Each prefix (rtctrlMatchRtDest) in the match prefixes list can be aggregated to support multiple subnets matching with one
prefix list entry.
Differences in Behavior for 0.0.0.0/0 with Aggregation
The 0.0.0.0/0 with Aggregate configuration creates an IP prefix-list equivalent to “0.0.0.0/0 le 32”. The 0.0.0.0/0 with Aggregate
configuration can be used mainly in two situations:
-
“Export Route Control Subnet” with “Aggregate Export” scope in L3Out subnet under the L3Out network (L3Out EPG)
-
An explicit prefix-list (Match Prefix rule) assigned to a route map with the name “default-export”
When used with the “Export Route Control Subnet” scope under the L3Out subnet, the route map will only match routes learned
from dynamic routing protocols. It will not match BD subnets or directly-connected networks.
When used with the explicit route map configuration, the route map will match all routes, including BD subnets and directly-connected
networks.
Consider the following examples to get a better understanding of the expected and
unexpected (inconsistent) behavior in the two situations described above.
Scenario 1
For the first scenario, we configure a route map (with a name of
rpm_with_catch_all) using a configuration post similar to
the following:
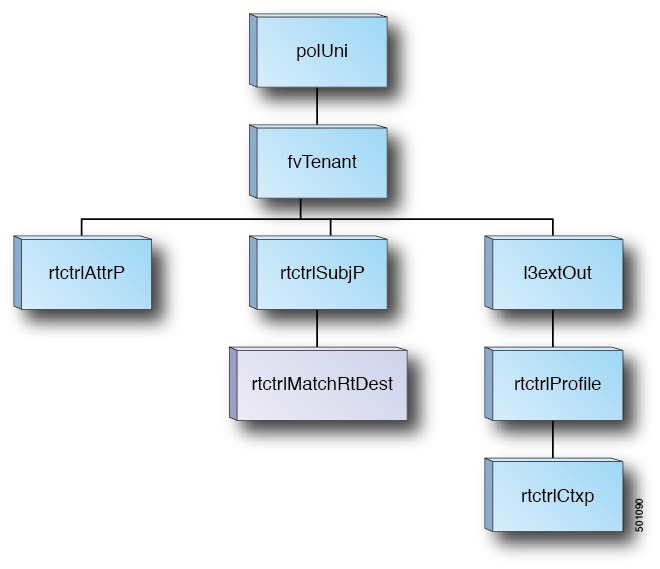
<l3extOut annotation="" descr="" dn="uni/tn-t9/out-L3-out" enforceRtctrl="export" name="L3-out" nameAlias="" ownerKey="" ownerTag="" targetDscp="unspecified">
<rtctrlProfile annotation="" descr="" name="rpm_with_catch_all" nameAlias="" ownerKey="" ownerTag="" type="combinable">
<rtctrlCtxP action="permit" annotation="" descr="" name="catch_all" nameAlias="" order="0">
<rtctrlScope annotation="" descr="" name="" nameAlias="">
<rtctrlRsScopeToAttrP annotation="" tnRtctrlAttrPName="set_metric_type"/>
</rtctrlScope>
</rtctrlCtxP>
</rtctrlProfile>
<ospfExtP annotation="" areaCost="1" areaCtrl="redistribute,summary" areaId="backbone" areaType="regular" descr="" multipodInternal="no" nameAlias=""/>
<l3extRsEctx annotation="" tnFvCtxName="ctx0"/>
<l3extLNodeP annotation="" configIssues="" descr="" name="leaf" nameAlias="" ownerKey="" ownerTag="" tag="yellow-green" targetDscp="unspecified">
<l3extRsNodeL3OutAtt annotation="" configIssues="" rtrId="20.2.0.2" rtrIdLoopBack="no" tDn="topology/pod-1/node-104">
<l3extLoopBackIfP addr="14.1.1.1/32" annotation="" descr="" name="" nameAlias=""/>
<l3extInfraNodeP annotation="" descr="" fabricExtCtrlPeering="no" fabricExtIntersiteCtrlPeering="no" name="" nameAlias="" spineRole=""/>
</l3extRsNodeL3OutAtt>
<l3extLIfP annotation="" descr="" name="interface" nameAlias="" ownerKey="" ownerTag="" tag="yellow-green">
<ospfIfP annotation="" authKeyId="1" authType="none" descr="" name="" nameAlias="">
<ospfRsIfPol annotation="" tnOspfIfPolName=""/>
</ospfIfP>
