Posture Types
The following posture agents monitor and enforce Cisco ISE posture policies:
-
AnyConnect: Deploys the AnyConnect agent to monitor and enforce Cisco ISE posture policies that require interaction with the client. The AnyConnect agent stays on the client. For more information about using AnyConnect in Cisco ISE, see Cisco AnyConnect Secure Mobility.
-
AnyConnect Stealth: Runs posture as a service, with no user interface. The agent stays on the client.
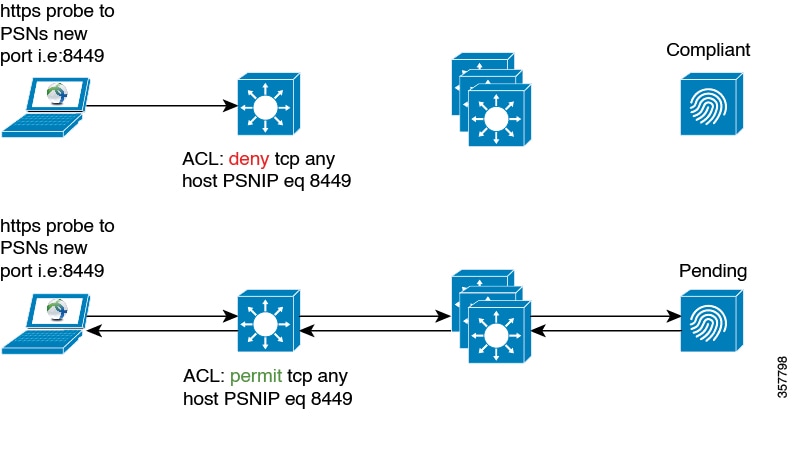
When you choose the AnyConnect Stealth posture type in the posture requirement, some of the conditions, remediations, or attributes in a condition are disabled (grayed out). For example, when you enable AnyConnect Stealth requirement, the Manual Remediation Type is disabled (grayed out) because this action requires client-side interaction.
When you map the posture profile to the AnyConnect configuration, and then map the AnyConnect configuration to the Client Provisioning window for AnyConnect Stealth mode deployment:
-
AnyConnect can read the posture profile and set it to the intended mode.
-
AnyConnect can send information related to the selected mode to Cisco ISE during the initial posture request.
-
Cisco ISE can match the right policy, based on the mode and other factors, such as identity group, OS, and compliance module.

Note
AnyConnect Stealth mode requires AnyConnect version 4.4 and later.
For more information about configuring AnyConnect Stealth in Cisco ISE, see Configure AnyConnect Stealth Mode Workflow.
-
-
Temporal Agent: When a client attempts to access the trusted network, Cisco ISE opens the Client Provisioning portal. The portal instructs the user to download and install the agent, and run the agent. The temporal agent checks the compliance status, and sends the status to Cisco ISE. Cisco ISE acts based on the results. The temporal agent removes itself from the client after compliance processing completes. The temporal agent does not support custom remediation. The default remediation supports only message text.
The Temporal Agent does not support the following conditions:
-
Service Condition MAC—System Daemon check
-
Service Condition-MAC—Daemon or User Agent check
-
PM—Up To Date check
-
PM—Enabled check
-
DE—Encryption check
-
Configure posture policies using the Posture Types Temporal Agent and Compliance Module 4.x or later. Do not configure the compliance module as 3.x or earlier or Any Version.
