Overview of File Reputation Filtering and File Analysis
Advanced Malware Protection protects against zero-day and targeted file-based threats in email attachments by:
- Obtaining the reputation of known files.
- Analyzing behavior of certain files that are not yet known to the reputation service.
- Continuously evaluating emerging threats as new information becomes available, and notifying you about files that are determined to be threats after they have entered your network.
This feature is available for incoming messages and outgoing messages.
The file reputation and file analysis services have options for either public- or private-cloud (on-premesis).
-
The private-cloud file reputation service is provided by Cisco AMP Virtual Private Cloud appliance, operating in either “proxy” or “air-gap” (on-premises) mode. See Configuring an On-premises File Reputation Server.
-
The private-cloud file analysis service is provided by an on-premises Cisco AMP Threat Grid appliance. See Configuring an On-Premises File Analysis Server.
File Threat Verdict Updates
Threat verdicts can change as new information emerges. A file may initially be evaluated as unknown or clean, and the file may therefore be released to the recipient. If the threat verdict changes as new information becomes available, you will be alerted, and the file and its new verdict appear in the AMP Verdict Updates report. You can investigate the point-of-entry message as a starting point to remediating any impacts of the threat.
Verdicts can also change from malicious to clean.
When no dynamic content is found in a file after file analysis, the verdict is Low Risk. The file is not sent for file analysis, and the message continues through the email pipeline.
When the appliance processes subsequent instances of the same file, the updated verdict is immediately applied.
Information about the timing of verdict updates is included in the file-criteria document referenced in Supported Files for File Reputation and Analysis Services.
Related Topics
File Processing Overview
Evaluation of file reputation and sending of files for analysis occur immediately after anti-virus scanning, regardless of verdicts from previous scanning engines, unless a final action has been taken on the message.
 Note |
By default, if a message has malformed MIME headers, the file reputation service returns a verdict of “unscannable.” The appliance will also attempt to extract the attachments from this message. If the appliance is unable to extract the attachments, verdict will remain as “unscannable.” If the appliance is able to extract the attachments, the file reputation of the attachments is evaluated. If the attachments are malicious, the verdict is changed from “unscannable” to “malicious.” |
Communications between the appliance and the file reputation service are encrypted and protected from tampering.
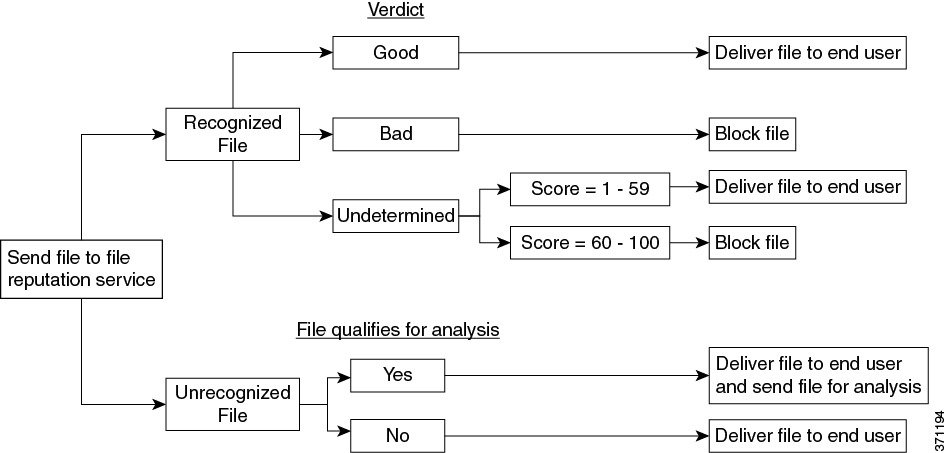
After a file’s reputation is evaluated:
- If a message does not contain any attachments, the file reputation service will return a verdict of “skipped.”
- If the file is known to the file reputation service and is determined to be clean, the message continues through the workqueue.
- If the file reputation service returns a verdict of malicious, for any attachment in the message, then the appliance applies the action that you have specified in the applicable mail policy.
- If the file is known to the reputation service but there is insufficient information for a definitive verdict, the reputation service returns a reputation score based on characteristics of the file such as threat fingerprint and behavioral analysis. If this score meets or exceeds the configured reputation threshold, the appliance applies the action that you have configured in the mail policy for files that contain malware .
- If the reputation service has no information about the file, and the file does not meet the criteria for analysis (see Supported Files for File Reputation and Analysis Services), the file is considered clean and the message continues through the workqueue.
