- About IS-IS
- Licensing Requirements for IS-IS
- Prerequisites for IS-IS
- Guidelines and Limitations for IS-IS
- Default Settings
- Configuring IS-IS
- IS-IS Configuration Modes
- Enabling the IS-IS Feature
- Creating an IS-IS Instance
- Restarting an IS-IS Instance
- Shutting Down IS-IS
- Configuring IS-IS on an Interface
- Shutting Down IS-IS on an Interface
- Configuring IS-IS Authentication in an Area
- Configuring IS-IS Authentication on an Interface
- Configuring a Mesh Group
- Configuring a Designated Intermediate System
- Configuring Dynamic Host Exchange
- Setting the Overload Bit
- Configuring the Attached Bit
- Configuring the Transient Mode for Hello Padding
- Configuring a Summary Address
- Configuring Redistribution
- Limiting the Number of Redistributed Routes
- Disabling Strict Adjacency Mode
- Configuring a Graceful Restart
- Configuring Virtualization
- Tuning IS-IS
- Verifying the IS-IS Configuration
- Monitoring IS-IS
- Configuration Examples for IS-IS
- Related Topics
Configuring IS-IS
This chapter describes how to configure Integrated Intermediate System-to-Intermediate System (IS-IS) on the Cisco NX-OS device.
About IS-IS
IS-IS is an Interior Gateway Protocol (IGP) based on Standardization (ISO)/International Engineering Consortium (IEC) 10589. Cisco NX-OS supports Internet Protocol version 4 (IPv4) and IPv6. IS-IS is a dynamic link-state routing protocol that can detect changes in the network topology and calculate loop-free routes to other nodes in the network. Each router maintains a link-state database that describes the state of the network and sends packets on every configured link to discover neighbors. IS-IS floods the link-state information across the network to each neighbor. The router also sends advertisements and updates on the link-state database through all the existing neighbors.
This section includes the following topics:
- IS-IS Overview
- IS-IS Authentication
- Mesh Groups
- Overload Bit
- Route Summarization
- Route Redistribution
- Load Balancing
- BFD
- Virtualization Support
- High Availability and Graceful Restart
- Multiple IS-IS Instances
IS-IS Overview
IS-IS sends a hello packet out every configured interface to discover IS-IS neighbor routers. The hello packet contains information, such as the authentication, area, and supported protocols, which the receiving interface uses to determine compatibility with the originating interface. The hello packets are also padded to ensure that IS-IS establishes adjacencies only with interfaces that have matching maximum transmission unit (MTU) settings. Compatible interfaces form adjacencies, which update routing information in the link-state database through link-state update messages (LSPs). By default, the router sends a periodic LSP refresh every 10 minutes and the LSPs remain in the link-state database for 20 minutes (the LSP lifetime). If the router does not receive an LSP refresh before the end of the LSP lifetime, the router deletes the LSP from the database.
The LSP interval must be less than the LSP lifetime or the LSPs time out before they are refreshed.
IS-IS sends periodic hello packets to adjacent routers. If you configure transient mode for hello packets, these hello packets do not include the excess padding used before IS-IS establishes adjacencies. If the MTU value on adjacent routers changes, IS-IS can detect this change and send padded hello packets for a period of time. IS-IS uses this feature to detect mismatched MTU values on adjacent routers. For more information, see the “Configuring the Transient Mode for Hello Padding” section.
IS-IS Areas
You can design IS-IS networks as a single area that includes all routers in the network or as multiple areas that connect into a backbone or Level 2 area. Routers in a nonbackbone area are Level 1 routers that establish adjacencies within a local area (intra-area routing). Level 2 area routers establish adjacencies to other Level 2 routers and perform routing between Level 1 areas (inter-area routing). A router can have both Level 1 and Level 2 areas configured. These Level 1/Level 2 routers act as area border routers that route information from the local area to the Level 2 backbone area (see Figure 8-1).
Within a Level 1 area, routers know how to reach all other routers in that area. The Level 2 routers know how to reach other area border routers and other Level 2 routers. Level 1/Level 2 routers straddle the boundary between two areas, routing traffic to and from the Level 2 backbone area. Level1/Level2 routers use the attached (ATT) bit signal Level 1 routers to set a default route to this Level1/Level2 router to connect to the Level 2 area.
