Trust in Physical Infrastructure for Service Providers Solution Overview
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Establish trust from the ground up with Cisco’s hardware-anchored security. By embedding advanced protections like Chip Guard and a Secure Unique Device Identifier (SUDI) into every device, Cisco enables service providers to proactively defend against sophisticated threats, ensure regulatory compliance, and deliver reliable, high-quality services customers can count on.
Service providers today face mounting threats that target not just network software but also the underlying physical hardware. Attackers exploit vulnerabilities in the supply chain, firmware, and boot processes, often bypassing traditional security measures and introducing risks like service outages, data breaches, and reputational harm. Additionally, the complexity of multivendor environments and increasing regulatory requirements make it even harder to maintain visibility and trust across all network components.
Cisco’s trusted physical infrastructure solutions address these challenges by embedding security at the hardware level. Features such as Chip Guard and the Secure Unique Device Identifier (SUDI) provide real-time detection of hardware tampering and authenticate each device before it joins the network. Combined with Secure Boot processes, continuous integrity validation, and powerful monitoring tools like Cisco Crosswork® Trust Insights, this solution helps ensure that only genuine, uncompromised devices operate in your network. As a result, service providers gain proactive protection against sophisticated attacks, streamlined compliance, and the operational confidence to deliver reliable, high-quality services to their customers.
● Proactive protection against hardware tampering:
Cisco’s Chip Guard technology detects and responds to unauthorized modifications at the silicon level, helping ensure that only uncompromised devices operate in your network.
● End-to-end device authentication:
The SUDI, securely stored in the Cisco® Trust Anchor Module (TAm), provides cryptographic proof of each device’s authenticity, blocking counterfeit or altered hardware.
● Continuous validation of integrity:
Automated, real-time monitoring and Secure Boot processes verify the integrity of firmware and software, reducing the risk of persistent threats like rootkits and bootloader attacks.
● Regulatory compliance and forensic readiness:
Cisco Crosswork Trust Insights delivers dashboards, alerts, and audit trails to support compliance requirements and accelerate incident response.
● Operational efficiency and service reliability:
Integrated security and automation streamline deployment, minimize manual errors, and help providers deliver consistent, high-quality services.
Rising threats and the need for hardware-level trust
Service providers are facing an unprecedented surge in cyberthreats targeting not only software, but also the physical hardware at the foundation of their networks. Attackers are increasingly sophisticated, exploiting vulnerabilities in the supply chain, firmware, and boot processes—often bypassing traditional network security controls. According to a recent Gartner report, “By 2026, 30% of successful cyberattacks against enterprises will exploit unknown vulnerabilities in hardware and firmware, up from less than 10% today.” This evolving threat environment puts service continuity, customer trust, and regulatory compliance at greater risk than ever before.
As networks become more complex and rely on multivendor ecosystems, maintaining consistent trust and visibility across all components becomes a significant challenge. Service providers must validate the authenticity and integrity of every device, regardless of origin, while also navigating increasing regulatory pressures for stronger auditability and forensic readiness. IDC notes that “Service providers globally are investing in supply chain security and device attestation tools to meet regulatory and customer expectations for trustworthy infrastructure.”
In this landscape, the ability to prove the integrity of your infrastructure—starting at the hardware level—is both a business imperative and a powerful differentiator. Providers that can demonstrate end-to-end security are better positioned to win customer confidence, accelerate service rollouts, and stay ahead of compliance demands. Cisco’s trusted physical infrastructure solutions enable service providers to meet these challenges head-on, turning trust into a strategic advantage.
