|
Audit
|
|
Adaptive Network Control Audit
|
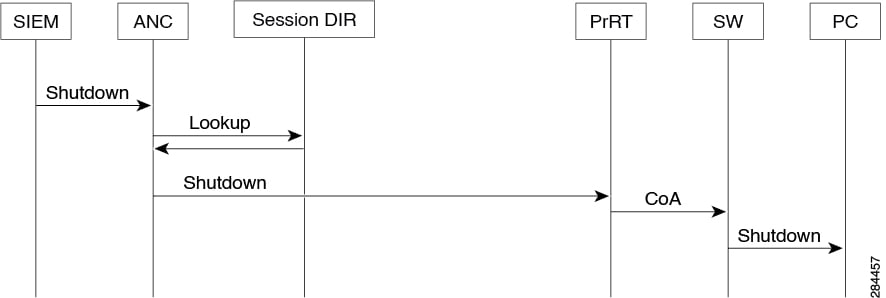
The Adaptive Network Control Audit report is
based on RADIUS accounting. It displays historical reporting of
all the network sessions for each endpoint.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and click Passed
Authentications and RADIUS
Accounting. ) and choose
, and click Passed
Authentications and RADIUS
Accounting.
|
|
Administrator Logins
|
The Administrator Logins report provides information about all the GUI-based
administrator login events as well as successful CLI login
events.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and click Administrative and
Operational Audit. ) and choose
, and click Administrative and
Operational Audit.
|
|
Change Configuration Audit
|
The Change Configuration Audit report provides details about configuration changes within a specified time period. If you
need to troubleshoot a feature, this report can help you determine if a recent configuration change contributed to the problem.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and click Administrative and
Operational Audit. ) and choose
and click Administrative and
Operational Audit.
|
|
Data Purging Audit
|
The Data Purging Audit report records when the logging data is purged.
This report reflects two sources of data purging.
At 4 a.m. daily, Cisco ISE checks whether
there are any logging files that meet the criteria you have set
on the Administration > Maintenance > Data
Purging window. If yes, the files are deleted
and recorded in this report. Additionally, Cisco ISE continually
maintains a maximum of 80 percent used storage space (threshold)
for the log files. Every hour, Cisco ISE verifies this
percentage and deletes the oldest data until this threshold is
reached again. This information is also recorded in this report.
If there is high disk space utilization, an alert message stating
ISE Monitor node(s) is about to exceed the
maximum amount allocated is displayed at 80
percent of the threshold, that is 60 percent of total disk
space. Subsequently, an alert message stating ISE
Monitor node(s) has exceeded the maximum amount
allocated is displayed at 90 percent of the
threshold, that is 70 percent of the total disk space.
|
—
|
|
Endpoints Purge Activities
|
The Endpoints Purge Activities report enables a user to review the history of endpoints
purge activities. This report requires that the Profiler logging
category is enabled. (Note that this category is enabled by
default.)
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and click Profiler. ) and choose
, and click Profiler.
|
|
Internal Administrator Summary
|
The Internal Administrator Summary report enables you to verify the entitlement of administrator users. From this report,
you can also access the Administrator Logins and Change Configuration Audit reports, which enables you to view these details
for each administrator.
|
—
|
|
Operations Audit
|
The Operations Audit report provides details
about any operational changes, such as, running backups,
registering a Cisco ISE node, or restarting an application.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and click Administrative and
Operational Audit. ) and choose
, and click Administrative and
Operational Audit.
|
|
pxGrid Administrator Audit
|
The pxGrid Administrator Audit report provides details of the pxGrid administration
actions, such as client registration, client deregistration,
client approval, topic creation, topic deletion,
publisher-subscriber addition, and publisher-subscriber deletion
on the Primary PAN.
Every record has the name of the administrator who has performed the action on the node.
