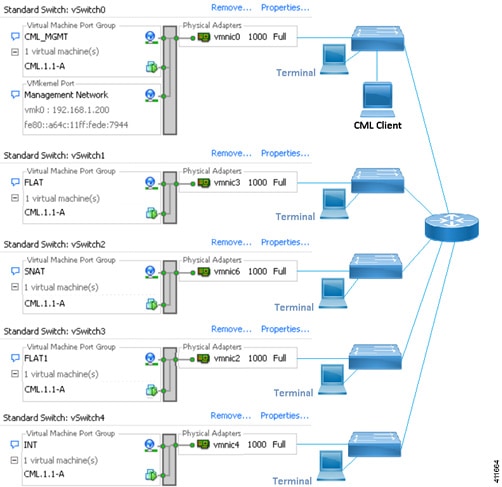
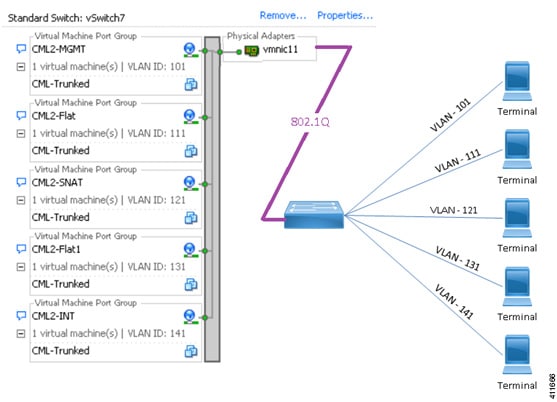
Cisco Modeling Labs Server Requirements
This section details the hardware and software requirements for installing the Cisco Modeling Labs server.
The following table lists hardware requirements that are based on the number of virtual nodes used.
| Requirement | Description |
|---|---|
| Disk Space | 500 GB minimum |
| Chip Set | Intel® with Intel virtualization technology VT-x and Extended Page Tables (EPT) |
| Hypervisor | VMware ESXi 5.1 U2, ESXi 5.5 U1, ESXi 6.0 (Build 3620759), ESXi 6.5 (Build 4564106) |
| Server type for OVA package | Any server with Intel virtualization technology VT-x and Extended Page Tables (EPT) |
| Server type for ISO package | Supported only on Cisco UCS® C220 M4 and C460 M4 with local storage |
| Server Recommendation | Cisco UCS C-Series |
For more information on UCS servers, see the applicable data sheets at http://www.cisco.com/c/en/us/products/servers-unified-computing/ucs-c-series-rack-servers/index.html.
For bare metal installations, Cisco Modeling Labs ISO package is certified only with the Cisco UCS C220 M4 servers.
Sizing the Server: Number of Cores and Memory Requirements
-
Type and number of virtual machines concurrently active
-
Number of routing protocols
-
Timer sets within the configurations
-
Amount of traffic generated
The general rule of thumb is three virtual nodes to one physical core CPU for simulation of 49 nodes and below, and two virtual nodes to one physical core CPU for 50 nodes and above.
 Note |
In order to size the Cisco Modeling Lab Server resources, you must use the Cisco Modeling Labs resource calculator available at http://www.cisco.com/go/cml |
| Requirement | Description | ||
|---|---|---|---|
| VMware | |||
| VMware vSphere | Any of the following:
|
||
| Browser | Any of the following:
|
|
Name |
Description |
||||
|---|---|---|---|---|---|
|
Intel Hyper-Threading Technology |
|
||||
|
Intel VT |
|
||||
|
Intel VT-d |
|
 Important |
Check that these server requirements are in place before proceeding to the next step in the installation process. |
 Feedback
Feedback