Introduction
This document describes how to troubleshoot the "452 Suspected Replay Attack" error in the CSC SWG Module.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on Cisco Secure Client (CSC) and Secure Web Gateway (SWG).
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Problem
You are running into a "452 Suspected Replay Attack" error while trying to connect to the Cisco Secure Client (CSC) (formerly AnyConnect) Secure Web Gateway (SWG) module:
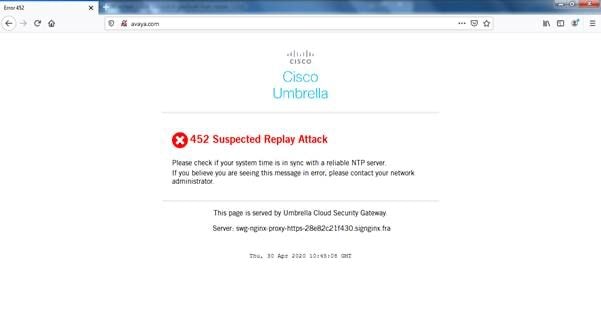 360073322452
360073322452
Solution
Please note that the message "replay attack" is a general warning for time discrepancies because one way to attack an encrypted connection is to repeatedly replay old packets. However, in this case, there is no replay attack actually occurring. Once the time on your computer has been changed, the error can be resolved.
Cause
This error can occur if the system clock on the endpoint is adrift by more than 4 minutes. Because the current time is used for negotiating encryption, if there is a large amount of time difference between the client and the server, they cannot mutually negotiate a safe encrypted connection.


 Feedback
Feedback