You can filter the pxGrid Administrator Audit report based on the administrator and message criteria.
|
—
|
|
Secure Communications Audit
|
The Secure Communications Audit report provides auditing details about security-related events in Cisco ISE Admin CLI, which
includes authentication failures, possible break-in attempts, SSH logins, failed passwords, SSH logouts, invalid user accounts,
and so on.
|
—
|
|
User Change Password Audit
|
The User Change Password Audit report displays
verification about employees' password changes.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and click Administrative and
Operational Audit. ) and choose
, and click Administrative and
Operational Audit.
|
| Trustsec Audit |
TrustSec Audit logs contains:
-
Management (Create, Rename, Update, and Delete) of TrustSec components.
-
Deployments of SGACLs and SGTs to TrustSec-enabled NADs
-
TrustSec Sessions.
If Cisco ISE is integrated with Catalyst Center, and SD Access is managed by Catalyst Center, then this log is empty.
|
—
|
|
Device Administration
|
|
TACACS Authentication Summary
|
The TACACS Authentication Summary report provides details about the most common
authentications, and the reason for authentication failures.
|
—
|
|
TACACS Accounting
|
The TACACS Accounting report provides accounting details for a device session. It
displays information related to the generated and logged time of
the users and devices.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and select TACACS Accounting. ) and choose
and select TACACS Accounting.
|
|
Top N Authentication by Failure Reason
|
The Top N Authentication by Failure Reason report displays the total number of
authentications by failure reason for a specific period, based
on the selected parameters.
|
—
|
|
Top N Authentication by Network Device
|
The Top N Authentication by Network Device report displays the number of passed and
failed authentications by network device name for a specific
period, based on the selected parameters.
|
—
|
|
Top N Authentication by User
|
The Top N Authentication by User report displays the number of passed and failed authentications by the user name for the
specific period based on the selected parameters.
|
—
|
|
Diagnostics
|
|
AAA Diagnostics
|
The AAA Diagnostics report provides details of all the
network sessions between Cisco ISE and users. If users cannot
access the network, you can review this report to identify
trends and identify whether the issue is isolated to a
particular user or indicative of a more widespread problem.
|
Note
|
Sometimes ISE will silently drop the Accounting Stop request of an endpoint if user
authentication is in progress. However, ISE starts acknowledging
all the accounting requests after user authentication is
completed.
|
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and select the following logging categories:
Policy Diagnostics,
Identity Stores Diagnostics,
Authentication Flow Diagnostics, and
RADIUS Diagnostics. ) and choose
, and select the following logging categories:
Policy Diagnostics,
Identity Stores Diagnostics,
Authentication Flow Diagnostics, and
RADIUS Diagnostics.
|
|
AD Connector Operations
|
The AD Connector Operations report provides log of
operations performed by the AD Connector, such as Cisco ISE
Server password refresh, Kerberos tickets management, DNS
queries, DC discovery, LDAP, RPC Connections management, and so
on.
If some AD failures are encountered, you can review the details in this report to identify the possible causes.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and select AD Connector. ) and choose
, and select AD Connector.
|
|
Endpoint Profile Changes
|
The Top Authorization by Endpoint (MAC address) report displays how many times each endpoint MAC address was authorized by
Cisco ISE to access the network.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and select Passed
Authentications and Failed
Attempts. ) and choose
, and select Passed
Authentications and Failed
Attempts.
|
|
Health Summary
|
The Health Summary report provides details
similar to the Dashboard. However, the Dashboard only displays
data for the past 24 hours. Also, you can review more historical
data using this report.
You can evaluate this data to see consistent patterns in data. For example, you would expect heavier CPU usage when most employees
start their work days. If you see inconsistencies in these trends, you can identify potential problems.
The CPU Usage table lists the percentage of CPU usage for the different Cisco ISE functions. The output of the show cpu usage CLI command is presented in this table and you can correlate these values with the issues in your deployment to identify
possible causes.
|
—
|
|
ISE Counters
|
The ISE Counters report lists the threshold values for various attributes. The values for
these different attributes are collected at different intervals
and the data is presented in a tabular format; one at 5-minute
interval and another after 5 minutes.