-
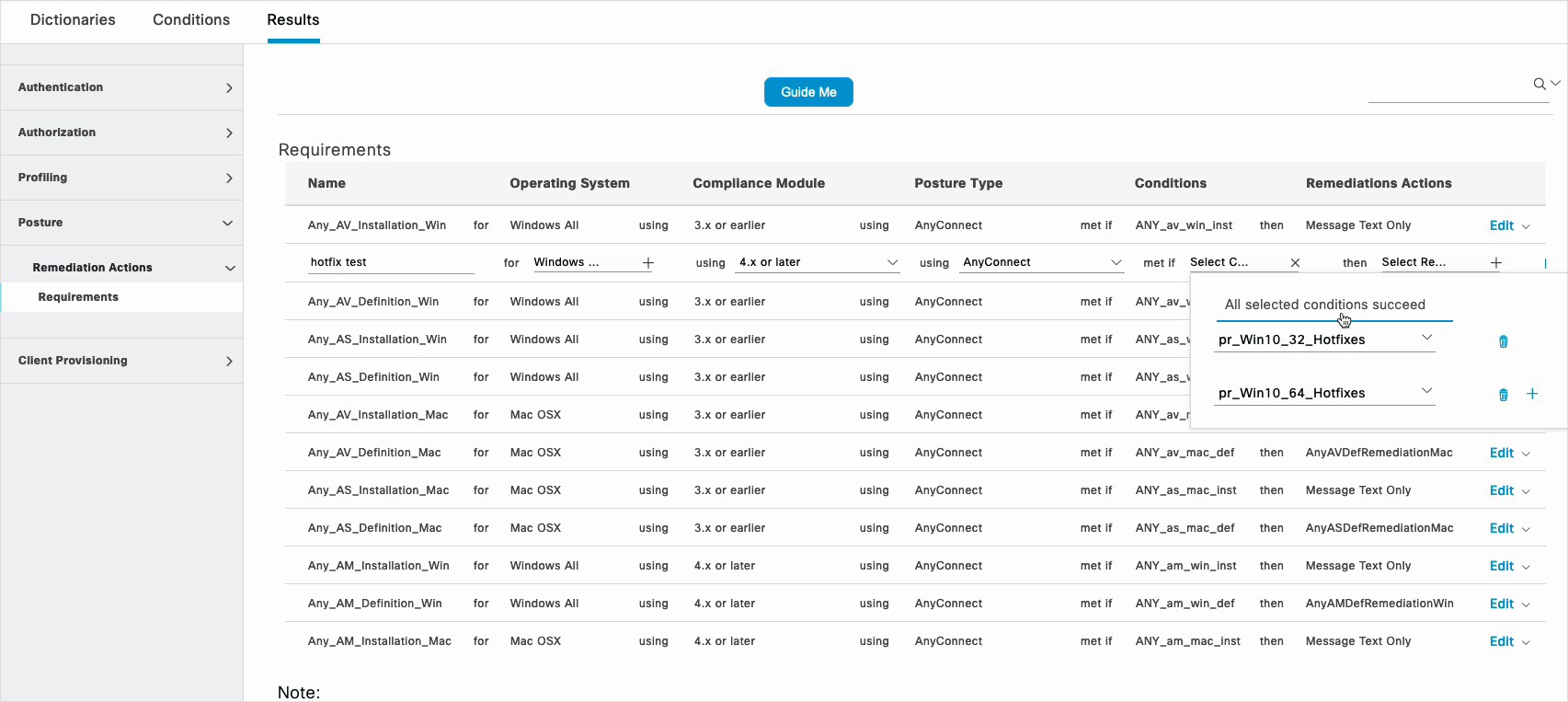
For the Temporal Agent, you can only view Patch Management conditions containing the Installation check type in the Requirements window.
-
Cisco ISE does not support VLAN-controlled posture with the Temporal Agent for macOS because macOS cannot detect VLAN changes. When you change the network access from an existing VLAN to a new VLAN, the user’s IP address is released before the VLAN change. The client gets a new IP address by DHCP when the user connects to the new VLAN. Recognizing the new IP address requires root privileges, but the Temporal Agent runs as a user process.
-
For the other operating systems, the Temporal Agent does not renew the IP address. The operating system should renew the IP address.
-
Cisco ISE supports ACL-controlled posture environment, which does not require the refreshing of endpoint IP addresses.
-
For more information about configuring the Temporal agent in Cisco ISE, see Configure Cisco Temporal Agent Workflow.
-
-
AMP Enabler—The AMP Enabler pushes the AMP for Endpoints software to a subset of endpoints from a server hosted locally within the enterprise, and installs AMP services to its existing user base.
