Meeting installation prerequisites
Cisco Crosswork Network Controller (CNC) Fleet Upgrade is a pre-built use case that enables users to manage, distribute, and commit software image upgrades on multiple network devices at the same time.
Fleet Upgrade is automated, usable out of the box, and provides strong error checking. It is customizable, extensible, and supports devices from Cisco and other vendors.
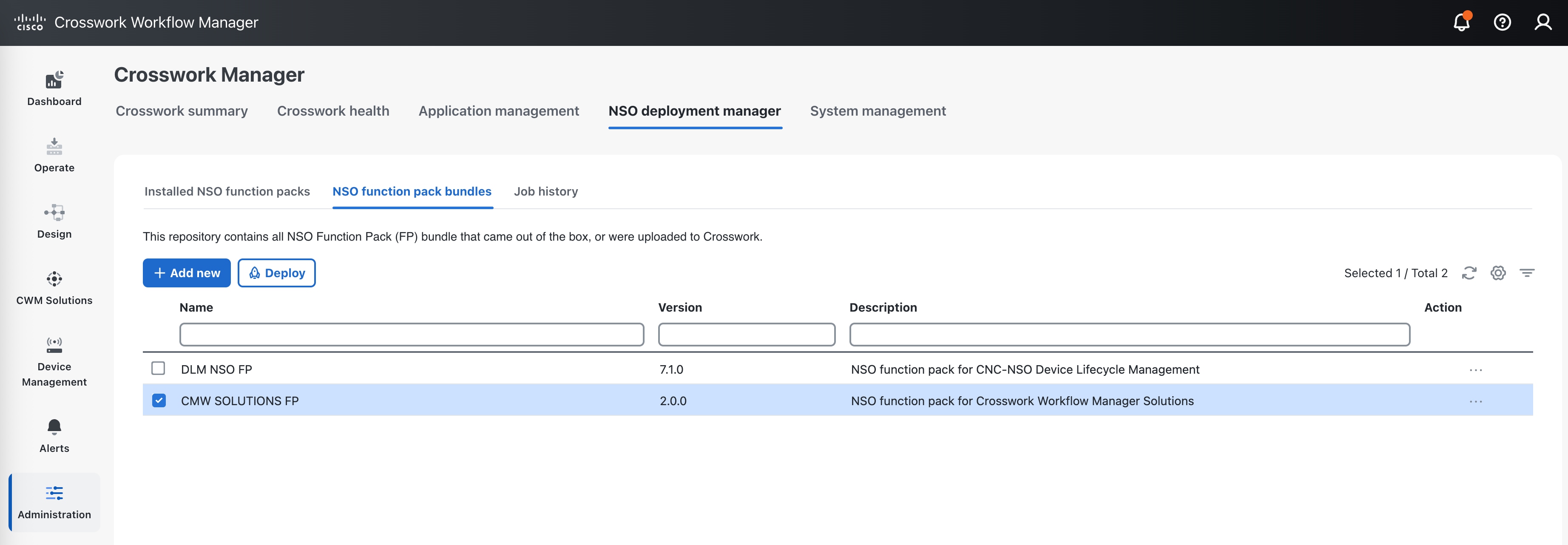
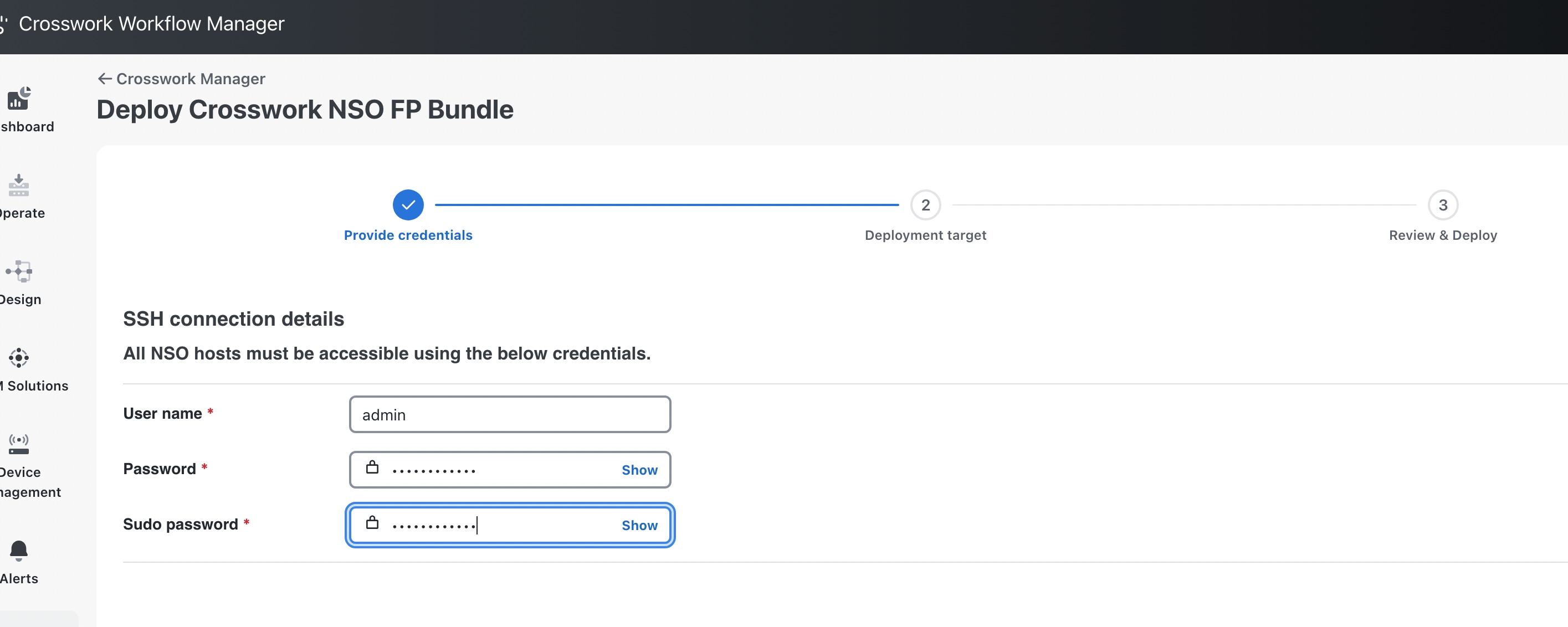
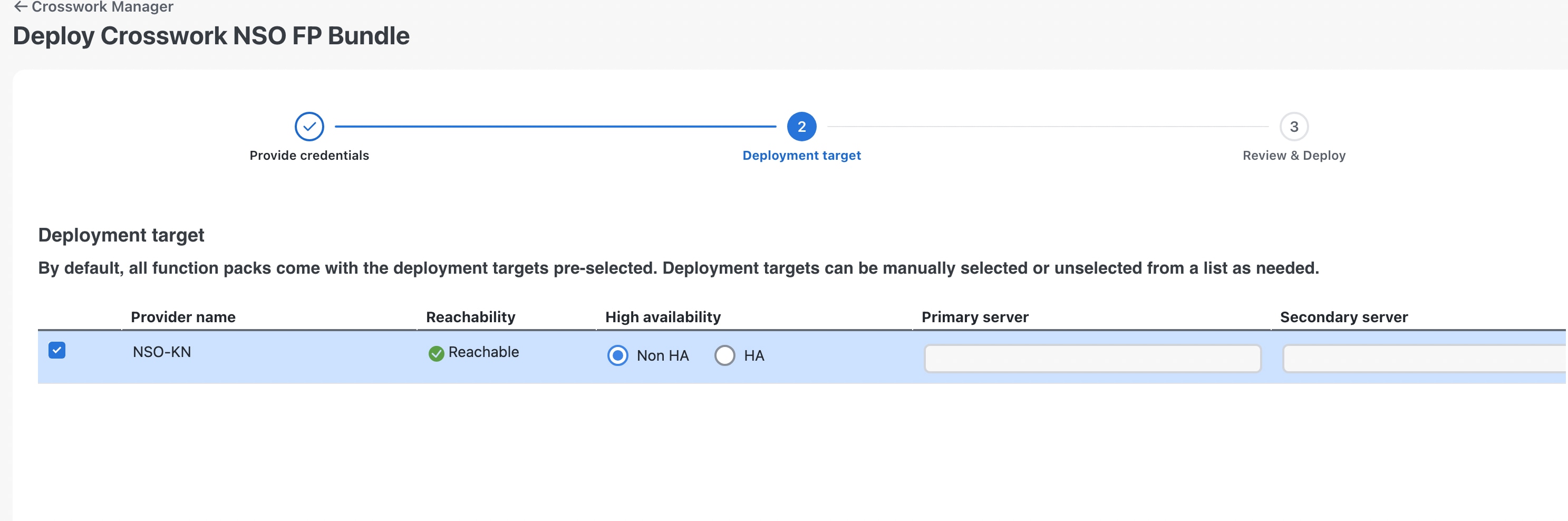
Installing Fleet Upgrade requires installation of Cisco Crosswork Network Controller (CNC), Crosswork Data Gateway (CDG), and Cisco Network Services Orchestrator (NSO). Fleet Upgrade leverages the capabilities of CNC Workflow Automation. By following the installation instructions in this document, you should be able to meet the additional hardware, software and other requirements detailed below. You will want to refer to this requirements as a checklist if you experience issues with your installation.