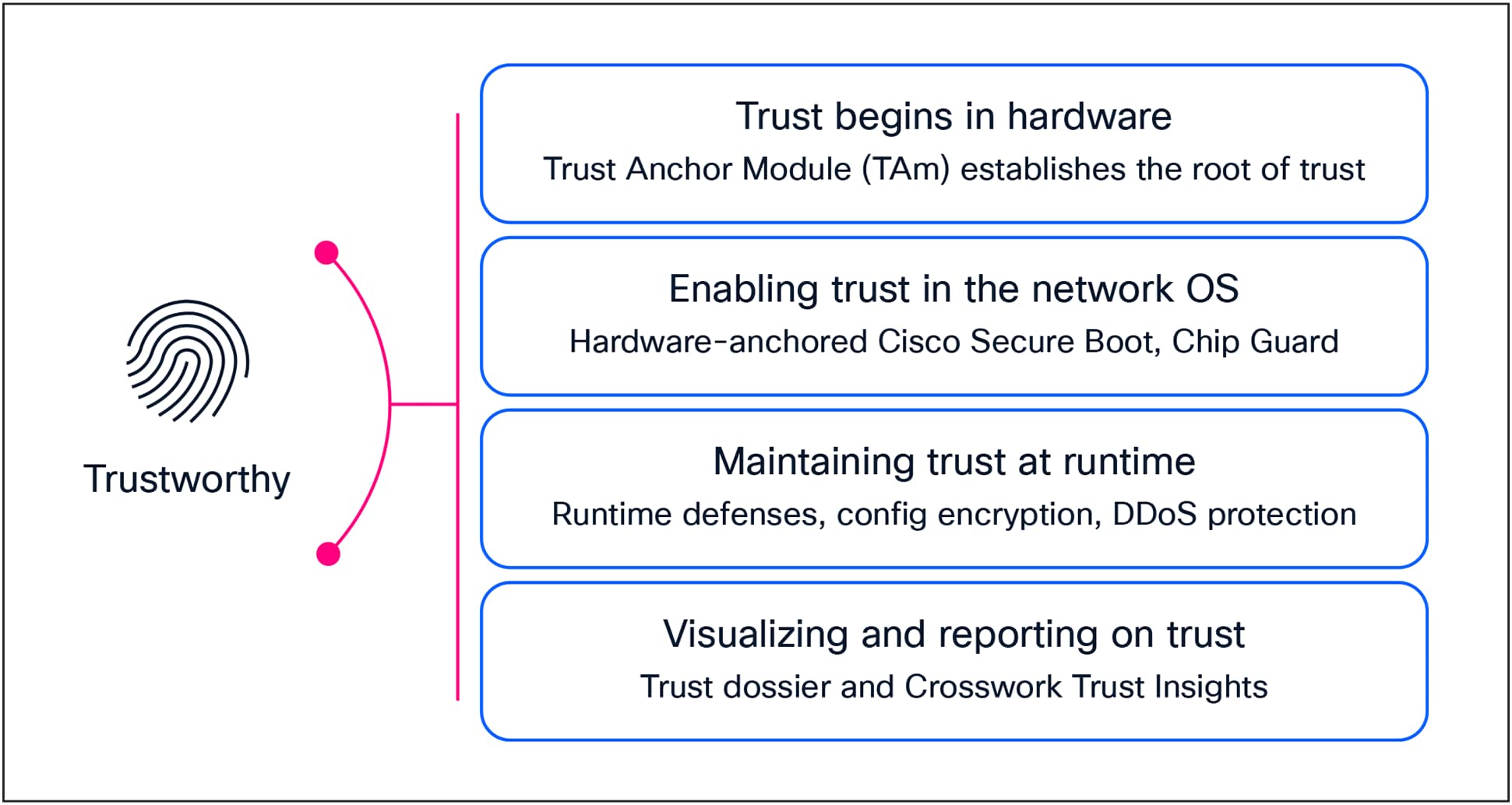
Cisco’s trustworthy platforms
Trust begins in hardware
Cisco’s approach to trusted infrastructure starts at the very foundation—hardware. Each Cisco device integrates a TAm, a tamper-resistant chip that provides secure storage and cryptographic operations. The TAm houses the SUDI, an immutable, factory-provisioned X.509 certificate that uniquely identifies each device and proves its authenticity throughout its lifecycle.
