Introduction
This document describes how to deploy the Security Connector using Intune.
Overview
This is a step-by-step guide on how to get your iOS/iPadOS device MDM-manage via Intune, and push the profile via Apple Configurator
You can also reference our Intune Registration documentation and PDF guide here
Note: this method shows you how to MDM your devices via Intune and Apple Configurator
Important Notes:
If you are MDM-ing your supervised devices via the Company Portal App, then you can start at Step 14.
This article is provided as-is as of 04/12/2023, Umbrella support does not guarantee these instructions will remain valid after this date and is subject to change based on updates from Microsoft Intune and Apple iOS.
Procedure
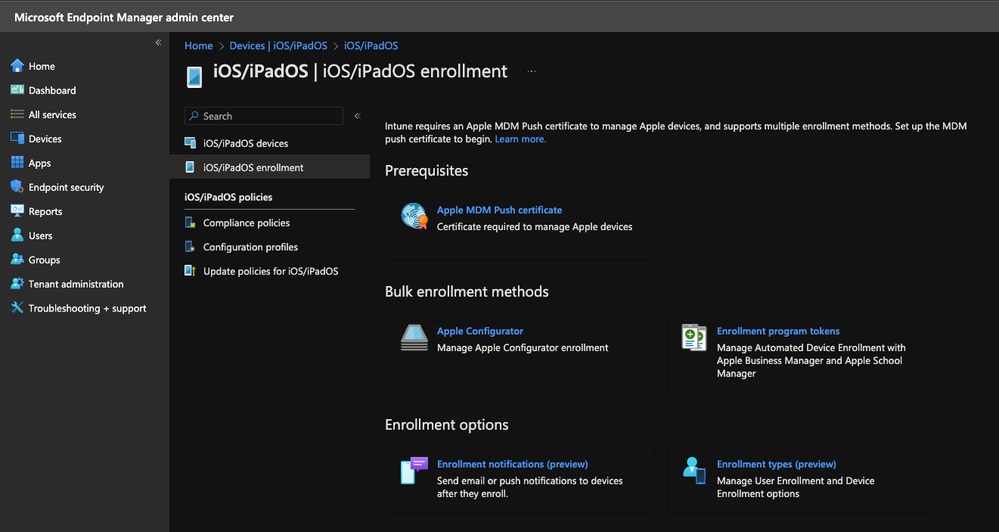
- Log into the Azure Portal and search for "Intune". Alternatively, go to https://intune.microsoft.com/Error/UE_404?aspxerrorpath=/ and login
- Once you are on the Intune homepage, go to Devices --> iOS/iPadOS --> iOS/iPadOS enrollment --> Apple MDM Push certificate and click "Download your CSR"
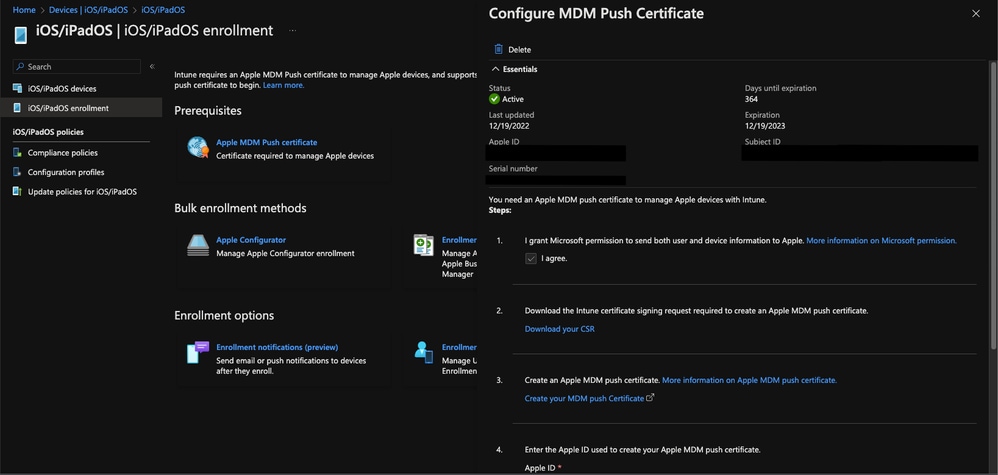 11752925317012
11752925317012
- Then, click on "Create your MDM push Certificate", which redirects you to https://identity.apple.com/pushcert/
- On the Apple Push Certificates Portal, go to "Create a Certificate" and upload the IntuneCSR.csr file you just downloaded. Once the CSR file has been uploaded successfully, click "Download" to download the Privacy Enhanced Mail (.pem file) and proceed to the next step
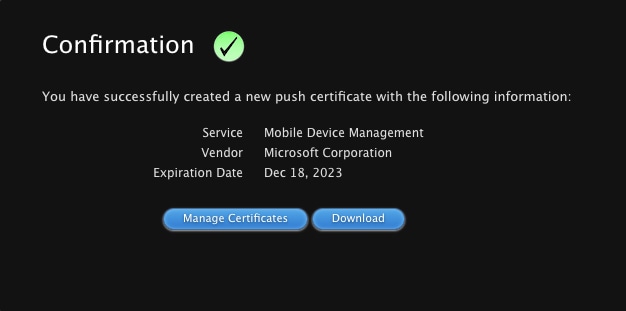 11752968667924
11752968667924
- Enter the email address of your Apple ID account that you used to sign into the Apple Push Certificates Portal and upload the .pem file under "Apple MDM push certificate" and press "Upload". If the upload is successful, you see the other options for the "Bulk enrollment methods" unlock.
