Release Notes for Cisco Secure Firewall ASDM, 7.18(x)
This document contains release information for ASDM Version 7.18(x) for the Secure Firewall ASA series.
Important Notes
-
ASDM signed-image support in 9.18(2)/7.18(1.152) and later—The ASA now validates whether the ASDM image is a Cisco digitally signed image. If you try to run an older ASDM image with an ASA version with this fix, ASDM will be blocked and the message “%ERROR: Signature not valid for file disk0:/<filename>” will be displayed at the ASA CLI. ASDM release 7.18(1.152) and later are backwards compatible with all ASA versions, even those without this fix. (CSCwb05291, CSCwb05264)
-
Downgrade issue from 9.18 or later—There is a behavior change in 9.18 where the access-group command will be listed before its access-list commands. If you downgrade, the access-group command will be rejected because it has not yet loaded the access-list commands. This outcome occurs even if you had previously enabled the forward-reference enable command, because that command is now removed. Before you downgrade, be sure to copy all access-group commands manually, and then after downgrading, re-enter them.
-
9.18(1) upgrade issue if you enabled HTTPS/ASDM (with HTTPS authentication) and SSL on the same interface with the same port—If you enable both SSL (webvpn > enable interface) and HTTPS/ASDM (http ) access on the same interface, you can access AnyConnect from https://ip_address and ASDM from https://ip_address/admin, both on port 443. However, if you also enable HTTPS authentication (aaa authentication http console), then you must specify a different port for ASDM access starting in 9.18(1). Make sure you change the port before you upgrade using the http command. (CSCvz92016)
-
Behavior change for Secure Firewall 3100 in 9.18(2.7)—When you set the FEC to Auto using the fec command on the Secure Firewall 3100 fixed ports, the default type is now set to cl108-rs instead of cl74-fc for 25 GB SR, CSR, and LR transceivers. (CSCwc75082)
-
ASDM Upgrade Wizard—Due to ASD API migration, you must use ASDM 7.18 or later to upgrade to ASA 9.18 or later. Because ASDM is backwards compatible with earlier ASA versions, you can upgrade ASDM to 7.18 or later for any ASA version.
-
ASDM 7.18 ending support for Java Web Launch—Starting with ASDM 7.18, ASDM will no longer support Java Web Start due to Oracle’s end of support for JRE 8 and Java Network Launching Protocol (JNLP). You will have to install the ASDM Launcher to launch ASDM.
System Requirements
ASDM requires a computer with a CPU with at least 4 cores. Fewer cores can result in high memory usage.
ASDM Java Requirements
You can install ASDM using Oracle JRE 8.0 (asdm-version.bin) or OpenJRE 1.8.x (asdm-openjre-version.bin).
The Oracle version of ASDM is included in the ASA package; if you want to use the OpenJRE version, you will need to copy it to the ASA and configure the ASA to use that version of ASDM.
 Note |
ASDM is not supported on Linux. |
|
Operating System |
Browser |
Oracle JRE |
OpenJRE |
||||||
|---|---|---|---|---|---|---|---|---|---|
|
Firefox |
Safari |
Chrome |
|||||||
|
Microsoft Windows (English and Japanese):
|
Yes |
No support |
Yes |
8.0 version 8u261 or later |
1.8
|
||||
|
Apple OS X 10.4 and later |
Yes |
Yes |
Yes (64-bit version only) |
8.0 version 8u261 or later |
1.8 |
||||
ASDM Compatibility Notes
The following table lists compatibility caveats for ASDM.
|
Conditions |
Notes |
||
|---|---|---|---|
|
ASDM Launcher compatibility with ASDM version |
"Unable to Launch Device Manager" error message. If you upgrade to a new ASDM version and then get this error, you may need to re-install the latest Launcher.
