Overview
Alibaba Cloud is a public cloud environment. The Firewall Threat Defense Virtual runs as a guest in the Alibaba Cloud environment.
Alibaba Supported Instance Types
Firewall Threat Defense Virtual on Alibaba can use the following instance types:
|
Network Enhanced Machine Types |
|||
|---|---|---|---|
|
Configuration |
No of vCPUs |
Memory (GB) |
Maximum Interfaces Supported |
|
ecs.g5ne.xlarge |
4 |
16 |
4 |
|
ecs.g5ne.2xlarge |
8 |
32 |
6 |
|
ecs.g5ne.4xlarge |
16 |
64 |
8 |
 Note |
Firewall Threat Defense Virtual needs a minimum of four interfaces (ENIs) to support the instance. |
 Note |
We do not support resizing the instance type and deploying the Firewall Threat Defense Virtual. You can only deploy a Firewall Threat Defense Virtual with a different instance size through a new deployment. |
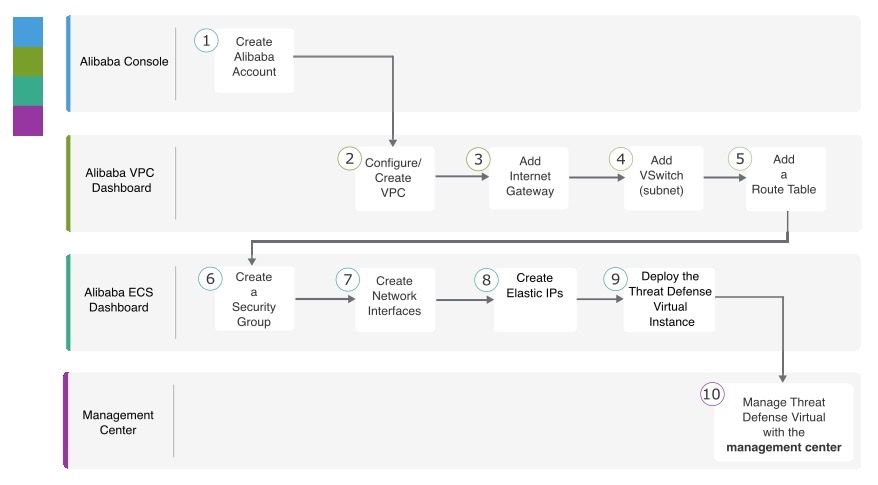
Network Requirement
-
You can create one VPC with four Vswitch (Subnet) for basic Firewall Threat Defense Virtual support.
-
Management Vswitch must be available in the same zone in which instance is being deployed, otherwise, you have to create it.
Related Documentation
For more information on instance types and their configuration, see Alibaba Cloud
 Feedback
Feedback