| Allow AAA Override |
AAA Override option of a WLAN enables you to configure the WLAN for identity networking. It enables you to apply VLAN, Access
Control Lists (ACLs) and Quality of Service (QoS) to individual WLANs on the returned RADIUS attributes from the AAA server.
|
|
PMF
|
This is specific to 802.11w protocol. The 802.11w protocol applies only to a set of robust management frames that are protected
by the Protected Management Frames (PMF) service. These include Disassociation, De-authentication, and Robust Action frames.
|
|
Exclusion List
|
When exclusion list is enabled for a WLAN, clients trying to associate with the corresponding WLAN are put in a blocked list
if they experience authentication failure five times consecutively. The timeout for the clients to be in block list is 180
seconds.
By default, the Exclusion list is enabled for a WLAN.
|
|
SAE Anti-clog Threshold
|
An anti-clogging token is a mechanism to protect entities from Denial of Service (DoS) attack. The anti-clogging token is
bound to the MAC address of the station (STA). The length of the token cannot be more than 256 bytes.
You can configure anti-clogging threshold in terms of resource percentage. On hitting the threshold for the resource, the
primary AP starts to reject authentication commit requests that come with anti-clogging token. Subsequent authentication commit
requests from the client must have the same token. The Primary AP processes only the authentication commit requests that have
valid anti-clogging tokens.
The valid range for the block limit is 0 to 90. If the anti-clogging threshold limit is 90, the anti-clogging is enforced
by the primary AP when the number of clients reach 90 percent of the supported number.
The threshold limit is set to 50 by default.
|
| 802.11r |
802.11r enabled WLAN provides faster roaming for wireless client devices. It is desired that 11r capable devices will be able
to join a WLAN with 11r enabled for better roaming experience. However, if 11r is enabled on a WLAN, the legacy devices (non-11r
clients) will not be able to join the WLAN.
-
This feature help clients roam better by telling them when to roam and providing them with information about neighboring APs
so that no time is wasted scanning when roaming is needed.
-
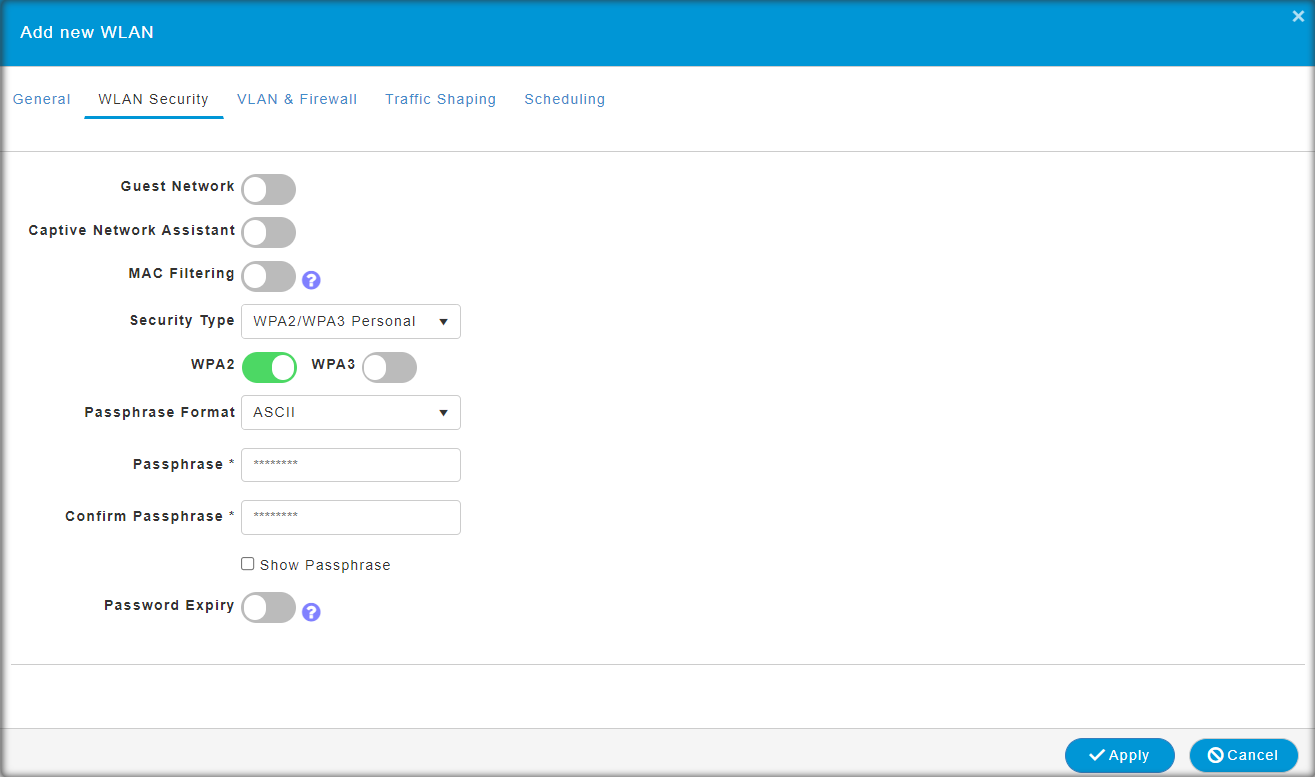
This option is available only for WPA2/WPA3 Personal WLAN with the WPA2 toggle button alone enabled, or WPA2 Enterprise enabled
WLANs. By default, this option is Disabled.
The 802.11r and WPA3 are not compatible with each other.
|
| Over The DS |
Click this button to enable or disable the fast roaming facility. By default, this is Disabled.
