Cisco Group-Based Policies for Zero-Trust Security White Paper
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
A Collaborative planning model for state and local governments to expand broadband services in their communities.
The current state of digital infrastructure
Just as video conferencing, mobile technologies, and the Internet of Things (IoT) became widely adopted, a global pandemic unexpectedly struck. The emergence of the COVID-19 virus revealed the inherent inadequacies of these systems and many of their processes. As a result, the flow of goods and services, basic commerce, and delivery of healthcare and education were disrupted globally.
The pandemic exposed the limitations of our various infrastructures. But it also clearly illustrated the inequities, both physical and digital, that exist between those with access to adequate digital infrastructure and those without.
The challenge of digital inequity
Terms such as the digital divide, homework gap, underserved, and unserved have been used to describe the economic, educational, and social shortcomings experienced by many due to a lack of access to digital infrastructure. In general, digital infrastructure is used as a catch-all for a scalable, resilient, and secure communications network.
At the beginning of the pandemic, many government leaders quickly became aware that the lack of access to this digital infrastructure was resulting in negative impacts on the lives of many of their residents, including:
● Children who began falling behind in their studies.
● Patients with chronic or emergency conditions unrelated to COVID-19 who were fearful of seeking in-person care.
● People limiting their access to public resources for employment and other government resources.
The growing awareness for change
