Introduction
This document describes how to deploy the AnyConnect Umbrella Roaming Security Module using Cisco Firewall Management Console (FMC).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Access to the Cisco Umbrella Dashboard
- Access to Cisco Firewall Management Console (FMC), version 6.7 or later, as this version adds support for additional AnyConnect modules. For versions earlier than 6.7, FlexConfig can be used to deploy the module, you can refer to the Cisco documentation for details.
- AnyConnect Umbrella Module Profile (orginfo.json)
- AnyConnect VPN configuration is already complete and functional on the FMC/FTD
Components Used
The information in this document is based on these software and hardware versions:
- AnyConnect Umbrella Roaming Security Module
- Cisco Firewall Management Console (FMC) for versions 6.7 or later
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Overview

Note: Cisco announced the End-of-Life of Cisco AnyConnect in 2023. Cisco announced the End-of-Life for Umbrella Roaming Client on April 2, 2024, and the last date of support was April 2, 2025. Many Cisco Umbrella customers are already benefiting from migrating to Cisco Secure Client, and you are encouraged to begin migration as soon as possible to get a better roaming experience. Read more in this Knowledge Base article: How do I install Cisco Secure Client with the Umbrella Module?
This configuration guide covers the steps to provision the AnyConnect Umbrella Roaming Security Module via Cisco Firewall Management Console (FMC) for versions 6.7 or later.
AnyConnect Umbrella Module Installation and Download from the FMC :
Complete these steps to enable the AnyConnect Umbrella module installation/download from the FMC :
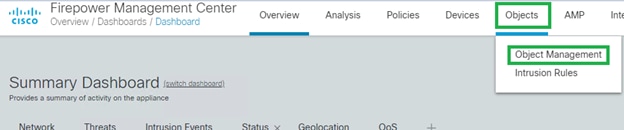
1. Go to Objects > Object Management:
 8178144512532
8178144512532
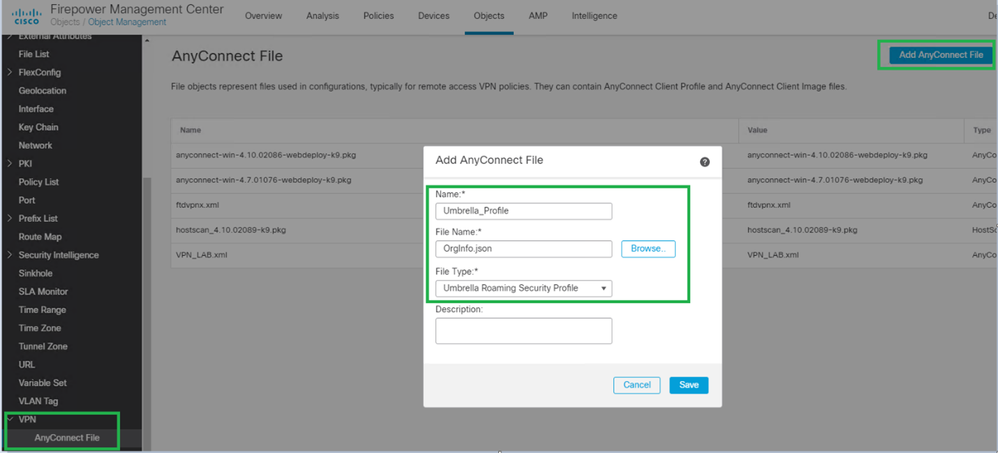
2. Navigate to VPN > AnyConnect File > Add AnyConnect File. Set a name for the profile (locally significant).
- Browse for the JSON downloaded from your Cisco Umbrella dashboard.
- Under File Type, select Umbrella Roaming Security Profile and then Save.
 8178144531860
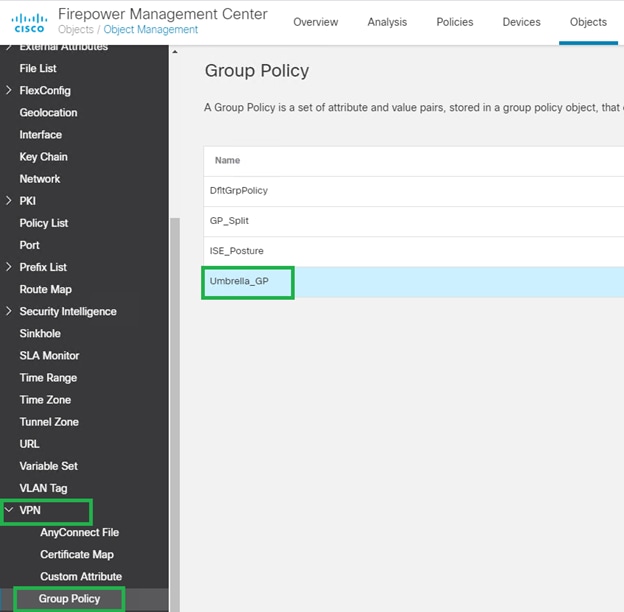
81781445318603. Once there, select Group Policy, then select the group policy that you are using to deploy Umbrella ("Umbrella_GP" in this case):
 8178147609492
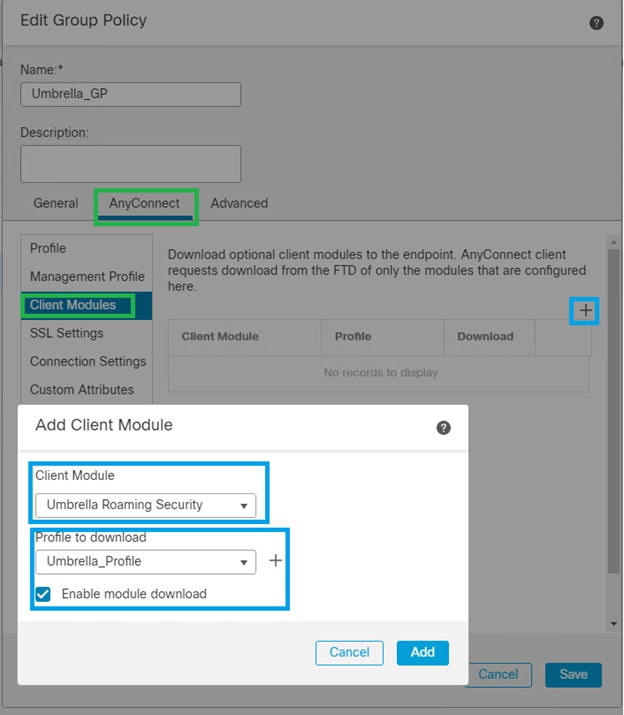
81781476094924. Select AnyConnect > Client Modules > Add Client Module.
- Under Client Module, select the Umbrella Roaming Client, and then Profile to download the profile we defined under step 2.
- Ensure that the Enabled module download is selected so that users connecting via AnyConnect can automatically download the Umbrella JSON profile.
 8178147636628
8178147636628Optional: VPN Local Authentication (FMC 7.0 or Later Required)
If you want to test a separate profile with Local Authentication on the FMC/FTD, you can complete these steps (FMC 7.0 or later is required):
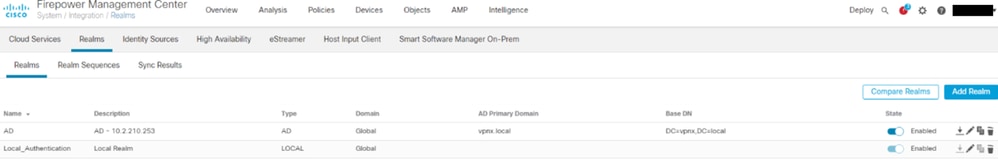
1. Create a local realm.
- Local usernames and passwords are stored in local realms.
- When you create a realm (System > Integration > Realms) and select the new LOCAL realm type, the system prompts you to add one or more local users.
2. Configure RA VPN to use local authentication.
- Create or edit an RA VPN policy (Devices > VPN > Remote Access).
- Create a connection profile within that policy.
- Specify LOCAL as the primary, secondary, or fallback authentication server in that connection profile.
3. Associate the local realm you created with an RA VPN policy.
- In the RA VPN policy editor, use the new Local Realm setting. Every connection profile in the RA VPN policy that uses local authentication can use the local realm you specify here.
 8178273923732
8178273923732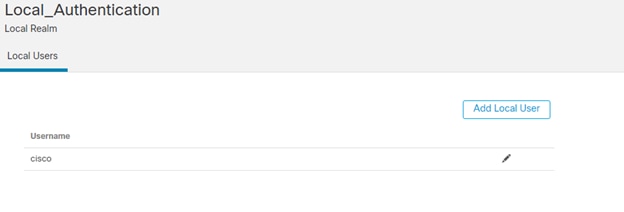 8178144714388
8178144714388
Additional Information
Cisco Firewall (formerly Firepower) Release Notes, Version 7.0.x








 Feedback
Feedback