Before You Begin
 Note |
This section is applicable only for customer-hosted solutions. |
Before you begin using Crosswork Data Gateway, Cisco recommends that you complete the following planning and information-gathering steps, in any order you wish:
-
User Roles: Cisco recommends that you use role-based access control to confine users to just the software functions needed to perform their job duties. See Supported User Roles.
-
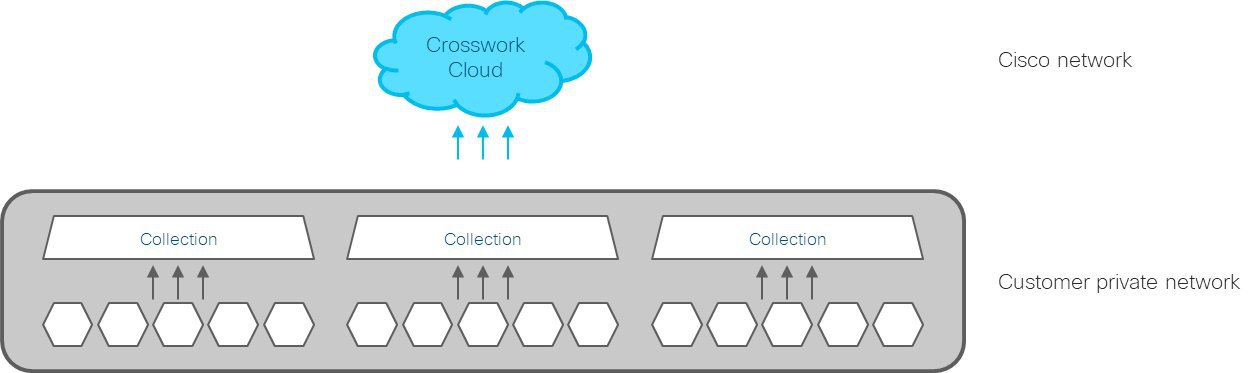
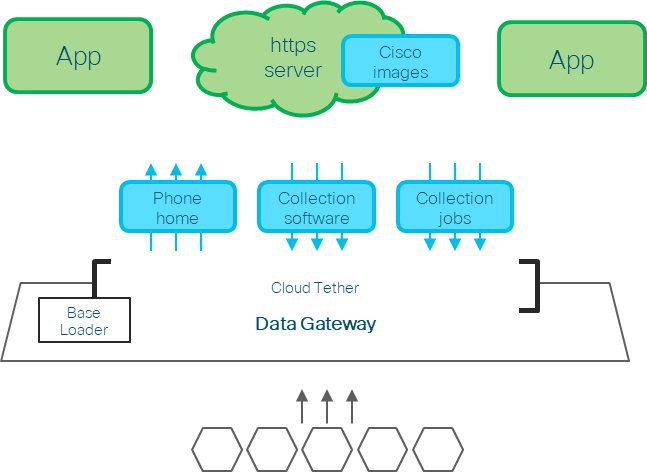
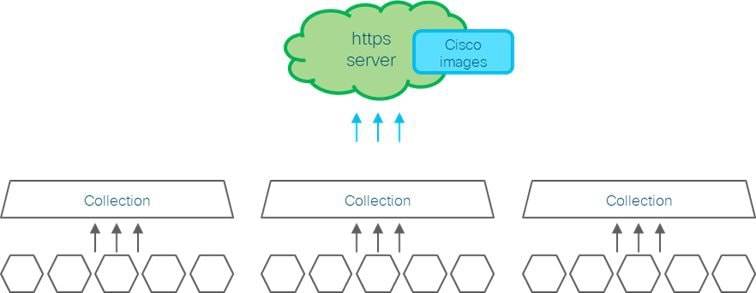
Data Collection: Decide what type of data collection method (CLI, SNMP, or MDT) you want to use, the type of data you want to collect, and duration for which you want to collect the data.
-
Devices: If you are using Crosswork Data Gateway for customer-hosted solution, decide the number of devices you want to collect data from, types of the devices, and OS running on the devices.