This awareness led many government leaders to begin honest and open discussions on how to expand secure and affordable access to digital infrastructure in their communities. Such conversations have reached across a variety of government agencies and their leadership, resulting in:
● School Superintendents who previously focused only on in-person instruction now advancing home broadband access for their instructional staff and students.[1]
● Public health officials and healthcare providers accelerating their call for increased use of, and reimbursement for, telehealth technologies.[2]
● Utility companies seeking ways to build more distributed systems of generation and delivery of services (electric, natural gas, water).[3]
● Public transportation officials turning from ridership issues to resource planning due to increased social distancing demands.[4]
● Public safety officials and first responders calling for modern tools that deliver real-time information sharing to speed incident response and better outcomes for all.[5]
A closer look
The need is real for extending wireless connectivity in communities. Millions of low-income students and adults do not have access to fast and reliable internet in their home.
What if you could bridge that gap to provide access to a better life?
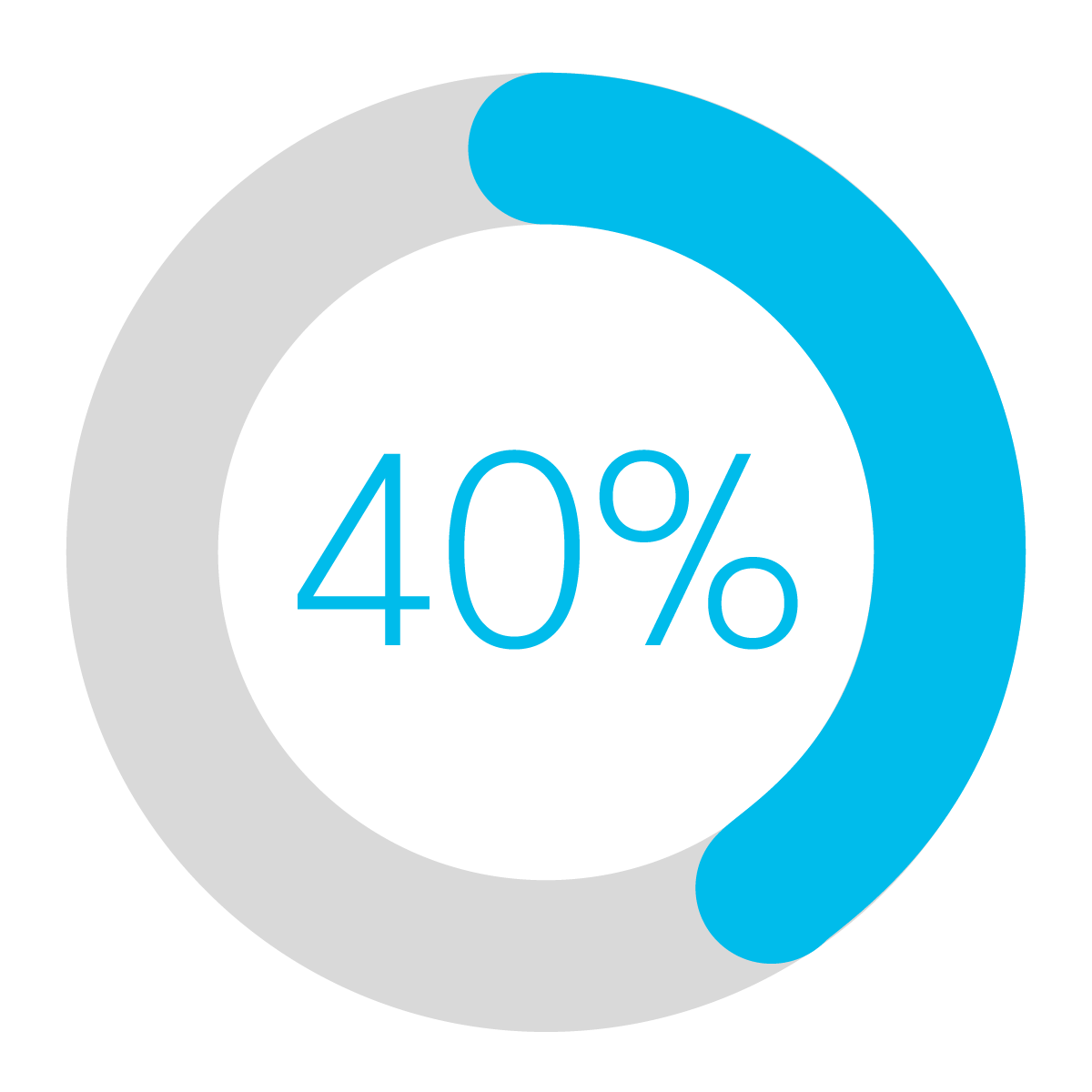
Lower-income parents report public Wi-Fi used to finish homework due to lack of reliable home internet.
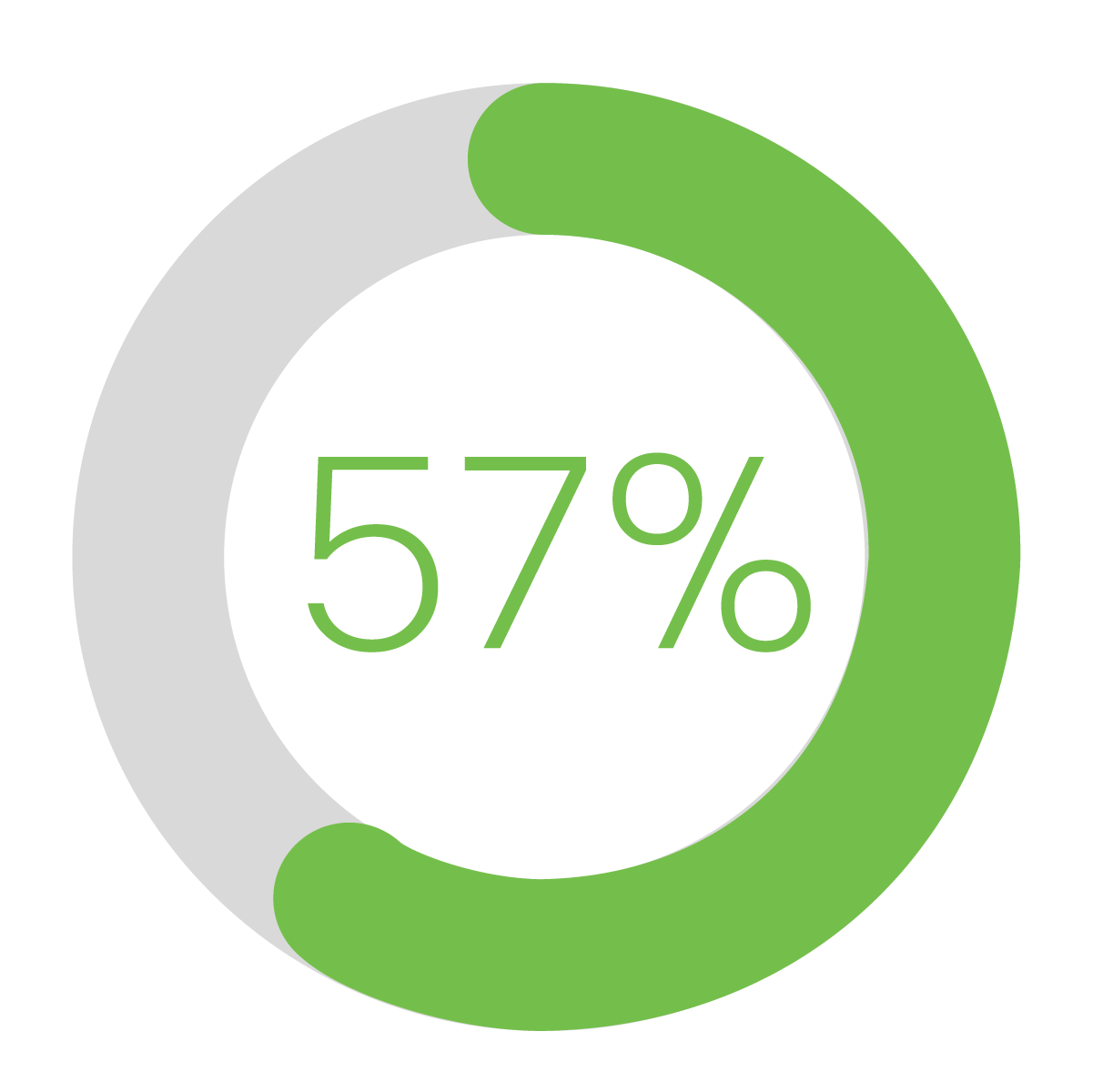
Lower-income U.S. adults have significantly less access to home broadband than those with higher-income levels.
Source: Pew Research
Unprecedented Federal and private funding
In response to the present challenges and expected future demands, the U.S. Congress and the White House have appropriated an unprecedented level of funding to help provide more equitable access to broadband. The total includes up to $800 Billion in direct and indirect investment over the next 5-10 years. The various funding mechanisms created are designed to help overcome challenges related to the prohibitive costs of universal broadband access.
