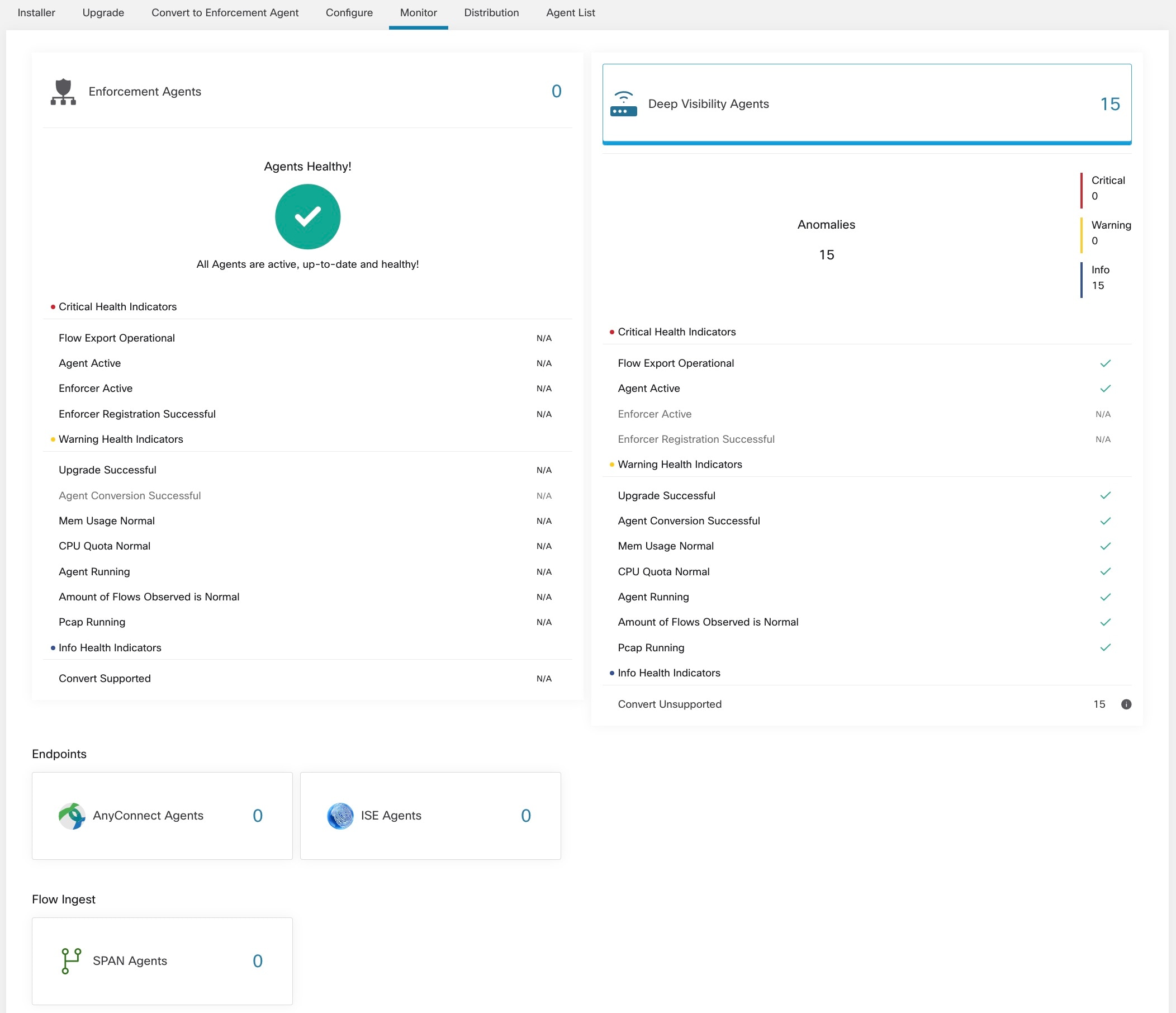
Agent Monitoring
The page displays the count of all monitored agents in a cluster based on the currently selected root scope.