Note
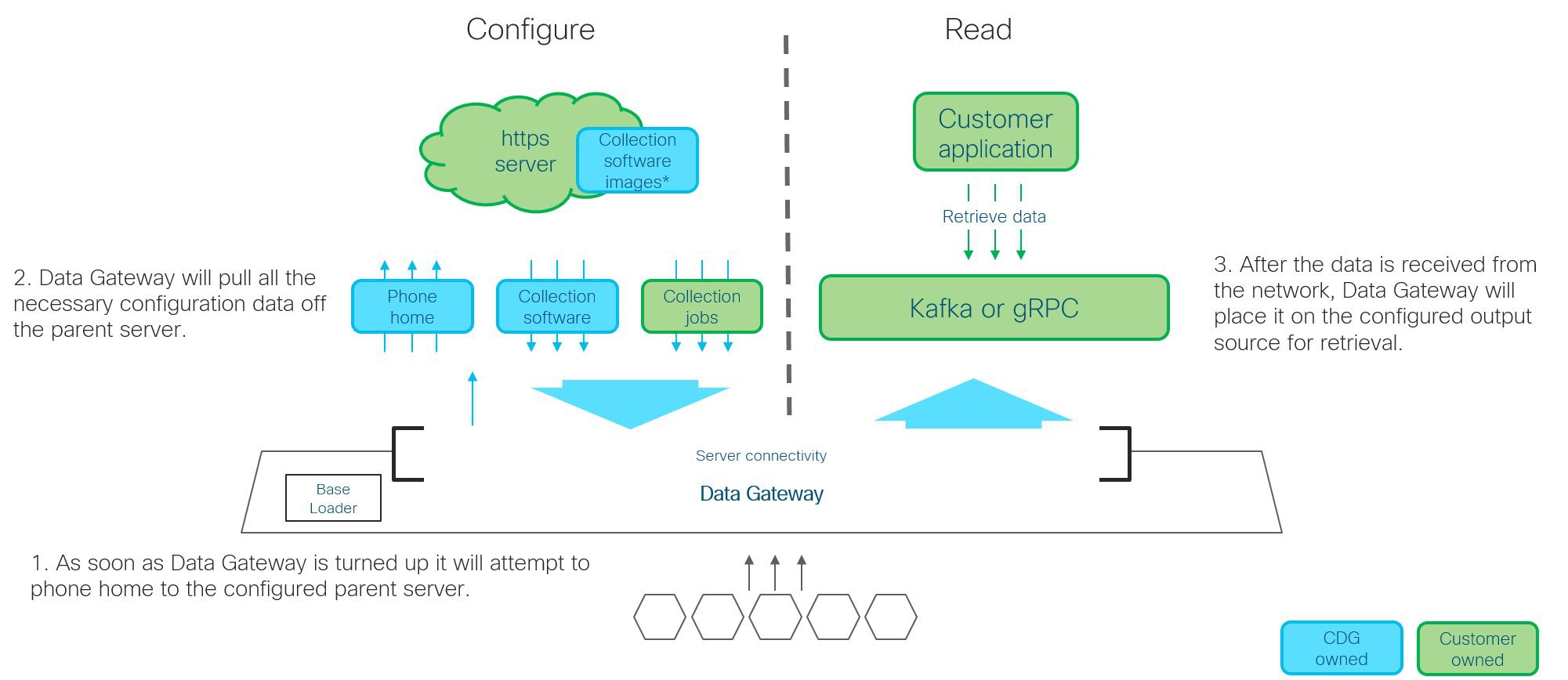
Crosswork Data Gateway is read only to the network. The devices must be configured for the correct data metrics in advance of the Crosswork Data Gateway collecting them.
-
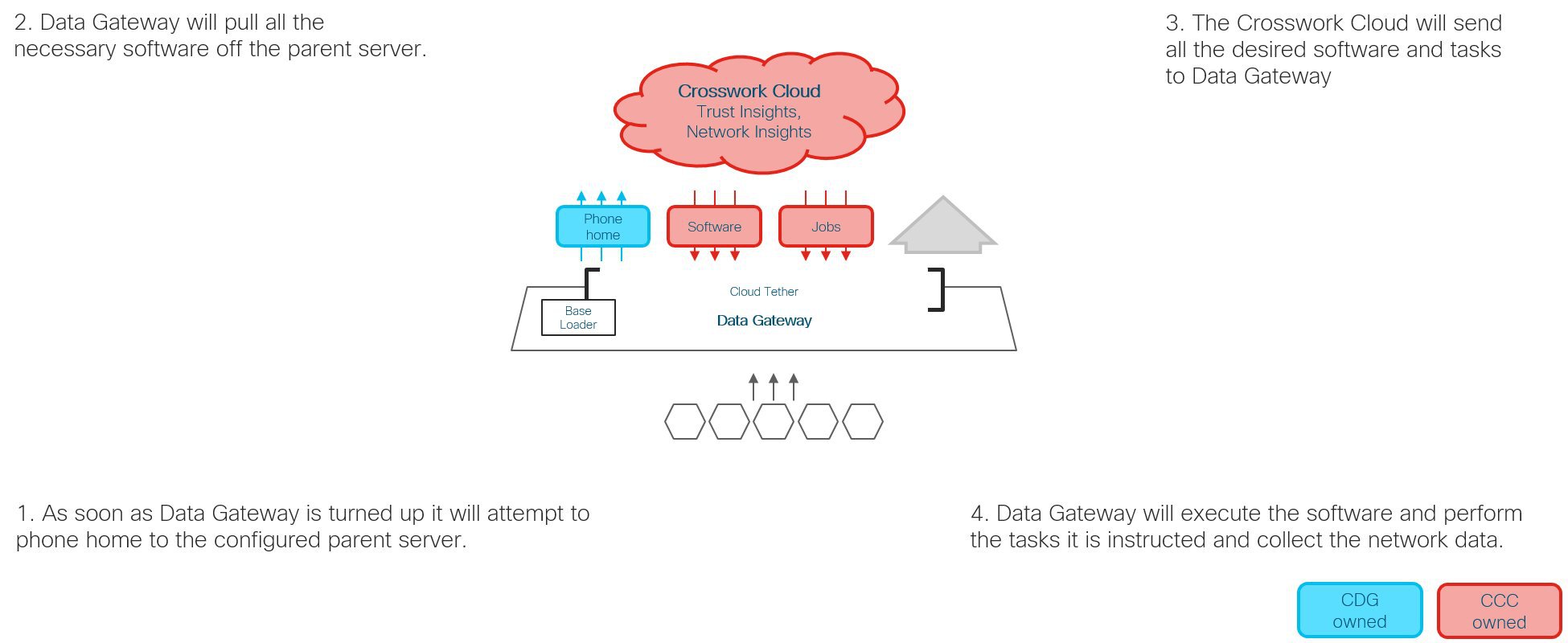