Server hardware
To install CNC Workflow Automation and Fleet Upgrade, you must install the CNC Premier Package on a server equipped with CNC cluster. Note that the requirements given in the table are for Cisco CNC installed in cluster deployments with the CNC Premier package.
As a general guideline, users should select high-specification computing hardware for Workflow Manager Solutions installations. Installation of the CNC OVA on VMware requires vCenter 8 and ESXi 8 hosts. Due to their high performance, solid state drives (SSDs) are preferred over traditional hard disk drives (HDDs). If you are using HDDs, their minimum speed should be over 15000 RPM. The VM data store(s) must have disk-access latency less than 10 ms or greater than 5000 IOPS.
| Component | Software form | Size | vCPUs | Memory | Disk (SSD) | Swap disk |
|---|---|---|---|---|---|---|
|
Cisco CNC Cluster 7.1.0 |
VMware vCenter or KVM VMs |
Minimum 3 hybrid + 2 worker nodes |
Varies with your choice of hypervisor. For details, see Cisco Crosswork Network Controller 7.1 Installation Guide topic, Identify the Resource Footprint. |
|||
| Cisco Workflow Manager 2.0 | OVA | XLarge profile | 24 | 128GB | 1TB | n/a |
| Cisco NSO 6.4.1 | Tar / signed binary | n/a | 16 | 256GB | 1TB | 256GB |
Server software
Fleet Upgrade runs on the following minimum versions of server software:
-
Cisco Crosswork Network Controller (CNC) 7.1 with Cisco Crosswork Data Gateway (CDG) 7.1
-
CNC Premier Package bundle cw-na-cncpremier-7.1.0-582-develop-250319.tar.gz
-
Cisco NSO version 6.4.1, with the following additional requirements:
-
The NSO installation must be a System install, NOT a Local install. For details on the distinction, see Ways to Deploy NSO.
-
Python 3.9 or later installed on the NSO host.
-
Python package textfsm installed on the NSO host.
-
Java 17 or later installed on the NSO host.
-
Ubuntu 22 or RHEL 8 installed on the NSO host.
-
NSO host ports open for 8080 or 8888 (HTTP/HTTPS for RESTCONF), and 20243 for Device Lifecycle Management.
-
Fleet Upgrade supported NOS and devices
The Fleet Upgrade workflow has been tested with and is known to work with the network operating systems and devices shown in the following table.
| Network OS | Device |
|
Cisco IOS-XR Versions: 7.8.2, 7.9.2, 7.10.1, 7.11.1, 24.1.1, 24.2.2 |
Cisco NCS 540, Cisco C8000 (VXR), ASR9903, NCS 5501, XR LNDT and eXR platforms |
|
Cisco IOS-XE Versions: IOS-XE 17.09, IOS-XE 17.12 |
ASR 1000 series, Catalyst 9000 series |
|
Juniper JunOS versions 18.1R1.9, 21.1R3.11 |
Juniper MX960 |
Additional requirements
Supported browsers: Google Chrome (Version 131.0.x or later) and Mozilla Firefox (134.0.1 or later). For full functionality, browsers must have JavaScript and cookies enabled.
Site preparation: The user network environment and additional requirements vary with your choice of CNC cluster hypervisor. For guidance, see:
 Note |
CNC Workflow Automation and Fleet Upgrade do not currently support installation using the AWS EC2 cluster hypervisor option. |
 Feedback
Feedback