 11752971407380
11752971407380
- Go to Apple Configurator --> Profiles --> Create and create a new profile. Give it a meaningful name and for User affinity select "Enroll without user affinity". Once that profile has been created, click into your newly created profile and select "Export Profile" and then "Download Profile" on the right hand side
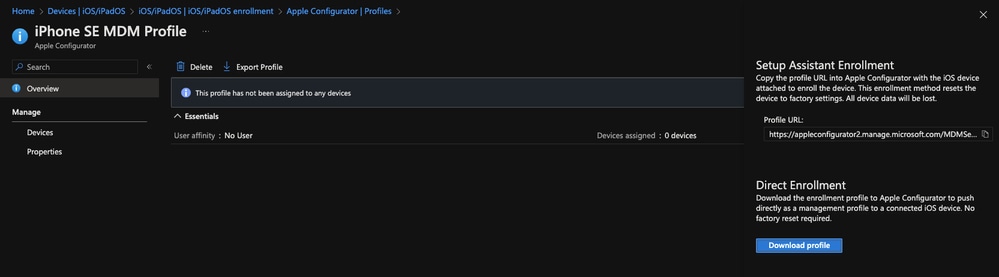 11753020728596
11753020728596
- Download and launch "Apple Configurator" on your macOS from the App Store and connect your phone via Lightning Cable. Right click on your device within Apple Configurator select Add --> Profiles and then select the profile.mobileconfig file you just downloaded
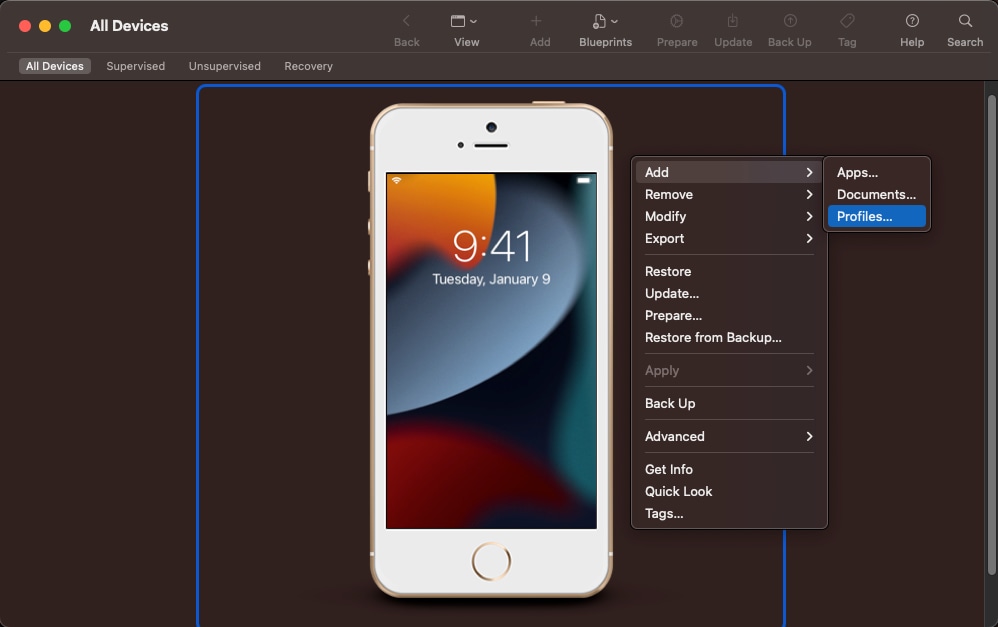 11753024446100
11753024446100
Windows alternate: iPhone Configuration Utility
- Once the sync has finished, on your iOS/iPadOS device go to Settings app and go to General --> VPN & Device Management --> Management Profile