 Note |
Total Inventory count is the summation of all inventory observed on the network after applying collection rules. |
Agent Monitoring Type
To monitor agents, click in the left navigation bar, then click the Monitor tab.
This page is only available for users that have Site Admin and Customer Support roles. Scope owners can see Inventory, Deep Visibility Agents, and Enforcement Agents.
The following table shows the differences between each agent type.
|
Agent Type |
Description |
|
Deep Visibility |
Provides highest fidelity in terms of time series flow data, processes running on a host. Most Linux and Windows platforms are supported. See sw_agents_deployment-label |
|
Enforcement |
Provides all capabilities available in Deep Visibility Agents. In addition, Enforcement agents are capable of setting firewall rules on the installed host. |
|
AnyConnect |
Provides time series flow data on endpoints running AnyConnect Secure Mobility Agent with Network Visibility Module (NVM) without requiring any Cisco Secure Workload agent installation. IPFIX records generated by NVM are sent to Secure Workload AnyConnect Proxy connector. Windows, Mac, and certain smartphone platforms are supported. |
|
ISE |
Provides metadata about endpoints registered with Cisco ISE. Through ISE pxGrid, ISE connector collects the metadata, registers the ISE endpoints on Secure Workload as ISE agents pushes labels based on the attributes fetched from ISE appliance and LDAP attributes for the users logged in to the endpoints. |
|
The following table provides a brief summary of various appliance agents provided by Cisco Secure Workload. |
|
|
Appliance Agents |
Description |
|
SPAN |
Provides the flow analysis without requiring any per-host agent installation. It runs in the Secure Workload ERSPAN VM appliance. It consumes ERSPAN packets sourced by any Cisco switch. |
 Note |
Appliance agents such as NetFlow, NetScaler, F5, AWS, and AnyConnect Proxy are now supported as connectors. For more information on connectors, see What are Connectors. |
Any non-zero agent type button allows further drill-down into the distribution of each agent type.