- If you have enabled the File Analysis service, and the reputation service has no information about the file, and the file meets the criteria for files that can be analyzed (see Supported Files for File Reputation and Analysis Services), then the message can be quarantined (see Quarantining Messages with Attachments Sent for Analysis) and the file sent for analysis. If you have not configured the appliance to quarantine messages when attachments are sent for analysis, or the file is not sent for analysis, then the message is released to the user.
- For deployments with on-premises file analysis, the reputation evaluation and file analysis occur simultaneously. If the reputation service returns a verdict, that verdict is used, as the reputation service includes inputs from a wider range of sources. If the file is unknown to the reputation service, the file the file analysis verdict is used.
- If the file reputation verdict information is unavailable because the connection with the server timed out, the file is considered as Unscannable and the actions configured are applied.
If the file is sent for analysis:
- If the file is sent to the cloud for analysis: Files are sent over HTTPS.
- Analysis normally takes minutes, but may take longer.
- A file that is flagged as malicious after File Analysis may not be identified as malicious by the reputation service. File reputation is determined by a variety of factors over time, not necessarily by a single file analysis verdict.
- Results for files analyzed using an on premises Cisco AMP Threat Grid appliance are cached locally.
For information about verdict updates, see File Threat Verdict Updates.
Supported Files for File Reputation and Analysis Services
The reputation service evaluates most file types. File type identification is determined by file content and is not dependent on the filename extension.
Some files with unknown reputation can be analyzed for threat characteristics. When you configure the file analysis feature, you choose which file types are analyzed. New types can be added dynamically; you will receive an alert when the list of uploadable file types changes, and can select added file types to upload.
Details about what files are supported by the reputation and analysis services are available only to registered Cisco customers. For information about which files are evaluated and analyzed, see File Criteria for Advanced Malware Protection Services for Cisco Content Security Products, available from https://www.cisco.com/c/en/us/support/security/email-security-appliance/products-user-guide-list.html. The criteria for evaluating a file’s reputation and for sending files for analysis may change at any time.
In order to access this document, you must have a Cisco customer account with a support contract. To register, visit https://tools.cisco.com/RPF/register/register.do.
You should configure policies to block delivery of files that are not addressed by Advanced Malware Protection.
 Note |
A file (either in incoming mail or outgoing mail) that has already been uploaded for analysis from any source will not be uploaded again. To view analysis results for such a file, search for the SHA-256 from the File Analysis reporting page. |
Related Topics
Archive or Compressed File Processing
If the file is compressed or archived,
- Reputation of the compressed or archive file is evaluated.
For information about which archived and compressed files are examined, including file formats, see the information linked from Supported Files for File Reputation and Analysis Services.
In this scenario,
- If one of the extracted files is malicious, the file reputation service returns a verdict of Malicious for the compressed or the archive file.
- If the compressed or archive file is malicious and all the extracted files are clean, the file reputation service returns a verdict of Malicious for the compressed or the archive file.
- If the verdict of any of the extracted files is unknown, the extracted files are optionally (if configured and the file type is supported for file analysis) sent for file analysis.
- If the verdict of any of the extracted files or attachments is low risk, the file is not sent for file analysis.
- If the extraction of a file fails while decompressing a compressed or an archive file, the file reputation service returns a verdict of Unscannable for the compressed or the archive file. Keep in mind that, in this scenario, if one of the extracted files is malicious, the file reputation service returns a verdict of Malicious for the compressed or the archive file (Malicious verdict takes precedence over Unscannable verdict).
-
An archive or compressed file is treated as unscannable in the following scenarios:
-
The data compression ratio is more than 20.
-
The archive file contains more than five levels of nesting.
-
The archive file contains more than 200 child files.
-
The archive file size is more than 50 MB.
-
The archive file is password protected or unreadable.
-
 Note |
Reputation of the extracted files with safe MIME types, for example, text/plain, are not evaluated. |
Privacy of Information Sent to the Cloud
- Only the SHA that uniquely identifies a file is sent to the reputation service in the cloud. The file itself is not sent.
- If you are using the file analysis service in the cloud and a file qualifies for analysis, the file itself is sent to the cloud.
-
Information about every file that is sent to the cloud for analysis and has a verdict of "malicious" is added to the reputation database. This information is used along with other data to determine a reputation score.
Information about files analyzed by an on premises Cisco AMP Threat Grid appliance is not shared with the reputation service.
 Feedback
Feedback