In some instances, such as when you have two or more Level1/Level 2 routers in an area, you may want to control which Level1/Level2 router that the Level 1 routers use as the default route to the Level 2 area. You can configure which Level1/Level2 router sets the attached bit. For more information, see the “Verifying the IS-IS Configuration” section.
Each IS-IS instance in Cisco NX-OS supports either a single Level 1 or Level 2 area, or one of each. By default, all IS-IS instances automatically support Level 1 and Level 2 routing.
Figure 8-1 IS-IS Network Divided into Areas
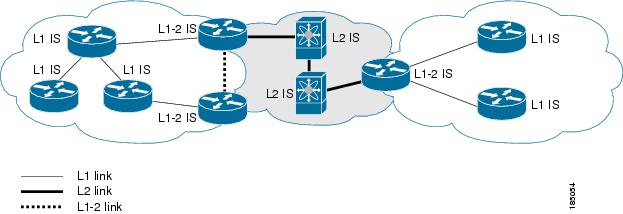
An autonomous system boundary router (ASBR) advertises external destinations throughout the IS-IS autonomous system. External routes are the routes redistributed into IS-IS from any other protocol.
NET and System ID
Each IS-IS instance has an associated network entity title (NET). The NET is comprised of the IS-IS system ID, which uniquely identifies this IS-IS instance in the area and the area ID. For example, if the NET is 47.0004.004d.0001.0001.0c11.1111.00, the system ID is 0000.0c11.1111.00 and the area is ID 47.0004.004d.0001.
Designated Intermediate System
IS-IS uses a designated intermediate system (DIS) in broadcast networks to prevent each router from forming unnecessary links with every other router on the broadcast network. IS-IS routers send LSPs to the DIS, which manages all the link-state information for the broadcast network. You can configure the IS-IS priority that IS-IS uses to select the DIS in an area.

Note![]() No DIS is required on a point-to-point network.
No DIS is required on a point-to-point network.
IS-IS Authentication
You can configure authentication to control adjacencies and the exchange of LSPs. Routers that want to become neighbors must exchange the same password for their configured level of authentication. IS-IS blocks a router that does not have the correct password. You can configure IS-IS authentication globally or for an individual interface for Level 1, Level 2, or both Level 1/Level 2 routing.
IS-IS supports the following authentication methods:
- Clear text—All packets exchanged carry a cleartext 128-bit password.
- MD5 digest—All packets exchanged carry a message digest that is based on a 128-bit key.
To provide protection against passive attacks, IS-IS never sends the MD5 secret key as cleartext through the network. In addition, IS-IS includes a sequence number in each packet to protect against replay attacks.
You can use also keychains for hello and LSP authentication. See the Cisco Nexus 9000 Series NX-OS Security Configuration Guide for information on keychain management.
Mesh Groups
A mesh group is a set of interfaces in which all routers reachable over the interfaces have at least one link to every other router. Many links can fail without isolating one or more routers from the network.
In normal flooding, an interface receives a new LSP and floods the LSP out over all other interfaces on the router. With mesh groups, when an interface that is part of a mesh group receives a new LSP, the interface does not flood the new LSP over the other interfaces that are part of that mesh group.

Note![]() You may want to limit LSPs in certain mesh network topologies to improve network scalability. Limiting LSP floods might also reduce the reliability of the network (in case of failures). For this reason, we recommend that you use mesh groups only if specifically required, and then only after you make a careful network design.
You may want to limit LSPs in certain mesh network topologies to improve network scalability. Limiting LSP floods might also reduce the reliability of the network (in case of failures). For this reason, we recommend that you use mesh groups only if specifically required, and then only after you make a careful network design.
You can also configure mesh groups in block mode for parallel links between routers. In this mode, all LSPs are blocked on that interface in a mesh group after the routers initially exchange their link-state information.
Overload Bit
IS-IS uses the overload bit to tell other routers not to use the local router to forward traffic but to continue routing traffic destined for that local router.
Route Summarization
You can configure a summary aggregate address. Route summarization simplifies route tables by replacing a number of more-specific addresses with an address that represents all the specific addresses. For example, you can replace 10.1.1.0/24, 10.1.2.0/24, and 10.1.3.0/24 with one summary address, 10.1.0.0/16.
If more specific routes are in the routing table, IS-IS advertises the summary address with a metric equal to the minimum metric of the more specific routes.