|
||
|
Windows Active Directory directory access |
In some cases, Active Directory settings for Windows users may restrict access to program file locations needed to successfully launch ASDM on Windows. Access is needed to the following directories:
If your Active Directory is restricting directory access, you need to request access from your Active Directory administrator. |
||
|
Windows 10 |
"This app can't run on your PC" error message. When you install the ASDM Launcher, Windows 10 might replace the ASDM shortcut target with the Windows Scripting Host path, which causes this error. To fix the shortcut target:
|
||
|
OS X |
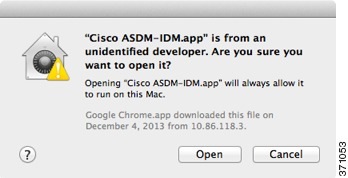
On OS X, you may be prompted to install Java the first time you run ASDM; follow the prompts as necessary. ASDM will launch after the installation completes. |
||
|
OS X 10.8 and later |
You need to allow ASDM to run because it is not signed with an Apple Developer ID. If you do not change your security preferences, you see an error screen. 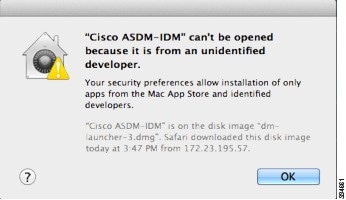
|
||
|
(ASA 5500 and ISA 3000) Requires Strong Encryption license (3DES/AES) on ASA
|
ASDM requires an SSL connection to the ASA. You can request a 3DES PAK license from Cisco:
|
||
|
When the ASA uses a self-signed certificate or an untrusted certificate, Firefox and Safari are unable to add security exceptions when browsing using HTTPS over IPv6. See https://bugzilla.mozilla.org/show_bug.cgi?id=633001. This caveat affects all SSL connections originating from Firefox or Safari to the ASA (including ASDM connections). To avoid this caveat, configure a proper certificate for the ASA that is issued by a trusted certificate authority. |
||
|
If you change the SSL encryption on the ASA to exclude both RC4-MD5 and RC4-SHA1 algorithms (these algorithms are enabled by default), then Chrome cannot launch ASDM due to the Chrome “SSL false start” feature. We suggest re-enabling one of these algorithms (see the pane); or you can disable SSL false start in Chrome using the --disable-ssl-false-start flag according to Run Chromium with flags. |
Install an Identity Certificate for ASDM
When using Java 7 update 51 and later, the ASDM Launcher requires a trusted certificate. An easy approach to fulfill the certificate requirements is to install a self-signed identity certificate.
See Install an Identity Certificate for ASDM to install a self-signed identity certificate on the ASA for use with ASDM, and to register the certificate with Java.
Increase the ASDM Configuration Memory
ASDM supports a maximum configuration size of 512 KB. If you exceed this amount you may experience performance issues. For example, when you load the configuration, the status dialog box shows the percentage of the configuration that is complete, yet with large configurations it stops incrementing and appears to suspend operation, even though ASDM might still be processing the configuration. If this situation occurs, we recommend that you consider increasing the ASDM system heap memory. To confirm that you are experiencing memory exhaustion, monitor the Java console for the "java.lang.OutOfMemoryError" message.
In addition, we recommend reducing your configuration size if possible, for example, by removing unused objects.
Increase the ASDM Configuration Memory in Windows
To increase the ASDM heap memory size, edit the run.bat file by performing the following procedure.
Procedure
|
Step 1 |
Go to the ASDM installation directory, for example C:\Program Files (x86)\Cisco Systems\ASDM. |
|
Step 2 |
Edit the run.bat file with any text editor. |
|
Step 3 |
In the line that starts with “start javaw.exe”, change the argument prefixed with “-Xmx” to specify your desired heap size. For example, change it to -Xmx768M for 768 MB or -Xmx1G for 1 GB. For very large configurations, you may need to specify a heap size up to 2 GB. |
|
Step 4 |
Save the run.bat file. |
Increase the ASDM Configuration Memory in Mac OS
To increase the ASDM heap memory size, edit the Info.plist file by performing the following procedure.
