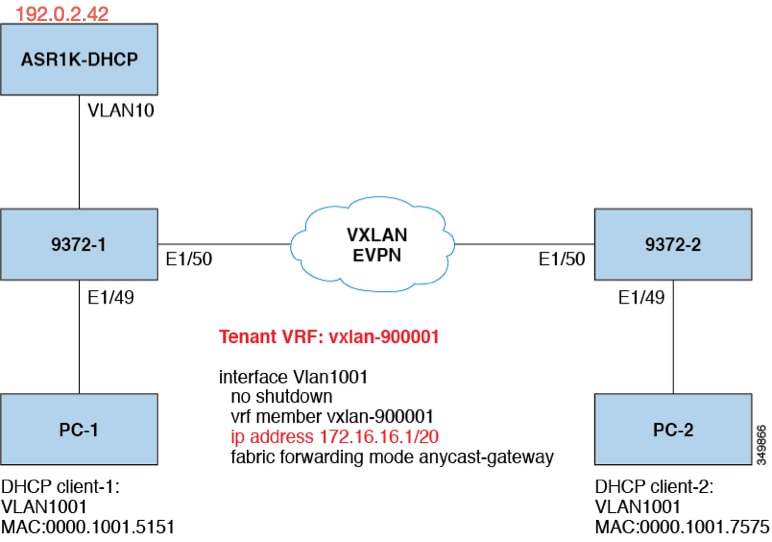
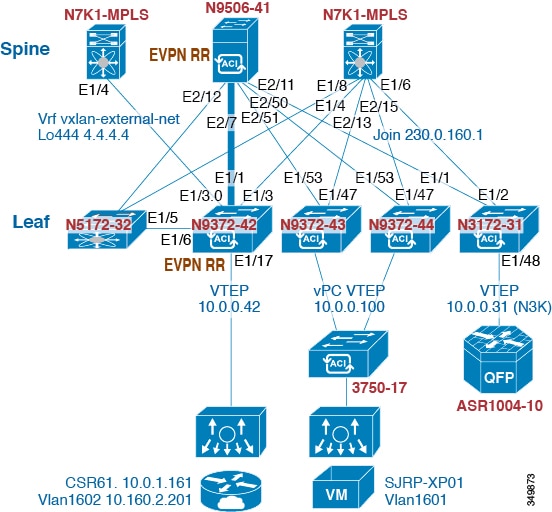
Guidelines and limitations for DHCP relay in VXLAN BGP EVPN
DHCP Relay in VXLAN BGP EVPN has the following configuration guideline and limitation:
-
DHCP Relay in VXLAN BGP EVPN feature is not supported on EoR switches.
DHCP relay in VXLAN BGP EVPN supported release and platform
|
Release |
Platform |
|---|---|
|
7.x and later |
Cisco Nexus 9300-EX/FX/FX2 Series switches |
|
9.2(x) and later |
Cisco Nexus 9300-GX Series switches |
|
9.3(x) and later |
Cisco Nexus 9300-FX3 Series switches |
|
10.2(3)F and later |
Cisco Nexus 9300-GX2 Series switches |
|
10.4(1)F and later |
Cisco Nexus 9332D-H2R switches |
|
10.4(2)F and later |
Cisco Nexus 93400LD-H1 switches |
|
10.4(3)F and later |
Cisco Nexus 9364C-H1 switches |

 Feedback
Feedback