The Federal investment comes from programs like the Coronavirus Aid, Relief, and Economic Security Act (CARES), the American Rescue Plan Act (ARPA), and the Infrastructure Investment and Jobs Act (IIJA). These funding programs will have rules and guidance that will set parameters on the use of this funding. Understanding these funding opportunities can be a challenge. That’s why we encourage you to reach out to the Cisco Public Funding Office. Their experts will be glad to help answer questions and guide you through the funding opportunities that best fit your needs.
Key funding questions to consider before you start
Community leaders should have a sense of urgency in researching and understanding these Federal funds. Some key questions they should consider as they begin their research include:
● Which constituent does this funding source target? Each program will have specific beneficiaries. Local governments should understand these beneficiaries and coordinate across funding sources.
● Is there a match required? Does the local or county government or school district need to provide a match to the Federal funding?
● Is there an unserved or underserved requirement? How is the funding applied to areas where there is currently no broadband service that meets the FCC definition of minimum broadband speed (currently 25Mbps download and 3Mbps upload)? And how is the funding applied to areas that lack 100Mbps download and 20Mbps upload service?
● Can broadband infrastructure be an eligible cost add-on to another type of project (like a water/sewer, natural gas, or electrical power infrastructure project)? Can digital infrastructure costs be rolled into another project?