Agent Status and Statistics
To view the charts described in this topic, choose Manage > Agents, then click the Distribution tab.
The following charts are available for both Deep Visibility and Enforcement Agent types.
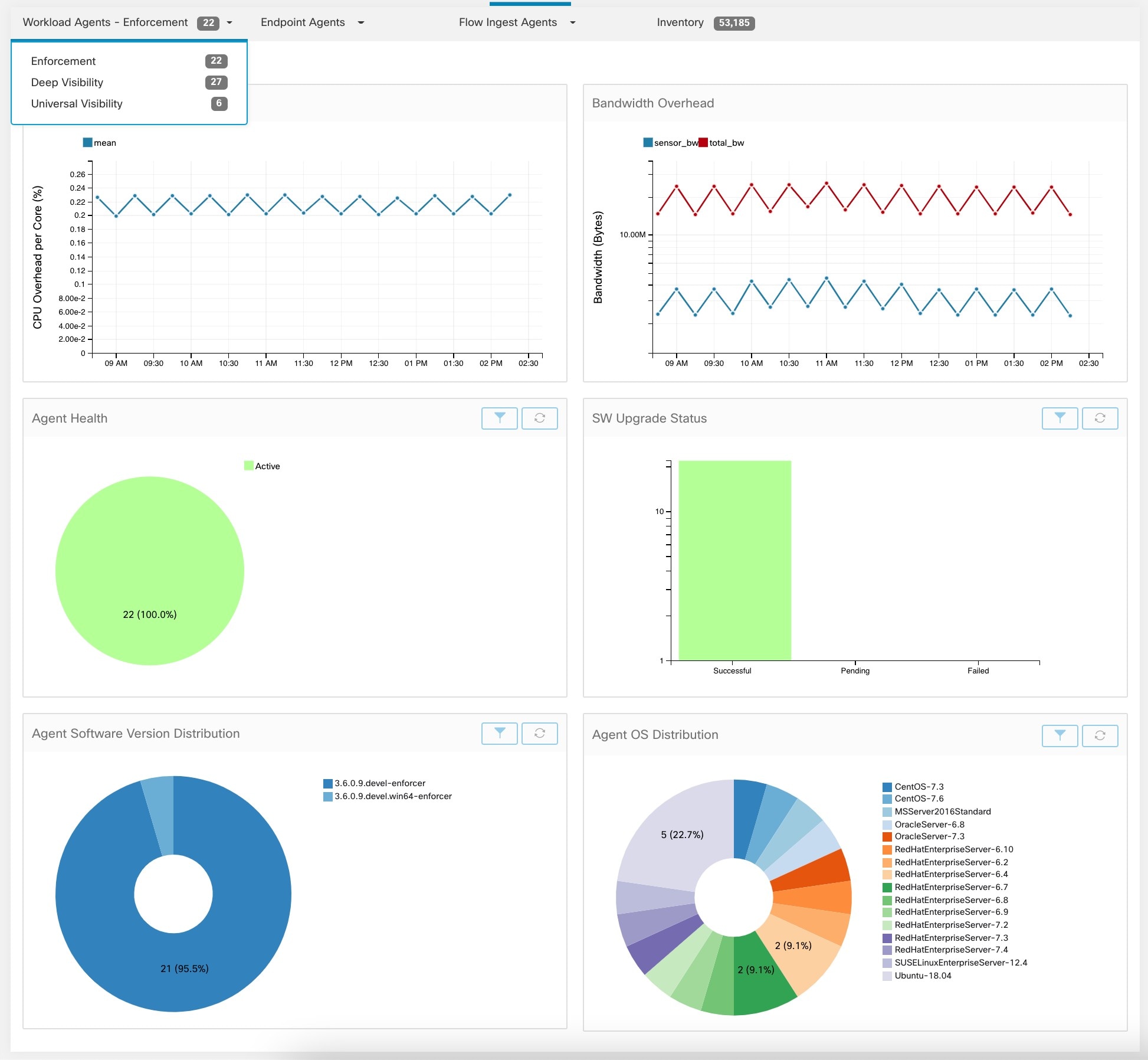
For each agent type, this page provides an overview and the health of registered agents including overall CPU overhead, bandwidth overhead, missed packets, OS/version distribution and agent upgrade status.
CPU Overhead Chart
The CPU Overhead chart provides an aggregated view of CPU overhead per core from all agents. Per-agent CPU Overhead is provided as part of the Workload Profile. This chart is only available for Deep Visibility and Enforcement Agent Types.
Bandwidth Overhead Chart
The Bandwidth Overhead chart provides aggregated stats of total bandwidth and bandwidth used by agents. Per-agent bandwidth overhead is provided as part of the Workload Profile. This chart is only available for Deep Visibility and Enforcement Agent Types.
Agent Health Chart
The Agent Health chart provides the number of active/inactive agents. Active agents are the one schecking in with config server for upgrade on regular intervals. The checking interval is 30 minutes. If we see that an agent has missed more than two check-in periods from a agent, it would be declared as inactive agent.
Software Agent Updates to Latest Revision Chart
Every time an agent checks in with the config server, the agent would also provide its current RPM version. If an agent is configured to a specific version and is not able to update after 2 check-in periods, the agent would be declared as not able to upgrade to the latest version.
Agent Packet Missed Chart
In rare occasions when the traffic volume traversing a host is greater than the rate at which the agent is able to inspect, some packets are skipped from being analyzed. The number of missed packets and the corresponding agent name are displayed in this chart.
Agent Software Version/OS Distribution Charts
These charts show the agent version distribution and parent OS platform of all agents registered with the Secure Workload cluster.





 Feedback
Feedback