View the Vulnerability Dashboard
To view the Vulnerability Dashboard, in the left navigation pane, click .
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
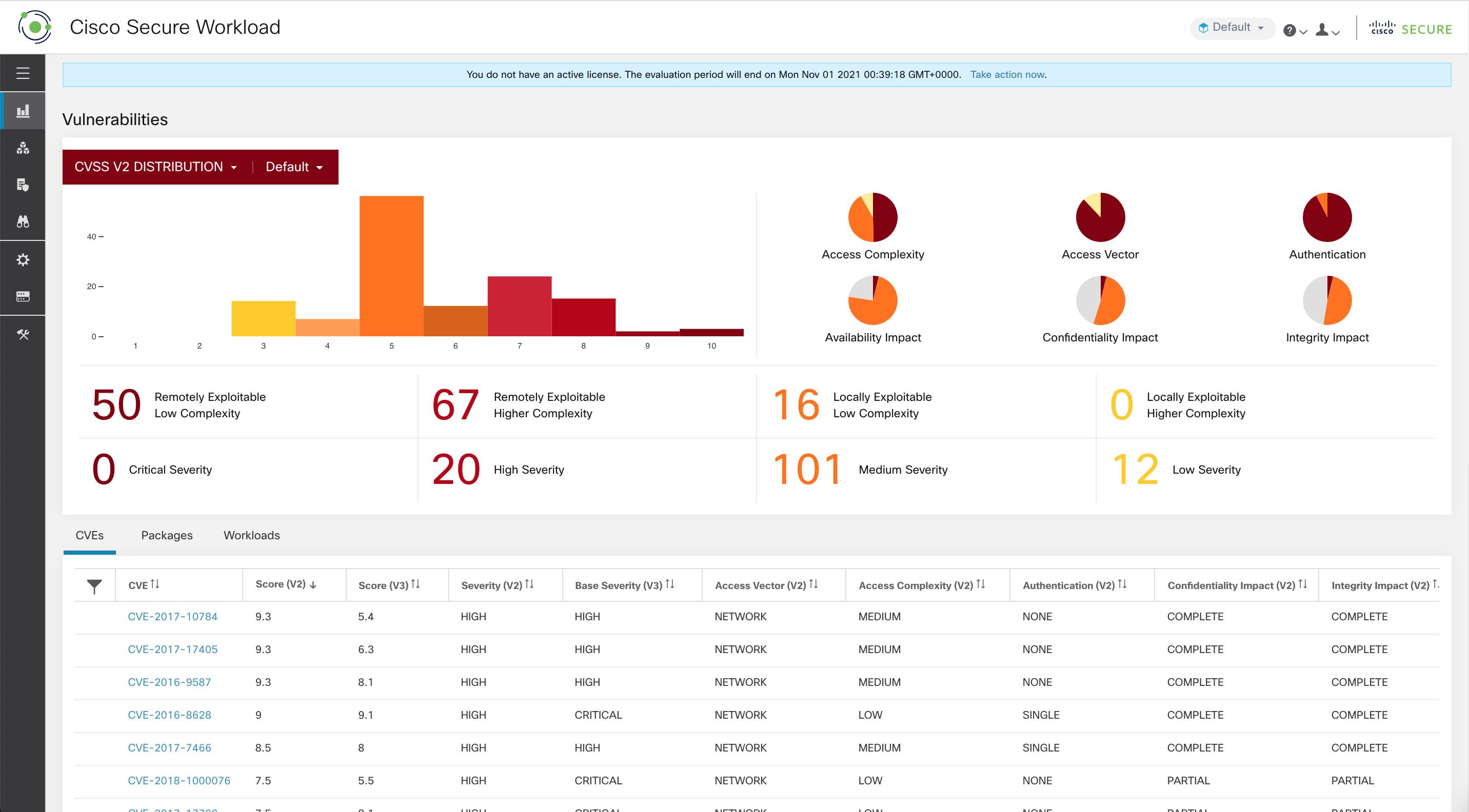
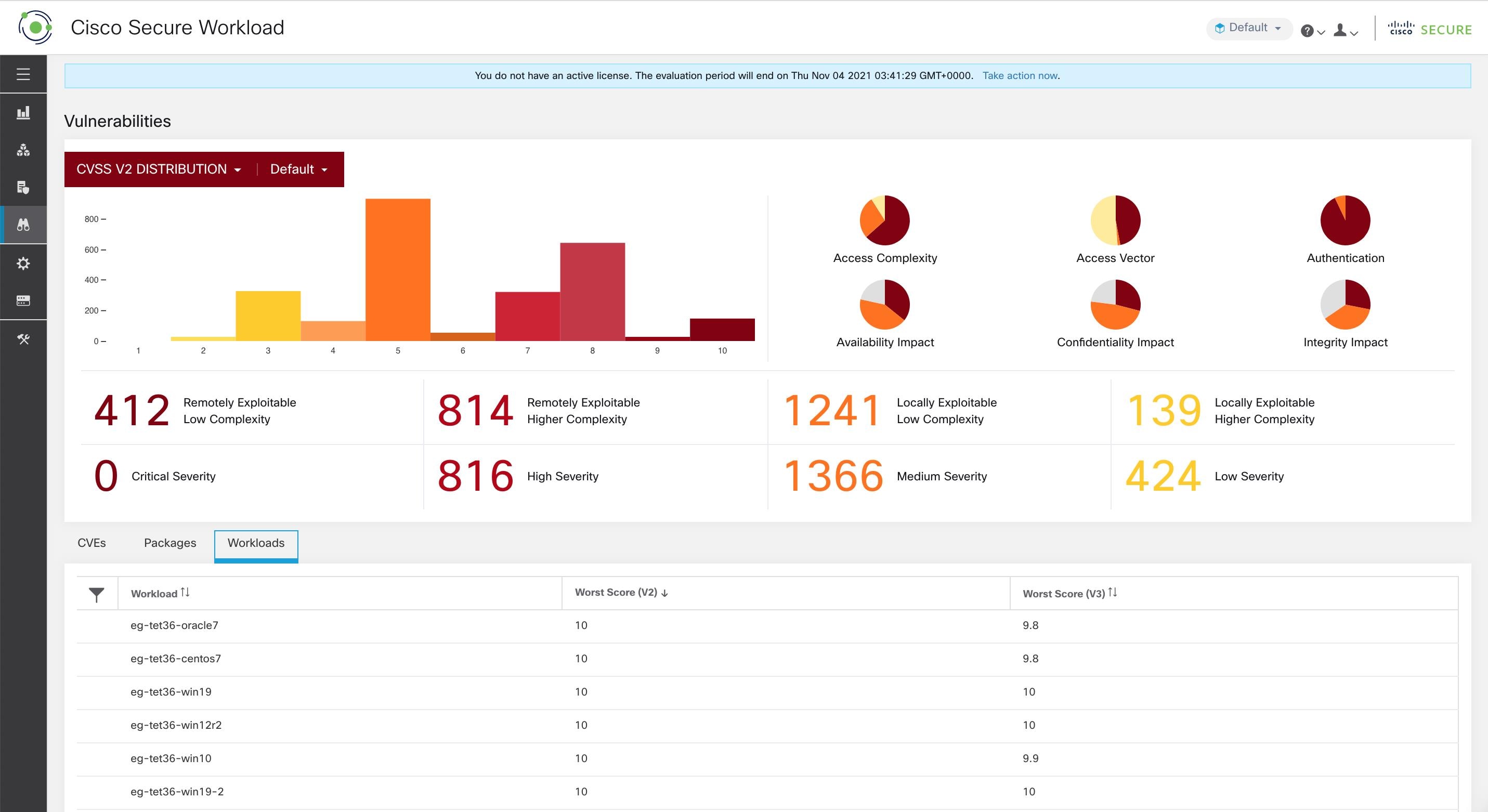
Vulnerability Dashboard enables end users to focus their effort on critical vulnerabilities and workloads that need most attention. You can select relevant scope at the top of this page and select the scoring system for vulnerabilities they want to view (Common Vulnerability Scoring System v2 or v3). The new page highlights the distribution of vulnerabilities in the chosen scope and displays vulnerabilities by different attributes, for example, complexity of exploits, can the vulnerabilities be exploited over the network or does attacker need local access to the workload. Furthermore, there are statistics to quickly filter out vulnerabilities that are remotely exploitable and have lowest complexity to exploit.