● What are considered eligible expenses under the funding sources? And what expenses are covered related to planning, project management, engineering, environmental review, construction labor, materials, ongoing maintenance and operating expenses?
● How much flexibility is there for funds allocated to local governments? For example, the U.S. Treasury has put restrictions on how ARPA funds can be used for commercial (residential and business) broadband investments, but these same restrictions do not exist for building digital infrastructure that serve government owned facilities.
Questions when seeking private sector partners
Federal funding will also seed investments of private capital from broadband service providers (such as Verizon, Comcast, AT&T, Charter Spectrum, and Lumen) and private equity firms. So another question public sector organizations should consider is what criteria will they use to select any private sector partners. Some basic criteria when seeking a service provider or private funding partners can include:
● Time horizon match – Does the service provider or private investor have a time horizon for generating a return that matches the reality of the project?
● Cultural fit/shared vision – Does the service provider or private investor share a common vision for outcomes from the project?
● Mutual accountability – Can an agreement between the public entity and the service provider or private investor be crafted so that each side has long term accountability to one another, with claw-backs and penalties for non-performance on either side?
Local Governments as a convener on broadband infrastructure
Local governments are comfortable taking leadership roles in traditional infrastructure planning for their communities. This has generally included assessing their community’s needs for long term investments in both vehicular and pedestrian corridor construction and maintenance as well as traffic control. This involves appointing a lead to outline initial project parameters, followed by adoption of a planning process that includes all stakeholders and that will provide transparency throughout the project’s lifetime.
Appointing a lead to initiate project parameters
As lead, the government agency in charge can assign a point person to do the following:
● Implement surveys, community meetings, and hearings.
● Involve either the regional or metropolitan planning organization to better understand regional impacts of the project(s).
● Engineer or scope potential solutions for the project(s) using internal resources.
