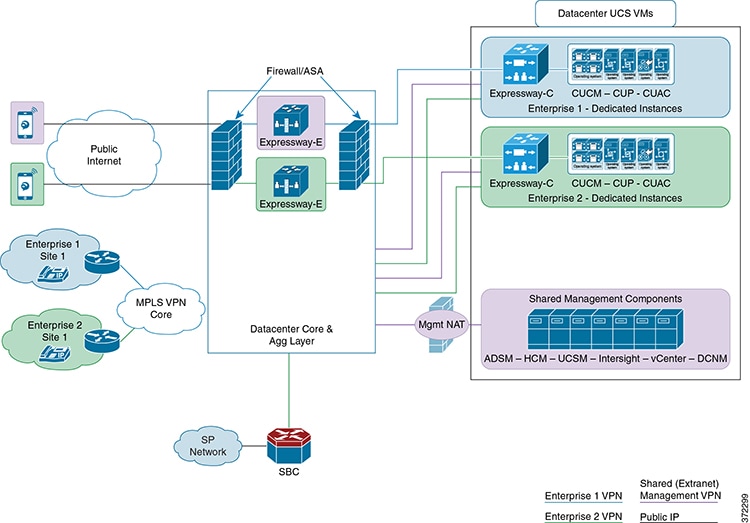
You can enable
Single Sign-On for Jabber client endpoints that access unified communications
services from outside of the network (over the top, OTT). Single Sign-on OTT
relies on the following:
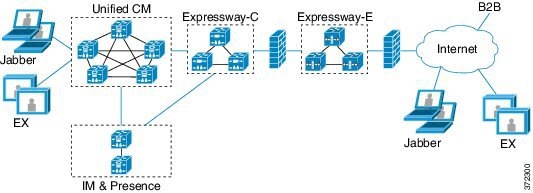
Endpoints connect
using one identity and one authentication mechanism to access multiple unified
communications services. Authentication is owned by the IdP. No authentication
occurs at the Expressway or at the internal unified communications services.
Cisco Jabber
determines whether it is inside your network before it requests a unified
communications service. When Jabber is outside of the network, it requests the
service from the Expressway-E on the edge of the network. If SSO is enabled at
the edge, the Expressway-E redirects Jabber to the IdP with a request to
authenticate the user.
The IdP challenges
Jabber to identify itself. After the identify is authenticated, the IdP
redirects the Jabber service request to the Expressway-E with a signed
assertion that the identity is authentic.
Because the
Expressway-E trusts the IdP, it passes the request to the appropriate service
inside the network. The unified communications service trust the IdP and the
Expressway-E, so it provides the requested service to the Jabber client.
The provisioning of
Jabber Client SSO involves such tasks as downloading the federation metadata
file, configuring Unified CM and Cisco Unity Connection, configuring SAML SSO,
and configuring AD FS. For more information, see the
Cisco Unified Communications Domain Manager Maintain and Operate Guide.
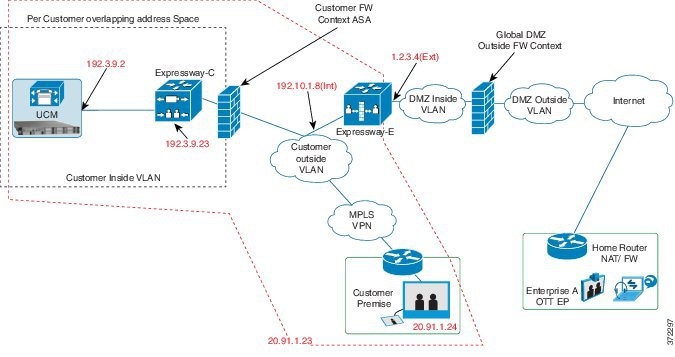
This feature is
supported in the following deployment models:
-
IdP and the
directory are in the customer premises, with LDAP synchronization from the
Directory server to CUCM and then to CUCDM
-
IdP and the
directory are in the customer premises, with LDAP synchronization from the
Directory server to CUCM and then to CUCDM
-
IdP and the
directory are in a per-customer domain in the Data Center, with LDAP
synchronization from the Directory server to CUCM and then to CUCDM
-
IdP and the
directory are in a per-customer domain in the Data Center, with LDAP
synchronization from the Directory server to CUCM and then to CUCDM

 Feedback
Feedback