<l3extRsPathL3OutAtt addr="36.1.1.1/24" annotation="" autostate="disabled" descr="" encap="vlan-3063" encapScope="local" ifInstT="ext-svi" ipv6Dad="enabled" llAddr="::" mac="00:22:BD:F8:19:FF" mode="regular" mtu="inherit" tDn="topology/pod-1/paths-104/pathep-[accBndlGrp_104_pc13]" targetDscp="unspecified"/>
<l3extRsNdIfPol annotation="" tnNdIfPolName=""/>
<l3extRsIngressQosDppPol annotation="" tnQosDppPolName=""/>
<l3extRsEgressQosDppPol annotation="" tnQosDppPolName=""/>
</l3extLIfP>
</l3extLNodeP>
<l3extInstP annotation="" descr="" exceptionTag="" floodOnEncap="disabled" matchT="AtleastOne" name="epg" nameAlias="" prefGrMemb="exclude" prio="unspecified" targetDscp="unspecified">
<l3extRsInstPToProfile annotation="" direction="export" tnRtctrlProfileName="rpm_with_catch_all"/>
<l3extSubnet aggregate="" annotation="" descr="" ip="0.0.0.0/0" name="" nameAlias="" scope="import-security"/>
<fvRsCustQosPol annotation="" tnQosCustomPolName=""/>
</l3extInstP>
</l3extOut>
<rtctrlAttrP annotation="" descr="" dn="uni/tn-t9/attr-set_metric_type" name="set_metric_type" nameAlias="">
<rtctrlSetRtMetricType annotation="" descr="" metricType="ospf-type1" name="" nameAlias="" type="metric-type"/>
</rtctrlAttrP>
<rtctrlSubjP annotation="" descr="" dn="uni/tn-t9/subj-catch_all_ip" name="catch_all_ip" nameAlias="">
<rtctrlMatchRtDest aggregate="yes" annotation="" descr="" ip="0.0.0.0/0" name="" nameAlias=""/>
</rtctrlSubjP>
With this route map, what we would expect with 0.0.0.0/0 is that all the routes would
go with the property metricType="ospf-type1", but only for the OSPF
route.
In addition, we also have a subnet configured under a bridge domain (for example,
209.165.201.0/27), with a bridge domain to L3Out relation, using a route map with a
pervasive subnet (fvSubnet) for a static route. However, even though the route map
shown above is combinable, we do not want it applied for the subnet configured under
the bridge domain, because we want 0.0.0.0/0 in the route map above to apply only
for the transit route, not on the static route.
Following is the output for the show route-map and show ip
prefix-list commands, where exp-ctx-st-2555939 is
the name of the outbound route map for the subnet configured under the bridge
domain, and the name of the prefix list is provided within the output from the
show route-map command:
leaf4# show route-map exp-ctx-st-2555939
route-map exp-ctx-st-2555939, deny, sequence 1
Match clauses:
tag: 4294967295
Set clauses:
route-map exp-ctx-st-2555939, permit, sequence 15801
Match clauses:
ip address prefix-lists: IPv4-st16391-2555939-exc-int-inferred-export-dst
ipv6 address prefix-lists: IPv6-deny-all
Set clauses:
leaf4# show ip prefix-list IPv4-st16391-2555939-exc-int-inferred-export-dst
ip prefix-list IPv4-st16391-2555939-exc-int-inferred-export-dst: 1 entries
seq 1 permit 209.165.201.0/27
leaf4#
In this situation, everything behaves as expected, because when the bridge domain
subnet goes out, it is not applying the rpm_with_catch_all
route map policies.