The Secure Boot process is anchored in the hardware. When a Cisco device powers on, the TAm conducts self-checks, verifies the CPU microloader signature, and cryptographically validates the bootloader and Network Operating System (NOS) kernel signatures. This helps ensure that only authentic, unmodified firmware and software are loaded, blocking the execution of bootkits and persistent firmware attacks.
In addition, Chip Guard technology is embedded at the silicon level in select devices, providing real-time monitoring for hardware tampering. If unauthorized changes are detected, the device can be automatically isolated or disabled, protecting the network from compromised or counterfeit hardware.
Enabling trust in the NOS
Trust extends from the hardware into the software that operates on it. Cisco’s Secure Boot process continues into the NOS, requiring all software components—including the bootloader and NOS kernel—to be cryptographically signed and verified before execution. This helps ensure that only authorized, untampered software runs on Cisco devices.
By chaining trust from the hardware root to the NOS, Cisco blocks attempts to load unauthorized or malicious software.
The result is a robust, layered defense that protects against advanced persistent threats and rootkit attacks targeting the operating system level.
Maintaining trust in runtime
Cisco’s commitment to trust does not stop at boot-up. Throughout device operation, Cisco implements continuous validation of integrity. The system collects cryptographically secured hash data from running code, constantly verifying that firmware and software remain in a trusted state.
Runtime defenses such as Address Space Layout Randomization (ASLR) and Built-in Object Size Checking (BOSC) further protect against code injection and exploitation during operation. The TAm also supports attestation, allowing external systems to verify that the device remains uncompromised while in service. These measures provide ongoing assurance against emerging threats and unauthorized changes.
Visualizing and reporting on trust
To deliver comprehensive visibility, Cisco offers Cisco Crosswork Trust Insights, a cloud-based software-as-a-service platform for device trust management. Crosswork Trust Insights aggregates trust and inventory data from across the network via the Crosswork Data Gateway. Service providers can use intuitive dashboards to track system integrity, receive alerts on device trust events, and access investigative workflows for compliance and forensic readiness.
These tools simplify compliance reporting, speed up incident response, and provide verifiable audit trails to demonstrate infrastructure integrity. With these capabilities, service providers can proactively monitor, audit, and report on the trustworthiness of their entire network infrastructure.
In summary, Cisco’s trusted physical infrastructure solution combines hardware-anchored trust, secure software validation, continuous runtime monitoring, and robust visibility tools to deliver end-to-end security and operational confidence for service providers.
“Continuous, automated validation of physical infrastructure is essential; without it,
unauthorized changes or tampering can go unnoticed, exposing networks to risks like route hijacking,
unauthorized access, and service outages.”
“Cisco’s comprehensive approach—combining trustworthy hardware, continuous validation,
integrated security, and supply chain assurance—empowers service providers to build and
sustain trust across their networks.”
Financing to help you achieve your objectives
Cisco Capital® can help you acquire the technology you need to achieve your objectives and stay competitive. We can help you reduce CapEx. Accelerate your growth. Optimize your investment dollars and ROI. Cisco Capital financing gives you flexibility in acquiring hardware, software, services, and complementary third-party equipment. And there’s just one predictable payment.
Cisco Capital is available in more than 100 countries. Learn more.
Cisco uniquely safeguards service provider networks by embedding trust at the hardware level with innovations like Chip Guard and SUDI. Our integrated approach—spanning secure manufacturing, real-time tamper detection, continuous validation, and actionable insights—helps ensure that only authentic, uncompromised devices operate in your network. With Cisco, service providers gain unmatched protection, compliance, and operational confidence, built on decades of leadership in secure infrastructure.
Take the next step toward trusted infrastructure
Discover how Cisco’s hardware-anchored security solutions can protect your network and strengthen customer confidence.
Learn more or request a consultation at: www.cisco.com/go/trustworthy.