|
| Reassociation Timeout(secs) |
Enter the number of seconds after which the re-association attempt of a client to an AP should time out. The valid range is
1 to 100 seconds. The default is 20 seconds.
|
| DTIM Period 802.11a/n (beacon intervals) |
Depending on the timing set for your AP, it “buffers” broadcast and multicast data and let your mobile devices or clients
know when to “wake up” to receive those data.
|
| DTIM Period 802.11b/g/n (beacon intervals) |
Depending on the timing set for your AP, it “buffers” broadcast and multicast data and let your mobile devices or clients
know when to “wake up” to receive those data.
|
| Client Band Select |
Band selection enables client radios that are capable of dual-band (2.4 and 5GHz) operation to move to a less congested band.
|
| Client Load Balancing |
This feature can be used in order to load-balance clients across access points. Enabling this will improve client distribution
on the wireless network.
You cannot configure the number of clients per AP.
|
| Umbrella ProfileUmbrella ModeUmbrella DHC Override |
For details on these options refer to Configuring Cisco Umbrella on Primary AP.
|
| mDNSmDNS Profile |
For details on these options refer to Mapping mDNS Profile to WLAN.
|
|
Multicast IP
|
Enter the Multicast IP group address. By default, the field will be null.
|
|
Multicast Direct
|
Enable the Multicast Direct toggle button to enhance the video streaming for wireless clients by converting multicast packets
to unicast at CBW AP. By default, this is Disabled.
To enable this toggle, change the QoS value under the Traffic Shaping section to Gold or Platinum.
For details, see Media Steam.
|
| 802.11ax BSS Configuration |
|
Down Link MU-MIMO
|
This toggle is used to enable/disable downlink (AP to Wireless Client) multi-user, multiple input, multiple output support
for the WLAN. By default, this is Enabled.
|
|
Up Link MU-MIMO
|
This toggle is used to enable/disable uplink (Wireless Client to AP) multi-user, multiple input, multiple output support for
the WLAN. By default, this is Enabled.
|
|
Down Link OFDMA
|
This toggle is used to enable/disable downlink (AP to Wireless Client) orthogonal frequency-division multiple access support
for the WLAN. By default, this is Enabled.
|
|
Up Link OFDMA
|
This toggle is used to enable/disable uplink (Wireless Client to AP) orthogonal frequency-division multiple access support
for the WLAN. By default, this is Enabled.
|





 Feedback
Feedback
This feature provides social login privileges for guest users that are connected using Google or Facebook accounts. To enable this option, follow the steps below on your AP.