● Consider and aggregate funding streams from various sources (Federal, State, Local and in recent years, potential private investment) to determine the feasibility of the project(s).
● Prioritize the list of project(s).
● Seek public input on the prioritization.
● Produce a final list of proposed transportation and transit infrastructure project(s).
Implementing a strong and transparent planning process
Publicly funded broadband infrastructure projects can also benefit from a similar planning process. To help our partners in the public sector achieve success in their broadband efforts, we offer the following broadband planning process projected timeline (Figure 1) and detailed steps. They can help illustrate the value of instituting a formal process by providing guiderails that can increase the comfort level among leaders in government and other stakeholders, increasing buy-in.
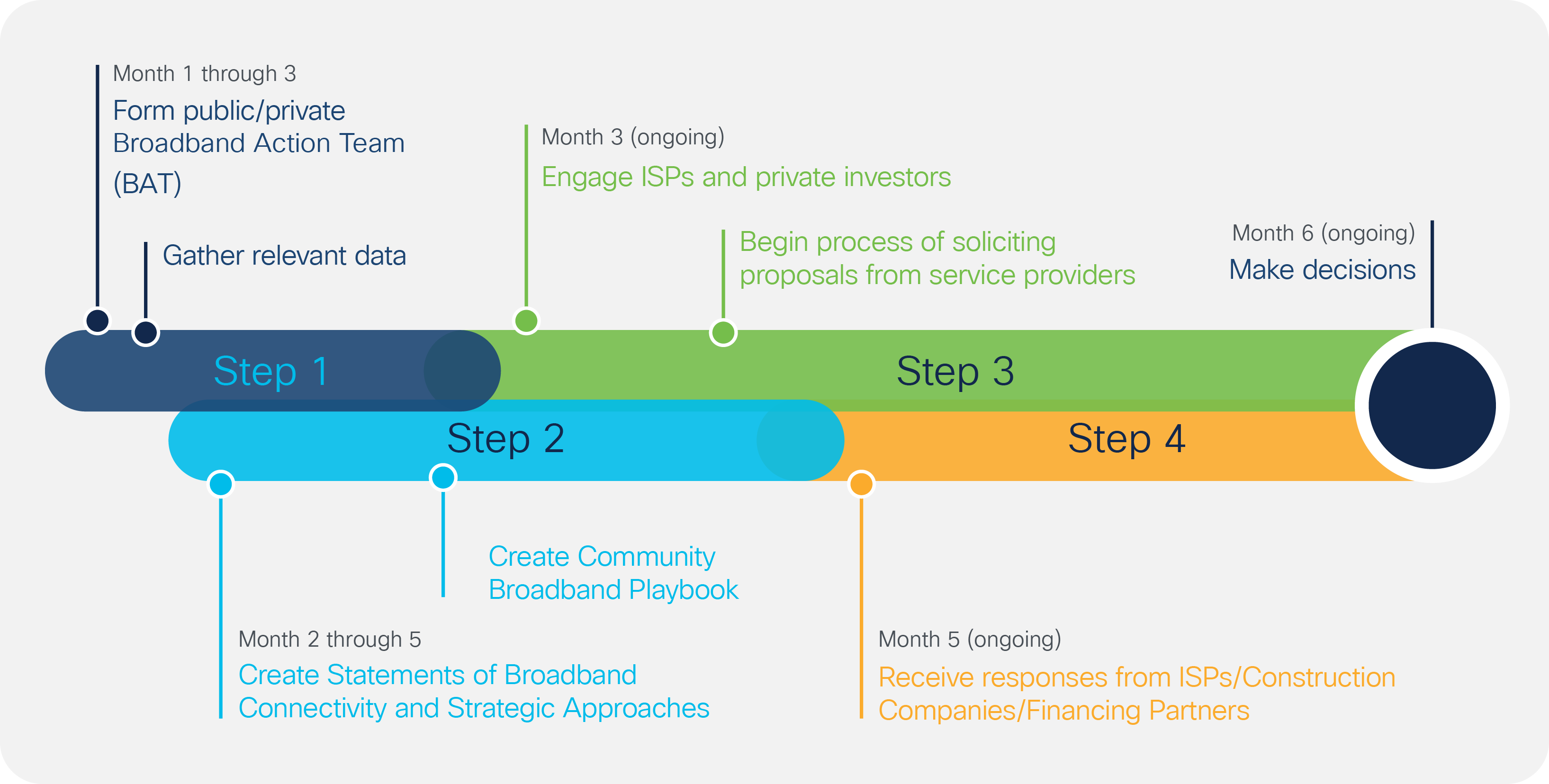
Timeline of the Broadband Planning Process
Terms to know
Digital divide - Refers to the gap between those that have access to computers and internet and those that do not. This gap has disadvantaged those that are poor, rural, elderly, and racial and ethnic minority groups.
Underserved - Some funding programs define this as areas that are served by lower speed broadband that do not exceed a certain threshold. For example, 100 Mbps download/20 Mbps upload or 25 Mbps download/3 Mbps upload.
Unserved - Some FCC/NTIA programs define this as having internet speeds below 10 Mbps download and 1 Mbps uploads. FCC/NTIA standards being introduced will increase this minimum to 25 Mbps download and 5 Mbps.
Public Private Partnerships (PPP) - A long-term contract between a private party and a government agency for providing a public asset or services.
Open Access Networks - A network in which the physical network infrastructure is utilized by multiple providers delivering service to subscribers.
For leaders in one Texas metro area, Cisco has served as a bridge to advance broadband cooperation.
By reaching across organizational silos, Cisco’s Todd Brown brought twenty-five community leaders together in an integrated workshop to speak freely about their broadband experiences and needs.
Together, Cisco and Mighty River helped leaders of cities, counties, K-12 schools, and institutions of Higher Education better understand Federal funding and the benefits of working collectively to achieve better outcomes.
One example of leveraging resources collectively was the county college’s need to expand three miles of fiber. It’s home city had existing fiber which they could use but college leaders were unaware of it. The workshop allowed them to connect.