You can evaluate this data to see the trend, and if you find values that are higher than
the threshold, you can correlate this information with the
issues in your deployment to identify possible causes.
By default, Cisco ISE collects the values for these attributes. You can choose to disable
this data collection from the Cisco ISE CLI using the
application configure ise command. Choose option
14 to enable or disable counter attribute collection.
|
—
|
|
Key Performance Metrics
|
The Key Performance Metrics report provides statistical information about the number of endpoints that connect to your deployment
and the amount of RADIUS requests that are processed by each of the PSNs on an hourly basis. This report lists the average
load on the server, average latency per request, and the average transactions per second.
|
—
|
|
Misconfigured NAS
|
The Misconfigured NAS report provides
information about NADs with inaccurate accounting frequency,
typically when sending accounting information frequently. If you
have taken corrective actions and fix the misconfigured NADs,
the report displays fixed acknowledgment in the report.
|
Note
|
RADIUS Suppression should be enabled to run this
report.
|
|
—
|
|
Misconfigured Supplicants
|
The Misconfigured Supplicants report provides
a list of misconfigured supplicants along with the statistics
because of failed attempts that are performed by a specific
supplicant. If you have taken corrective actions and fix the
misconfigured supplicant, the report displays fixed
acknowledgment in the report.
|
Note
|
RADIUS Suppression should be enabled to run this
report.
|
|
—
|
|
Network Device Session Status
|
The Network Device Session Status Summary
report enables you to display switch configuration without
logging in to the switch directly.
Cisco ISE accesses these details using an SNMP
query and requires that your network devices are configured with
SNMP v1 or v2c.
If a user is experiencing network issues, this
report can help you identify if the issue is related to switch
configuration or with Cisco ISE.
|
—
|
|
OCSP Monitoring
|
The OCSP Monitoring Report specifies the
status of the Online Certificate Status Protocol (OCSP)
services. It identifies whether Cisco ISE can successfully
contact a certificate server, and provides certificate status
auditing. It also provides a summary of all the OCSP
certificate-validation operations performed by Cisco ISE. It
retrieves information related to the good and revoked primary
and secondary certificates from the OCSP server. Cisco ISE
caches the responses and utilizes them for generating subsequent
OCSP Monitoring Reports. In the event the cache is cleared, it
retrieves information from the OCSP server.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and select System
Diagnostics. ) and choose
, and select System
Diagnostics.
|
|
RADIUS Errors
|
The RADIUS Errors report enables you to check
for RADIUS Requests Dropped (authentication or accounting
requests that are discarded from unknown Network Access Device),
EAP connection time outs, and unknown NADs.
|
Note
|
You can view the report only for the past 5 days.
|
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and select Failed
Attempts. ) and choose
, and select Failed
Attempts.
|
|
System Diagnostics
|
The System Diagnostic report provides details about the status of the Cisco ISE nodes. If a Cisco ISE node is unable to register,
you can review this report to troubleshoot the issue.
This report requires that you first enable several diagnostic logging categories. Collecting these logs can negatively impact
Cisco ISE performance. So, these categories are not enabled by default, and you should enable them just long enough to collect
the data. Otherwise, they are automatically disabled after 30 minutes.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and select the following logging categories:
Internal Operations Diagnostics,
Distributed Management, and
Administrator Authentication and
Authorization. ) and choose
, and select the following logging categories:
Internal Operations Diagnostics,
Distributed Management, and
Administrator Authentication and
Authorization.
|
|
Endpoints and Users
|
|
Agentless Posture
|
Lists all the endpoints that ran Agentless posture.
|
—
|
|
Authentication Summary
|
The Authentication Summary report is based on
the RADIUS authentications. It enables you to identify the most
common authentications and the reason for authentication
failures, if any. For example, if one Cisco ISE server is
handling significantly more authentications than others, you
might want to reassign users to different Cisco ISE servers to
better balance the load.
