Email Authentication Overview
AsyncOS supports email verification and signing to prevent email forgery. To verify incoming mail, AsyncOS supports Sender Policy Framework (SPF), Sender ID Framework (SIDF), DomainKeys Identified Mail (DKIM), Domain-based Message Authentication, Reporting and Conformance (DMARC), and Forged Email Detection. To authenticate outbound mail, AsyncOS supports DomainKeys and DKIM signing.
Related Topics
DomainKeys and DKIM Authentication
With DomainKeys or DKIM email authentication, the sender signs the email using public key cryptography. The verified domain can then be used to detect forgeries by comparing it with the domain in the From: (or Sender:) header of the email.
DomainKeys and DKIM consist of two main parts: signing and verification. AsyncOS supports the “signing” half of the process for DomainKeys, and it supports both signing and verification for DKIM. You can also enable bounce and delay messages to use DomainKeys and DKIM signing.
Related Topics
DomainKeys and DKIM Authentication Workflow
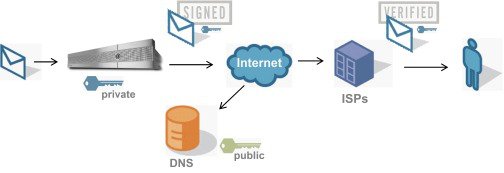
- Administrator (domain owner) publishes a public key into the DNS name space.
- Administrator loads a private key in the outbound Mail Transfer Agent (MTA).
- Email submitted by an authorized user of that domain is digitally signed with the respective private key. The signature is inserted in the email as a DomainKey or DKIM signature header and the email is transmitted.
- Receiving MTA extracts the DomainKeys or DKIM signature from the header and the claimed sending domain (via the Sender: or From: header) from the email. The public key is retrieved from the claimed signing domain which is extracted from DomainKeys or DKIM signature header fields.
- The public key is used to determine whether the DomainKeys or DKIM signature was generated with the appropriate private key.
To test your outgoing DomainKeys signatures, you can use a Yahoo! or Gmail address, as these services are free and provide validation on incoming messages that are DomainKeys signed.
DomainKeys and DKIM Signing in AsyncOS
DomainKeys and DKIM signing in AsyncOS is implemented via domain profiles and enabled via a mail flow policy (typically, the outgoing “relay” policy). For more information, see the “Configuring the Gateway to Receive Mail” chapter. Signing the message is the last action performed by the appliance before the message is sent.
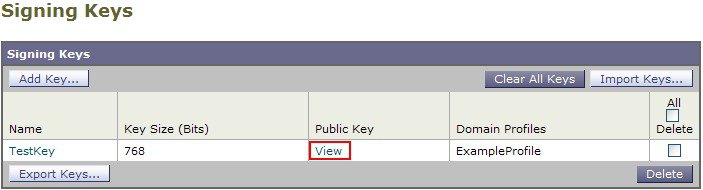
Domain profiles associate a domain with domain key information (signing key and related information). As email is sent via a mail flow policy on the appliance , sender email addresses that match any domain profile are DomainKeys signed with the signing key specified in the domain profile. If you enable both DKIM and DomainKeys signing, the DKIM signature is used. You implement DomainKeys and DKIM profiles via the domainkeysconfig CLI command or via the Mail Policies > Domain Profiles and the Mail Policies > Signing Keys pages in the GUI.
DomainKeys and DKIM signing works like this: a domain owner generates two keys — a public key stored in the public DNS (a DNS TXT record associated with that domain) and a private key that is stored on the appliance is used to sign mail that is sent (mail that originates) from that domain.
-
There is no Sender: header.
-
You select the Use From Header for DKIM Signing option in the DKIM Global Setting page in the web interface.
 Note |
From Async0S 10.0 and later, you can select whether you want to use the From: header for DKIM Signing option in the DKIM Global Settings page of the web interface. It is mainly important to use the From: header with DKIM Signing for proper DMARC verification. |
If a valid address is not found, the message is not signed and the event is logged in the mail_logs.
 Note |
If you create both a DomainKey and DKIM profile (and enable signing on a mail flow policy), AsyncOS signs outgoing messages with both a DomainKeys and DKIM signature. |
If a valid sending address is found, the sending address is matched against the existing domain profiles. If a match is found, the message is signed. If not, the message is sent without signing. If the message has an existing DomainKeys (a “DomainKey-Signature:” header) the message is only signed if a new sender address has been added after the original signing. If a message has an existing DKIM signature, a new DKIM signature is added to the message.
AsyncOS provides a mechanism for signing email based on domain as well as a way to manage (create new or input existing) signing keys.
The configuration descriptions in this document represent the most common uses for signing and verification. You can also enable DomainKeys and DKIM signing on a mail flow policy for inbound email, or enable DKIM verification on a mail flow policy for outbound email.
 Note |
When you configure domain profiles and signing keys in a clustered environment, note that the Domain Key Profile settings and Signing Key settings are linked. Therefore, if you copy, move or delete a signing key, the same action is taken on the related profile. |

 Feedback
Feedback