization has taken place, normal authorization, which is usually the domain authorization, continues.
Logical Line ID
The LLID is an alphanumeric string of from 1 to 253 characters that serves as the logical identification of a subscriber line. LLID is maintained in a RADIUS server customer profile database and enables users to track their customers on the basis of the physical lines in which customer calls originate. Downloading the LLID is also referred to as preauthorization because it occurs before normal virtual private dialup network (VPDN) authorization downloads L2TP tunnel information.
This command enables LLID and SSS querying only for PPP over Ethernet over ATM (PPPoEoATM) and PPP over Ethernet over VLAN (PPPoEoVLAN or Dot1Q) calls; all other calls, such as ISDN, are not supported.
Per-NAS-Port Session Limits for PPPoE
Use this command to configure SSS preauthorization on the LAC so that the PPPoE per-NAS-port session limit can be downloaded from the customer profile database. To use PPPoE per-NAS-port session limits, you must also configure the PPPoE Session-Limit per NAS-Port Cisco AV-pair in the user profile.
Examples
The following example signals SSS to preauthorize the NAS-Port-ID string before authorizing the domain name. This policy applies only to sessions that have a PPPoE access type.
aaa new-modelaaa group server radius sg_llidserver 172.20.164.106 auth-port 1645 acct-port 1646aaa group server radius sg_waterserver 172.20.164.106 auth-port 1645 acct-port 1646aaa authentication ppp default group radiusaaa authorization confg-commandsaaa authorization network default group sg_wateraaa authorization network mlist_llid group sg_llidaaa session-id common!username s7200_2 password 0 labusername s5300 password 0 labusername sg_water password 0 labvpdn enable!vpdn-group 2request-dialinprotocol 12tpdomain <domain>.cominitiate-to ip 10.1.1.1local name s7200_2!vpdn-group 3accept dialinprotocol pppoevirtual-template 1!! Signals Subscriber Service Switch to preauthorize the NAS-Port-ID string before! authorizing the domain name.subscriber access pppoe pre-authorize nas-port-id mlist_llid!interface Loopback0ip address 10.1.1.2 255.255.255.0!interface Loopback1ip address 10.1.1.1 255.255.255.0!interface Ethernet1/0ip address 10.2.2.2 255.255.255.0 secondaryip address 10.0.58.111 255.255.255.0no cdp enable!interface ATM4/0no ip addressno atm ilmi-keepalive!interface ATM4/0.1 point-to-pointpvc 1/100encapsulation aa15snapprotocol pppoe!interface virtual-template1no ip unnumbered Loopback0no peer default ip addressppp authentication chap!radius-server host 172.20.164.120 auth-port 1645 acct-port 1646 key rad123radius-server host 172.20.164.106 auth-port 1645 acct-port 1646 key rad123ip radius source-interface Loopback1Related Commands
subscriber authorization enable
Enables SSS type authorization.
vpdn authorize domain
Enables domain preauthorization on a NAS.
subscriber authorization enable
To enable Subscriber Service Switch type authorization, use the subscriber authorization enable command in global configuration mode. To disable the Subscriber Service Switch authorization, use the no form of this command.
subscriber authorization enable
no subscriber authorization enable
Syntax Description
This command has no arguments or keywords.
Defaults
Authorization is disabled.
Command Modes
Global configuration
Command History
12.2(13)T
This feature was introduced.
12.2(27)SBA
This command was integrated into Cisco IOS Release 12.2(27)SBA.
Usage Guidelines
The subscriber authorization enable command triggers Subscriber Service Switch type authorization for local termination, even if virtual private dialup network (VPDN) and Stack Group Bidding Protocol (SGBP) are disabled.
Examples
The following example enables Subscriber Service Switch type authorization:
subscriber authorization enableRelated Commands
subscriber access
Enables Subscriber Service Switch preauthorization.
vpdn authorize domain
Enables domain preauthorization on a NAS.
vpdn authorize domain
To enable domain preauthorization on a network access server (NAS), use the vpdn authorize domain command in global configuration mode. To disable domain preauthorization, use the no form of this command.
vpdn authorize domain
no vpdn authorize domain
Syntax Description
This command has no arguments or keywords.
Defaults
Domain preauthorization is disabled by default.
Command Modes
Global configuration
Command History
Usage Guidelines
A RADIUS domain preauthorization user profile must also be created. See the "Examples" section and refer to the latest edition of the Cisco IOS Security Configuration Guide for information on how to create these profiles.