|
Note
|
Because the Authentication Summary report or dashboard collects and
displays the latest data corresponding to failed or passed
authentications, the contents of the report appear after a delay
of a few minutes.
|
|
—
|
|
Client Provisioning
|
The Client Provisioning report indicates the
client provisioning agents applied to particular endpoints. You
can use this report to verify the policies applied to each
endpoint, and in turn, use this to verify whether the endpoints
have been correctly provisioned.
|
Note
|
The MAC address of an endpoint is not displayed in the Endpoint
ID column if the endpoint does not connect with
ISE (no session is established), or if a Network Address
Translation (NAT) address is used for the session.
|
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
, and select Posture and Client
Provisioning Audit and Posture and
Client Provisioning Diagnostics. ) and choose
, and select Posture and Client
Provisioning Audit and Posture and
Client Provisioning Diagnostics.
|
|
Current Active Sessions
|
The Current Active Sessions report enables you
to export a report with details about who is on the network
within a specified time period.
If a user isn't getting network access, you
can see whether the session is authenticated or terminated, or
if there is another problem with the session.
|
—
|
|
Endpoint Scripts Provisioning Summary
|
The Endpoint Scripts Provisioning Summary window displays details
of jobs run through the Endpoint Scripts
window over the last 30 days.
|
—
|
|
External Mobile Device Management
|
The External Mobile Device Management report provides details about integration between Cisco ISE and the external Mobile
Device Management (MDM) server.
You can use this report to see which endpoints have been provisioned by the MDM server without logging into the MDM server
directly. It also displays information such as registration and MDM-compliance status.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and select MDM. ) and choose
and select MDM.
|
|
Passive ID
|
The Passive ID report enables you to monitor the state of WMI connection to the domain controller and gather statistics related to it (such
as amount of notifications received, amount of user login/logouts per second etc.)
|
Note
|
Sessions authenticated by this method do not have authentication details in the report.
|
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and select Identity Mapping. ) and choose
and select Identity Mapping.
|
|
Manual Certificate Provisioning
|
The Manual Certificate Provisioning report lists all the certificates that are provisioned manually via the certificate provisioning
portal.
|
—
|
|
Posture Assessment by Condition
|
The Posture Assessment by Condition report enables you to view records based on the posture policy condition configured in
ISE to validate that the most up-to-date security settings or applications are available on client machines.
|
—
|
|
Posture Assessment by Endpoint
|
The Posture Assessment by Endpoint report provides detailed information, such as the time, status, and PRA Action, of an endpoint.
You can click Details to view further information of an endpoint.
|
Note
|
The Posture Assessment by Endpoint report does not provide posture policy details of applications and hardware attributes
of an endpoint. You can view this information only in the Context Visibility page.
|
|
—
|
|
Posture Script Remediation
|
Posture Script Remediation is used to check the status of the remediation script execution.
The status is one of the following:
-
Remediation script execution was successful.
-
Remediation was attempted, and the script exited with failure.
-
Remediation was not attempted (default).
-
Remediation attempt failed. The script failed an integrity check as the policy included might have been tampered with.
-
Remediation attempt failed. Client failed to download the script.
-
Remediation attempt failed. The script failed an integrity test as the script might be corrupt or has been tampered with.
-
Remediation attempt failed. The script was executed but did not exit in time (timeout).
-
Remediation attempt failed. A generic internal system failure occurred.
-
Remediation attempt failed. The script type is not supported.
-
Remediation attempt failed. Failure with launching the script.