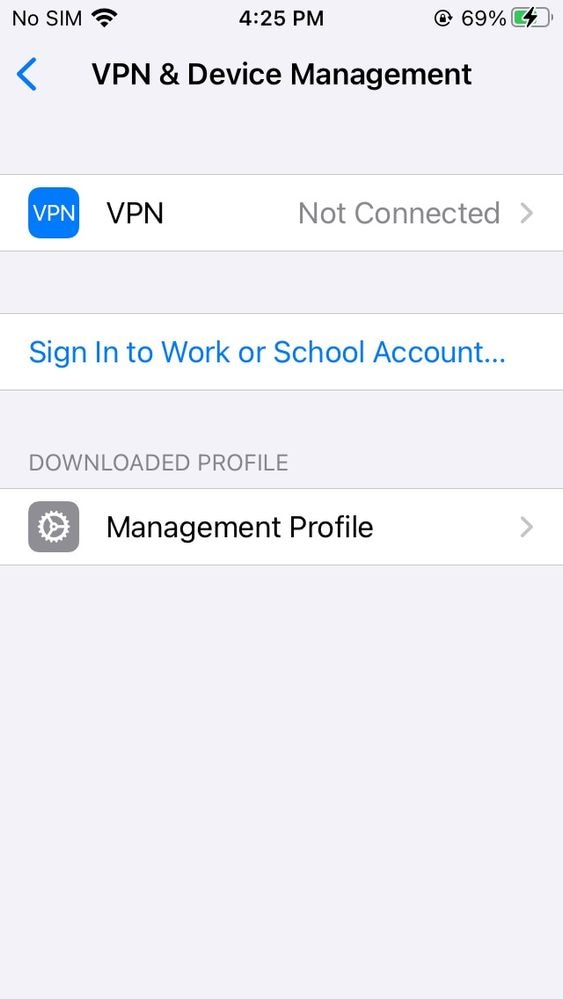 11753486730900
11753486730900
- On the top right, click Install
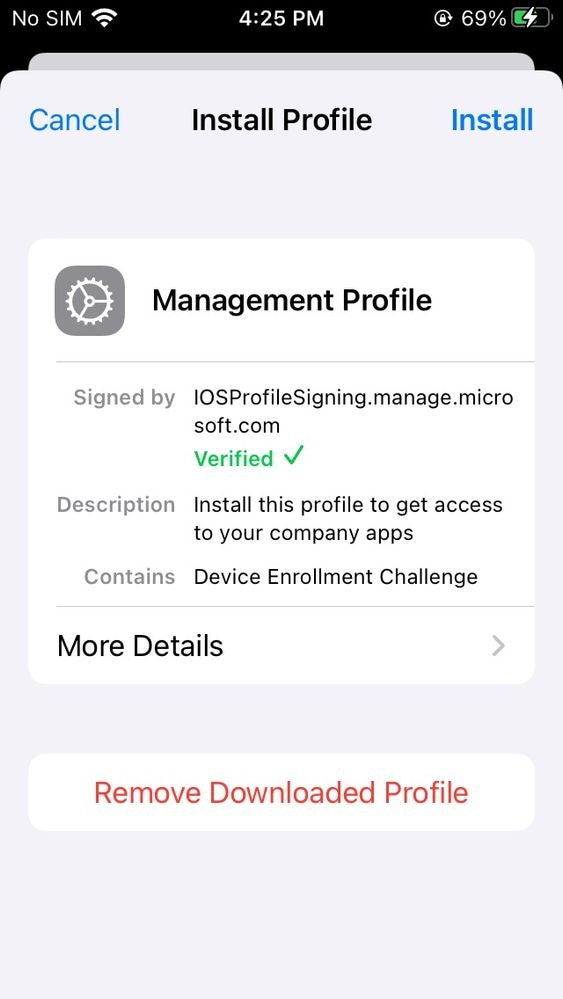 11753538844948
11753538844948
- If you get a Remote Management prompt, hit Trust and let the profile finish installing
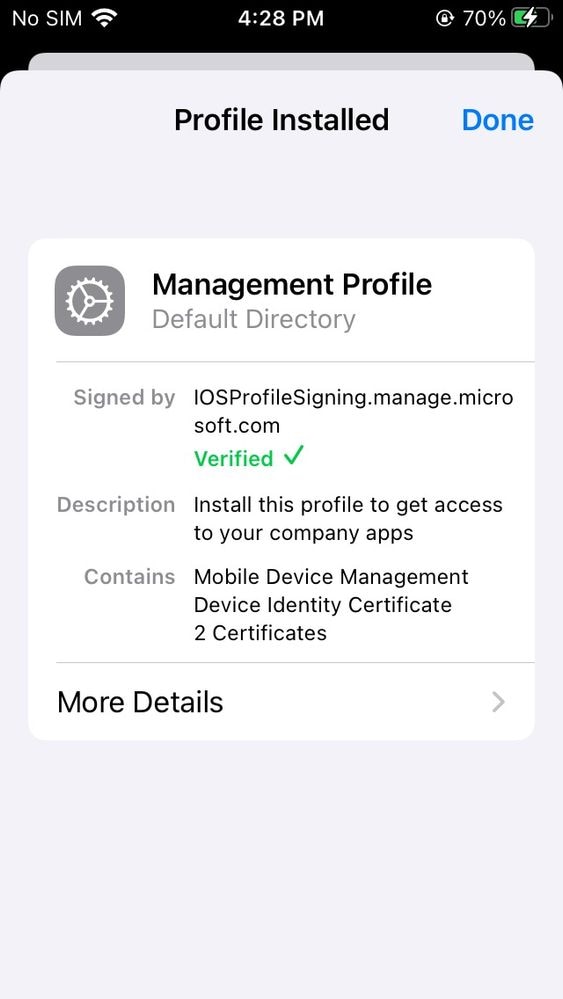 11753535457044
11753535457044
- To confirm the profile was exported and installed successfully on your iOS device, go back to Intune and under "Devices" you now see your new iOS device added
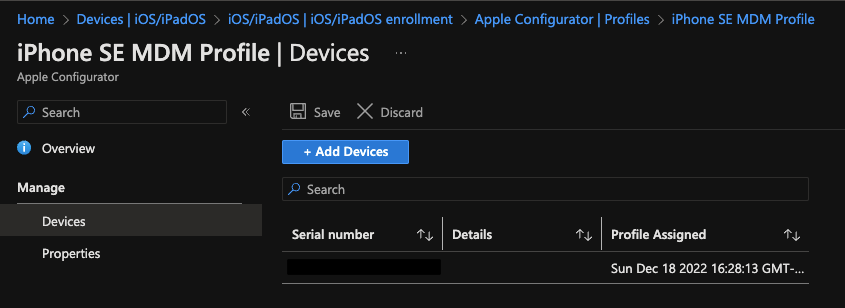 11753595983892
11753595983892
- Now that your device is MDM enrolled, go to Groups --> All Groups --> New Group and create a new group and assign your device. Make sure your Group type is "Security" and not Microsoft 365
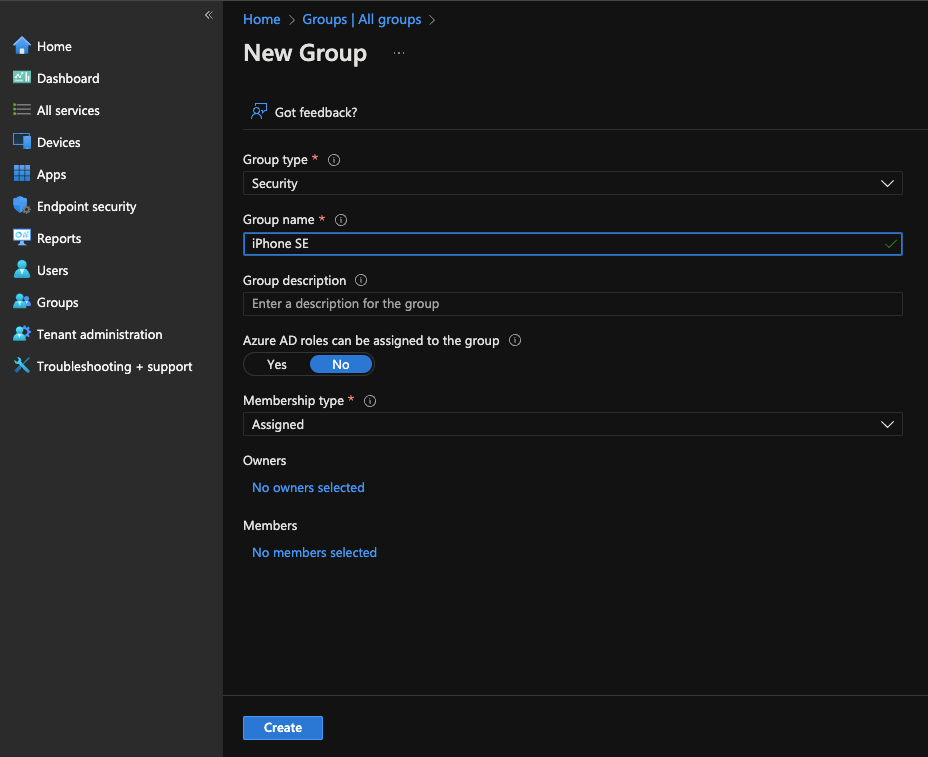 11753690347284
11753690347284
