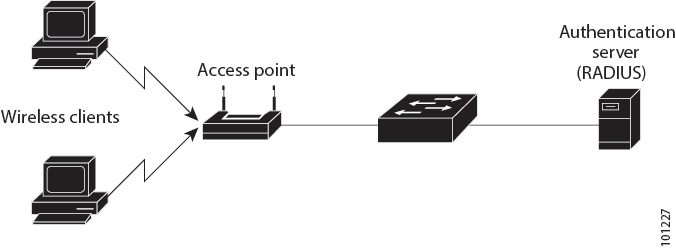
802.1X authentication
IEEE 802.1X port-based authentication is a network security protocol that
-
prevents unauthorized devices from accessing the network
-
utilizes EAP authentication models to ensure secure communication, and
-
integrates with devices like routers, switches, and access points based on configuration.
Feature history
|
Feature name |
Release information |
Feature description |
|---|---|---|
|
802.1X authentication |
Cisco IOS XE 16.9.1 |
IEEE 802.1X port-based authentication is a network security protocol that utilizes EAP authentication models to ensure secure communication, and integrates with devices like routers, switches, and access points based on configuration. |
|
Access ports with dual port authentication |
Cisco IOS XE 17.17.1 |
The access ports with dual port authentication feature supports dual Ethernet ports on Cisco Catalyst 9136 APs and Cisco Wireless 9178I APs. |
Currently, Cisco Wave 2 and Wi-Fi 6 (802.11AX) APs support 802.1X authentication with switch ports for EAP-FAST, EAP-TLS, and EAP-PEAP methods. Configuration and credential provision to APs can be done through the controller.
 Note |
If the AP is dot1x EAP-FAST, upon reboot, it should perform an anonymous PAC provision using ADH cipher suites to establish an authenticated tunnel. Authentication will fail if RADIUS servers do not support ADH cipher suites. |
EAP-FAST protocol
In the EAP-FAST protocol developed by Cisco, to establish a secured TLS tunnel with RADIUS, the AP requires a strong shared key (PAC), provided via in-band or manual out-band provisioning.
-
The EAP-FAST type configuration requires 802.1x credentials configuration for AP, since AP will use EAP-FAST with MSCHAP Version 2 method.
-
Cisco 7925 phones do not support Local EAP.
-
In Cisco Wave 2 APs, for 802.1x authentication using EAP-FAST after PAC provisioning (caused by the initial connection or after AP reload), ensure that you configure the switch port to trigger re-authentication using authentication timer restart num or authentication timer reauthenticate num.
EAP-TLS/EAP-PEAP Protocol
The EAP-TLS protocol or EAP-PEAP protocol provides certificate based mutual EAP authentication.
In EAP-TLS, both the server and the client side certificates are required, where the secured shared key is derived for the particular session to encrypt or decrypt data. In EAP-PEAP, only the server-side certificate is required, and the client authenticates using a password-based protocol in a secured channel.
The EAP-PEAP type configuration requires Dot1x credentials configuration for the AP, and the AP also needs to go through LSC provisioning. AP uses the PEAP protocol with MSCHAP Version 2 method.
 Feedback
Feedback