Cisco’s Laura Baker is also helping guide leaders in North Texas to their goal of creating the smartest, most connected region in the U.S. They’re bringing together leaders across various levels of government while expanding discussions to include digital equity and seeking engagement at a regional level to help communities connect.
As Todd stated, “at Cisco, we‘re the bridge, helping them build it once and build it together.”
Form a Public/Private Broadband Action Team and gather relevant data.
● Recruit Broadband Action Team (BAT) from elected officials, business leaders (across education, transportation, healthcare), economic development leaders and interested parties. The BAT should have members representing the following constituencies:
◦ Government Direct Broadband Users – Public sector entities who depend upon access to broadband communications services, in real-time, to do their job.
◦ Government Administrative Broadband Users – Public sector entities that use broadband communications service to communicate with their constituents asynchronously and synchronously, but not always in real-time.
◦ Business and Community Anchor Broadband Users – High-use bandwidth users, but often not subject to government procurement.
◦ Residential Broadband Users – Home broadband service users, particularly from low-income areas or underserved areas.
● Survey residential and business users on various aspects of and satisfaction with current broadband service.
● Analyze planned project (road, water/sewer, and other public works construction projects).
◦ Fiber infrastructure in the form of empty conduit, frequent handholes/interconnect points are a relatively inexpensive add-on to public works projects or regulated cooperative or investor-owned utility projects that involve trenching or installation of poles.
◦ Next generation light poles capable of supporting fiber interconnect and multiple radios/antennas using different spectrums for different purposes should be considered in any streetscape modernization projects.
◦ Microtrenching (a .5” to 2” wide trench 1’ to 2’ deep in existing hardscape) is becoming more common and can be less costly.
◦ New advancements in robotic installation of fiber along electrical transmission lines can be faster and less costly than traditional methods.
● Inventory community broadband assets such as existing fiber, conduit, buildings, land, and co-location facilities owned by public sector.
● Gather and assess planned fiber and wireless investments being made by public and private sector entities.
◦ Public safety communications investments, particularly in vertical assets.
◦ Fiber investments based on permit applications.
◦ Wireless infrastructure investments based on spectrum licenses and requests for access to the public right of way for vertical assets.
● Survey community anchor institutions concerning current service and future needs (Government agencies, K-12, higher education, libraries, healthcare, and nonprofits).
● Research Federal funds allocated in these areas and meet with providers to attain status of these deployments. Develop a strategy with the BAT to pursue Federal and State broadband funds available to governments and Internet Service Providers (ISPs).
Create a “Community Broadband Playbook.”
The playbook should include a statement of connectivity needs and strategic approaches as defined by the following elements:
● A market demographic summary noting:
◦ Population densities by area.
◦ Median income.
◦ Median household value.
◦ Internet adoption statistics.
◦ NTIA Broadband Availability Map (Combines Broadband Speed Tests with American Community Survey Data).
◦ FCC maps that are funded by the Broadband Deployment Accuracy and Technological Availability Act (expected publication Q2/Q3 of calendar year 2022).
● Business and Residential Broadband survey results summarizing the surveys distributed in phase one of planning.
● Performance characteristics for broadband needs of underserved or unserved areas.
● Details of priority projects that will address the most prevalent broadband infrastructure gaps in the community. For example:
◦ Match priority projects with potential public sector assets and public sector funding that could be leveraged in partnership with private sector broadband service providers.
◦ Match projects to potential public incentives including rights of way fee waivers, expedited engineering review, and franchise fee waivers.
◦ If the public sector decides to contribute assets, concessions, and/or funding to the priority projects, consider what accountability to construction timelines, initiation of service, and long-term operation of service will the public sector require of the partner to receive these incentives.
● Produce technical specifications for broadband service upgrades in areas that are served by below 100/20 service.
◦ Focus on the areas where local surveys from Step 1 show the following:
◦ Experience frequent outages.