Note![]() Cisco NX-OS does not support automatic route summarization.
Cisco NX-OS does not support automatic route summarization.
Route Redistribution
You can use IS-IS to redistribute static routes, routes learned by other IS-IS autonomous systems, or routes from other protocols. You must configure a route map with the redistribution to control which routes are passed into IS-IS. A route map allows you to filter routes based on attributes such as the destination, origination protocol, route type, route tag, and so on. For more information, see Chapter15, “Configuring Route Policy Manager”
Whenever you redistribute routes into an IS-IS routing domain, Cisco NX-OS does not, by default, redistribute the default route into the IS-IS routing domain. You can generate a default route into IS-IS, which can be controlled by a route policy.
You also configure the default metric that is used for all imported routes into IS-IS.
Load Balancing
You can use load balancing to allow a router to distribute traffic over all the router network ports that are the same distance from the destination address. Load balancing increases the utilization of network segments and increases the effective network bandwidth.
Cisco NX-OS supports the Equal Cost Multiple Paths (ECMP) feature with up to 16 equal-cost paths in the IS-IS route table and the unicast RIB. You can configure IS-IS to load balance traffic across some or all of those paths.
BFD
This feature supports bidirectional forwarding detection (BFD). BFD is a detection protocol designed to provide fast forwarding-path failure detection times. BFD provides subsecond failure detection between two adjacent devices and can be less CPU-intensive than protocol hello messages because some of the BFD load can be distributed onto the data plane on supported modules. See the Cisco Nexus 9000 Series NX-OS Interfaces Configuration Guide for more information.
Virtualization Support
Cisco NX-OS supports multiple process instances for IS-IS. Each IS-IS instance can support multiple virtual routing and forwarding (VRF) instances, up to the system limit. For the number of supported IS-IS instances, see the Cisco Nexus 9000 Series NX-OS Verified Scalability Guide.
High Availability and Graceful Restart
Cisco NX-OS provides a multilevel high-availability architecture. IS-IS supports stateful restart, which is also referred to as non-stop routing (NSR). If IS-IS experiences problems, it attempts to restart from its previous run-time state. The neighbors would not register any neighbor event in this case. If the first restart is not successful and another problem occurs, IS-IS attempts a graceful restart as per RFC 3847. A graceful restart, or non-stop forwarding (NSF), allows IS-IS to remain in the data forwarding path through a process restart. When the restarting IS-IS interface is operational again, it rediscovers its neighbors, establishes adjacency, and starts sending its updates again. At this point, the NSF helpers recognize that the graceful restart has finished.
A stateful restart is used in the following scenarios:
- First recovery attempt after process experiences problems
- User-initiated switchover using the system switchover command
A graceful restart is used in the following scenarios:
- Second recovery attempt after the process experiences problems within a 4-minute interval
- Manual restart of the process using the restart isis command
- Active supervisor removal
- Active supervisor reload using the reload module active-sup command

Note![]() Graceful restart is on by default, and we strongly recommend that you do not disable it.
Graceful restart is on by default, and we strongly recommend that you do not disable it.
Multiple IS-IS Instances
Cisco NX-OS supports multiple instances of the IS-IS protocol that run on the same node. You cannot configure multiple instances over the same interface. Every instance uses the same system router ID. For the number of supported IS-IS instances, see the Cisco Nexus 9000 Series NX-OS Verified Scalability Guide.
Licensing Requirements for IS-IS
The following table shows the licensing requirements for this feature:
Prerequisites for IS-IS
IS-IS has the following prerequisites:
- You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
Guidelines and Limitations for IS-IS
IS-IS has the following configuration guidelines and limitations:
Default Settings
Table 8-1 lists the default settings for IS-IS parameters.
|
|
|
|---|---|
Configuring IS-IS
To configure IS-IS, follow these steps:
Step 1![]() Enable the IS-IS feature (see the “Enabling the IS-IS Feature” section).
Enable the IS-IS feature (see the “Enabling the IS-IS Feature” section).
Step 2![]() Create an IS-IS instance (see the “Creating an IS-IS Instance” section).
Create an IS-IS instance (see the “Creating an IS-IS Instance” section).
Step 3![]() Add an interface to the IS-IS instance (see the “Configuring IS-IS on an Interface” section).