- Click into the group you have just created and go to Members --> Add Members. Find your MDM-device you want to install the Cisco Security Connector app on, on the list and add it to the group you have just created
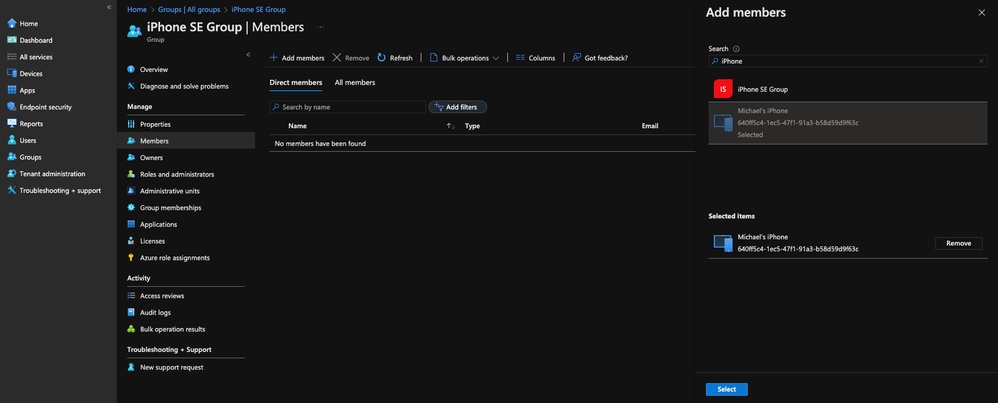 11753692550036
11753692550036
- Go to Apps --> All apps --> Add. Then for App type, select "iOS store app" and confirm by clicking "Select"
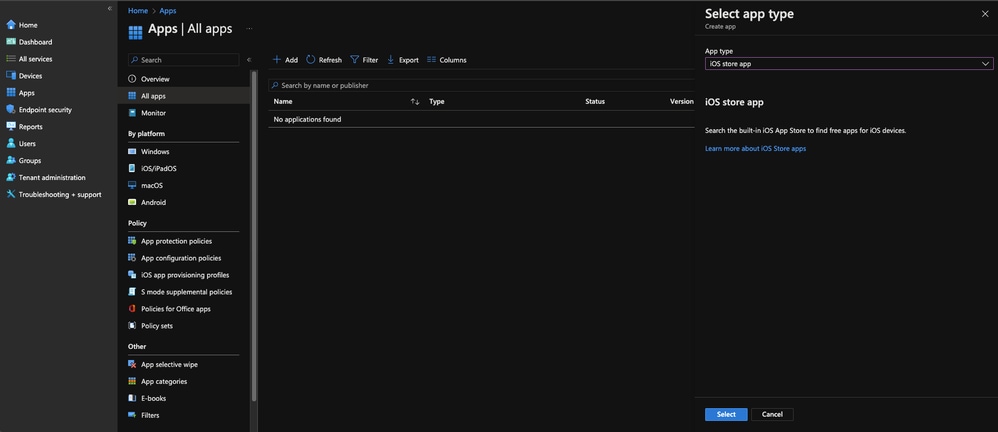 11753797372436
11753797372436
- Select "Search for App Store" and enter "Cisco Security Connector" in the search bar and select the "Cisco Security Connector" app by clicking "Select"
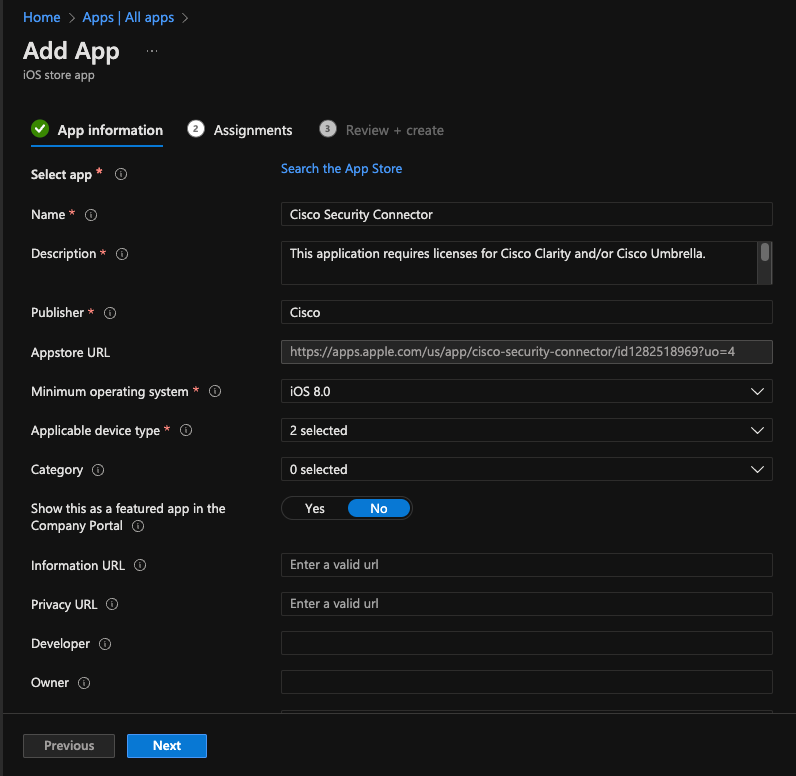 11753844054420
11753844054420
- Under Assignments, add the group you have created in the earlier steps which contains your MDM-device then proceed with Review and Create
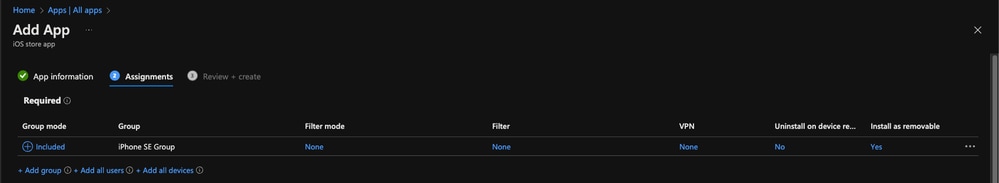 11753839516692
11753839516692
- [Optional step] Go to Devices --> iOS/iPadOS --> iOS/iPadOS devices --> Properties --> Device Category, create a profile and assign it to the device