Procedure
|
Step 1 |
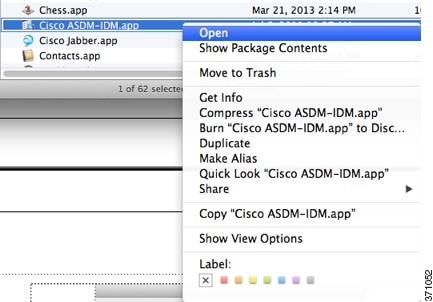
Right-click the Cisco ASDM-IDM icon, and choose Show Package Contents. |
|
Step 2 |
In the Contents folder, double-click the Info.plist file. If you have Developer tools installed, it opens in the Property List Editor. Otherwise, it opens in TextEdit. |
|
Step 3 |
Under , change the string prefixed with “-Xmx” to specify your desired heap size. For example, change it to -Xmx768M for 768 MB or -Xmx1G for 1 GB. 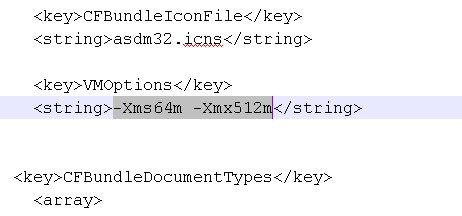 For very large configurations, you may need to specify a heap size up to 2 GB. |
|
Step 4 |
If this file is locked, you see an error such as the following: 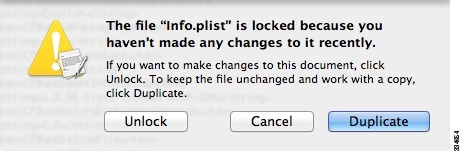 |
|
Step 5 |
Click Unlock and save the file. If you do not see the Unlock dialog box, exit the editor, right-click the Cisco ASDM-IDM icon, choose Copy Cisco ASDM-IDM, and paste it to a location where you have write permissions, such as the Desktop. Then change the heap size from this copy. |
ASA and ASDM Compatibility
For information about ASA/ASDM software and hardware requirements and compatibility, including module compatibility, see Cisco Secure Firewall ASA Compatibility.
VPN Compatibility
For VPN compatibility, see Supported VPN Platforms, Cisco ASA 5500 Series.
New Features
This section lists new features for each release.
 Note |
New, changed, and deprecated syslog messages are listed in the syslog message guide. |
New Features in ASDM 7.18(1.161)
Released: July 3, 2023
There are no new features in this release.
New Features in ASA 9.18(4)/ASDM 7.20(1)
Released: October 3, 2023
|
Feature |
Description |
|---|---|
|
High Availability and Scalability Features |
|
|
Reduced false failovers for ASA high availability |
We now introduced an additional heartbeat module in the data plane of the ASA high availability. This heartbeat module helps to avoid false failovers or split-brain scenarios that can happen due to traffic congestion in the control plain or CPU overload. Also in 9.20(1). |
|
show failover statistics includes client statistics |
The failover client packet statistics are now enhanced to improve debuggability. The show failover statistics command is enhanced to display np-clients (data-path clients) and cp-clients (control-plane clients) information. Modified commands: show failover statistics cp-clients , show failover statistics dp-clients Also in 9.20(2). |
|
show failover statistics events includes new events |
The show failover statistics events command is now enhanced to identify the local failures notified by the App agent: failover link uptime, supervisor heartbeat failures, and disk full issues. Modified commands: show failover statistics events Also in 9.20(2). |
|
Interface Features |
|
| FXOS local-mgtm show command improvements |
See the following additions for interface show commands in FXOS local-mgmt:
New/Modified FXOS commands: show portmanager switch tail-drop-allocated buffers all , show portmanager switch status , show portmanager switch default-rule-drop-counter |
|
Administrative, Monitoring, and Troubleshooting Features |
|
|
show tech support improvements |
Added output to show tech support for:
New/Modified commands: show tech support |
New Features in ASA 9.18(3)/ASDM 7.19(1.90)
Released: February 16, 2023
|
Feature |
Description |
|---|---|
|
Interface Features |
|
|
Default Forward Error Correction (FEC) on Secure Firewall 3100 fixed ports changed to cl108-rs from cl74-fc for 25 GB+ SR, CSR, and LR transceivers |
When you set the FEC to Auto on the Secure Firewall 3100 fixed ports, the default type is now set to cl108-rs instead of cl74-fc for 25 GB SR, CSR, and LR transceivers. New/Modified screens: Also in 9.19(1) and 9.18(2.7). |
|
VPN Features |
|
|
AnyConnect connection authentication using SAML |
In a DNS load balancing cluster, when SAML authentication is configured on ASAs, you can specify a local base URL that uniquely resolves to the device on which the configuration is applied. |
New Features in ASA 9.18(2)/ASDM 7.18(1.152)
Released: August 10, 2022
|
Feature |
Description |
|---|---|
|
Interface Features |
|
|
Loopback interface support for BGP and management traffic |
You can now add a loopback interface and use it for the following features:
New/Modified commands: interface loopback , logging host , neighbor update-source , snmp-server host , ssh , telnet No ASDM support. |
|
ping command changes |
To support pinging a loopback interface, the ping command now has changed behavior. If you specify the interface in the command, the source IP address matches the specified interface IP address, but the actual egress interface is determined by a route lookup using the data routing table. New/Modified commands: ping |
New Features in ASDM 7.18(1.152)
Released: August 2, 2022
There are no new features in this release.
New Features in ASA 9.18(1)/ASDM 7.18(1)
Released: June 6, 2022
|
Feature |
Description |
||
|---|---|---|---|
|
Platform Features |
|||
| ASAv-AWS Security center integration for AWS GuardDuty | You can now integrate Amazon GuardDuty service with ASAv. The integration solution helps you to capture and process the threat analysis data or results (malicious IP addresses) reported by Amazon GuardDuty. You can configure and feed these malicious IP addresses in the ASAv to protect the underlying networks and applications. | ||
|
Firewall Features |
|||
|
Forward referencing of ACLs and objects is always enabled. In addition, object group search for access control is now enabled by default. |
You can refer to ACLs or network objects that do not yet exist when configuring access groups or access rules. In addition, object group search is now enabled by default for access control for new deployments. Upgrading devices will continue to have this command disabled. If you want to enable it (recommended), you must do so manually.
We removed the forward-reference enable command and changed the default for new deployments for object-group-search access-control to enabled. |
||
|
Routing Features |
|||
|
Path monitoring metrics in PBR. |
PBR uses the metrics to determine the best path (egress interface) for forwarding the traffic. Path monitoring periodically notifies PBR with the monitored interface whose metric got changed. PBR retrieves the latest metric values for the monitored interfaces from the path monitoring database and updates the data path. New/Modified screens: |
||
|
Interface Features |
|||
|
Pause Frames for Flow Control for the Secure Firewall 3100 |
If you have a traffic burst, dropped packets can occur if the burst exceeds the buffering capacity of the FIFO buffer on the NIC and the receive ring buffers. Enabling pause frames for flow control can alleviate this issue. New/Modified screens: |
||
|
Breakout ports for the Secure Firewall 3130 and 3140 |
You can now configure four 10GB breakout ports for each 40GB interface on the Secure Firewall 3130 and 3140. New/Modified screens: |
||
|
License Features |
|||
|
Secure Firewall 3100 support for the Carrier license |
The Carrier license enables Diameter, GTP/GPRS, SCTP inspection. New/Modified screens: . |
||
|
Certificate Features |
|||
|
Mutual LDAPS authentication. |
You can configure a client certificate for the ASA to present to the LDAP server when it requests a certificate to authenticate. This feature applies when using LDAP over SSL. If an LDAP server is configured to require a peer certificate, the secure LDAP session will not complete and authentication/authorization requests will fail. New/Modified screens: , Add/Edit LDAP server. |
||
|
Authentication: Validate certificate name or SAN |
When a feature specific reference-identity is configured, the peer certificate identity is validated with the matching criteria specified under crypto ca reference-identity <name> submode commands. If there is no match found in the peer certificate Subject Name/SAN or if the FQDN specified with reference-identity submode command fail to resolve, the connection is terminated The reference-identity CLI is configured as a submode command for aaa-server host configuration and ddns configuration. New/Modified screens: |
||
|
Administrative, Monitoring, and Troubleshooting Features |
|||
|
Multiple DNS server groups |
You can now use multiple DNS server groups: one group is the default, while other groups can be associated with specific domains. A DNS request that matches a domain associated with a DNS server group will use that group. For example, if you want traffic destined to inside eng.cisco.com servers to use an inside DNS server, you can map eng.cisco.com to an inside DNS group. All DNS requests that do not match a domain mapping will use the default DNS server group, which has no associated domains. For example, the DefaultDNS group can include a public DNS server available on the outside interface. New/Modified screens: |
||
|