-
Certificate verification failure. Client could not verify the server certificate presented by Cisco ISE.
|
—
|
|
Profiled Endpoints Summary
|
The Profiled Endpoints Summary report provides profiling details about endpoints that are accessing the network.
|
Note
|
For endpoints that do not register a session time, such as a Cisco IP-Phone, the term Not Applicable is shown in the Endpoint
session time field.
|
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and select Profiler. ) and choose
and select Profiler.
|
|
RADIUS Accounting
|
The RADIUS Accounting report identifies how long users have been on the network. If users are losing network access, you can
use this report to identify whether Cisco ISE is the cause of the network connectivity issues.
|
Note
|
Radius accounting interim updates are included in the RADIUS Accounting report if the interim updates contain information
about the changes to the IPv4 or IPv6 addresses for the given sessions.
|
|
|
|
RADIUS Authentications
|
The RADIUS Authentications report enables you to review the history of authentication failures and successes. If users cannot
access the network, you can review the details in this report to identify possible causes.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and select these logging categories: Passed Authentications and Failed Attempts. ) and choose
and select these logging categories: Passed Authentications and Failed Attempts.
|
|
Registered Endpoints
|
The Registered Endpoints report displays all personal devices registered by employees.
|
—
|
|
Rejected Endpoints
|
The Rejected Endpoints report lists all rejected or released personal devices that are registered by employees.
|
—
|
|
Supplicant Provisioning
|
The Supplicant Provisioning report provides details about the supplicants provisioned to employee's personal devices.
|
Posture and Client Provisioning Audit
|
|
Top Authorizations by Endpoint
|
The Top Authorization by Endpoint (MAC address) report displays how many times each endpoint MAC address was authorized by
Cisco ISE to access the network.
|
Passed Authentications, Failed Attempts
|
|
Top Authorizations by User
|
The Top Authorization by User report displays how many times each user was authorized by Cisco ISE to access the network.
|
Passed Authentications, Failed Attempts
|
|
Top N Authentication by Access Service
|
The Top N Authentication by Access Service report displays the number of passed and failed authentications by the access service
type for the specific period based on the selected parameters.
|
—
|
|
Top N Authentication by Failure Reason
|
The Top N Authentication by Failure Reason report displays the total number of authentications by failure reason for the specific
period based on the selected parameters.
|
—
|
|
Top N Authentication by Network Device
|
The Top N Authentication by Network Device report displays the number of passed and failed authentications by the network
device name for the specific period based on the selected parameters.
|
—
|
|
Top N Authentication by User
|
The Top N Authentication by User report displays the number of passed and failed authentications by the user name for the
specific period based on the selected parameters.
|
—
|
|
Guest
|
|
AUP Acceptance Status
|
The AUP Acceptance Status report provides details of AUP acceptances from all the Guest portals.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and select Guest. ) and choose
and select Guest.
|
|
Guest Accounting
|
The Guest Accounting report is a subset of the RADIUS Accounting report. All users assigned to the Activated Guest or Guest
identity groups appear in this report.
|
—
|
|
Primary Guest Report
|
The Primary Guest Report combines data from various Guest Access reports and enables you to export data from different reporting sources.
The Primary Guest report also provides details about the websites that guest users are visiting. You can use this report for security
auditing purposes to demonstrate when guest users accessed the network and what they did on it.
You must also enable HTTP inspection on the network access device (NAD) used for guest traffic. This information is sent back
to Cisco ISE by the NAD.
To check when the clients reach the maximum simultaneous sessions limit, from the Admin portal, choose Administration > System > Logging > Logging Categories and do the following:
-
Increase the log level of "Authentication Flow Diagnostics" logging category from WARN to INFO.
-
Change LogCollector Target from Available to Selected under the "Logging Category" of AAA Diagnostics.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and select Passed Authentications. ) and choose
and select Passed Authentications.
|
|
My Devices Login and Audit
|
The My Devices Login and Audit report provides details about the login activities and the operations performed by the users
on the devices in My Devices Portal.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and select My Devices. ) and choose
and select My Devices.
|
|
Sponsor Login and Audit
|
The Sponsor Login and Audit report provides details of guest users' login, add, delete, enable, suspend and update operations
and the login activities of the sponsors at the sponsors portal.