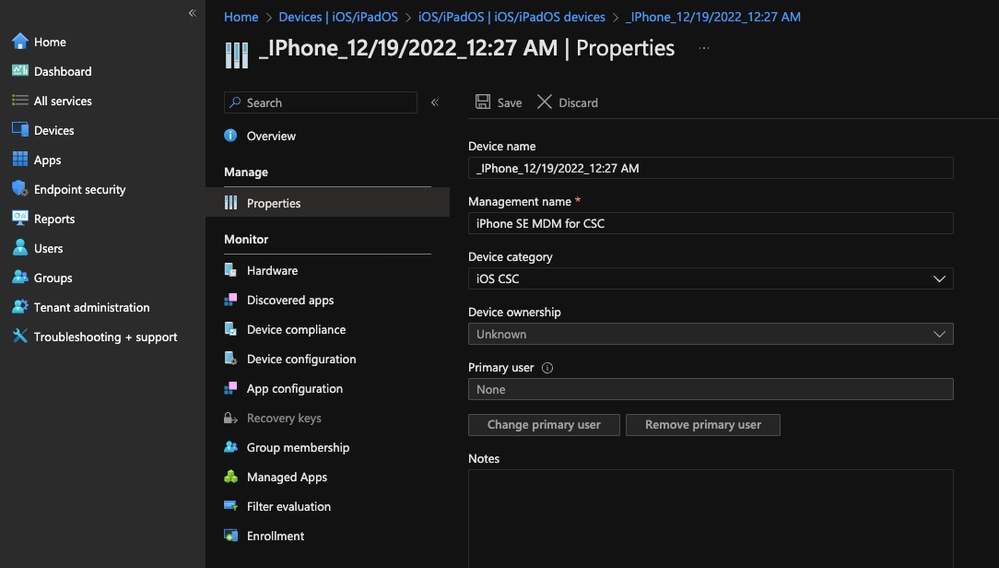 11753916236820
11753916236820
- Log into your Cisco Umbrella dashboard, under Deployments --> Core Identities --> Mobile Devices --> top right: Manage --> Managed by MDM
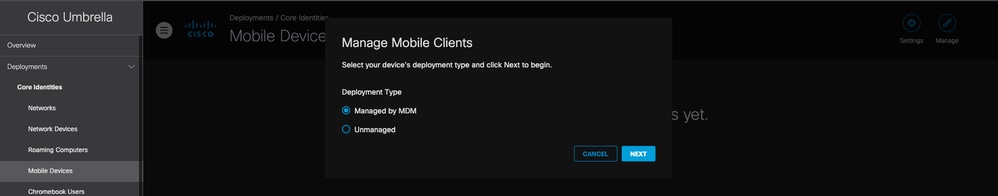 11753923081492
11753923081492
- Then go to iOS --> Microsoft Intune Config download. Enter your email address that you want emails to go to when users select "Report a problem" within the Cisco Security Connector app
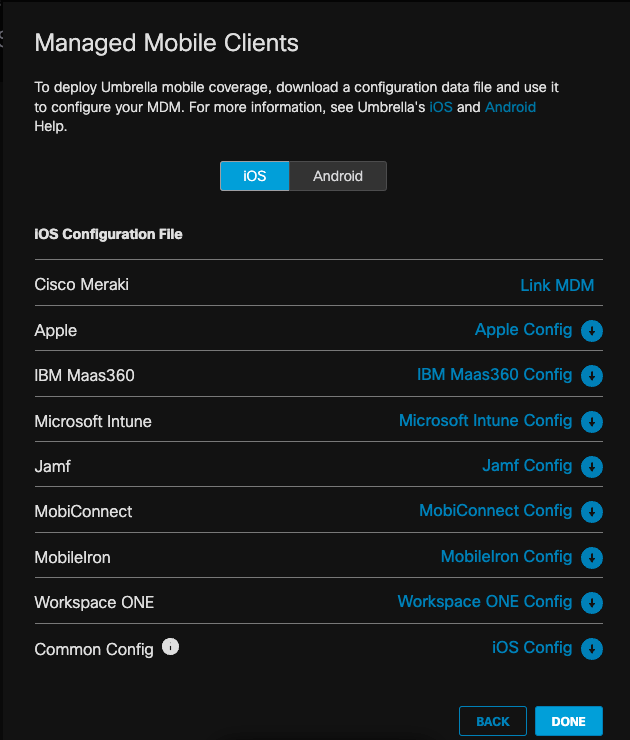 11753924523540
11753924523540
- Go back to your Intune portal, under Devices --> iOS/iPadOS --> Configuration Profiles --> Create Profile --> Templates --> Custom
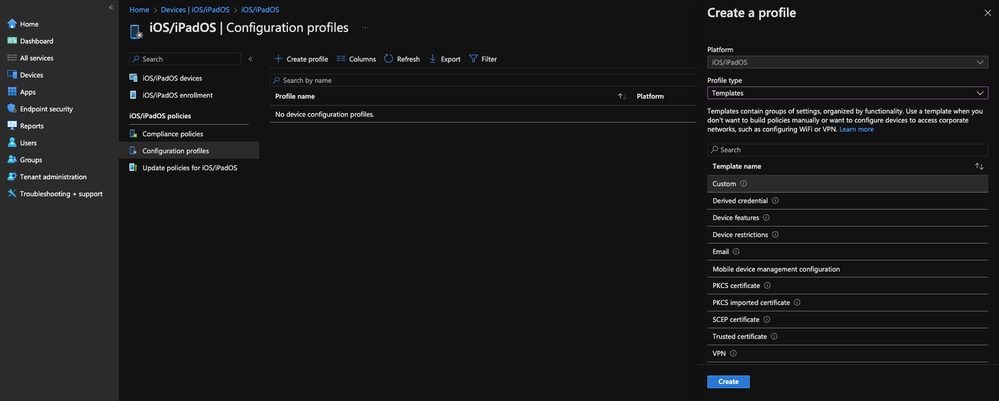 11753988354964
11753988354964
- Give it a meaningful name for your configuration profile. In Step 2 - Configuration settings, upload the XML file you have just downloaded from your Cisco Umbrella dashboard