Add an interface to the IS-IS instance (see the “Configuring IS-IS on an Interface” section).
Step 4![]() Configure optional features, such as authentication, mesh groups, and dynamic host exchange.
Configure optional features, such as authentication, mesh groups, and dynamic host exchange.
This section contains the following topics:
- IS-IS Configuration Modes
- Enabling the IS-IS Feature
- Creating an IS-IS Instance
- Restarting an IS-IS Instance
- Shutting Down IS-IS
- Configuring IS-IS on an Interface
- Shutting Down IS-IS on an Interface
- Configuring IS-IS Authentication in an Area
- Configuring IS-IS Authentication on an Interface
- Configuring a Mesh Group
- Configuring a Designated Intermediate System
- Configuring Dynamic Host Exchange
- Setting the Overload Bit
- Configuring the Attached Bit
- Configuring the Transient Mode for Hello Padding
- Configuring a Summary Address
- Configuring Redistribution
- Limiting the Number of Redistributed Routes
- Disabling Strict Adjacency Mode
- Configuring a Graceful Restart
- Configuring Virtualization
- Tuning IS-IS

Note![]() If you are familiar with the Cisco IOS CLI, be aware that the Cisco NX-OS commands for this feature might differ from the Cisco IOS commands that you would use.
If you are familiar with the Cisco IOS CLI, be aware that the Cisco NX-OS commands for this feature might differ from the Cisco IOS commands that you would use.
IS-IS Configuration Modes
The following sections show how to enter each of the configuration modes. From a mode, you can enter the ? command to display the commands available in that mode.
Router Configuration Mode
This example shows how to enter router configuration mode:
Router Address Family Configuration Mode
This example shows how to enter router address family configuration mode:
Enabling the IS-IS Feature
You must enable the IS-IS feature before you can configure IS-IS.
SUMMARY STEPS
DETAILED STEPS
|
|
|
|
|---|---|---|
To disable the IS-IS feature and remove all associated configuration, use the following command in configuration mode:
|
|
|
|---|---|
Disables the IS-IS feature and removes all associated configurations. |
Creating an IS-IS Instance
You can create an IS-IS instance and configure the area level for that instance.
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
SUMMARY STEPS
4.![]() (Optional) is-type {l evel-1 | level-2 | level-1-2 }
(Optional) is-type {l evel-1 | level-2 | level-1-2 }
DETAILED STEPS
To remove the IS-IS instance and the associated configuration, use the following command in configuration mode:
|
|
|
|---|---|
Deletes the IS-IS instance and all associated configurations. |

Note![]() You must also remove any IS-IS commands that are configured in interface mode to completely remove all configurations for the IS-IS instance.
You must also remove any IS-IS commands that are configured in interface mode to completely remove all configurations for the IS-IS instance.
You can configure the following optional parameters for IS-IS:
This example shows how to create an IS-IS instance in a level 2 area:
switch(config)# router isis Enterprise
switch(config-router)# net 47.0004.004d.0001.0001.0c11.1111.00
switch(config-router)# is-type level 2
switch(config-router)# copy running-config startup-config
To clear neighbor statistics and remove adjacencies, use the following command in router configuration mode:
|
|
|
|---|---|
clear isis [ instance-tag ] adjacency [ * | system-id | interface ] |
Clears neighbor statistics and removed adjacencies for this IS-IS instance. |
Restarting an IS-IS Instance
You can restart an IS-IS instance. This action clears all neighbors for the instance.
To restart an IS-IS instance and remove all associated neighbors, use the following command:
|
|
|
|---|---|
Shutting Down IS-IS
You can shut down the IS-IS instance. This action disables this IS-IS instance and retains the configuration.
To shut down the IS-IS instance, use the following command in router configuration mode:
|
|
|
|---|---|
Configuring IS-IS on an Interface
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
SUMMARY STEPS
2.![]() interface interface-type slot/port
interface interface-type slot/port
3.![]() (Optional) medium { broadcast | p2p }
(Optional) medium { broadcast | p2p }
4.![]() {ip | ipv6} router isis instance-tag
{ip | ipv6} router isis instance-tag
5.![]() (Optional) show isis [ vrf vrf-name ] [ instance-tag ] interface [ interface-type slot/port ]
(Optional) show isis [ vrf vrf-name ] [ instance-tag ] interface [ interface-type slot/port ]
DETAILED STEPS
You can configure the following optional parameters for IS-IS in interface mode:
This example shows how to add Ethernet 1/2 interface to an IS-IS instance:
switch(config)# interface ethernet 1/2
Shutting Down IS-IS on an Interface
You can gracefully shut down IS-IS on an interface. This action removes all adjacencies and stops IS-IS traffic on this interface but preserves the IS-IS configuration.
