Create and Use Third Party Certificate on UCSM
Available Languages
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
2.0 |
08-Jun-2023
|
Added Table of Contents and Related Information section
Updated Title, Introduction, Alt Text, Style Requirements, Machine Translation and Formatting. |
1.0 |
13-Aug-2018
|
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
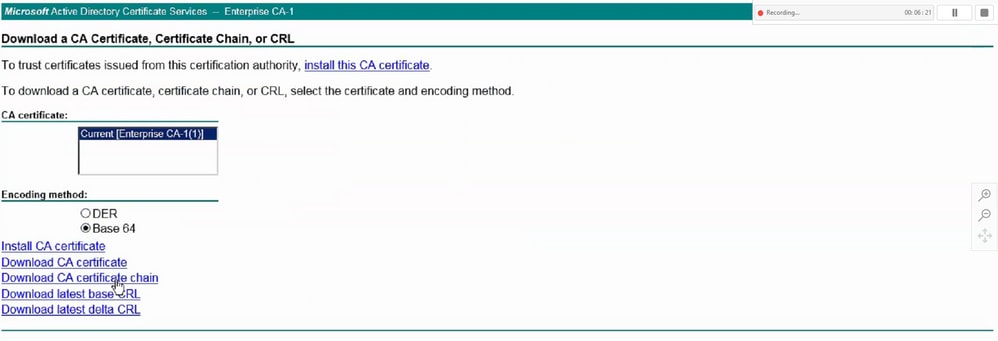
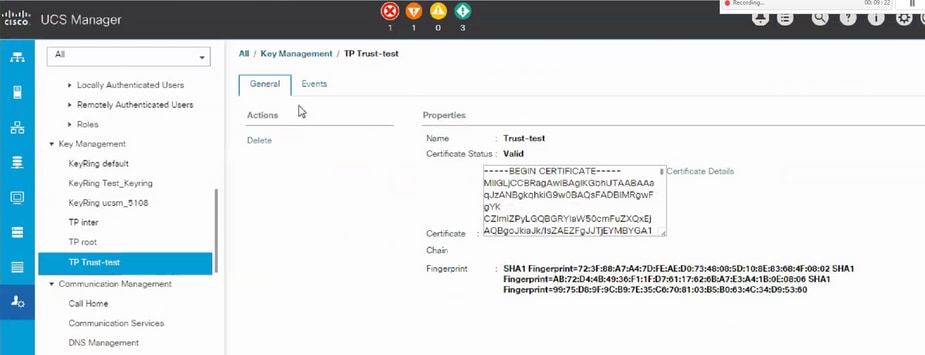
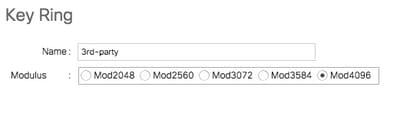

 Feedback
Feedback