Examples
Domain Preauthorization Configuration on the LAC Example
The following example shows the configuration necessary for an L2TP access concentrator (LAC) to participate in domain preauthorization:
!aaa new-modelaaa authorization network default local group radius!vpdn authorize domain!radius-server host 10.9.9.9 auth-port 1645 acct-port 1646radius-server attribute nas-port format dradius-server key MyKeyradius-server vsa send authentication!Domain Preauthorization RADIUS User Profile Example
The following example shows a domain preauthorization RADIUS user profile:
user = nas-port:10.9.9.9:0/0/0/30.33{profile_id = 826profile_cycle = 1radius=Cisco {check_items= {2=cisco}reply_attributes= {9,1="vpdn:vpn-domain-list=net1.com,net2.com"6=5}}vpn service
To configure a static domain name, use the vpn service command in ATM VC or VC class configuration mode. To remove a static domain name, use the no form of this command.
vpn service domain-name
no vpn service domain-name
Syntax Description
Defaults
No default behavior or values
Command Modes
ATM VC configuration
ATM VC class configurationCommand History
Usage Guidelines
Use the vpn service command in a permanent virtual circuit (PVC) or a PVC range configuration so that PPP over ATM (PPPoA) sessions in those PVCs will be forwarded according to the domain name supplied, without starting PPP.
Examples
In the following partial example, virtual private dialup network (VPDN) group 1 is selected for PPPoA session forwarding based on the domain name domain.com:
vpdn-group 1request-dialinprotocol l2tpdomain <domain>.cominitiate-to ip 10.1.1.1 priority 1...interface ATM1/0.1 multipointpvc 101protocol ppp virtual-template 1vpn service domain.comGlossary

Note
Refer to the Internetworking Terms and Acronyms for terms not included in this glossary.
L2TP access concentrator—See LAC.
L2TP network server—See LNS.
Layer 2 Forwarding Protocol—See L2F.
Layer 2 Tunneling Protocol—See L2TP.
L2F—Layer 2 Forwarding Protocol, as described in RFC 2341.
L2TP—Layer 2 Tunneling Protocol, as described in RFC2661.
LAC—L2TP access concentrator. The peer of the LNS that serves as one endpoint of an L2TP tunnel. The client connects to the LAC directly and PPP frames are tunneled over L2TP to the LNS.
LLID—logical line identification. An alphanumeric string that is a minimum of one character and a maximum of 253 characters in length, which is the logical identification of a subscriber line. LLID is maintained in a RADIUS server customer profile database. This customer profile database is connected to a LAC and is separate from the RADIUS server that the LAC and LNS use for the authentication and authorization of incoming users. When the customer profile database receives a preauthorization request from the LAC, the server sends the LLID to the LAC as the Calling-Station-ID attribute (attribute 31).
LNS—L2TP network server. A node that acts as one side of an L2TP tunnel endpoint. A peer to the LAC. The logical termination point of a PPP session that is being tunneled by the LAC.
locally terminated—Refers to a PPP session that will no longer be forwarded. The PPP framing and negotiation ends at this point to allow Layer 3 processing of the framed packet.
logical line identification—See LLID.
MLP—Multilink PPP. Method of splitting, recombining, and sequencing datagrams across multiple logical data links.
multihop—Traditional term for accepting a PPP session from a virtual private dial-up network (VPDN) protocol such as L2TP or L2F and tunneling it back out via L2TP or L2F.
Multilink PPP—See MLP.
NAS—network access server, the L2F equivalent of a LAC.
network access server—See NAS.
Packet Data Serving Node—See PDSN.
PDSN—Packet Data Serving Node. Provides access to the Internet, intranets and applications servers for mobile stations utilizing a cdma2000 Radio Access Network (RAN). Acting as an access gateway, PDSN provides simple IP and mobile IP access, foreign agent support, and packet transport for virtual private networking. It acts as a client for authentication, authorization, and accounting (AAA) servers and provides mobile stations with a gateway to the IP network. Mobility differentiates Cisco's PDSN from the traditional routed network. With PDSN, the host can move and, therefore, there must be a way to forward packets to it. Cisco's PDSN solution offers a secure way to provide packet data services to mobile stations.
PPPoA—PPP over ATM.
PPPoE—PPP over Ethernet (RFC 2516). Refers to the signaling protocol defined within PPPoE and as the encapsulation method. Sometimes ambiguous as to whether this term refers to PPPoE over ATM or PPPoE directly over Ethernet.
PPPoEoA—PPP over Ethernet over ATM. The most common form of PPPoE into LAC.
PPPoEoE—This acronym is often used to differentiate actual PPP over Ethernet from PPPoEoA, but does not imply that PPP is being encapsulated in two levels of Ethernet.
PPPoX—Either PPPoEoA, PPPoEoE, or PPPoA.
service—What a subscriber is provided. Example of a service may be tunneling an incoming PPP session from PPPoE to another location via L2TP, or local termination of the PPPoE session. In addition, QoS parameters or other specifics may be bundled as part of an identified service.
service key—An elemental piece of information about a subscriber that is used to determine a service for that subscriber. Examples include the PPP authenticated name, ATM VPI/VCI, the PPPoE service name, and so on.
SGF—stack group forwarding. Process used by the Stack Group Bidding Protocol (SGBP) to authorize a session for forwarding.
stack group forwarding—See SGF.
subscriber—An access user that typically uses a PPP-based service. This service may be PPPoE, PPPoA, L2TP, PPP over a dial infrastructure such as ISDN or analog, and so on.

Copyright © 2002, 2005 Cisco Systems, Inc. All rights reserved.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback