Dot1x Supplicant Support on the L2 interface
Feature is new for release 15.8(3)M1 and applies to the IR829 only
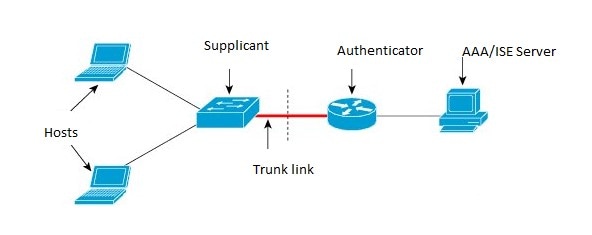
IEEE 802.1X authentication enables the access point to gain access to a secured wired network. You can enable the access point as an 802.1X supplicant (client) on the wired network. A user name and password that are encrypted using the MD5 (IR8x9 platform supports only md5 method) algorithm can be configured to allow the access point to authenticate using 802.1X. Supplicant Topology illustrates the Supplicant Topology.
Supplicant CLI Commands
#IR800-supplicant(config-eap-profile)?
Eap profile configuration commands:
description Provide a description for the EAP profile
exit Exit EAP profiles configuration submode
method Add an allowed method
no Negate a command or set its defaults
#IR800-supplicant(config-eap-profile)method ?
md5 EAP-MD5 method allowed
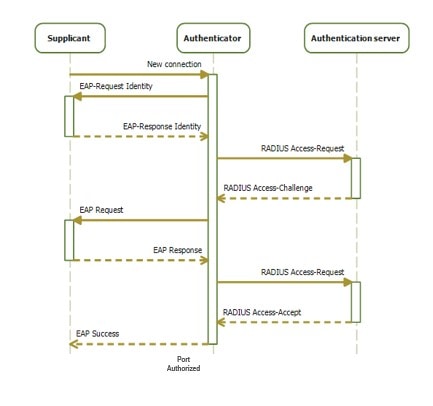
Refer to Workflow for the workflow.
Workflow details
-
On networks that use IEEE 802.1X port-based network access control, a supplicant cannot gain access to the network until the 802.1X authenticator grants access. If your network uses 802.1X, you must configure 802.1X authentication information on the WAP device, so that it can supply it to the authenticator.
-
Supplicant starts with EAPOL start request to the Authenticator
-
In Supplicant Request Authenticator send EAP request to supplicant
-
Supplicant sends the EAP response (W/MD5 Credentials) to Authenticator
-
Authenticator sends the relay request to AAA via radius to Authenticate the supplicants
-
If the supplicant entry is already defined there, Radius sends accept to the Authenticator and the Supplicant port gets authorized by the authenticator
-
Now the supplicant works as Authenticator for the host connected to it. The same flow happens when the host connects to the Supplicant.
Sample Configuration to Support DOT1x Supplicant on the IR829
 Note |
More details can be found here: |
https://www.cisco.com/c/en/us/support/docs/lan-switching/8021x/116681-config-neat-cise-00.html#anc14
! Enable supplicant switch to authenticate devices connected
dot1x system-auth-control
! Forces the switch to send only multicast EAPOL packets when it receives either
unicast or multicast packets, which allows NEAT to work on the supplicant
switch in all host modes.
dot1x supplicant force-multicast
! configure EAP mode used by supplicant switch to authenticate itself to authenticator switch eap profile EAP_PRO
method md5
! Configure credentials use by supplicant switch during that authentication.
dot1x credentials CRED_PRO
username bsnsswitch
password 0 C1sco123
The connection of the supplicant to the authenticator is already configured to be a trunk port (in contrast to access port configuration on the authenticator). At this stage, this is expected; configuration will dynamically change when the ISE returns the correct attribute.
interface FastEthernet0/6
switchport trunk encapsulation dot1q
switchport mode trunk
dot1x pae supplicant
dot1x credentials CRED_PRO
dot1x supplicant eap profile EAP_PRO
 Note |
For support of Dot1x in IR829 dot1x code is added in IR829 for L2 interface. |
IR800-supplicant# show dot1x interface gigabitEthernet 1 details
Dot1x Info for GigabitEthernet1
-----------------------------------
PAE = SUPPLICANT
StartPeriod = 30
AuthPeriod = 30
HeldPeriod = 60
MaxStart = 3
Credentials profile = CRED_PRO
EAP profile = EAP_PRO
Dot1x Supplicant Client List
-------------------------------
Authenticator = 80e0.1d66.2ce1
Supp SM State = AUTHENTICATED
Supp Bend SM State = IDLE
Port Status = AUTHORIZED
 Note |
Dot1x supplicant on L3 interfaces is not supported. |
 Feedback
Feedback