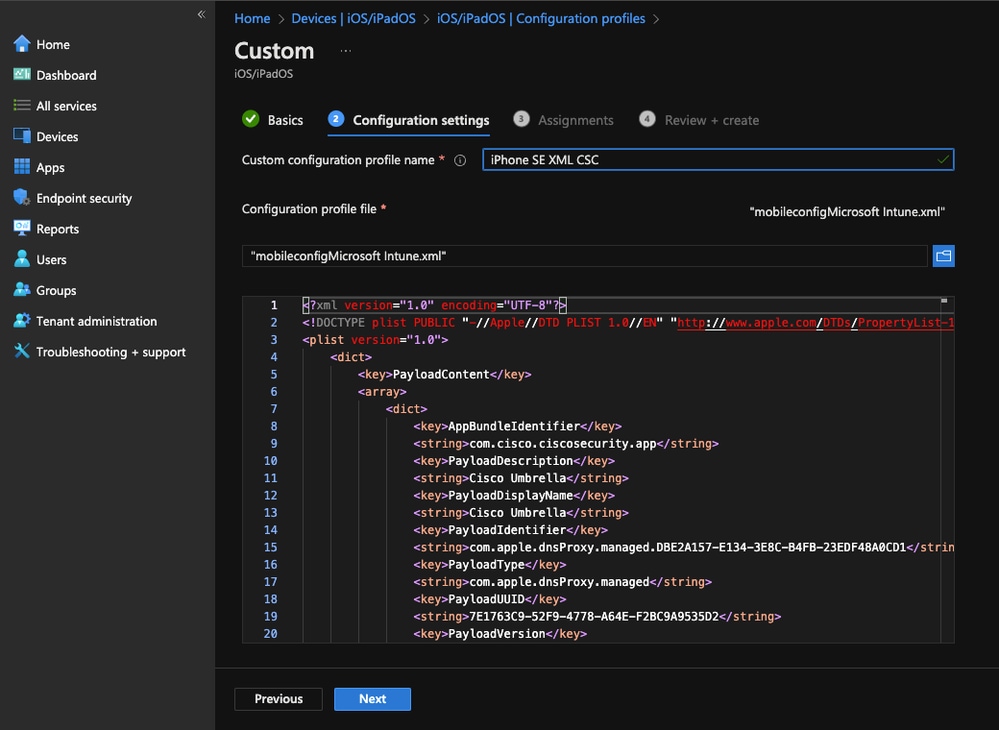 11754000962196
11754000962196
- Under Assignments, assign the group you have created earlier that contains your MDM-device and select "Review and Create"
- Go back to iOS/iPadOS devices and select your MDM-device and hit sync at the top and you get a pop-up on your MDM iOS/iPadOS device to install the Cisco Security Connector app
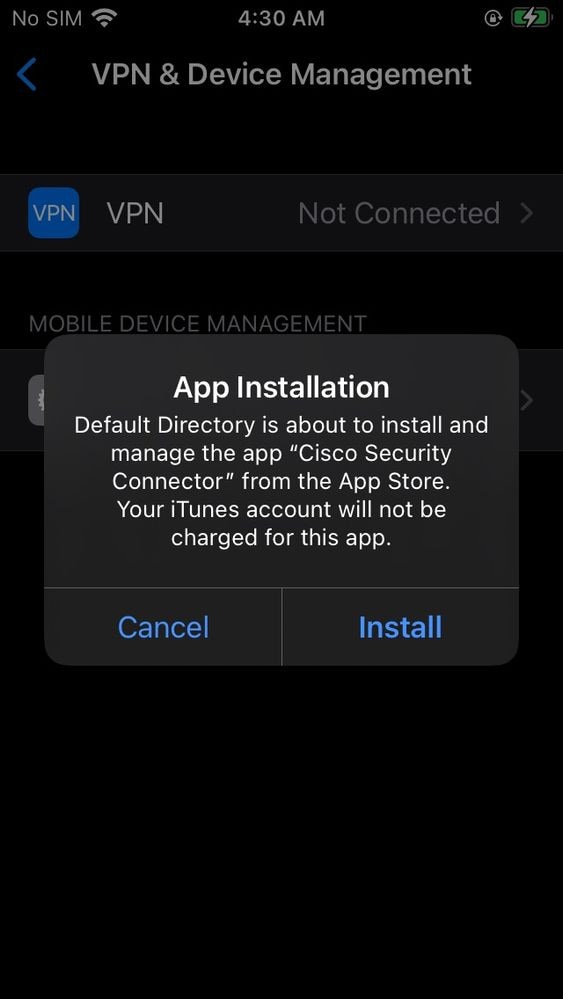 11754070231572
11754070231572
- Launch the Cisco Security Connector app on your iOS/iPadOS device. You might see the "Not Protected by Umbrella"
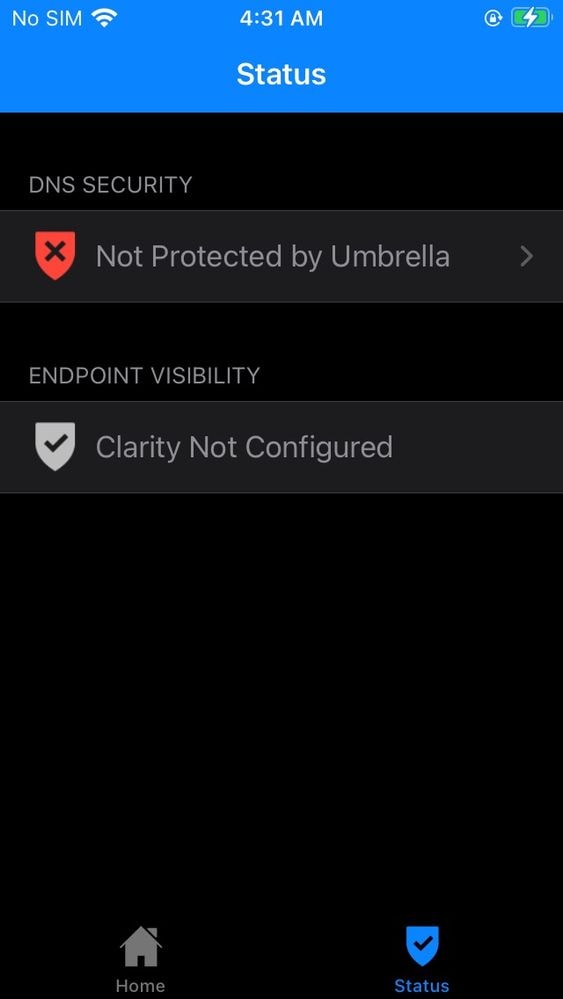 11754074006164
11754074006164
- When you click into it the IPv4 Status and IPv6 Status might show "Limited". You need to turn on/off your WiFi or LTE cellular network in order to see a status change. The next steps involves deploying the Cisco Umbrella Root Certificate - it is required in order for block pages to be properly displayed.