To disable IS-IS on an interface, use the following command in interface configuration mode:
|
|
|
|---|---|
Disables IS-IS on this interface. The IS-IS interface configuration remains. |
Configuring IS-IS Authentication in an Area
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
You must configure the keychain in global configuration mode if you reference it from the IS-IS configuration. See “Configuring Keychain Management” in the Cisco Nexus 9000 Series NX-OS Security Configuration Guide.
SUMMARY STEPS
3.![]() authentication-type { cleartext | md5 } {l evel-1 | level-2 }
authentication-type { cleartext | md5 } {l evel-1 | level-2 }
4.![]() authentication key-chain key { level-1 | level-2 }
authentication key-chain key { level-1 | level-2 }
DETAILED STEPS
This example shows how to configure cleartext authentication on an IS-IS instance:
switch(config)# router isis Enterprise
switch(config-router)# authentication-type cleartext level-2
switch(config-router)# authentication key-chain ISISKey level-2
Configuring IS-IS Authentication on an Interface
You can configure IS-IS to authenticate Hello packets on an interface.
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
SUMMARY STEPS
2.![]() interface interface-type slot/port
interface interface-type slot/port
3.![]() isis authentication-type { cleartext | md5 } { level-1 | level-2 }
isis authentication-type { cleartext | md5 } { level-1 | level-2 }
4.![]() isis authentication key-chain key { level-1 | level-2 }
isis authentication key-chain key { level-1 | level-2 }
5.![]() (Optional) isis authentication-check { level-1 | level-2 }
(Optional) isis authentication-check { level-1 | level-2 }
DETAILED STEPS
This example shows how to configure cleartext authentication on an IS-IS instance:
switch(config)# interface ethernet 1/2
switch(config-if)# isis authentication-type cleartext level-2
switch(config-if)# isis authentication key-chain ISISKey
switch(config-if)# copy running-config startup-config
Configuring a Mesh Group
You can add an interface to a mesh group to limit the amount of LSP flooding for interfaces in that mesh group. You can optionally block all LSP flooding on an interface in a mesh group.
To add an interface to a mesh group, use the following command in interface configuration mode:
|
|
|
|---|---|
Adds this interface to a mesh group. The range is from 1 to 4294967295. |
Configuring a Designated Intermediate System
You can configure a router to become the designated intermediate system (DIS) for a multiaccess network by setting the interface priority.
To configure the DIS, use the following command in interface configuration mode:
|
|
|
|---|---|
Sets the priority for DIS selection. The range is from 0 to 127. The default is 64. |
Configuring Dynamic Host Exchange
You can configure IS-IS to map between the system ID and the hostname for a router using dynamic host exchange.
To configure dynamic host exchange, use the following command in router configuration mode:
|
|
|
|---|---|
Setting the Overload Bit
You can configure the router to signal other routers not to use this router as an intermediate hop in their shortest path first (SPF) calculations. You can optionally configure the overload bit temporarily on startup, until BGP converges.
In addition to setting the overload bit, you might also want to suppress certain types of IP prefix advertisements from LSPs for Level 1 or Level 2 traffic.
To set the overload bit, use the following command in router configuration mode:
Configuring the Attached Bit
You can configure the attached bit to control which Level 1/Level 2 router that the Level 1 routers use as the default route to the Level 2 area. If you disable setting the attached bit, the Level 1 routers do not use this Level 1/Level 2 router to reach the Level 2 area.
To configure the attached bit for a Level 1/Level 2 router, use the following command in router configuration mode:
|
|
|
|---|---|
Configures the Level 1/Level 2 router to set the attached bit. This feature is enabled by default. |
Configuring the Transient Mode for Hello Padding
You can configure the transient mode for hello padding to pad hello packets when IS-IS establishes adjacency and remove that padding after IS-IS establishes adjacency.