There are three tabs that are available on this page – all of them adjust/filter based on user’s clicks on the widgets at the top of the page:
CVEs tab highlights the vulnerabilities to focus on in the chosen scope.
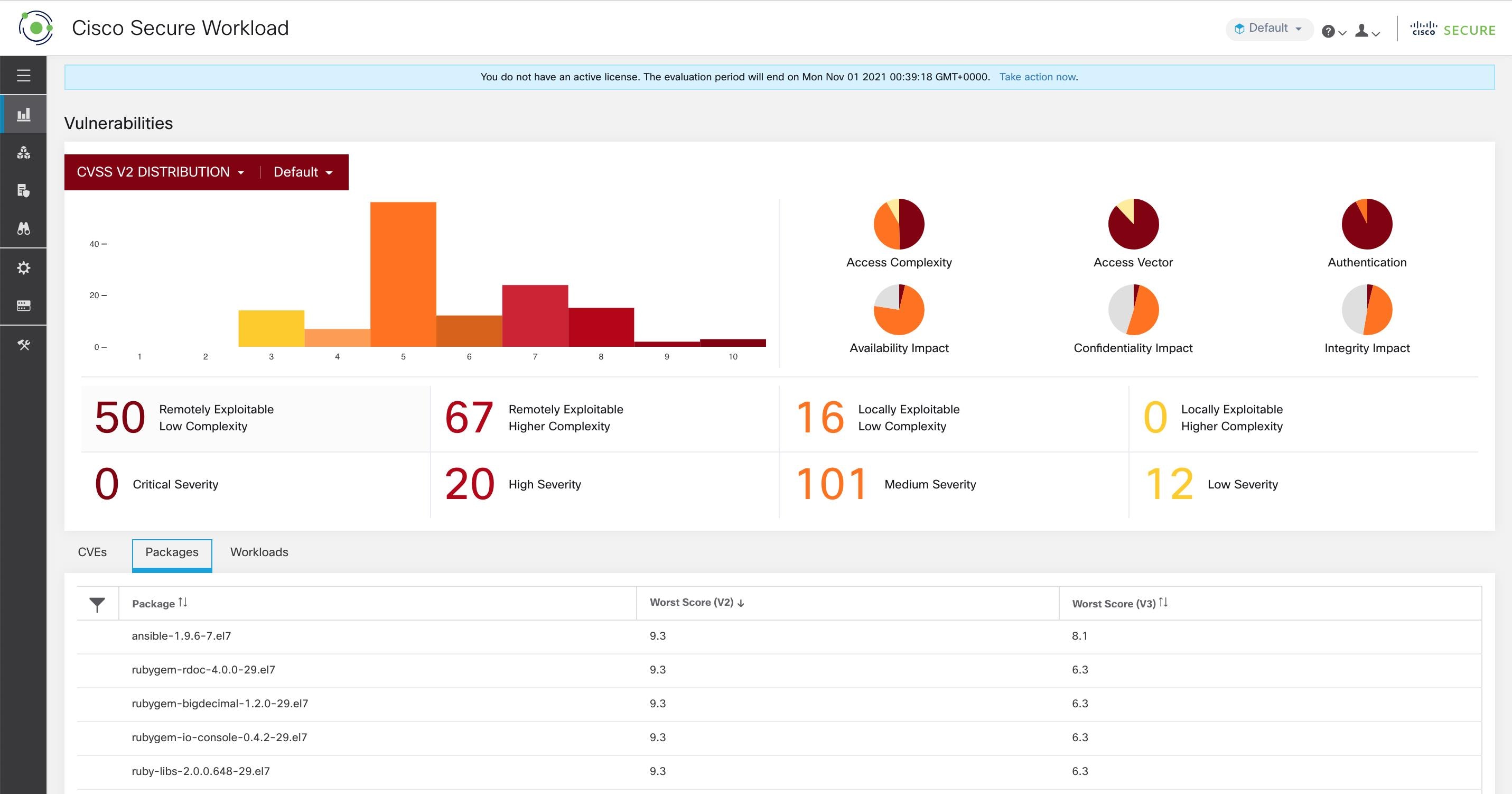
Packages tab shows the end users the packages that must be patched.