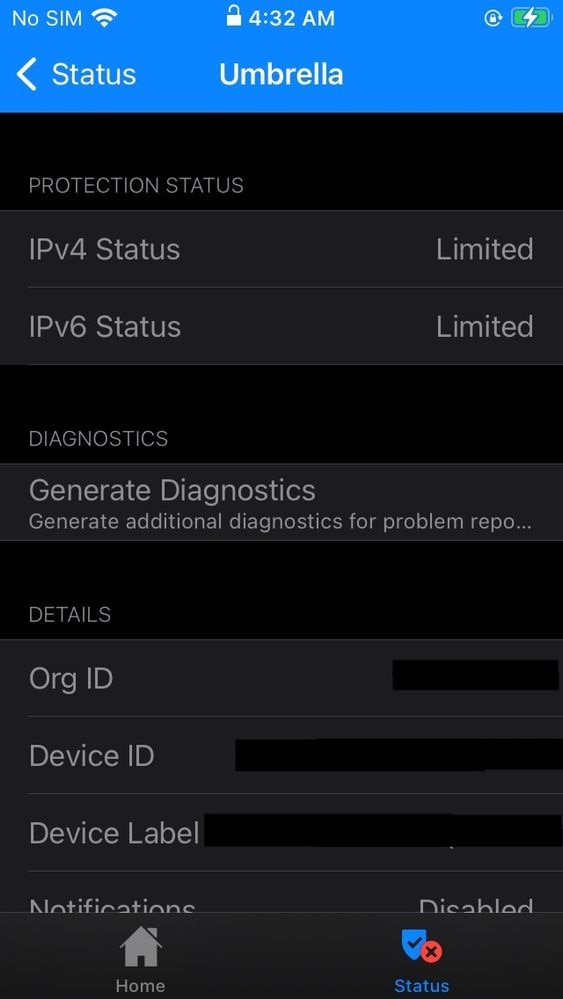 11754133161492
11754133161492
- Go to your Umbrella dashboard, under Deployments --> Root Certificate, download the Umbrella Root Certificate (.cer file)
- Go back to your Intune portal, under Devices --> iOS/iPadOS --> Configuration Profiles, create a new profile (just like in Step 21) for the Umbrella Root Certificate
- For "Profile type", select Templates --> Trusted certificate
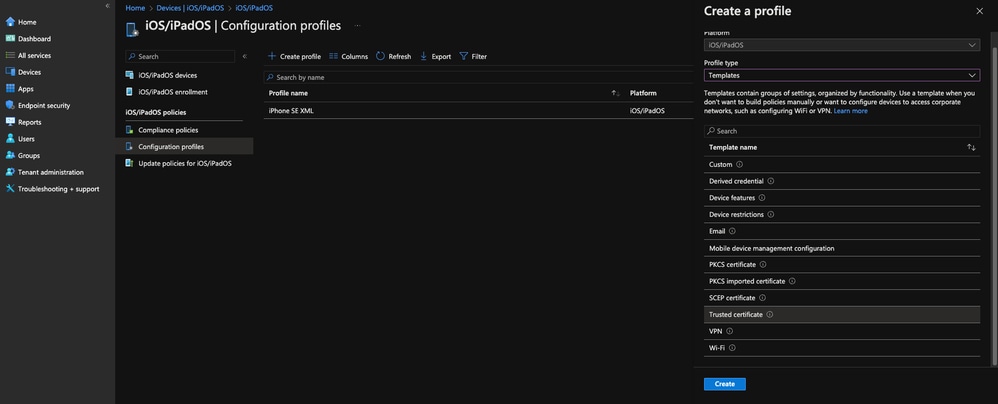 11754159037460
11754159037460
- In Step 2 - Configuration settings, upload the Umbrella Root Certificate you have just downloaded from Step 27
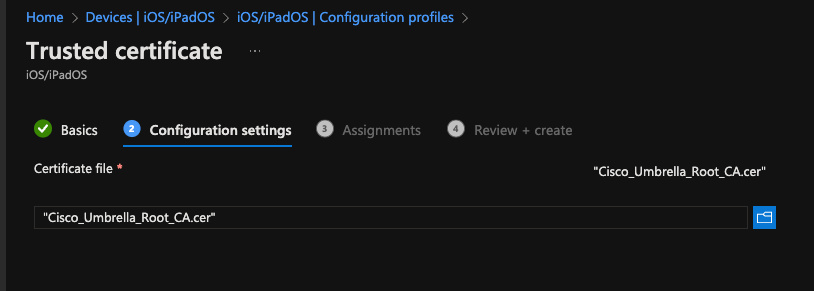 11754204605460
11754204605460
- For Step 3 - Assignments, select the group that contains your MDM iOS/iPadOS device and click "Next" and "Create"
- Go back to iOS/iPadOS devices and select your MDM-device and hit sync at the top once again (like step 24)
- Close and relaunch the Cisco Security Connector app again. You now see the status as "Protected by Umbrella"
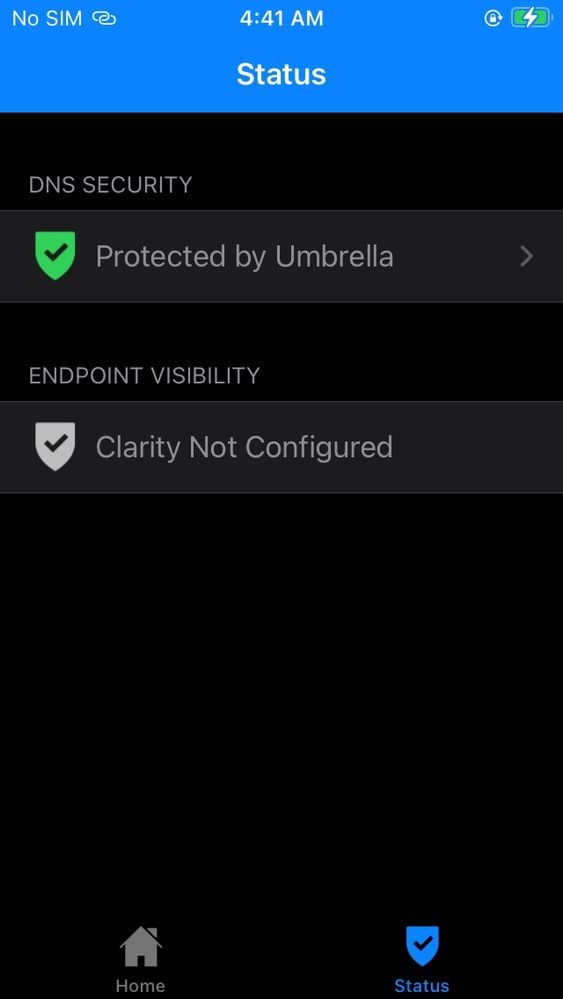 11754354334868
11754354334868
- You can verify you are being protected by Cisco Umbrella by going to welcome.umbrella.com in Safari
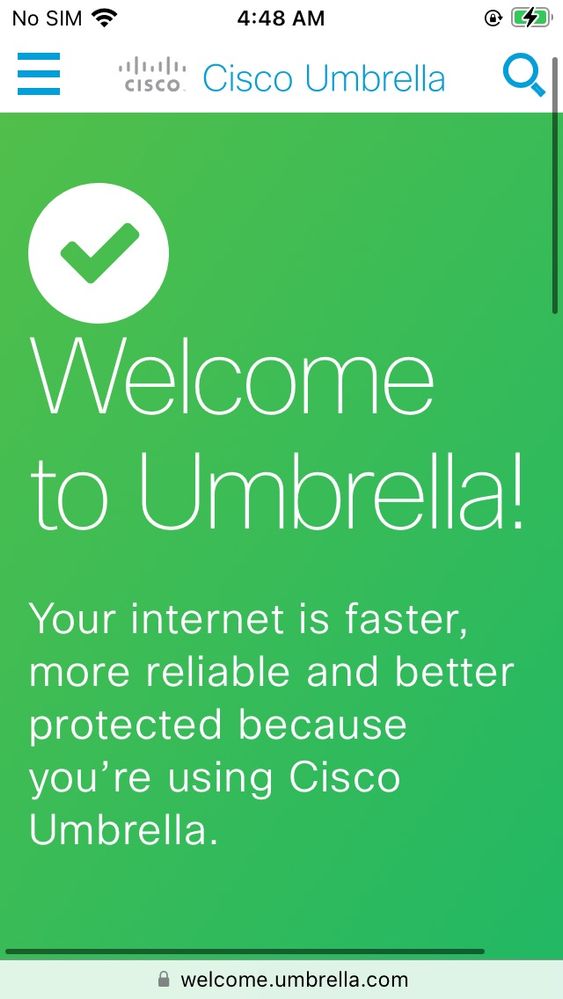 11754461786132
11754461786132