◦ Experience lower than advertised bandwidths.
◦ Experience high frequency of latency/buffering.
◦ Examples of technical specifications may include:
◦ Uptime requirements.
◦ Latency limits.
◦ Packet loss limits.
◦ Jitter limits.
◦ Oversubscription limits in all segments of the network (last mile, upstream to the regional point of presence (PoP), upstream to the Internet PoP).
◦ A continuous requirement to upgrade the service as equipment and other assets reach the end of their depreciable and/or technical support life.
● Define and detail government sector broadband service needs.
Engage the business community.
Engage local and national broadband service providers and private investors to explore option and begin the process of soliciting proposals from these providers.
● Areas to consider during these engagements:
◦ Investigate potentials for public/private partnerships, where the government and private firm each bring their assets and/or expertise and are accountable to each other.
◦ Investigate open access networks so that multiple service providers can service your community and share the infrastructure.
◦ Investigate status of available federal, state, and other grants that can support the project. Explore Federal and State funding opportunities.
Receive responses from ISPs/construction companies/financing partners on key projects.
● Define a process for engaging all local ISPs who have interest in the project(s).
● Implement a vendor evaluation process that is fair, transparent, and promotes long-term accountability of government to the general public and the partner ISPs to government.
● Possible evaluation criteria include:
◦ Ability to meet Service Level Agreement (SLA) standards set by the local government.
◦ Ability to meet the universal service requirement (every residence has the opportunity to subscribe).
◦ Inclusion of a low income service option for residential customers that is at or near the Federal broadband benefit program subsidy for low income families.
◦ Extensions or enhancements (addition of interconnects) of existing infrastructure are prioritized.
◦ Priority given to projects that serve the highest number of unserved homes, businesses, and community anchor institutions with the highest speeds.
◦ Provide enhanced services to K12 schools and higher education facilities in the service areas.
◦ Provide enhanced service to hospitals in the service area.
◦ Provide enhanced service to libraries in the service area.
Make decisions.
● Elected official bodies to make resource allocation decisions.
Cisco’s Business Architecture team is here to help public sector organizations like yours develop a roadmap for community broadband success.
Our team of experts can help you by:
● Engaging key stakeholders and reducing organizational silos
● Identifying potential barriers and solutions
● Distilling priorities
● Facilitating collaboration
The result is an inclusive, high-level executable plan to best achieve community broadband success and bridge the digital divide.
As a global leader in IT, Cisco believes that technology can bring positive change to our communities. That’s why we’re leveraging our solutions and services to help governments and educators connect, secure and automate their networks, extending connectivity to everyone regardless of geographic or economic limitations.
At Cisco, we’re helping the public sector optimize application experiences for all users while increasing transparency and engagement with their residents. Plus we’re guiding the return to work with secure Internet access and safer workplaces. And it’s all protected by industry-leading end-to-end security.
As a proven and reliable partner for public sector organizations like yours, Cisco is committed to overcoming the digital divide to power a more inclusive future for all.
To learn more, visit: Cisco.com.
This white paper was written in collaboration with Mighty River, advisor and counsel to state and local governments and electric utilities on issues related to deployment and operation of broadband infrastructure. www.mightyriverllc.com.
According to a recent study[6], the United States ranks 12th in the world in broadband penetration and 5th in broadband affordability. Yet we rank 3rd in the world in the importance of broadband to our daily lives. By leveraging a broadband planning process, governments and school districts can inspire stakeholders in their community to greater collaborative action to help correct this.
Thanks to historic funding mechanisms by the Federal government, we can finally begin to build the digital infrastructure needed to bridge the digital divide. And by doing so, create a more inclusive connectivity with greater opportunity for all.
Cisco and our ecosystem of partners are here to help communities like yours bridge the digital divide. Let our team of experts in inclusive connectivity, mass-scale infrastructure, and community broadband help bring this collaborative planning model to your community.
Get started at cisco.com/go/digitaldivide.