Workloads tab lists the workloads that need most attention in terms of patching in the chosen scope.
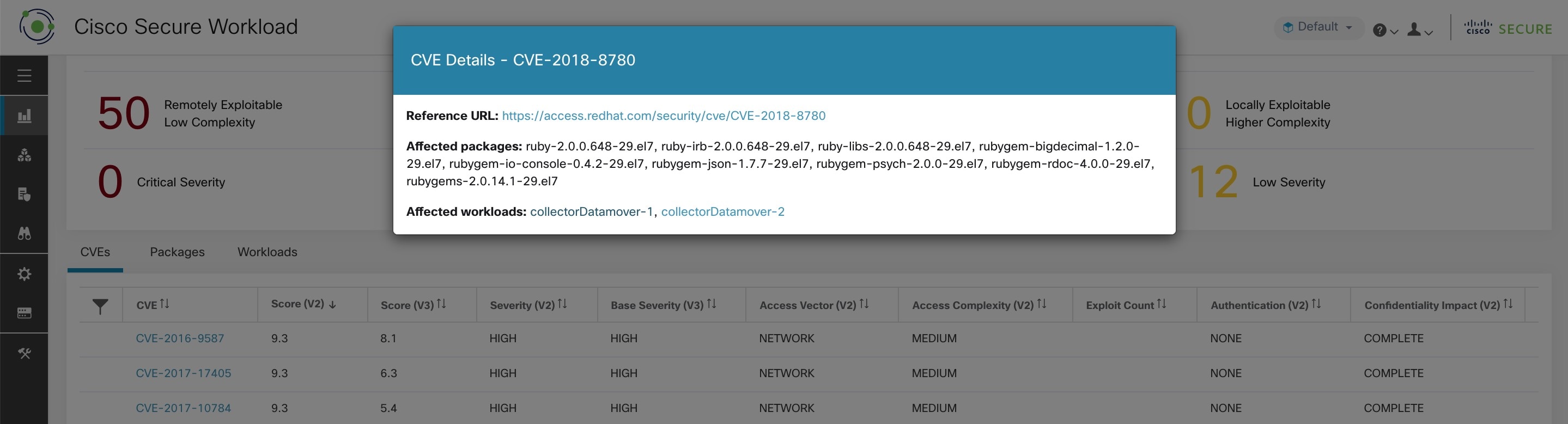
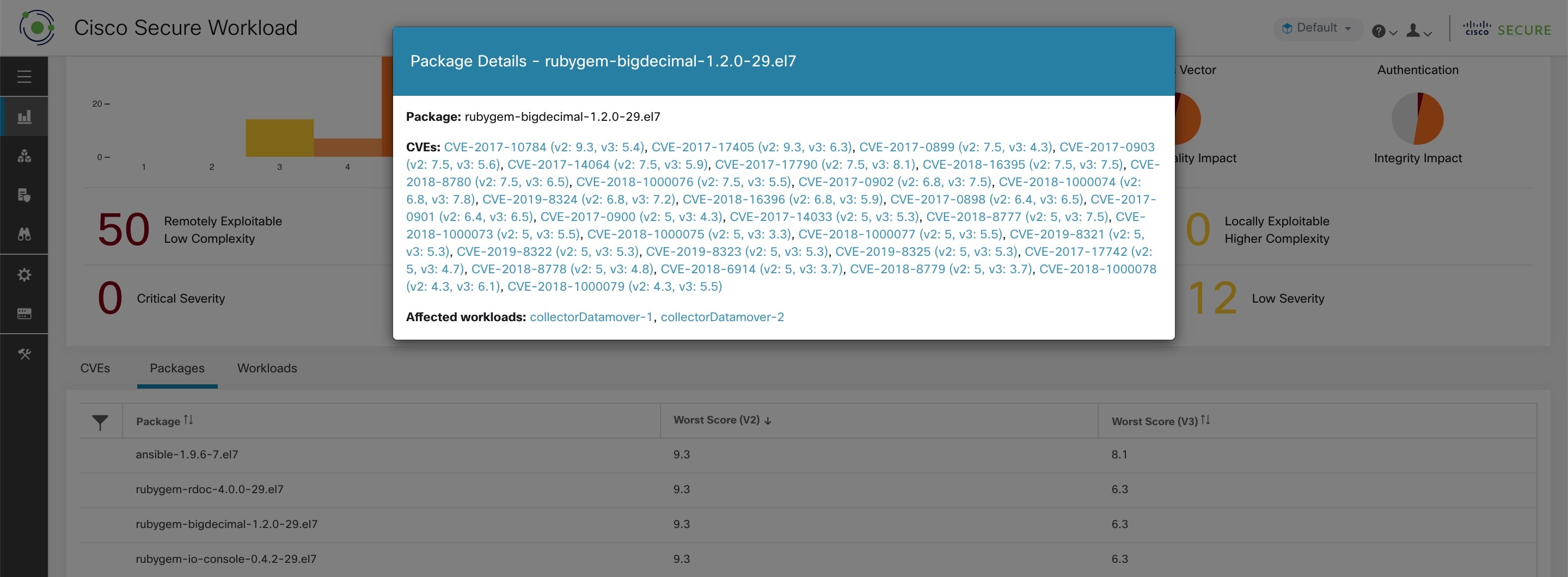
Clicking on any row in the above tabs display more information about that row, for example, clicking on package row in the packages tab show which workloads that package/version is installed on and the associated vulnerabilities for that package. Similarly, clicking on the row in workloads tab shows packages that are installed on the chosen workload along with the associated vulnerabilities.
This page is intended to help the users identify workloads to focus on first and which packages to patch first.
To view the Vulnerability Dashboard, in the left navigation pane, click .