Dynamic Logging Rate-limit |
A new option to limit logging rate when block usage exceeds a specified threshold value was added. It dynamically limits the logging rate as the rate limiting is disabled when the block usage returns to normal value. New/Modified screens: |
||
|
Packet Capture for Secure Firewall 3100 devices |
The provision to capture switch packets was added. This option can be enabled only for Secure Firewall 3100 devices. New/Modified screens: |
||
|
VPN Features |
|||
|
IPsec flow offload. |
On the Secure Firewall 3100, IPsec flows are offloaded by default. After the initial setup of an IPsec site-to-site VPN or remote access VPN security association (SA), IPsec connections are offloaded to the field-programmable gate array (FPGA) in the device, which should improve device performance. New/Modified screens: |
||
|
Certificate and SAML for Authentication |
You can configure remote access VPN connection profiles for certificate and SAML authentication. Users can configure VPN settings to authenticate a machine certificate or user certificate before a SAML authentication/authorization is initiated. This can be done using DAP certificate attributes along with user specific SAML DAP attributes. New/Modified screens: |
||
Upgrade the Software
This section provides the upgrade path information and a link to complete your upgrade.
Upgrade Link
To complete your upgrade, see the ASA upgrade guide.
Upgrade Path: ASA Appliances
On the Cisco Support & Download site, the suggested release is marked with a gold star. For example:

View Your Current Version
To view your current version and model, use one of the following methods:
-
ASDM: Choose .
-
CLI: Use the show version command.
Upgrade Guidelines
Be sure to check the upgrade guidelines for each release between your starting version and your ending version. You may need to change your configuration before upgrading in some cases, or else you could experience an outage.
For guidance on security issues on the ASA, and which releases contain fixes for each issue, see the ASA Security Advisories.
Upgrade Paths
This table provides upgrade paths for ASA.
 Note |
ASA 9.16 was the final version for the ASA 5506-X, 5508-X, and 5516-X. ASA 9.14 was the final version for the ASA 5525-X, 5545-X, and 5555-X. ASA 9.12 was the final version for the ASA 5512-X, 5515-X, 5585-X, and ASASM. ASA 9.2 was the final version for the ASA 5505. ASA 9.1 was the final version for the ASA 5510, 5520, 5540, 5550, and 5580. |
|
Current Version |
Interim Upgrade Version |
Target Version |
|---|---|---|
|
9.17 |
— |
Any of the following: → 9.18 |
|
9.16 |
— |
Any of the following: → 9.18 → 9.17 |
|
9.15 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 |
|
9.14 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 |
|
9.13 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 |
|
9.12 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 |
|
9.10 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.12 |
|
9.9 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.12 |
|
9.8 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.12 |
|
9.7 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.12 |
|
9.6 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.12 |
|
9.5 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.12 |
|
9.4 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.12 |
|
9.3 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.12 |
|
9.2 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.12 |
|
9.1(2), 9.1(3), 9.1(4), 9.1(5), 9.1(6), or 9.1(7.4) |
— |
Any of the following: → 9.12 |
|
9.0(2), 9.0(3), or 9.0(4) |
— |
Any of the following: → 9.12 |
Upgrade Path: ASA on Firepower 2100 in Platform Mode
To view your current version and model, use one of the following methods:
-
ASDM: Choose .
-
CLI: Use the show version command.
This table provides upgrade paths for the ASA on the Firepower 2100 in Platform mode. Some versions require an intermediate upgrade before you can upgrade to a newer version. Recommended versions are in bold.