NOTE: you might have to disconnect and reconnect to WiFI to see the change in status. Alternatively, connect to your mobile hotspot and/or a different WiFi network, then back to the same one to see a change in status
Limitations
- If you have removed your iOS/iPadOS device from Intune MDM within the last 24 hours, and try to re-add it, it does not populate under "Members" for when you are trying to locate the device for your "Groups" in Step 14.
- You cannot have any "Restricted Apps" setting restricting the Umbrella app, and/or any "Show or Hide" setting to hide the Umbrella app applied in your device configuration profile.(Under your Intune admin center > Devices > iOS/iPadOS > Configuration)
Troubleshooting
- How to Collect Cisco Security Connector Diagnostics Logs
- CSC Log "Report A Problem" Function "No Admin Email" Error
- CSC: "Unprotected" status on mobile networks
If you are getting an Error: "User Name not recognized. This user is not authorized to use Microsoft Intune", go to the Azure Portal, under "Users" and select the username or account you are using to configure Intune, go to "Licenses" and make sure you have an active Intune License assigned to the user
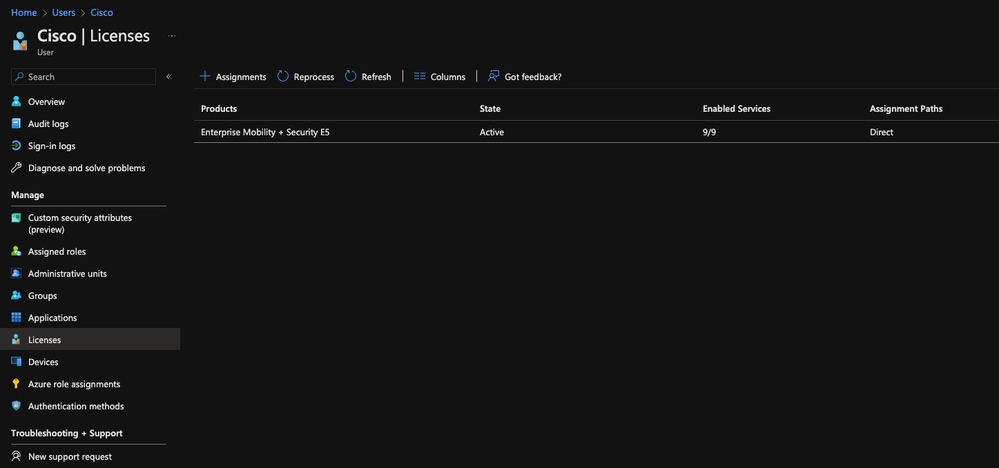 11754557401748
11754557401748
Logs
By default, the logs password is bypass_email_filters . This can also be located in the UmbrellaProblemReport.txt




























 Feedback
Feedback