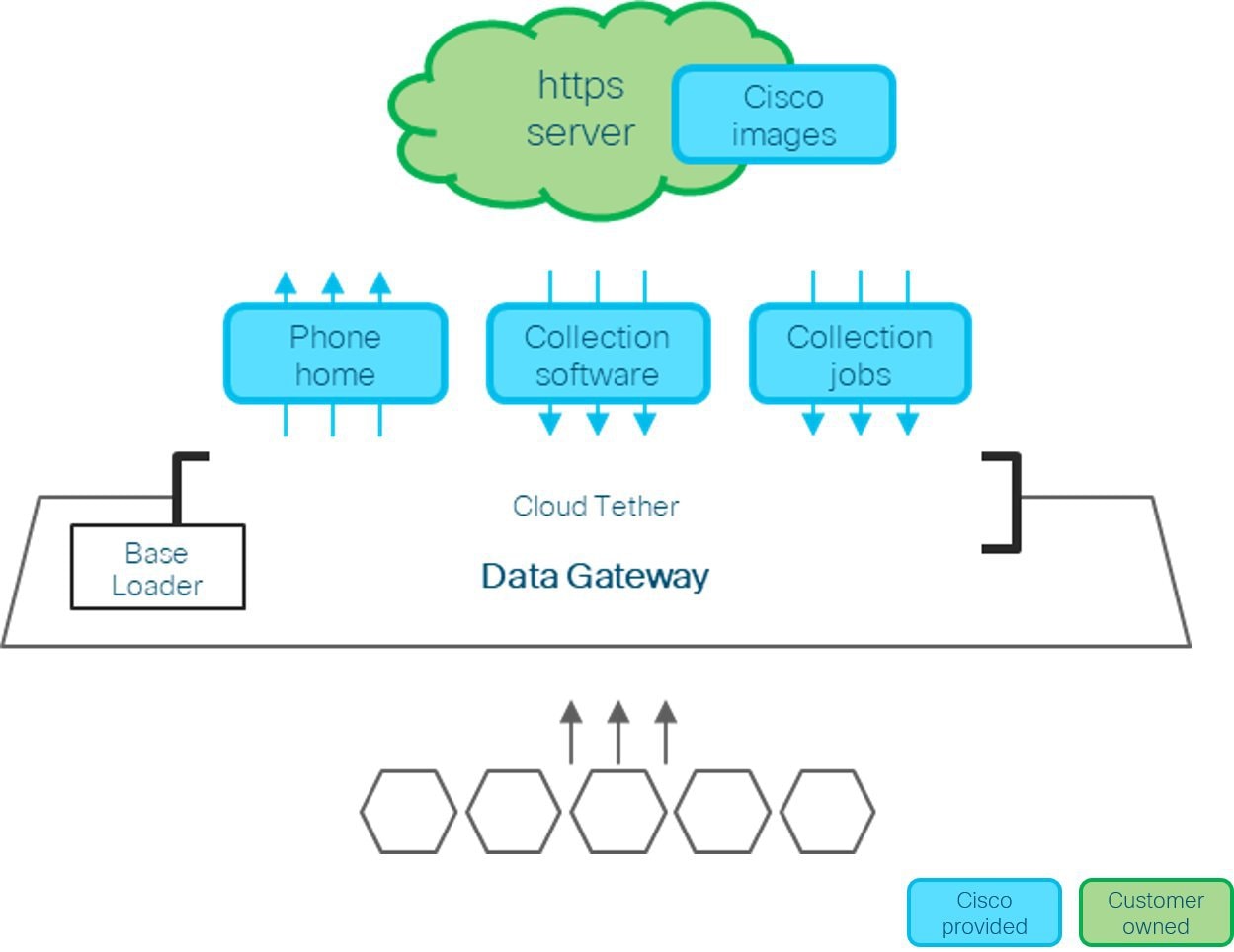
Output Destination: Decide which output server (Kafka or gRPC) you are going to use and ensure it is set up to receive input from Crosswork Data Gateway.
-
Controller: Have your Controller ready to be integrated with Crosswork Data Gateway.
 Feedback
Feedback