If guest users are added in bulk, they are visible under the column 'Guest Users.' This column is hidden by default. On export,
these bulk users are also present in the exported file.
|
In the Cisco ISE GUI, click the Menu icon ( ) and choose
and select Guest. ) and choose
and select Guest.
|
|
SXP
|
|
SXP Binding
|
The SXP Binding report provides information about the IP-SGT bindings that are exchanged over SXP connection.
|
—
|
|
SXP Connection
|
You can use this report to monitor the status of an SXP connection and gather information related to it, such as peer IP,
SXP node IP, VPN name, SXP mode, and so on.
|
—
|
|
Trustsec
|
|
RBACL Drop Summary
|
The RBACL Drop Summary report is specific to the TrustSec feature, which is available only with an Advanced Cisco ISE license.
This report also requires that you configure the network devices to send NetFlow events for dropped events to Cisco ISE.
If a user violates a particular policy or access, packets are dropped and indicated in this report.
|
Note
|
Flows for RBACL dropped packets are available only with the Cisco Catalyst 6500 series switches.
|
|
—
|
|
Top N RBACL Drops By User
|
The Top N RBACL Drops By User report is specific to the TrustSec feature, which is available only with an Advanced Cisco ISE
license.
This report also requires that you configure the network devices to send NetFlow events for dropped events to Cisco ISE.
This report displays policy violations (based on packet drops) by specific users.
|
Note
|
Flows for RBACL dropped packets are available only with the Cisco Catalyst 6500 series switches.
|
|
—
|
|
TrustSec ACI
|
This report lists the SGTs and SXP mappings that are synchronized with the IEPGs, EEPGs, endpoints, and subnet configuration
of APIC. These details are displayed only if the TrustSec APIC integration feature is enabled.
|
—
|
|
TrustSec Deployment Verification
|
You can use this report to verify whether the latest TrustSec policies are deployed on all network devices or if there are
any discrepancies between the policies configured in Cisco ISE and the network devices.
Click the Details icon to view the results of the verification process. You can view the following details:
-
When the verification process started and completed
-
Whether the latest TrustSec policies are successfully deployed on the network devices. You can also view the names and IP
addresses of the network devices on which the latest TrustSec policies are deployed.
-
Whether if there are any discrepancies between the policies configured in Cisco ISE and the network devices. It displays the
device name, IP address, and the corresponding error message for each policy difference.
You can view the TrustSec Deployment Verification alarms in the Alarms dashlet (under Work Centers > TrustSec > Dashboard and Home > Summary).
|
Note
|
-
The time taken for reporting depends on the number of network devices and TrustSec groups in your deployment.
-
The error message length in the TrustSec Deployment Verification report is currently limited to 480 characters. Error messages
with more than 480 characters will be truncated and only the first 480 characters will be displayed in the report.
|
|
—
|
|
Trustsec Policy Download
|
This report lists the requests sent by the network devices for policy (SGT/SGACL) download and the details sent by ISE. If
the Workflow mode is enabled, the requests can be filtered for production or staging matrix.
|
To view this report, you must do the following:
-
In the Cisco ISE GUI, click the Menu icon ( ) and choose
. ) and choose
.
-
Choose .
-
Set the Log Severity Level to DEBUG for RADIUS Diagnostics.
|
|
Threat Centric NAC Service
|
|
Adapter Status
|
The Adapter Status report displays the status of the threat and vulnerability adapters.
|
—
|
|
COA Events
|
When a vulnerability event is received for an endpoint, Cisco ISE triggers CoA for that endpoint. The CoA Events report displays
the status of these CoA events. It also displays the old and new authorization rules and the profile details for these endpoints.
|
—
|
|
Threat Events
|
The Threat Events report provides a list of all the threat events that Cisco ISE receives from the various adapters that you
have configured.
|
—
|
|
Vulnerability Assessment
|
The Vulnerability Assessment report provides information about the assessments that are happening for your endpoints. You
can view this report to check if the assessment is happening based on the configured policy.
|
—
|

 Feedback
Feedback