Scenario 2
For the second scenario, we configure a "default-export" route map for export route
control, where an explicit prefix-list (Match Prefix rule) is assigned to the
"default-export" route map, using a configuration post similar to the following:
<l3extOut annotation="" descr="" dn="uni/tn-t9/out-L3-out" enforceRtctrl="export" name="L3-out" nameAlias="" ownerKey="" ownerTag="" targetDscp="unspecified">
<rtctrlProfile annotation="" descr="" name="default-export" nameAlias="" ownerKey="" ownerTag="" type="combinable">
<rtctrlCtxP action="permit" annotation="" descr="" name="set-rule" nameAlias="" order="0">
<rtctrlScope annotation="" descr="" name="" nameAlias="">
<rtctrlRsScopeToAttrP annotation="" tnRtctrlAttrPName="set_metric_type"/>
</rtctrlScope>
</rtctrlCtxP>
</rtctrlProfile>
<ospfExtP annotation="" areaCost="1" areaCtrl="redistribute,summary" areaId="backbone" areaType="regular" descr="" multipodInternal="no" nameAlias=""/>
<l3extRsEctx annotation="" tnFvCtxName="ctx0"/>
<l3extLNodeP annotation="" configIssues="" descr="" name="leaf" nameAlias="" ownerKey="" ownerTag="" tag="yellow-green" targetDscp="unspecified">
<l3extRsNodeL3OutAtt annotation="" configIssues="" rtrId="20.2.0.2" rtrIdLoopBack="no" tDn="topology/pod-1/node-104">
<l3extLoopBackIfP addr="14.1.1.1/32" annotation="" descr="" name="" nameAlias=""/>
<l3extInfraNodeP annotation="" descr="" fabricExtCtrlPeering="no" fabricExtIntersiteCtrlPeering="no" name="" nameAlias="" spineRole=""/>
</l3extRsNodeL3OutAtt>
<l3extLIfP annotation="" descr="" name="interface" nameAlias="" ownerKey="" ownerTag="" tag="yellow-green">
<ospfIfP annotation="" authKeyId="1" authType="none" descr="" name="" nameAlias="">
<ospfRsIfPol annotation="" tnOspfIfPolName=""/>
</ospfIfP>
<l3extRsPathL3OutAtt addr="36.1.1.1/24" annotation="" autostate="disabled" descr="" encap="vlan-3063" encapScope="local" ifInstT="ext-svi" ipv6Dad="enabled" llAddr="::" mac="00:22:BD:F8:19:FF" mode="regular" mtu="inherit" tDn="topology/pod-1/paths-104/pathep-[accBndlGrp_104_pc13]" targetDscp="unspecified"/>
<l3extRsNdIfPol annotation="" tnNdIfPolName=""/>
<l3extRsIngressQosDppPol annotation="" tnQosDppPolName=""/>
<l3extRsEgressQosDppPol annotation="" tnQosDppPolName=""/>
</l3extLIfP>
</l3extLNodeP>
<l3extInstP annotation="" descr="" exceptionTag="" floodOnEncap="disabled" matchT="AtleastOne" name="epg" nameAlias="" prefGrMemb="exclude" prio="unspecified" targetDscp="unspecified">
<l3extSubnet aggregate="" annotation="" descr="" ip="0.0.0.0/0" name="" nameAlias="" scope="import-security"/>
<fvRsCustQosPol annotation="" tnQosCustomPolName=""/>
</l3extInstP>
</l3extOut>
Notice that this default-export route map has similar
information as the rpm_with_catch_all route map, where the IP
is set to 0.0.0.0/0 (ip=0.0.0.0/0), and the set rule in the
default-export route map is configured only with the Set
Metric Type (tnRtctrlAttrPName=set_metric_type).
Similar to the situation in the previous example, we also have the same subnet
configured under the bridge domain, with a bridge domain to L3Out relation, as we
did in the previous example.
However, following is the output in this scenario for the show
route-map and show ip prefix-list commands:
leaf4# show route-map exp-ctx-st-2555939
route-map exp-ctx-st-2555939, deny, sequence 1
Match clauses:
tag: 4294967295
Set clauses:
route-map exp-ctx-st-2555939, permit, sequence 8201
Match clauses:
ip address prefix-lists: IPv4-st16391-2555939-exc-int-out-default-export2set-rule0pfx-only-dst
ipv6 address prefix-lists: IPv6-deny-all
Set clauses:
metric-type type-1
leaf4# show ip prefix-list IPv4-st16391-2555939-exc-int-inferred-export-dst
% Policy IPv4-st16391-2555939-exc-int-inferred-export-dst not found
ifav82-leaf4# show ip prefix-list IPv4-st16391-2555939-exc-int-out-default-export2set-rule0pfx-only-dst
ip prefix-list IPv4-st16391-2555939-exc-int-out-default-export2set-rule0pfx-only-dst: 1 entries
seq 1 permit 209.165.201.0/27
leaf4#
Notice that in this situation, when the bridge domain subnet goes out, it is applying
the default-export route map policies. In this situation, that
route map matches all routes, including BD subnets and directly-connected networks.
This is inconsistent behavior.

 Feedback
Feedback