To configure the mode for hello padding, use the following command in router configuration mode:
|
|
|
|---|---|
Pads the hello packet to the full maximum transmission unit (MTU). The default is enabled. Use the no form of this command to configure the transient mode of hello padding. |
Configuring a Summary Address
You can create aggregate addresses that are represented in the routing table by a summary address. One summary address can include multiple groups of addresses for a given level. Cisco NX-OS advertises the smallest metric of all the more-specific routes.
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
SUMMARY STEPS
3.![]() address-family {ipv4 | ipv6} unicast
address-family {ipv4 | ipv6} unicast
4.![]() summary-address ip-prefix/mask-len { level-1 | level-2 | level-1-2 }
summary-address ip-prefix/mask-len { level-1 | level-2 | level-1-2 }
5.![]() (Optional) show isis [ vrf vrf-name ] { ip | ipv6} summary-address ip-prefix [ longer-prefixes ]
(Optional) show isis [ vrf vrf-name ] { ip | ipv6} summary-address ip-prefix [ longer-prefixes ]
DETAILED STEPS
This example shows how to configure an IPv4 unicast summary address for IS-IS:
switch(config)# router isis Enterprise
switch(config-router)# address-family ipv4 unicast
switch(config-router-af)# summary-address 192.0.2.0/24 level-2
switch(config-router-af)# copy running-config startup-config
Configuring Redistribution
You can configure IS-IS to accept routing information from another routing protocol and redistribute that information through the IS-IS network. You can optionally assign a default route for redistributed routes.
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
SUMMARY STEPS
3.![]() address-family { ipv4 | ipv6} unicast
address-family { ipv4 | ipv6} unicast
4.![]() redistribute { bgp as | direct |{ eigrp | isis | ospf | ospfv3 | rip } instance-tag | static } route-map map-name
redistribute { bgp as | direct |{ eigrp | isis | ospf | ospfv3 | rip } instance-tag | static } route-map map-name
5.![]() (Optional) default-information originate [ always ] [ route-map map-name ]
(Optional) default-information originate [ always ] [ route-map map-name ]
6.![]() (Optional) distribute { level-1 | level-2 } into { level-1 | level-2 } { route-map route-map | all }
(Optional) distribute { level-1 | level-2 } into { level-1 | level-2 } { route-map route-map | all }
7.![]() (Optional) show isis [ vrf vrf-name ] { ip | ipv6} route ip-prefix [ detail | longer-prefixes [ summary | detail ]]
(Optional) show isis [ vrf vrf-name ] { ip | ipv6} route ip-prefix [ detail | longer-prefixes [ summary | detail ]]
DETAILED STEPS
|
|
|
|
|---|---|---|
Creates a new IS-IS instance with the configured instance tag. |
||
address-family {ipv4 | ipv6} unicast |
||
redistribute { bgp as | { eigrp | isis | ospf | ospfv3 | rip } instance-tag | static | direct } route-map map-name switch(config-router-af)# redistribute eigrp 201 route-map ISISmap |
Redistributes routes from other protocols into IS-IS. See the “Configuring Route Maps” section for more information about route maps. |
|
default-information originate [ always ] [ route-map map-name ] switch(config-router-af)# default-information originate always |
||
distribute { level-1 | level-2 } into { level-1 | level-2 } { route-map route-map | all } switch(config-router-af)# distribute level-1 into level-2 all |
(Optional) Redistributes routes from one IS-IS level to the other IS-IS level. |
|
show isis [ vrf vrf-name ] { ip | ipv6} route ip-prefix [ detail | longer-prefixes [ summary | detail ]] |
||
copy running-config startup-config switch(config-router-af)# copy running-config startup-config |
This example shows how to redistribute EIGRP into IS-IS:
switch(config)# router isis Enterprise
switch(config-router)# address-family ipv4 unicast
switch(config-router-af)# redistribute eigrp 201 route-map ISISmap
switch(config-router-af)# copy running-config startup-config
Limiting the Number of Redistributed Routes
Route redistribution can add many routes to the IS-IS route table. You can configure a maximum limit to the number of routes accepted from external protocols. IS-IS provides the following options to configure redistributed route limits:
- Fixed limit—Logs a message when IS-IS reaches the configured maximum. IS-IS does not accept any more redistributed routes. You can optionally configure a threshold percentage of the maximum where IS-IS logs a warning when that threshold is passed.
- Warning only—Logs a warning only when IS-IS reaches the maximum. IS-IS continues to accept redistributed routes.