Be sure to check the upgrade guidelines for each release between your starting version and your ending version. You may need to change your configuration before upgrading in some cases, or else you could experience an outage.
For guidance on security issues on the ASA, and which releases contain fixes for each issue, see the ASA Security Advisories.
|
Current Version |
Interim Upgrade Version |
Target Version |
|---|---|---|
|
9.17 |
— |
Any of the following: → 9.18 |
|
9.16 |
— |
Any of the following: → 9.18 → 9.17 |
|
9.15 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 |
|
9.14 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.15 |
|
9.13 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.15 → 9.14 |
|
9.12 |
— |
Any of the following: → 9.18 → 9.17 → 9.16 → 9.15 → 9.14 |
|
9.10 |
→ 9.17 |
Any of the following: → 9.18 |
|
9.10 |
— |
Any of the following: → 9.17 → 9.16 → 9.15 → 9.14 → 9.12 |
|
9.9 |
→ 9.17 |
Any of the following: → 9.18 |
|
9.9 |
— |
Any of the following: → 9.17 → 9.16 → 9.15 → 9.14 → 9.12 |
|
9.8 |
→ 9.17 |
Any of the following: → 9.18 |
|
9.8 |
— |
Any of the following: → 9.17 → 9.16 → 9.15 → 9.14 → 9.12 |
Upgrade Path: ASA Logical Devices for the Firepower 4100/9300
-
FXOS: From FXOS 2.2.2 and later, you can upgrade directly to any higher version. (FXOS 2.0.1–2.2.1 can upgrade as far as 2.8.1. For versions earlier than 2.0.1, you need to upgrade to each intermediate version.) Note that you cannot upgrade FXOS to a version that does not support your current logical device version. You will need to upgrade in steps: upgrade FXOS to the highest version that supports your current logical device; then upgrade your logical device to the highest version supported with that FXOS version. For example, if you want to upgrade from FXOS 2.2/ASA 9.8 to FXOS 2.13/ASA 9.19, you would have to perform the following upgrades:
-
FXOS 2.2 → FXOS 2.11 (the highest version that supports 9.8)
-
ASA 9.8 → ASA 9.17 (the highest version supported by 2.11)
-
FXOS 2.11 → FXOS 2.13
-
ASA 9.17 → ASA 9.19
-
-
Firewall Threat Defense: Interim upgrades may be required for Firewall Threat Defense, in addition to the FXOS requirements above. For the exact upgrade path, refer to the Firewall Management Center upgrade guide for your version.
-
ASA: ASA lets you upgrade directly from your current version to any higher version, noting the FXOS requirements above.
|
FXOS Version |
Model |
ASA Version |
Firewall Threat Defense Version |
||||
|---|---|---|---|---|---|---|---|
|
2.16 |
Firepower 4112 |
9.18 9.17 |
7.6 (recommended) 7.4 7.3 7.2 7.1 |
||||
|
Firepower 4145 Firepower 4125 Firepower 4115 |
9.18 9.17 |
7.6 (recommended) 7.4 7.3 7.2 7.1 |
|||||
|
Firepower 9300 SM-56 Firepower 9300 SM-48 Firepower 9300 SM-40 |
|||||||
|
2.14(1) |
Firepower 4112 |
9.18 9.17 9.16 9.14 |
7.4 (recommended) 7.3 7.2 7.1 7.0 6.6 |
||||
|
Firepower 4145 Firepower 4125 Firepower 4115 |
9.18 9.17 9.16 9.14 |
7.4 (recommended) 7.3 7.2 7.1 7.0 6.6 |
|||||
|
Firepower 9300 SM-56 Firepower 9300 SM-48 Firepower 9300 SM-40 |
|||||||
|
2.13 |
Firepower 4112 |
9.18 9.17 9.16 9.14 |
7.3 (recommended) 7.2 7.1 7.0 6.6 |
||||
|
Firepower 4145 Firepower 4125 Firepower 4115 |
9.18 9.17 9.16 9.14 |
7.3 (recommended) 7.2 7.1 7.0 6.6 |
|||||
|
Firepower 9300 SM-56 Firepower 9300 SM-48 Firepower 9300 SM-40 |
|||||||
|
2.12 |
Firepower 4112 |