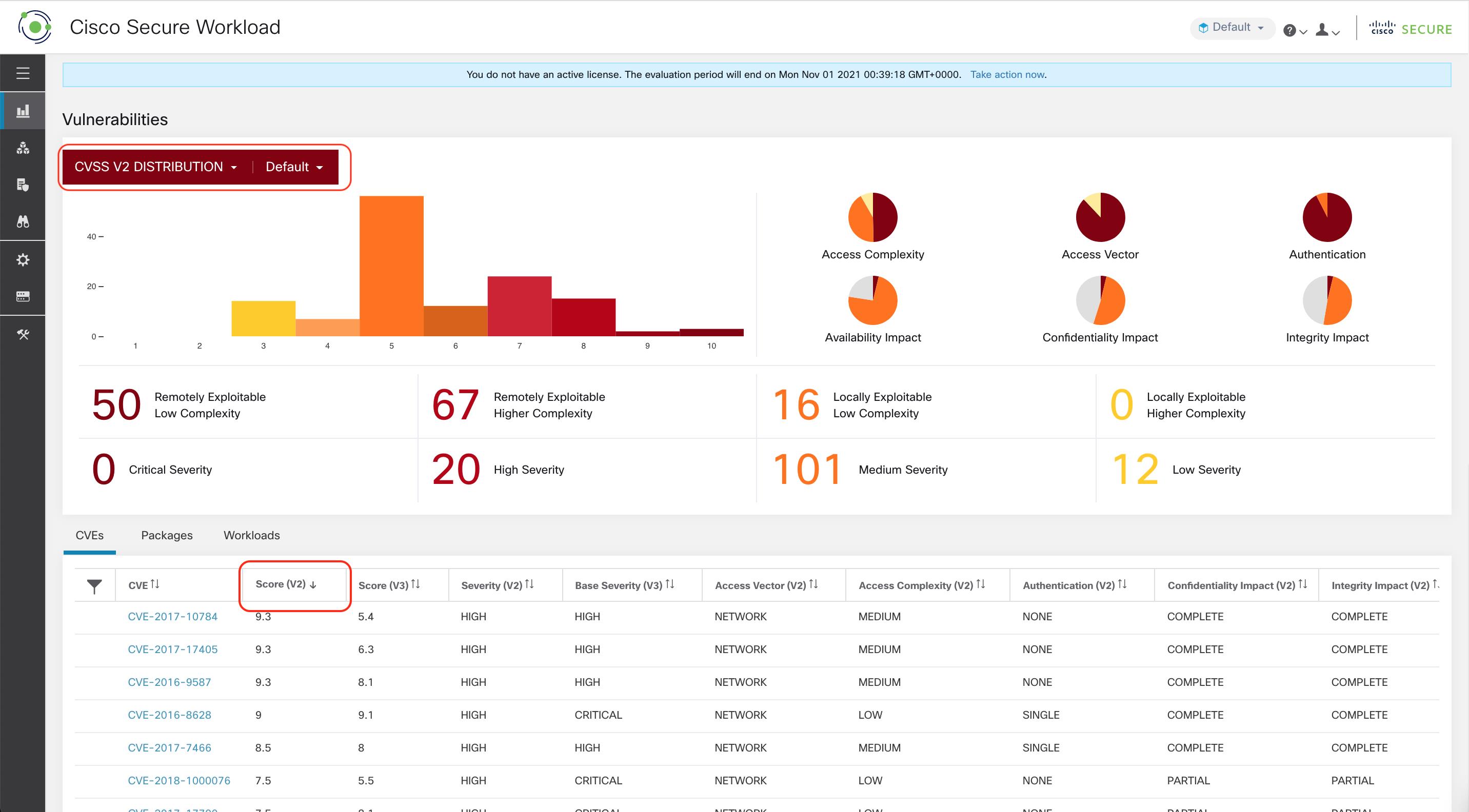
Based on the scope that is selected at the top of the page and the scoring system (v2 or v3), CVE tab highlights the vulnerabilities (sorted by the scores) on workloads in the selected scopes that need attention.
For each CVE, besides basic impact metrics, exploit information based on our threat intelligence is displayed:
Exploit Count: number of times CVE was seen exploited in the wild in the last year.
Last Exploited: last time CVE was seen exploited in the wild by our threat intelligence.
Clicking on any row in the CVEs table gives more details about that vulnerability and which workloads that it affects.
Packages tab lists the software packages that users must pay attention to and potentially upgrade to reduce their attack surface.
Clicking on any row in the packages table gives more details about which workloads that package is installed as well as the known CVEs for that package.
Workloads tab lists the workloads that need attention in terms of software updates or patches.
Clicking on any row in the workloads table provides the list of packages with vulnerabilities on that workload.