-
Agentless Posture—Agentless posture provides posture information from clients, and completely removes itself when finished. No action is required from the end user. Unlike the Temporal agent, Agentless Posture connects to the client as an administrative user. For more information about using Agentless Posture in Cisco ISE, see Agentless Posture.
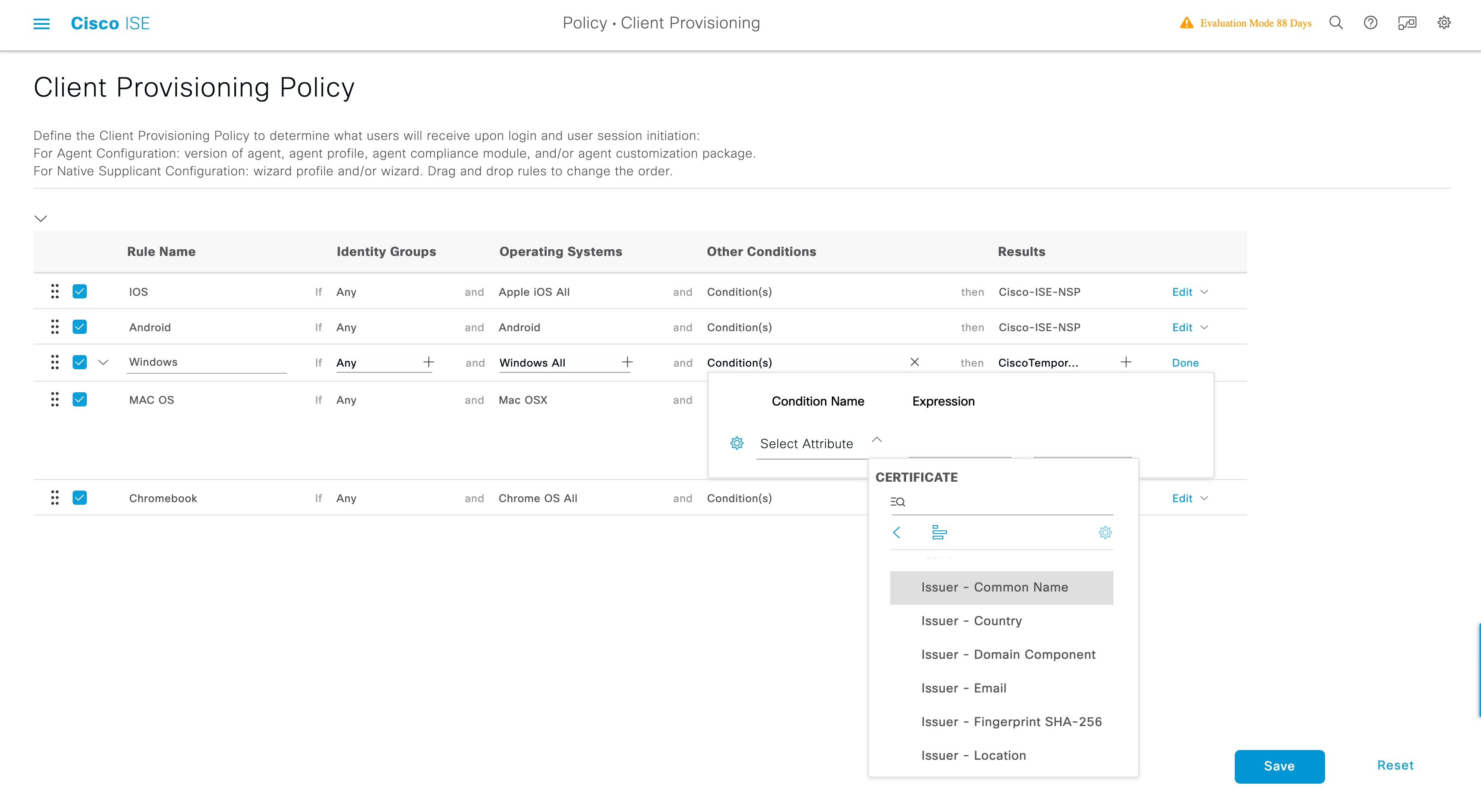