9.18 (recommended) 9.17 9.16 9.14 |
7.2 (recommended) 7.1 7.0 6.6 |
||||
|
Firepower 4145 Firepower 4125 Firepower 4115 |
9.18 (recommended) 9.17 9.16 9.14 9.12 |
7.2 (recommended) 7.1 7.0 6.6 6.4 |
|||||
|
Firepower 9300 SM-56 Firepower 9300 SM-48 Firepower 9300 SM-40 |
|||||||
|
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.18 (recommended) 9.17 9.16 9.14 9.12 |
7.2 (recommended) 7.1 7.0 6.6 6.4 |
|||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
|||||||
|
2.11 |
Firepower 4112 |
9.17 (recommended) 9.16 9.14 |
7.1 (recommended) 7.0 6.6 |
||||
|
Firepower 4145 Firepower 4125 Firepower 4115 |
9.17 (recommended) 9.16 9.14 9.12 |
7.1 (recommended) 7.0 6.6 6.4 |
|||||
|
Firepower 9300 SM-56 Firepower 9300 SM-48 Firepower 9300 SM-40 |
|||||||
|
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.17 (recommended) 9.16 9.14 9.12 9.8 |
7.1 (recommended) 7.0 6.6 6.4 |
|||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
|||||||
|
2.10
|
Firepower 4112 |
9.16 (recommended) 9.14 |
7.0 (recommended) 6.6 |
||||
|
Firepower 4145 Firepower 4125 Firepower 4115 |
9.16 (recommended) 9.14 9.12 |
7.0 (recommended) 6.6 6.4 |
|||||
|
Firepower 9300 SM-56 Firepower 9300 SM-48 Firepower 9300 SM-40 |
|||||||
|
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.16 (recommended) 9.14 9.12 9.8 |
7.0 (recommended) 6.6 6.4 |
|||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
|||||||
|
2.9 |
Firepower 4112 |
9.14 |
6.6 |
||||
|
Firepower 4145 Firepower 4125 Firepower 4115 |
9.14 9.12 |
6.6 6.4 |
|||||
|
Firepower 9300 SM-56 Firepower 9300 SM-48 Firepower 9300 SM-40 |
|||||||
|
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.14 9.12 9.8 |
6.6 6.4 |
|||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
|||||||
|
2.8 |
Firepower 4112 |
9.14 |
6.6
|
||||
|
Firepower 4145 Firepower 4125 Firepower 4115 |
9.14 (recommended) 9.12
|
6.6 (recommended)
6.4 |
|||||
|
Firepower 9300 SM-56 Firepower 9300 SM-48 Firepower 9300 SM-40 |
|||||||
|
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.14 (recommended) 9.12 9.8 |
6.6 (recommended)
6.4 6.2.3 |
|||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
|||||||
|
2.6(1.157)
|
Firepower 4145 Firepower 4125 Firepower 4115 |
9.12
|
6.4 |
||||
|
Firepower 9300 SM-56 Firepower 9300 SM-48 Firepower 9300 SM-40 |
|||||||
|
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.12 (recommended) 9.8 |
6.4 (recommended) 6.2.3 |
|||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
|||||||
|
2.6(1.131) |
Firepower 9300 SM-48 Firepower 9300 SM-40 |
9.12 |
Not supported |
||||
|
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.12 (recommended) 9.8 |
||||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
|||||||
|
2.3(1.73) |
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.8
|
6.2.3 (recommended)
|
||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
|||||||
|
2.3(1.66) 2.3(1.58) |
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.8
|
|||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
|||||||
|
2.2 |
Firepower 4150 Firepower 4140 Firepower 4120 Firepower 4110 |
9.8 |
Firewall Threat Defense versions are EoL |
||||
|
Firepower 9300 SM-44 Firepower 9300 SM-36 Firepower 9300 SM-24 |
Note on Downgrades
Downgrade of FXOS images is not officially supported. The only Cisco-supported method of downgrading an image version of FXOS is to perform a complete re-image of the device.
