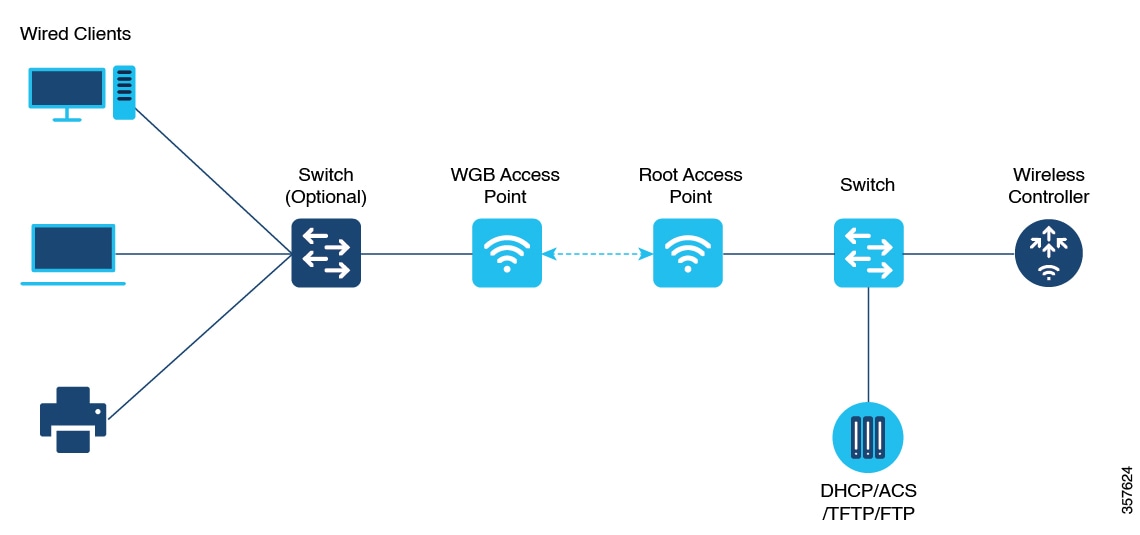
Workgroup Bridge
A Workgroup Bridge (WGB) is a feature in wireless networking that allows a wired device or a group of wired devices to connect to a wireless network. Both Workgroup Bridge (WGB) and Universal Workgroup Bridge (uWGB) modes are part of WGB and that enable seamless connectivity between wired and wireless networks. From Unified Industrial Wireless (UIW) Release 17.13.1, both of these modes are supported on the Cisco Catalyst IW9165E Rugged Access Point (AP) and wireless client.
WGB mode
WGB mode provides wireless connectivity to wired clients connected to the Ethernet port of the WGB.
Key characteristics
-
Bridges the wired network to a wireless segment.
-
Learns the MAC addresses of connected Ethernet-wired clients and shares these identifiers with the Controller. This is done through an AP infrastructure using Internet Access Point Protocol (IAPP) messaging.
-
Establishes a single wireless connection to the root AP, which treats the WGB as a wireless client.
 Note |
This mode is ideal for environments requiring wireless connectivity for wired devices that lack native wireless capabilities. |
Use case of WGB mode
A factory floor uses wired devices such as sensors and PLCs, which lack built-in wireless connectivity. These devices connect to the WGB using Ethernet, and it bridges them to the wireless infrastructure through a single connection to the root AP.
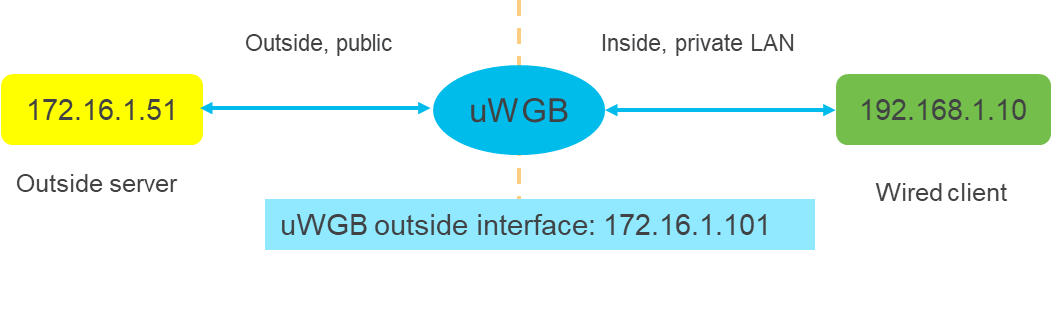
uWGB mode
uWGB mode is a complementary category to the WGB mode, designed to act as a wireless bridge between wired clients and wireless infrastructure.
Key characteristics
-
Supports both Cisco and non-Cisco wireless networks.
-
Uses a wireless interface to connect with the AP, employing the radio MAC address for association.
-
Ensures that wired clients connected to the uWGB can access wireless networks seamlessly.
 Note |
This mode is especially useful in scenarios where interoperability with non-Cisco wireless infrastructure is required. |
Comparison of key features of WGB and uWGB modes
This table outlines the differences between these two modes.
|
Feature |
WGB mode |
uWGB mode |
|---|---|---|
|
Connectivity |
Cisco wireless networks only |
Cisco and non-Cisco wireless networks |
|
Interface usage |
Learns MAC addresses using Ethernet ports |
Uses radio MAC address for association |
Use case of uWGB mode
A retail store employs a point-of-sale (POS) system with wired devices that require connectivity to a wireless network. uWGB connects these devices to the store's wireless infrastructure, supporting both Cisco and non-Cisco wireless networks. The uWGB uses its wireless interface to associate with the AP, enabling seamless communication between the wired POS devices and the wireless network.
Use both of these modes to efficiently extend wireless capabilities to wired devices to enhance both network scalability and flexibility.

 Feedback
Feedback