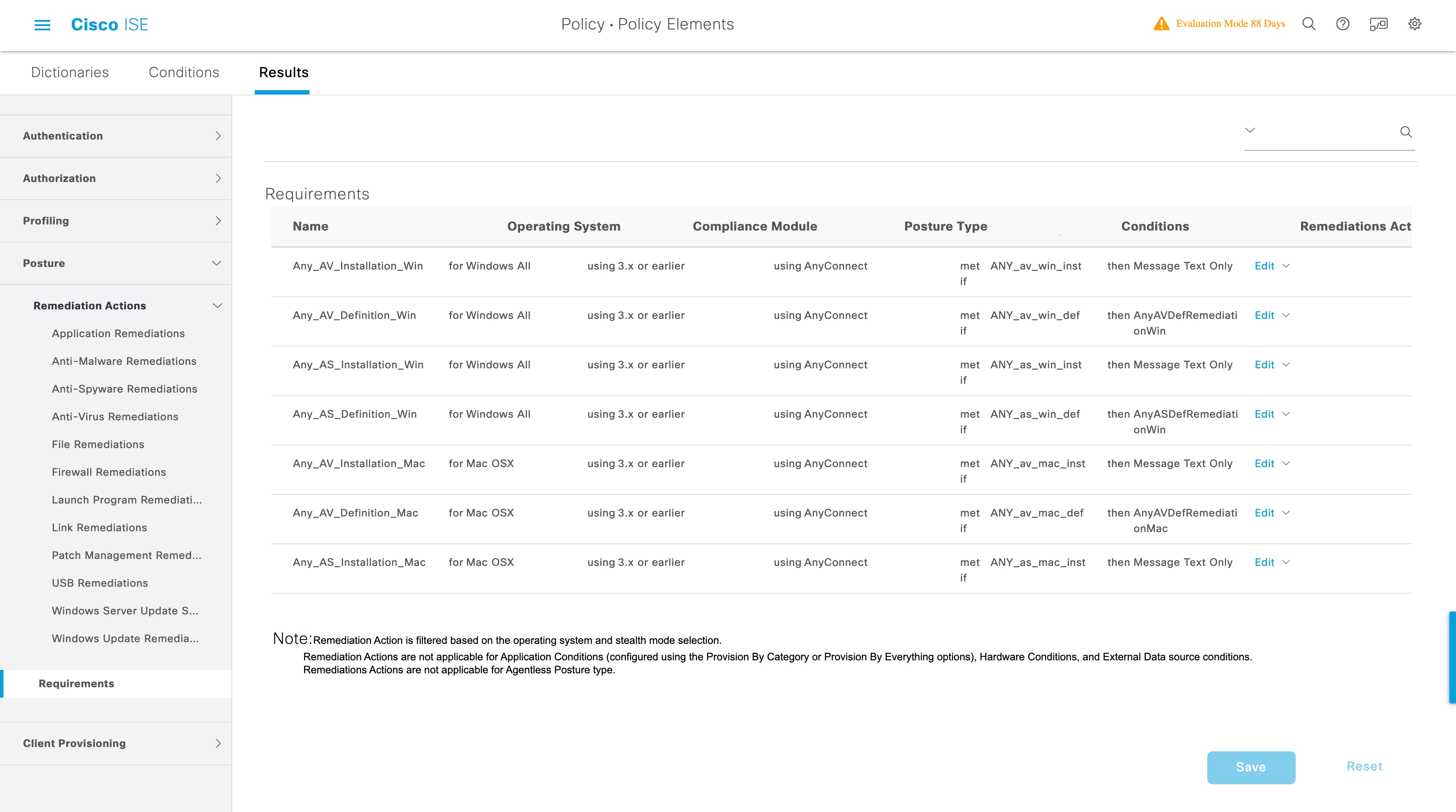
You can select the posture type in the Client Provisioning window (Policy > Policy Elements > Results > Client Provisioning > Resources) and the Posture Requirements window (Policy > Policy Elements > Results > Posture > Requirements). The best practice is to provision the posture profile in the Client Provisioning window.
 Feedback
Feedback