Open and Resolved Bugs
The open and resolved bugs for this release are accessible through the Cisco Bug Search Tool. This web-based tool provides you with access to the Cisco bug tracking system, which maintains information about bugs and vulnerabilities in this product and other Cisco hardware and software products.
 Note |
You must have a Cisco.com account to log in and access the Cisco Bug Search Tool. If you do not have one, you can register for an account. If you do not have a Cisco support contract, you can only look up bugs by ID; you cannot run searches. |
For more information about the Cisco Bug Search Tool, see the Bug Search Tool Help & FAQ.
Open Bugs
This section lists open bugs in each version.
Open Bugs in Version 7.18(1.161)
The following table lists select open bugs at the time of this Release Note publication.
|
Identifier |
Headline |
|---|---|
|
Appliance mode : checksum does not match issue while downloading asa image from CCO |
|
|
Cipher changes require in VPN wizard according to 9161/7161 CLIs |
Open Bugs in Version 7.18(1.152)
The following table lists select open bugs at the time of this Release Note publication.
|
Identifier |
Headline |
|---|---|
|
Appliance mode : checksum does not match issue while downloading asa image from CCO |
|
|
Cipher changes require in VPN wizard according to 9161/7161 CLIs |
Open Bugs in Version 7.18(1)
The following table lists select open bugs at the time of this Release Note publication.
|
Identifier |
Headline |
|---|---|
|
Appliance mode : checksum does not match issue while downloading asa image from CCO |
|
|
Cipher changes require in VPN wizard according to 9161/7161 CLIs |
Resolved Bugs
This section lists resolved bugs per release.
Resolved Bugs in Version 7.18(1.161)
The following table lists select resolved bugs at the time of this Release Note publication.
|
Identifier |
Headline |
|---|---|
|
ASDM initial connection/load time increased |
|
|
ASDM will delete all class-map configuration due delete class-map ACL that configured from CLI |
|
|
"Where used" option in ASDM not working |
|
|
Unable to update hostscan file from ASDM ,Unable to edit the DAP if we install hostscan image |
|
|
Unable to Edit the ACL objects if it is already in use, getting the exception. |
|
|
ASDM Fails to Launch with security exception error - invalid SHA1 signature file |
Resolved Bugs in Version 7.18(1.152)
The following table lists select resolved bugs at the time of this Release Note publication.
|
Identifier |
Headline |
|---|---|
|
Cisco Adaptive Security Device Manager Remote Code Execution Vulnerability |
|
|
Cisco ASDM and ASA Software Client-side Arbitrary Code Execution Vulnerability |
Resolved Bugs in Version 7.18(1)
The following table lists select resolved bugs at the time of this Release Note publication.
|
Identifier |
Headline |
|---|---|
|
Check box not available for disable delete tunnel with no delay in simultaneous connection prempt |
|
|
Hostscan 4.3.x to 4.6.x Migration steps should not be display when the SDM have the HS 4.10.x |
|
|
"load balancing" item is not displayed on ASDM. |
|
|
ASDM: Transforms file name must start with "_" underscore to take effect to multiple AC modules |
|
|
Unable to restrict user access when using ASDM |
|
|
ASDM session/quota count mismatch in ASA when multiple context switchover is done from ASDM |
|
|
ASDM side changes for the ASA #CSCvz89126 |
|
|
ASDM on MAC popup remove hostscan/CSD pkg |
|
|
ASDM:DAP config missing AAA Attributes type (Radius/LDAP) |
|
|
Evaluation OpenJDK CVEs for ASDM & ASA REST API |
Cisco General Terms
The Cisco General Terms (including other related terms) governs the use of Cisco software. You can request a physical copy from Cisco Systems, Inc., P.O. Box 641387, San Jose, CA 95164-1387. Non-Cisco software purchased from Cisco is subject to applicable vendor license terms. See also: https://cisco.com/go/generalterms.
Related Documentation
For additional information on the ASA, see Navigating the Cisco Secure Firewall ASA Series Documentation.
 Feedback
Feedback