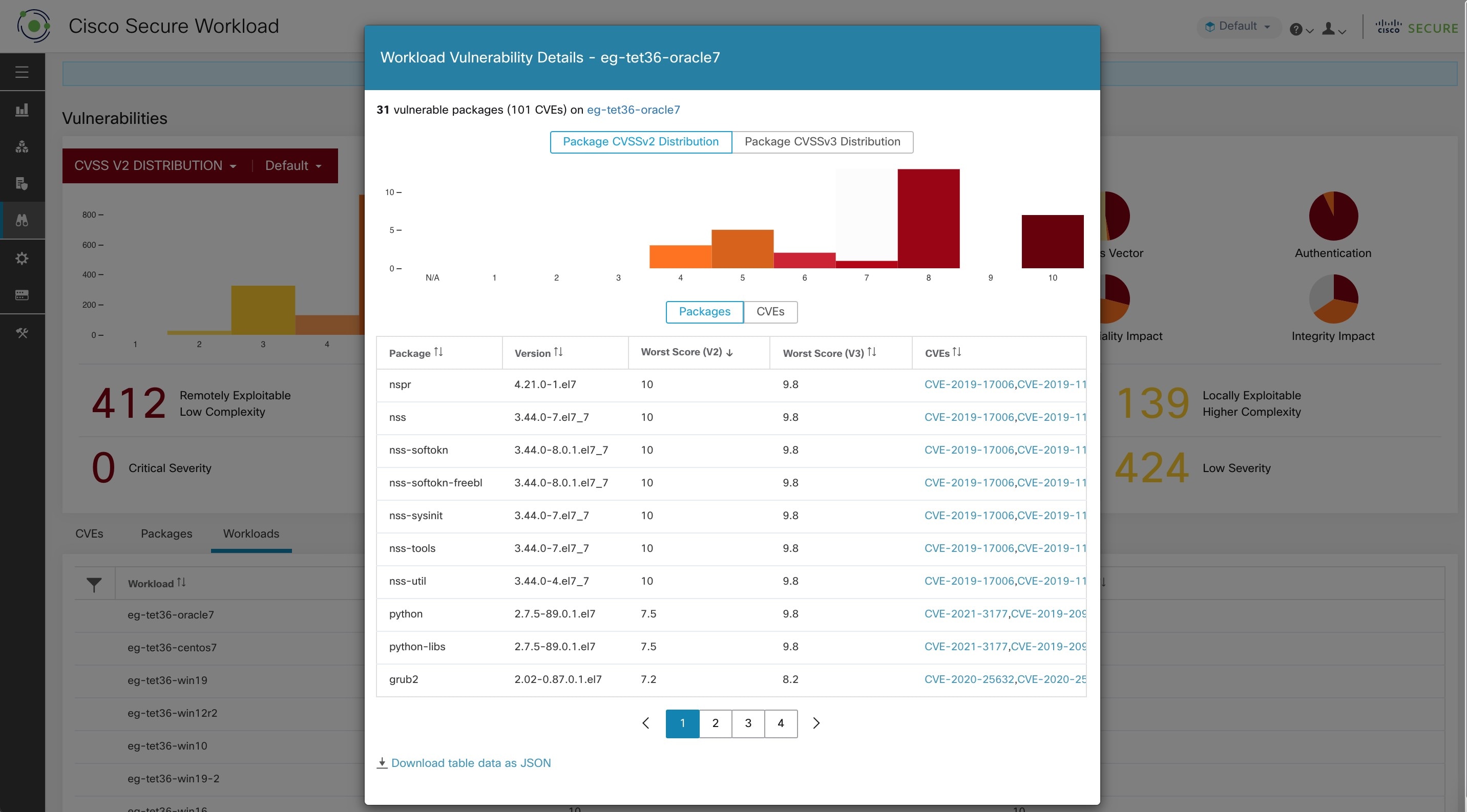
All of the above tables are downloadable using the Download links at the bottom of the tables.