- Withdraw—Starts the timeout period when IS-IS reaches the maximum. After the timeout period, IS-IS requests all redistributed routes if the current number of redistributed routes is less than the maximum limit. If the current number of redistributed routes is at the maximum limit, IS-IS withdraws all redistributed routes. You must clear this condition before IS-IS accepts more redistributed routes. You can optionally configure the timeout period.
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
SUMMARY STEPS
3.![]() redistribute { bgp id | direct | eigrp id | isis id | ospf id | rip id | static } route-map map-name
redistribute { bgp id | direct | eigrp id | isis id | ospf id | rip id | static } route-map map-name
4.![]() redistribute maximum-prefix max [ threshold ] [ warning-only | withdraw [ num-retries timeout ]]
redistribute maximum-prefix max [ threshold ] [ warning-only | withdraw [ num-retries timeout ]]
DETAILED STEPS
This example shows how to limit the number of redistributed routes into IS-IS:
switch(config)# router eigrp isis Enterprise
switch(config-router)# redistribute bgp route-map FilterExternalBGP
Disabling Strict Adjacency Mode
When both IPv4 and IPv6 address families are enabled, strict adjacency mode is enabled by default. In this mode, the device does not form an adjacency with any router that does not have both address families enabled. You can disable strict adjacency mode using the no adjacency-check command.
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
SUMMARY STEPS
3.![]() address-family ipv4 unicast
address-family ipv4 unicast
6.![]() address-family ipv6 unicast
address-family ipv6 unicast
DETAILED STEPS
|
|
|
|
|---|---|---|
Creates a new IS-IS instance with the configured instance tag. |
||
copy running-config startup-config switch(config-router-af)# copy running-config startup-config |
Configuring a Graceful Restart
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
SUMMARY STEPS
4.![]() graceful-restart t3 manual time
graceful-restart t3 manual time
DETAILED STEPS
This example shows how to enable a graceful restart:
switch(config)# router isis Enterprise
Configuring Virtualization
You can configure multiple IS-IS instances and multiple VRFs and use the same or multiple IS-IS instances in each VRF. You assign an IS-IS interface to a VRF.
You must configure a NET for the configured VRF.

Note![]() Configure all other parameters for an interface after you configure the VRF for an interface. Configuring a VRF for an interface deletes all the configuration for that interface.
Configure all other parameters for an interface after you configure the VRF for an interface. Configuring a VRF for an interface deletes all the configuration for that interface.
BEFORE YOU BEGIN
You must enable IS-IS (see the “Enabling the IS-IS Feature” section).
SUMMARY STEPS
10.![]() { ip | ipv6 } address ip-prefix / length
{ ip | ipv6 } address ip-prefix / length
11.![]() { ip | ipv6 } router isis instance-tag
{ ip | ipv6 } router isis instance-tag
12.![]() (Optional) show isis [ vrf vrf-name ] [ instance-tag ] interface [ interface-type slot/port ]
(Optional) show isis [ vrf vrf-name ] [ instance-tag ] interface [ interface-type slot/port ]
DETAILED STEPS
This example shows how to create a VRF and add an interface to the VRF:
switch(config)# vrf context NewVRF
switch(config)# router isis Enterprise
switch(config-router)# vrf NewVRF
switch(config-router-vrf)# net 47.0004.004d.0001.0001.0c11.1111.00
switch(config-router-vrf)# interface ethernet 1/2
switch(config-if)# vrf member NewVRF
switch(config-if)# ip address 192.0.2.1/16
switch(config-if)# ip router isis Enterprise
switch(config-if)# copy running-config startup-config
Tuning IS-IS
You can tune IS-IS to match your network requirements.
You can use the following optional commands in router configuration mode to tune IS-IS:
You can use the following optional command in router address configuration mode:
You can use the following optional commands in interface configuration mode to tune IS-IS:
Verifying the IS-IS Configuration
To display the IS-IS configuration, perform one of the following tasks:
Monitoring IS-IS
To display IS-IS statistics, use the following commands:
To clear IS-IS configuration statistics, perform one of the following tasks:
Configuration Examples for IS-IS
This example shows how to configure IS-IS:
Related Topics
See the Chapter 15, “Configuring Route Policy Manager” for more information on route maps.
 Feedback
Feedback